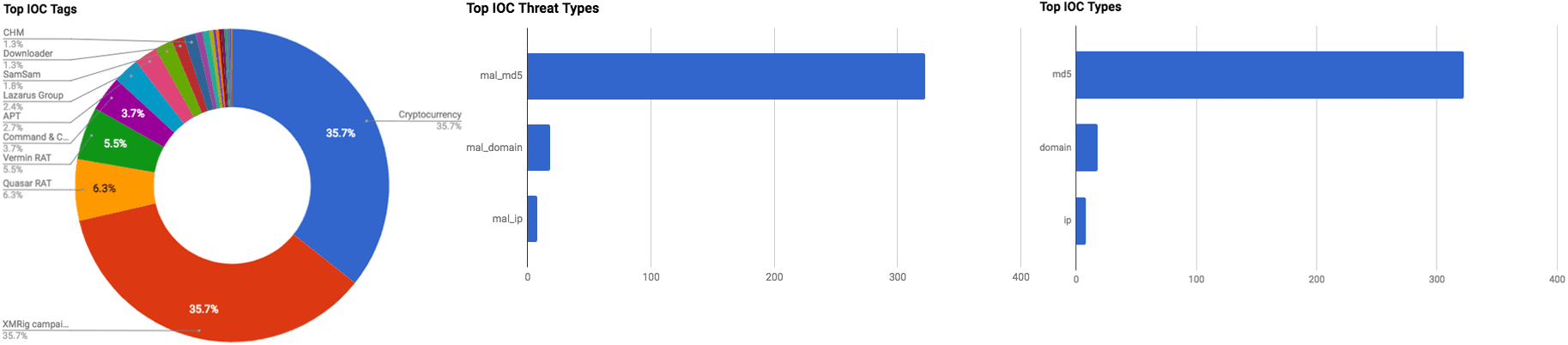

The intelligence in this week’s iteration discuss the following threats: APT, Cryptocurrency miners, Phishing, Ransomware, Remote Access Trojan, Targeted attacks, Tax-related malicious activity, and Vulnerabilities. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
Tax Identity Theft Awareness Week (January 29, 2018)
The United States Computer Emergency Readiness (US-CERT) team has issued a statement regarding “Tax Identity Theft Awareness Week” which is January 29 through February 2. The U.S. Internal Revenue Service (IRS) and other federal agencies are offering information and resources in regard to tax-related threats and scams.
Click here for Anomali recommendation
VERMIN: Quasar RAT and Custom Malware Used In Ukraine (January 29, 2018)
A new Remote Access Tool/Trojan (RAT) dubbed “Vermin” has been observed being used by threat actors in combination with the “Quasar” RAT in a campaign that dates back to late 2015, according to Palo Alto Unit 42 researchers. The Vermin RAT is being distributed via malicious Self Extracting (SFX) executables, some of which will display documents that are themed after the Ukrainian Ministry of Defense as Vermin before continuing to execute the RAT. Vermin is capable of stealing various information from an infected machine such as architecture, OS name, local IP address, machine name, and username. Researchers note that Vermin is also capable of installing a keylogger if the malware does not detect an antivirus software on the machine.
Click here for Anomali recommendation
Keylogger Campaign Hits Over 2,000 WordPress Sites (January 26, 2018)
Approximately 2,000 WordPress powered websites have been identified to be infected with a keylogger on the backend administrator login page, according to security researchers. On the front end, researchers observed an in-browser cryptocurrency miner. Threat actors are targeting older versions of WordPress websites, or those that are using older themes and plugins that are still vulnerable to known exploits to inject code into the Content Management System source code. Researchers found that actors are injecting malicious code in two parts, the first being the keylogger hosted on a third-party domain, and the second is the JavaScript Monero miner “Coinhive.”
Click here for Anomali recommendation
OilRig Uses RgDoor IIS Backdoor on Targets in the Middle East (January 25, 2018)
The Advanced Persistent Threat (APT) group “OilRig” has been observed to be using a new Internet Information Services (ISS) backdoor dubbed “RGDoor,” according to Palo Alto Unit 42 researchers. Researchers believe that OilRig installs RGDoor on a compromised web server to function as a secondary backdoor in case a “TwoFace” webshell used by the group is discovered. At the time of this writing, researchers do not have any HTTP logs that show OilRig interacting with RGDoor, however, researchers did find that RGDoor is written in the programming language C++. This means the backdoor will result in a Dynamic Link Library (DLL), inside of which researchers found a function named “RegisterModule.” This led researchers to believe that the DLL “used as a custom native-code HTTP module that the threat actor would into ISS.”
