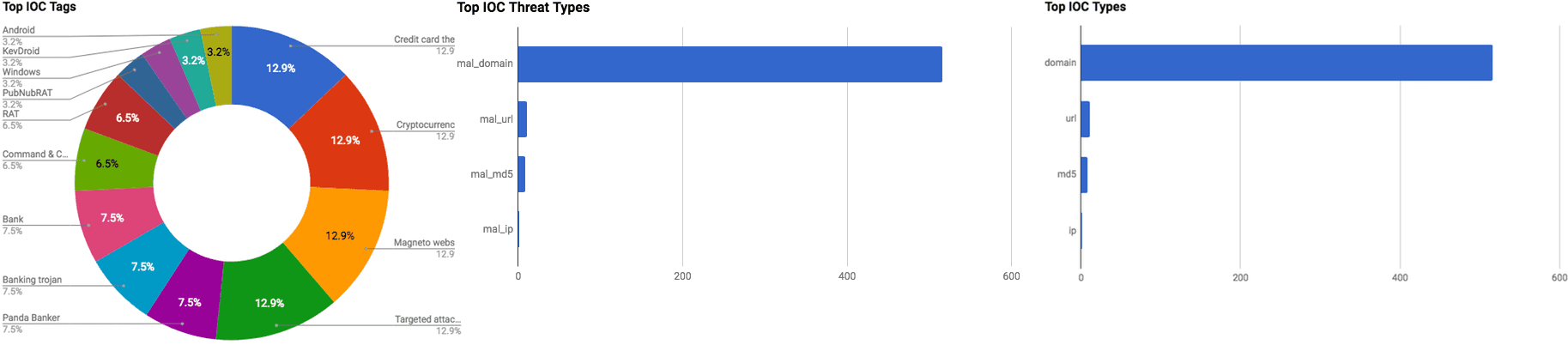

This section listed below contains summaries on various threat intelligence stories that occurred during the past week. The intelligence in this week’s iteration discuss the following threats: APT, Data breach, Credit card theft, Data leak, Malspam, Mobile malware, RAT, Targeted attacks, Threat group, Underground markets, and Vulnerabilities. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
Panerabread[.]com Leaks Millions of Customer Records (April 2, 2018)
The website U.S.-based bakery-café restaurant chain “Panera Bread” (panerabread[.]com) was leaking millions of customer records for at least eight months. Anyone individual who traveled to the correct URL would be able to view the plaintext data. The leaked data consists of birthdays, names, email and physical addresses, and the last four digits of a credit card number associated to approximately 37 million customers. The website was taken down on April 2, 2018. The exposed data belongs to customers who registered for an account that is used to order food for pickup or delivery. Panera Bread was informed of this data leak by security researcher Dylan Houlihan back in August 2017.
Click here for Anomali recommendation
Fake AV Investigation Unearths KevDroid, New Android Malware (April 2, 2018)
Cisco Talos researchers have discovered two variants of an Android Remote Administration Tool (RAT) dubbed “KevDroid,” and one Windows RAT dubbed “PubNubRAT.” The Android RATs are able to steal device information such as contacts, phone history, and SMS messages. In addition, one KevDroid variant was observed to exploit an Android vulnerability (CVE-2015-3636) to gain root access on an infected device. The PubNubRAT uses the “PubNub” platform, a global data stream network, as its Command and Control (C2) server.
Click here for Anomali recommendation
Compromised Magneto Sites Delivering Malware (April 2, 2018)
Approximately 1,000 “Magneto” (open source ecommerce platform) administrator portals have been found to be compromised, according to Flashpoint researchers. The threat actors behind this campaign are brute-force attacking, or using common default credentials, to gain access to administrator panels to conduct malicious activity on the Magento websites. The malicious activity consists of scraping credit card numbers and installing cryptocurrency-mining malware. The threat actors were observed to use a fake Adobe Flash Player update that was placed on the website in attempts to trick visitors to downloading the “update.” If this “update” is downloaded, a user will launch malicious JavaScript that downloads malware from an actor controlled servers on GitHub and from other compromised sites onto a user’s machine.
