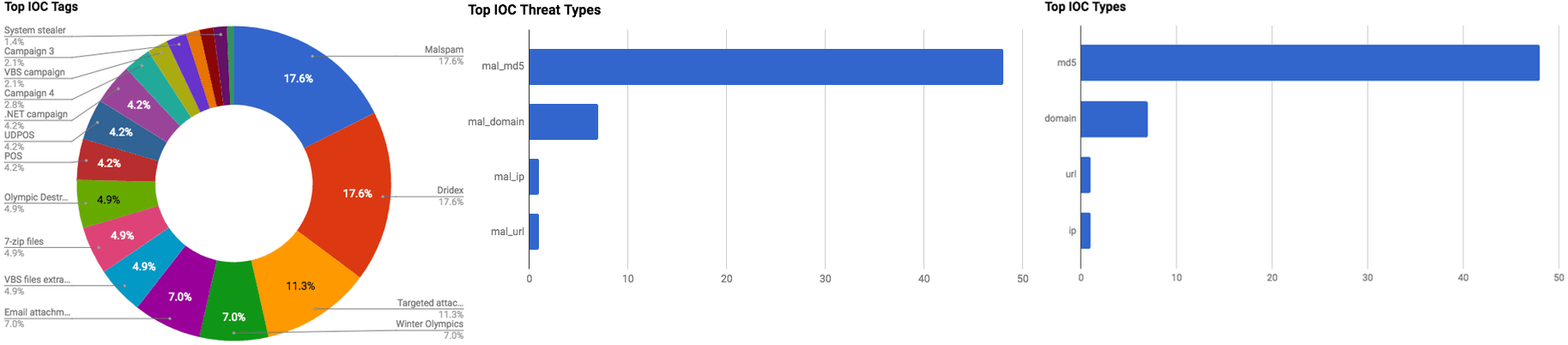

The intelligence in this week’s iteration discuss the following threats: Compromised server, Cryptocurrency miner, Data theft, Malspam, Phishing, Targeted attacks, Underground markets, and Vulnerabilities. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
Olympic Destroyer Takes Aim At Winter Olympics (February 12, 2018)
On February 11, 2018, Winter Olympic officials confirmed that the games were struck by a cyber-attack shortly before the opening ceremony on February 9. The target was the official Pyeongchang 2018 website. The website was inaccessible for approximately 12 hours. In addition, the internet and televisions stopped working in the main press center, as well as the Wi-Fi in the Pyeongchang Olympic stadium, according to the U.K. newspaper outlet The Guardian. Cisco Talos researchers believe with moderate confidence that they have identified malware samples used in this attack. The malware, dubbed “Olympic Destroyer,” appears to have been used with the objective to disrupt the games by rendering affected machines “unusable by deleting shadow copies, event logs and trying to use PSExec & WMI to further move through the environment.”
Click here for Anomali recommendation
Thousands of Government, Orgs’ Websites Found Serving Crypto Mining Script (February 12, 2018)
Security researcher Scott Helme discovered that the U.K.’s Information Commissioner’s Office (ICO) had a crypto miner installed on it. Further investigation led Helme to discover that the cause of this incident was the compromise of the “Browsealoud” service run by U.K. firm Texthelp; the service uses a JavaScript that “adds speech, reading, and translation to websites.” Texthelp’s script server was compromised and threat actors added an obfuscated script to the Browsealoud one that would limit the processing power of the crypto miner to assist in staying hidden. Researchers believe that approximately 4,200 websites were infected as a result of this incident.
Click here for Anomali recommendation
Lenovo Warns Critical Wi-Fi Vulnerability Impacts Dozens of ThinkPad Models (February 9, 2018)
Lenovo has released a security advisory in which they state that 24 of its ThinkPad models are to firmware vulnerabilities registered as “CVE-2017-11120” and “CVE-2017-11121.” These are the same firmware vulnerabilities that were patched by Apple and Google for their products in September 2017. The vulnerabilities are associated with controllers used by Broadcom’s wireless LAN driver that contain buffer overflow vulnerabilities. The buffer overflow can be exploited by threat actors to acquire arbitrary code execution on the adapter.
Click here for Anomali recommendation
U.S. Arrests 13, Charges 36 in “Infraud” Cybercrime Forum Bust (February 8, 2018)
The U.S. Department of Justice (DOJ) has announced that it has filed charges against 36 individuals for “Alleged Roles in Transnational Criminal Organization Responsible for More than $530 Million in Losses from Cybercrimes.” The DOJ worked with Asian, Australian, and European officials during this takedown called “Operation Shadow Web.” The individuals are believed to be influential members of an underground cybercrime forum called “Infraud.” The forum, which began in October 2010, had approximately 11,000 members prior to the takedown, who bought, sold, and traded various data and malwares including ATM skimmers, botnet hosting, credit card accounts, and malware.
Click here for Anomali recommendation
UDPOS – Exfiltrating Credit Card Data via DNS (February 8, 2018)
A Point-of-Sale (POS) malware, dubbed “UDPOS,” is being distributed by threat actors by impersonating a service pack provided by “LogMeln,”. According to Forcepoint researchers one sample, of UDPOS, has been observed in the wild, and there is evidence to suggesting it is being used. Evidence consists of LogMeln file names and Command and Control (C2) URLs. If the fake package is downloaded and the file named “update.exe” is executed, the content of the file is automatically launched with 7-Zip’s “RunProgram” feature. The malware then creates a new service to maintain persistence on an affected system. UDPOS is designed to steal magnetic stripe data (Track 1 and Track 2) from debit and credit cards by scraping the memory of running processes.
