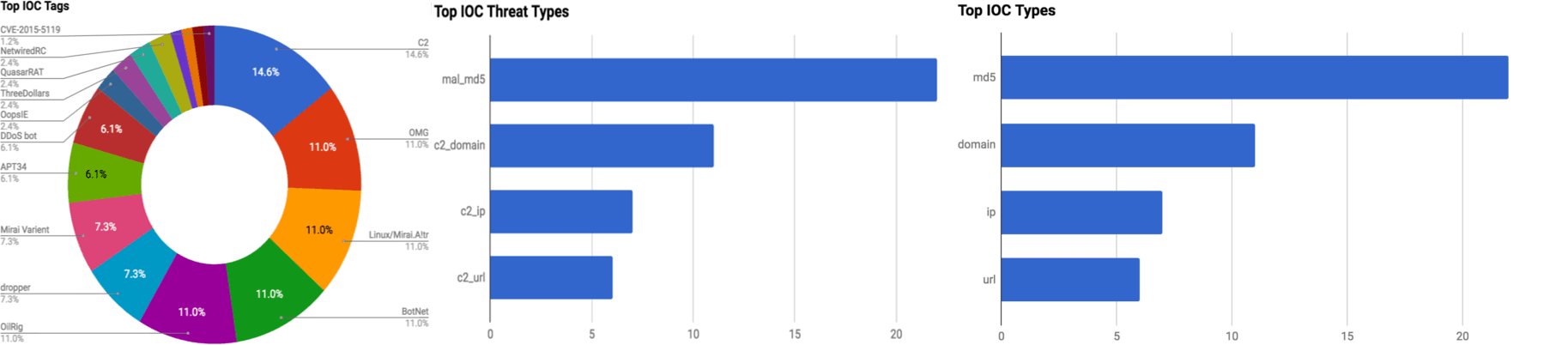

The intelligence in this week’s iteration discuss the following threats: APT37, ASMI Bypassing, Bank Account Breaches, Business Email Compromises, Cryptojacking, NetwiredRC, OilRig, OMG Botnet and QuasarRAT. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
OopsIE! OilRig Uses ThreeDollars to Deliver New Trojan (February 23, 2018)
The OilRig (APT34) threat group have recently been observed, by Palo Alto Networks researchers, delivering a new Trojan, dubbed "OopsIE". In one case the Trojan was delivered by a malicious document that uses macros. In the other observed case, the Trojan was delivered directly via a link. OopsIE contacts a Command and Control (C2) server to fetch commands. The trojan is able to run shell commands and upload/download files.
Click here for Anomali recommendation
Drive-by download campaign targets Chinese websites, experiments with exploits (February 22, 2018)
A new drive-by download attack has been planted on Chinese websites according to Malwarebytes researchers. The campaign leverages compromised websites to load external content via scripts and iframes. Three vulnerabilities observed being exploited on these websites are "CVE-2008-2551", "CVE-2015-5119", and "CVE-2016-0189" affecting an ActiveX component, Flash Player, and Internet Explorer respectively. The final payload being dropped was a DDoS bot.
Click here for Anomali recommendation
Chase 'Glitch' Exposed Customer Accounts (February 22, 2018)
A glitch on "Chase[.]com" allowed users to see other customer's bank accounts when logging in. The Director of Communications for JP Morgan Chase, Trish Wexler, stated that the incident happened for "a pretty limited number of customers". The glitch was the fault of the company and not a malicious actor. The glitch affected both users of "chase[.]com" and the Chase mobile banking app.
Click here for Anomali recommendation
OMG: Mirai-based Bot Turns IoT Devices into Proxy Servers (February 21, 2018)
A new Mirai-based bot which has been dubbed "OMG", has been discovered by Fortinet researchers. It differs from the original Mirai botnet, in that the string commands to determine if a successful brute force into an IoT device are different and add-ons are used to add a firewall rule to allow traffic on two random ports. OMG keeps Mirai's original modules. This variant is capable of Distributed Denial of Service (DDoS) attacks and setting up proxy servers.
Click here for Anomali recommendation
IBM X-Force IRIS Uncovers Active Business Email Compromise Campaign Targeting Fortune 500 Companies (February 21, 2018)
Threat actors of Nigerian origin are conducting a widespread campaign of credential harvesting, phishing, and social engineering for the objective of stealing financial assets. The groups used business email compromise scams to convince accounts payable personnel at Fortune 500 companies to initiate fraudulent wire transfers into accounts owned by attackers, resulting in the theft of millions of dollars. Compromises were achieved by sending spear phishing emails containing links, to fake "DocuSign" portals, requesting the user to authenticate their email provider to download the referenced document.
Click here for Anomali recommendation
Malicious RTF document leading to NetwiredRC and Quasar RAT (February 20, 2018)
New Rich Text Format (RTF) documents have been observed in the wild to use an interesting technique to get targets to enable macros, according to ThreatLabZ researchers. Threat actors are using a new technique that attempts to force users to run macros by spamming multiple popups for the user to enable macros in the hope that the user accepts one of them. This is achieved by embedding ten Excel spreadsheets with macros so that the user is prompted ten times to enable macros. If the user enables macros then a script will download the NetwiredRC and QuasarRat remote access trojans (RATs) as the final payload.
Click here for Anomali recommendation
Tesla Internal Servers Infected with Cryptocurrency Miner (February 20, 2018)
Tesla's cloud servers that are used by the companies engineers have been breached and installed with Monero cryptocurrency miners. The breach occurred when Tesla engineers forgot to secure their Kubernetes console with an access password. This allowed threat actors to access and discover Amazon Web Services (AWS) login credentials, to which the cryptocurrency miner was installed. The actors took care in regards to operational security and hid the mining pool behind CloudFlare, and throttled the software to only use a small portion of Tesla's AWS CPU resources.
Click here for Anomali recommendation
APT37 (REAPER): The Overlooked North Korean Actor (February 20, 2018)
FireEye has released a report introducing the Advanced Persistent Threat (APT) group dubbed APT37 (Group123, Scarcruft, FreeMilk). The group has been active since at least 2012 and their primary mission is to gather intelligence for the North Korean government pertaining to their military, political and economic interests. The group often deploys exploits for vulnerabilities soon after they are publicly announced. In addition, the group has recently exploited zero-day vulnerabilities, suggesting a sophisticated or well-resourced group. Furthermore, the group has a large arsenal of malware that is used to inject targets and exfiltrate data.
Click here for Anomali recommendation
AMSI Bypass With a Null Character (February 16, 2018)
A technique to bypass the Antimalware Scan Interface (AMSI) has been discovered which could be exploited to run malicious PowerShell scripts. AMSI is an interface standard in Windows 10 onwards that provides security software developers the ability to integrate their features better with Windows. The bug meant that if a null character in a PowerShell script was included then the full content of the string would not be scanned by AMSI, therefore allowing malicious content to be overlooked.
Click here for Anomali recommendation
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