Click here for Anomali recommendation
Fin7 Syndicate Hacks Saks Fifth Avenue and Lord & Taylor Stores (March 30, 2018)
Gemini Advisory researchers observed that March 28, 2018, the threat group “Fin7” had made an announcement that over five million credit and debit cards will be offered for purchase on the underground carding forum called “Joker’s Stash.” Further research into the posting in combination with assistance from financial institutions, led to the discovered with high probability that the credit and debit card data was stolen from customers of “Saks Fifth Avenue” and “Lord & Taylor” department stores. Researchers believe that the threat group had compromised said store’s since “May 2017 to present.” At the time of this writing, the offer on Joker’s Stash consists of approximately 125,000 records and researchers believe that more records will be offered for purchase in the near future.
Recommendation: Bank accounts and credit card numbers should be protected with the utmost care, and only used with vendors that you trust to keep your information in compliance with the relevant standards. Regular monitoring of financial accounts in addition to identity protection and fraud prevention services can assist in identifying potential theft of data.
Click here for Anomali recommendation
150 million MyFitnessPal accounts compromised – here’s what to do (March 30, 2018)
Approximately 150 million user accounts of Under Armour’s fitness tracker “MyFitnessPal” have been compromised. The affected data includes email addresses, usernames, and hashed passwords; the passwords were hashed using “bcrypt.” While the “majority” of account passwords hashed it would take significant time to brute force attack, users could now be targets of spear phishing attacks because user email addresses were exposed.
Click here for Anomali recommendation
Microsoft Issues Out-Of-Band Update for Windows 7 & Windows Server 2008 (March 29, 2018)
Microsoft has issued a security update for Windows 7 and Windows Server 2008 R2 that is out of sync with the company’s typical Patch Tuesday cycle. This indicates that a high-severity problem has been addressed. Specifically, this security update fixes a vulnerability, registered as “CVE-2018-1038,” which was discovered by Swedish security expert Ulf Frisk that was caused by a different security update that was meant to fix the “Meltdown” vulnerability registered as “CVE-2017-5754.” The Meltdown update was found to have “accidentally flipped a bit that controlled access permissions to kernel memory.” The bit flip allows any process on the machine to read and write to any memory location, including kernel space memory, without the need for an exploit. A threat actor would need physical access to the machine, or have infected the machine with malware previously to exploit this vulnerability.
Click here for Anomali recommendation
Omitting the “o” in .com Could Be Costly (March 29, 2018)
Senior security advisor at “SecureWorks,” an Atlanta-based cybersecurity firm, discovered a large typosquatting campaign domain while trying to visit the website “espn[.]com.” Typosquatting is a tactic used by threat actors in which domains are registered that impersonate legitimate, and often well-known domains. The domains were all found to have omitted the “o” in “.com.” Additional research into the typosquatted domain revealed the IP address (85.25.199[.]30) is hosting thousands of typosquatted domains. Furthermore, visiting one of these domains redirectors visitors to one of two landing pages of which will sometimes request the visitor to complete a “short survey” in exchange for an opportunity to win gift cards, coupons and “other amazing deals!”
Click here for Anomali recommendation
Drupal core – Highly critical – Remote Code Execution – SA-CORE-2018-002 (March 28, 2018)
A highly critically rated vulnerability, registered as “CVE-2018-7600,” has been found to exist “within multiple subsystems of Drupal 7.x and 8.x.” CVE-2018-7600 is a remote code execution vulnerability that could be exploited by threat actors to take control of a Drupal website and also opening up other vectors for malicious activity.
Click here for Anomali recommendation
Monero-Mining HiddenMiner Android Malware Can Potentially Cause Device Failure (March 28, 2018)
A new Android malware, dubbed “HiddenMiner,” has been discovered to be infecting mobile devices to mine the “Monero” cryptocurrency, according to Trend Micro researchers. The malware is distributed via malicious applications in third-party application stores. HiddenMiner will use a device’s CPU to continuously mine Monero until the device’s resources are exhausted. This functionality of HiddenMiner could potentially cause a device to overheat which could possibly lead to device failure. At the time of this writing, the malware is primarily targeting individuals located in China and India.
