Weekly Threat Briefing: MuddyWater Expands Operations
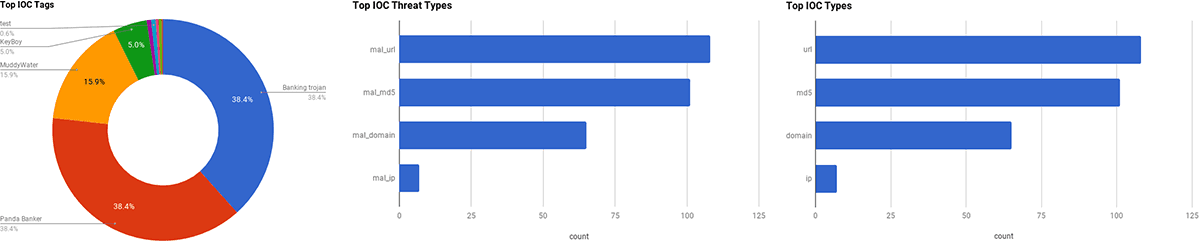

This section listed below contains summaries on various threat intelligence stories that occurred during the past week. The intelligence in this week’s iteration discuss the following threats: APT, Data breach, Drupal, FruityArmor, Gallmaker, KeyBoy, Magecart, Panda Banker, Phishing, Remote access tool, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Branch.io Flaws Exposed Tinder, Shopify, Yelp Users To XSS Attacks (October 15, 2018)
Several websites such as Tinder, Shopify, Yelp, Imgur, and many others, have been observed to suffer cross-site scripting (XSS) vulnerabilities due to a flaw in the Branch.io company all those affected sites use for sharing links, referral systems, and analytic purposes. These vulnerabilities were due to a Document Object Model (DOM)-based XSS because of Branch.io’s failure to use a Content Security Policy (CSP). A DOM-based XSS attack results in a payload being executed following the modification of the DOM environment in a victim’s browser so built-in XSS mitigation features cannot detect or respond to the malicious payload. The security vulnerabilities have been patched and there appears to be no malicious exploitation of this at the time of the writing.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Drive-by Compromise (T1189)
Pentagon Discloses Card Breach (October 13, 2018)
A Pentagon official announced that the US Department of Defense (DoD) suffered a data breach due to a third-party contractor. The breach affected approximately 30,000 military and civilian personnel. The breach occurred on October 4, 2018, after an unknown threat actor(s) compromised a third-party contractor somehow and used their access to get into the Pentagon’s network to steal travel information for the DoD personnel. They were able to gain illicit access to payment card data and personal information. The Pentagon announced that they have plans to contact all the affected personnel, and will offer fraud protection services.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Trusted Relationship (T1199)
No Cookie For CartThief, A New Magecart Variant (October 12, 2018)
A recent campaign has been observed to target small e-commerce websites, using similar tactics of the threat group "MageCart" to steal bank card credentials. This attack inputs malware dubbed “CartThief” on the payment pages of legitimate Magneto-hosted retail sites. Similar to Magecart attacks, the CartThief malware collects, encrypts, and sends Personally Identifiable Information (PII) taken from the payment page to the threat actor’s Command and Control (C2) server. To avoid detection, the malware does not contain user-identifying cookies or source codes. This campaign has been targeting smaller companies and are believed to be testing their malware before moving onto a larger-scaled attack, which may come during the holiday season.
Click here for Anomali recommendation
Largest Cyber Attack Against Iceland Driven By Complex Phishing Scheme (October 12, 2018)
The country of Iceland suffered a large-scaled phishing campaign utilising emails containing a malicious link. The campaign began on October 6, 2018, when individuals began receiving an email masquerading as the Icelandic police, Lögreglan, and asked them to come in for questioning or else face an arrest warrant. The email contained a link that impersonated the police’s website via typosquatting the official site by replacing a part of the domain with a capital “I” which appears similar to the typical lowercase “L.” The fake site requests users to enter in their “kennitala” which is the Icelandic version of a Social Security Number (SSN). The actors are able to verify that the user entered a legitimate kennitala which could potentially indicate that the actors have access to a database containing that information that was leaked in the past. The unknown threat actors used Remcos, a legitimate Remote Access Tool (RAT) used to access computers remotely as well as used a VBScript that runs at startup to ensure execution of Remcos. Once the user enters in their kennitala, they receive a password-protected archive that states to be the files with the information regarding the case against the individual; however, this archived file is actually the disguised RAT that is intended to siphon credentials, specifically banking credentials, and grant the threat actor access to the computer. The day after this attack was detected, the domain landing page was removed. As of this writing, it is unknown how many people were affected.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Link (T1192) | [MITRE ATT&CK] Remote Access Tools (T1219)
Fake Browser Update Seeks To Compromise More MikroTik Routers (October 12, 2018)
MikroTik routers have faced an increase in attacks, specifically exploiting the vulnerability registered as “CVE-2018-11847” that allows to bypass authentication and read arbitrary files. Despite MikroTik patching the vulnerability, a large number of routers remain unpatched and thus remain vulnerable. In this recent campaign, routers are sent to a fake browser update page which, if the update is deployed, runs a malicious download. A payload runs that pretends to be the update and once it runs, it pops up with an error code that is used as a decoy for the user, but still eventually unpacks a Python Dynamic Link Library (DLL). This leads to the router becoming infected using the CVE vulnerability and ultimately creates a backdoor on the machine to load a CoinHive cryptocurrency miner.