Click here for Anomali recommendation
Targeted Attacks In The Middle East (February 7, 2018)
Cisco Talos researchers have published their researcher regarding a new campaign consisting of targeted attacks against the Middle East. The threat actor(s) behind this campaign are using lure documents that purport to be “written by the Jordanian publishing and research house, Dar El-Jaleel.” Dar El-Jaleel is an organization now for their research and publications regarding the Palestinian-Israeli and Sunni-Shia conflicts. The campaign begins with a VBScript document titled “From inside Iran’s secret war in Syria.vbs” that generates a PowerShell script that creates a Microsoft Office document called “Report.doc” and opens it. The document contains a macro that is capable of creating a Windows Script File (WSF) and execute it to register the infected machine with the Command and Control (C2) server. The script then performs a loop to continually contact the C2 to download additional payloads. The payloads are designed to steal the information from the affected machine such as architecture, IP address, operating system, and username in addition to maintaining persistence on the host.
Click here for Anomali recommendation
Cisco: You Need to Patch Our Security Devices Again for Dangerous ASA VPN Bug (February 6, 2018)
Cisco has stated that it has found that its Adaptive Security Appliance (ASA) software is vulnerable to a new attack vector that its engineers identified. This means that the update Cisco issued for ASA in late January does not apply in this scenario. According to Cisco, the vulnerability can be exploited by a remote actor “to cause a reload of the affected system or to remote execute code.”
Click here for Anomali recommendation
T-Mobile Is Sending a Mass Text Warning of “Industry-Wide” Phone Hijacking Scam (February 5, 2018)
T-Mobile has distributed text messages en masse to its cell phone customers warning them of potential hijacking activity. The threat actor’s objective in this campaign is to gain control over a T-Mobile customer phone number. This can be accomplished by an actor calling T-Mobile and impersonating a legitimate customer and requesting a new SIM card for the customer’s phone number; a SIM card associated with authentic customer’s phone number can give an actor control over that number. An actor could also, again via social engineering, call T-Mobile and request that the phone number be moved to another provider. Once an actor has control over a phone number, he/she can pivot to other malicious activities to gain illicit revenue. This activity could include resetting passwords for financial accounts by asking a bank to send a reset link via text and two-factor authentication.
Click here for Anomali recommendation
Critical Flaw in Grammarly Spell Checker Could Let Attackers Steal Your Data (February 5, 2018)
Google Project Zero researcher Tavis Ormandy discovered a vulnerability in the “Grammarly” spell-checking extension for Chrome and Firefox. The vulnerability affects approximately 22 million Grammarly users by exposing authentication tokens to all websites that a user visits. A threat actor could exploit this vulnerability could steal said authentication tokens with a measly four lines of code, according to researchers.
Click here for Anomali recommendation
Malspam Using PDF Attachments to Push Dridex since 2018-01-30 (February 5, 2018)
Security researchers have observed a malspam campaign that is distributing the “Dridex” banking trojan via PDF file attachments. The PDF attachment contains a fake Google reCaptcha image that, when clicked, directs a user to a location that requests a 7-Zip (.7z) file be downloaded. Download and extraction of the 7-Zip file will unarchive a VBScript file that when run will result in Dridex infection.
Click here for Anomali recommendation
FEATURED RESOURCES

Anomali Cyber Watch: LockBit 5.0, Chrome Zero-Day CVE-2026-2441, Infostealer Targets OpenClaw, and more

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more