Click here for Anomali recommendation
Fauxpersky: Credstealer Malware Written in Autohotkey Masquerades as Kaspersky Antivirus, Spreading Through Infecting USB Drives (March 28, 2018)
Cybereason researchers, while conducting an investigation in a customer’s environment, discovered a new credential-stealing malware dubbed “Fauxpersky.” The malware is written in “AutoHotKey” which allows individuals to write keystroke scripts that interact with the Windows operating system. Fauxpersky impersonates “Kaspersky Antivirus” and is distributed via infected USB drives. The researchers discovered four files that masqueraded as legitimate Windows files titled “Explorers.exe,” Spoolsvc.exe,” “Svhost.exe,” and “Taskhosts.exe” used for the malware to gain persistence on a machine. Fauxpersky uses keylogger functionality to steal information and replicates itself to drives listed on a machine for persistence.
Click here for Anomali recommendation
North Korean Malicious Cyber Activity (March 28, 2018)
The United States Computer Emergency Readiness Team (US-CERT) has issued an alert regarding new malicious activity attributed to the government Democratic People’s Republic of Korea (DPRK). The Advanced Persistent Threat (APT) group “HIDDEN COBRA,” the cyber-arm of the DPRK, has created a new trojan called “SHARPKNOT.” SHARPKNOT is a “wiper ” malware that destroys an infected Windows machine by overwriting the Master Boot Record (MBR) and deleting files on network shares and connected external storage devices.
Click here for Anomali recommendation
AVCrypt ransomware attempts to eradicate your antivirus (March 27, 2018)
The security researcher known as “MalwareHunterTeam” has found a new ransomware, dubbed “AVCrypt,” that attempts to uninstall antivirus software from an infected machine prior to encrypting files. At the time of this writing, it is unknown how AVCrypt targets machines. To remove antivirus software, the ransomware will target “Windows Defender” and “Malwarebytes,” or query for other antivirus software before attempting to remove it. This is followed by deleting Windows services that are needed for the antivirus software to function properly. Researchers note that AVCrypt appears to be in the developmental stages because the ransom note does not contain any instructions or request for payment.
Click here for Anomali recommendation
Panda Banking Zeros in on Japanese Targets (March 27, 2018)
Arbor Networks has found that a threat actor is targeting Japanese financial institutions with the “Panda Banker” (PandaBot, Zeus Panda) trojan. Panda Banker is a variant of the notorious Zeus malware family. Panda Banker is capable of stealing account numbers, and user credentials with the objective of eventually stealing money. This malicious activity is accomplished by exploiting web browser vulnerabilities and web-injections. Panda Banker is offered for purchase on underground forums, and researchers note that this is the first observation of the newest variant in version 2.6.6.
Click here for Anomali recommendation
Mozilla Releases Security updates for Firefox (March 27, 2018)
The United States Computer Emergency Readiness Team (US-CERT) has issued an alert regarding security updates for a vulnerability in “Firefox” and “Firefox Extended Support Release (ESR).” A threat actor could exploit the vulnerability to “cause a denial-of-service condition.”
Click here for Anomali recommendation
Malspam Pushing Sigma Ransomware (March 26, 2018)
A malspam campaign has been observed to be distributing the “Sigma” ransomware, according to security researchers. The email text claims that attachment is a receipt that is password protected, and provides the password to access the document. In addition, the text also reminds the recipient not to open attachments or follow links from unknown senders. If the document is opened and the password is entered, the document then requests that “Enable Content,” “Enabled Editing,” or “Enable Macro” be clicked to properly view the document. If any of these are enabled, the infection process for Sigma will begin.
Click here for Anomali recommendation
Forgot About Default Account? No Worries, GoScanSSH Didn’t (March 26, 2018)
Cisco Talos researchers have discovered a new malware family, dubbed “GoScanSSH,” that threat actors are using to compromise Secure Shell (SSH) servers and subsequently targets Linux systems. The malware is written in the “Go” programming language and uses the “Tor2Web” proxy service for Command and Control (C2) communication in attempts to make tracking and potential C2 takedown more difficult. Researchers believe that the initial infection vector for GoScanSSH is “likely an SSH credential brute-force attack against a publicly accessible SSH server that allowed password-based SSH authentication.”
Click here for Anomali recommendation
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