Click here for Anomali recommendation
Fake Adobe Flash Updates Hide Malicious Crypto Miners (October 11, 2018)
Unknown threat actors have launched a new fake Adobe Flash player update that installs the cryptocurrency miner, XMRig. It is not known how victims are being directed to the URLs serving the fake updater. When the fake Adobe Flash updater is executed, it first starts the cryptominer, then it executes a legitimate Flash updater borrowed from Adobe and accompanying browser pop-ups. The miner runs in the background and is able to run undetected. A user may be able to detect the miner if he/she does a thorough run-through of the files in the update where they will see Windows executable files with “AdobeFlashPlayer” names from non-Adobe web servers.
Click here for Anomali recommendation
Gallmaker: New Attack Group Eschews Malware To Live Off The Land (October 11, 2018)
A new threat group has been identified targeting government and military entities in Eastern Europe and the Middle East, according to Symantec researchers. The group, dubbed “Gallmaker,” has been observed to be active since at least December 2017. They utilise Living-off-the-Land (LotL) tactics and pre-existing open-source hacking tools to engage in their attacks. To obtain access to target machines, the threat group does not use malware, but rather uses spear phishing emails with malicious documents that exploit the Microsoft Office Dynamic Data Exchange (DDE) protocol to attain access into the system. If they gain access, they then utilise tools such as “WindowsRoamingToolsTask” to schedule PowerShell scripts, a “reverse_tcp” payload that download a reverse shell, a “WinZip” console to communicate with the command and control (C2) server, and “Rex PowerShell” library to create and manipulate PowerShell scripts to use with Metasploit exploits.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] PowerShell (T1086) | [MITRE ATT&CK] Obfuscated Files or Information (T1027) | [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Mshta (T1170)
MuddyWater Expands Operations (October 10, 2018)
The Advanced Persistent Threat (APT) group, MuddyWater, has been actively engaged in a variety of spear phishing campaigns against government, military, telecommunications, and educational institutions. Kaspersky Lab researchers determined that the targeted countries include Austria, Azerbaijan, Bahrain, Iraq, Iran, Jordan, Mali, Pakistan, Russia, Saudi Arabia, and Turkey. The APT group uses spear phishing emails that are geopolitically motivated. The emails contain a malicious Word document that requests macros to be enabled if opened. To evade spam and anti-virus detection, the document is password protected. If macros are enabled, obfuscated VBA code is executed which begins dropping files and adding registry entries into the machine. Communication with the command and control (C2) server is established and the threat actors obtain the victim’s public IP address along with their operating system, internal IP, machine name, domain name, and username to then accept or reject future victims based on their IP, country, geo-location, etc.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Obfuscated Files or Information (T1027) | [MITRE ATT&CK] Spearphishing Attachment (T1193)
Threat Actors Prey on Drupalgeddon Vulnerability To Mass-Compromise Websites And Underlying Servers (October 10, 2018)
Researchers at IBM discovered recent malicious activity targeting the content management system, Drupal. The unknown threat actors are leveraging two Remote Code Execution (RCE) vulnerabilities to create a backdoor using Shellbot malware on vulnerable sites. The two vulnerabilities are registered as “CVE-2018-7600” (also called Drupalgeddon 2.0) and “CVE-2018-7602.” The threat actors use automated scanning to identify vulnerable Drupal sites, and if one is found, they would then brute-force administrative access while running a Perl script to install the Shellbot backdoor. Shellbot contains multiple tools so it can commit Distributed-Denial-of-Service (DDoS) attacks as well as search for SQL injection weakness and other vulnerabilities. Both RCE vulnerabilities have patches released for them.
