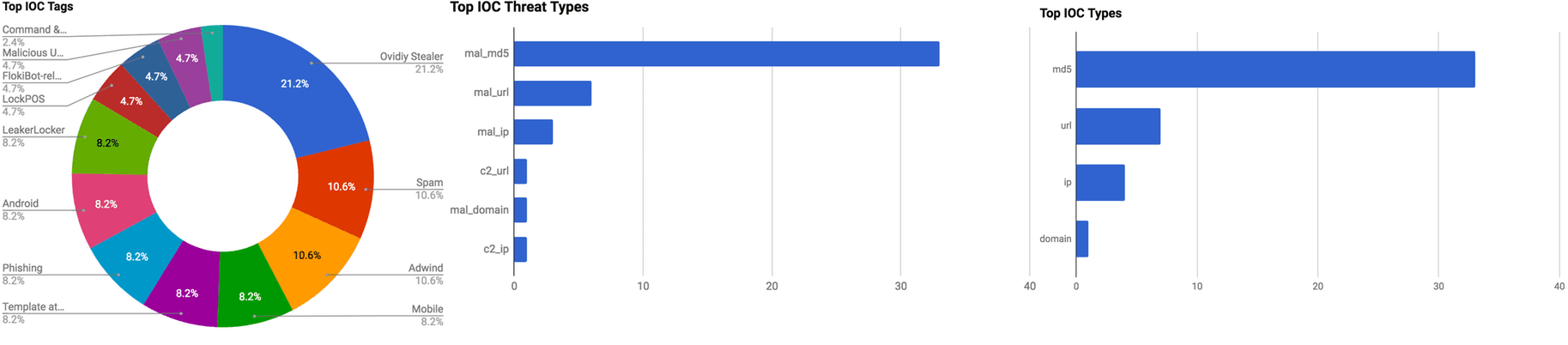

The intelligence in this week’s iteration discuss the following threats: Adobe Patches, Android Malware, Cloud Leaks, Point-of-Sale, Ransomware, Remote Access Trojan, and Windows Protocol Vulnerabilities. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
GhostCtrl Is an Android RAT That Also Doubles as Ransomware (July 17, 2017)
A new Android Remote Access Trojan (RAT) called "GhostCtrl RAT," has been used in a wave of attacks against Israeli healthcare organizations. GhostCtrl RAT is a variant of OmniRAT, which targets four operating systems: Android, Linux, macOS and Windows. GhostCtrl tries to hide itself by masquerading as popular applications. It has a large amount of functions such as data exfiltration, audio and video recording, ransomware, controlling bluetooth, and more.
Recommendation: Ensure that your company's firewall blocks all entry points for unauthorized users, and maintain records of how normal traffic appears on your network. Therefore it will be easier to spot unusual traffic and connections to and from your network to potentially identify malicious activity.
Tags: RAT, Android, Malware
New "WPSetup" Attack Targets Fresh WordPress Installs (July 14, 2017)
A campaign was discovered that took place in May and June that targeted fresh installations of WordPress which allowed an attacker to take over the hosting account. The attackers scanned for a URL used by new installations of WordPress, "/wp-admin/setup-config.php." The URL, if present, indicates that the user did not complete the installation steps. An attacker is able to go through the first steps of the installation and enter their own database server information. This allows an attacker to create an admin-level account on the victim's server, which gives the attacker the ability to run any PHP code on the hosting account.
Recommendation: Website administrators should always make sure that their WordPress installation is complete as soon as possible. Additionally, website administrators should also use a web application firewall to block unwanted access. One can also use a ".htaccess" file to limit access by IP address.
Tags: WordPress, Vulnerability
A .NET malware abusing legitimate ffmpeg (July 13, 2017)
A new wave of malware that records videos and spies on user activities is being distributed in a new campaign, according to researchers. First discovered in 2015, the malware's objective is to spy on a user's banking activities. The malware contacts a Command and Control (C2) server over TCP. The C2 server requests information on the infected machine, and then sends the infected machine a list of targeted banks which are saved in the registry. The legitimate program "FFmpeg" is downloaded and used to record videos of the victim. The recording event is triggered when the victim opens a website associated with banking. The video is then sent to the C2 server encoded in Base64.
Recommendation: Malware authors are always innovating new methods of communicating back to the control servers. Always practice Defense in Depth (don't rely on single security mechanisms - security measures should be layered, redundant, and failsafe). Also take a look at processes running in your computer in the background that should not be running. If there are unexpected processes running, you should terminate them and run a virus scan immediately.