Click here for Anomali recommendation
Large Scale Monero Cryptocurrency Mining Operation using XMRig (January 24, 2018)
Palo Alto Networks Unit 42 researchers have discovered a significant cryptocurrency mining campaign that is primarily targeting individuals in Asia, northern Africa, and South America. Researchers believe that as many as 30 million people have been infected with the open-source cryptocurrency mining software “XMRig” that is used to mine “Monero.” Threat actors are using Virtual Basic script (VBS) files and URL shortening services to install and execute the XMRig payload. Researchers observed the actors are presenting users with Adf.ly (URL shortening service that pays URL owner every time URL is clicked) links that will automatically download XMRig on to the machine.
Click here for Anomali recommendation
Lazarus Campaign Targeting Cryptocurrencies Reveals Remote Controller Tool, an Evolved RATANKBA (January 24, 2018)
The Advanced Persistent Threat (APT) group “Lazarus Group” has been observed conducting a new campaign with the objective of stealing cryptocurrencies, according to Trend Micro researchers. The specific cryptocurrencies Lazarus Group is targeting is Bitcoin (BTC) and Ant Share (NEO). To target cryptocurrencies, the group is distributing lure documents such as Microsoft Office documents with malicious macros, Microsoft Compiled HTML Help (CHM) files, and script downloaders to infect users with a new version of the “RATANKBA” backdoor. RATANKBA is able to receive and execute commands and steal data from an affected machine. RATANKBA has been observed to be transferring shares of NEO to a different wallet, as well as mining NEO on an infected machine. of This version of RATANKBA is written in PowerShell to make it more difficult to detect.
Click here for Anomali recommendation
New Hide ‘N Seek IoT Botnet Using Custom-Built Peer-to-Peer Communication Spotted in the Wild (January 24, 2018)
A new Internet-of-Things (IoT) botnet, dubbed Hide ‘N Seek (HNS), has added been observed infecting devices beginning in January 2018, according to Bitdefender researchers. The botnet was first observed January 10 and slowly ceased activity the next several days. Researchers then observed HNS on January 20 and noticed that its creators had “significantly improved” it. HNS spreads like a work via a technique that randomly generates IP addresses to identify possible targets. In addition, HNS can conduct web exploitation via the “Reaper” exploit, registered as CVE-2016-10401. Furthermore, HNS is capable of stealing data and executing arbitrary code on an affected device.
Click here for Anomali recommendation
Severe Electron Framework Vulnerability Impacts Apps Like Skype and Slack (January 23, 2018)
Researchers have discovered that the application writing platform “Electron” is affected by a remote code execution vulnerability. The vulnerability, registered as “CVE-2018-1000006,” affects Electron applications only if they are running on Windows and “register themselves as the default handler for a protocol like “mayapp://.” MacOS and Linux applications are not affected by this vulnerability. Some popular applications that are affected by this vulnerability are Discord, Signal, and Skype.
Click here for Anomali recommendation
desuCrypt Ransomware in the Wild with DEUSCRYPT and Decryptable Insane Variants (January 22, 2018)
Researchers have discovered that two variants of the open-source ransomware project “desuCrypt” are currently being used in the wild. The variants are named after the file extensions they append to encrypted files. One appends .insane and the other .DEUSCRYPT. Researchers do not note how the ransomware is infecting its victims, however, the creator of ID ransomware Michael Gillespie has managed to create decryptors for both variants.
Click here for Anomali recommendation
SamSam – The Evolution Continues Netting over $325,000 in 4 Weeks (January 22, 2018)
Cisco Talos researchers and Incident Response Services have published a report discussing a new variant of the “SamSam” ransomware. SamSam has targeted multiple industries including government, healthcare, and Industrial Control Systems. This variant’s encryption process is the same as previous versions, however, the actor(s) behind the malware have added new string obfuscation and anti-analysis techniques to make detection more difficult. Researchers note that the infection vector for this SamSam variant is currently unknown and that investigation into the matter is ongoing. However, researchers do note that SamSam targeted JBoss hosts in 2016, and that this campaign the actor(s) may have used compromised RDP/VNC servers to gain an initial foothold.
Click here for Anomali recommendation
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