Click here for Anomali recommendation
Zero-day Exploit (CVE-2018-8453) Used In Targeted Attacks (October 10, 2018)
Kaspersky Lab researchers discovered a zero-day vulnerability in the Windows operating system, specifically the “win32k.sys.” This vulnerability allows for malware to obtain persistence in the system, and is registered as “CVE-2018-8453.” The vulnerability is classified as a Use-After-Free vulnerability located within the “win32kfull!xxxDestroyWindow” function and when successfully executed, results in a powerful arbitrary kernel Read/Write that works on a majority of Windows versions, including the latest updates. The exploit has been observed to be executed during the first stage of a malware installer. This particular malware campaign has been seen to be highly targeted towards victims in the Middle East. Based on this campaign’s use of a PowerShell backdoor and similar domains used for the Command and Control (C2) server, this campaign is being attributed to the Advanced Persistent Threat (APT) group “FruityArmor.”
Click here for Anomali recommendation
The Magecart Seal Of Approval: Card-Skimming Group Executes Scaled Supply Chain Attack On Shopper Approved (October 9, 2018)
The financially-motivated threat group, “Magecart,” has attacked another commercial site in their latest string of campaigns. This is yet another incident where the threat group comprised the check-out payment webpage of the “Shopper Approved” site and injected their own skimming code to steal credit card credentials. The incident was reported on September 15th, 2018 after Magecart modified the webpage’s script to contain the skimming code, but forgot to obfuscate it. The skimming code was removed from the site on September 17th, and Shopper Approved has now launched a full-scale internal investigation into the incident to determine who was affected and how the threat group was able to execute this in the first place.
Click here for Anomali recommendation
Threat Spotlight: Panda Banker Trojan Targets The US, Canada And Japan (October 9, 2018)
The banking trojan, Panda Banker, has been observed to actively be infecting targeted financial institutions in Canada, Japan, and the United States since 2016. The malware focuses upon stealing banking, credit card, and virtual wallet information from its victims. In this most recent campaign, Panda Banker is being delivered through the Emotet malware. The Panda Banker trojan is highly sophisticated in its evasion and attack techniques. In the infected machine, it will check the environment to determine if it is in a sandbox as well as search for debuggers and other malware analysis tools, and if any are detected, it will leave the environment and delete its payload file. If those come back clear, it creates four new files on the system, including a copy of itself. The malicious payload has code to connect to the threat actor’s Command and Control (C2) server to both get commands and exfiltrate the stolen information from the victims.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Man in the Browser (T1185) | [MITRE ATT&CK] Exfiltration Over Command and Control Channel (T1041) | [MITRE ATT&CK] Obfuscated Files or Information (T1027) | [MITRE ATT&CK] File Deletion (T1107)
Google Says Social Network Bug Exposed Private Data (October 8, 2018)
Google announced that their social network application, Google+, had a software bug that gave third-party applications access to users’ private profile data. The private information consisted of name, email address, age, gender, and occupation, but no data such as posts, private messages, Google account data or phone numbers were allegedly breached. The breach of certain Personally Identifiable Information (PII) was accessible via one of the Google+ People APIs. According to Google, there was no evidence that developers were aware of the bug or abusing the API to misuse the data. Google stated that approximately 500,000 accounts were affected, though they cannot determine which specific accounts were impacted. According to other news outlets, Google did not specify how long this bug had existed or why it did not disclose it closer to the security audit in March 2018 when it found the bug. Along with this announcement, Google stated that they will be shutting down Google+ for consumers due to its low usage amongst other reasons.
Click here for Anomali recommendation
Delivery (Key)Boy (October 8, 2018)
The Chinese-linked threat group, KeyBoy, has been observed recently participating in several different campaigns targeting government and Non-Government Organisations (NGOs) in Southeast Asia. One campaign used spear phishing emails pretending to be from India’s “National Informatics Centre”, oriented towards India’s Ambassador to Ethiopia. The email contained a malicious powerpoint attachment that, if opened, executes a script to install malware onto the targeted machine. The script utilises a pre-packed version of a popular and open-sourced exploit, “CVE-2017-0199.” The threat group’s campaign uses the malware family, “TSSL”, to install a backdoor onto the infected machine. Another campaign this threat group has been participating in recently utilise the “Titan” Android malware that infects a device if a victim downloads a malicious Android application.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193)
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