Tags: Malware, FFmpeg, Banking
Meet Ovidiy Stealer: Bringing Credentials Theft to the Masses (July 13, 2017)
A new credential-stealing malware called "Ovidiy Stealer" has been found being advertised for sale on Russian-speaking marketplaces, according to Proofpoint researchers. The malware is offered for purchase for 450-750 Rubles (approximately $7-13 USD). Ovidiy Stealer is being distributed via emails with compressed executable attachments or links to an executable download. The malware can steal information from multiple web browsers and credentials from targeted applications on a Windows OS machine.
Recommendation: Always be on high alert while reading email, in particular when it has attachments, attempts to redirect to a URL, comes with an urgent label, or uses poor grammar. Use anti-spam and antivirus protection, and avoid opening email from untrusted or unverified senders.
Tags: Crenditla theft, Ovidiy
New Ransomware Threatens to Send Your Internet History and Private Pics to All Your Friends (July 13, 2017)
Two malicious applications were discovered in the Google Play Store to contain malware called "LeakerLocker," according to McAfee researchers. Researchers call the malware a form of ransomware except that it does not encrypt files. Instead the malware gathers information from the infected device and then displays a screen that threatens to share the data unless a payment is made. LeakerLocker can read various forms of data including Chrome history, device information, email address, pictures, as well as random text messages and call information.
Recommendation: Always keep your mobile phone fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. In addition, it is important to review the permission the application will request and comments from others who have downloaded the application. Furthermore, it is paramount that mobile devices be kept up-to-date with the latest security patches and employ trusted antivirus software.
Tags: Ransomware, LeakerLocker, Mobile
Telegram-based Katyusha SQL injection scanner sold on hacker forums (July 12, 2017)
A Russian-speaking hacker is offering an automated SQL injection vulnerability scanner tool, called "Katyusha," for sale on an underground forum. The tool is based on the open source Arachni web app security scanner. Katyusha is controlled via a web app and it can be monitored using the Telegram messenger. In addition to identifying SQL injection flaws within websites, the tool is able to perform actions such as brute-forcing logins, dumping databases, and uploading web shells.
Recommendation: Properly sanitize user provided data to prevent injection attacks. Using prepared statements and stored procedures, implementing escape schemes, properly limiting privileged accounts, and using input validation are also different steps you can take to better protect your company from SQL injections attacks.
Tags: Telegram, SQL, Vulnerability
Cloud Leak: How A Verizon Partner Exposed Millions of Customer Accounts (July 12, 2017)
UpGuard researchers discovered in late June that the Israeli technology company, "Nice Systems," controlled an Amazon S3 storage bucket that was misconfigured. The bucket was configured to be publicly accessible, and the data was downloadable by anyone who was able to guess the correct web address. The data was available for download for approximately one week, according to researchers. The files stored consisted of 14 million Verizon customer records with each record containing cell phone number, full name, and their account PIN.
Recommendation: Always make sure your cloud storage is properly configured. Experts have been warning companies that Amazon S3 buckets are too often misconfigured. Leaked data can be used by extortionists in an attempt to make money. Ensure that any cloud storage services you use are properly configured to only allow access to trusted and authorized users. Require multi-factor authentication for access to the most sensitive materials you store.
Tags: Verizon, Breach
LockPOS Joins the Flock (July 12, 2017)
Arbor Networks researchers have discovered that an inactive C2 server for the "FlokiBot" Point of Sale (POS) malware has recently become active. Interestingly, the C2 is not distributing FlokiBot but was instead identified to be distributing a new strain of POS malware dubbed "LockPOS." Additionally, researchers believe that the same actors behind FlokiBot are responsible for LockPOS because both are distributed by the same botnet have a mutual C2 host.
Recommendation: Customer facing companies that store credit card data must actively defend against Point-of-Sale (POS) threats and stay on top of industry compliance requirements and regulations. All POS networks should be aggressively monitored for these type of threats. In the case of FastPoS infection, the affected networks should be repopulated, and customers should be notified and potentially offered fraud protection to avoid negative media coverage and reputation.
Tags: POS, LockPOS
Spam Campaign Delivers Cross-Platform Remote Access Trojan Adwind (July 11, 2017)
The "Adwind" Remote Access Trojan (RAT) has reappeared in a spam-distribution campaign, according to Trend Micro researchers. The spam emails attempt to trick recipients into following a malicious URL to download a PDF file. This download will install the Adwind RAT that is capable of filming and retrieving videos, exfiltrating data, keylogging, stealing credentials, and taking pictures or screenshots.
Recommendation: Always be on high alert while reading email, in particular when it has attachments, attempts to redirect to a URL, comes with an urgent label, or uses poor grammar. Use anti-spam and antivirus protection, and avoid opening email from untrusted or unverified senders.
Tags: RAT, Adwind
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



