Weekly Threat Briefing: US Arrests Chinese Man Involved With Sakula Malware Used in OPM and Anthem Hacks
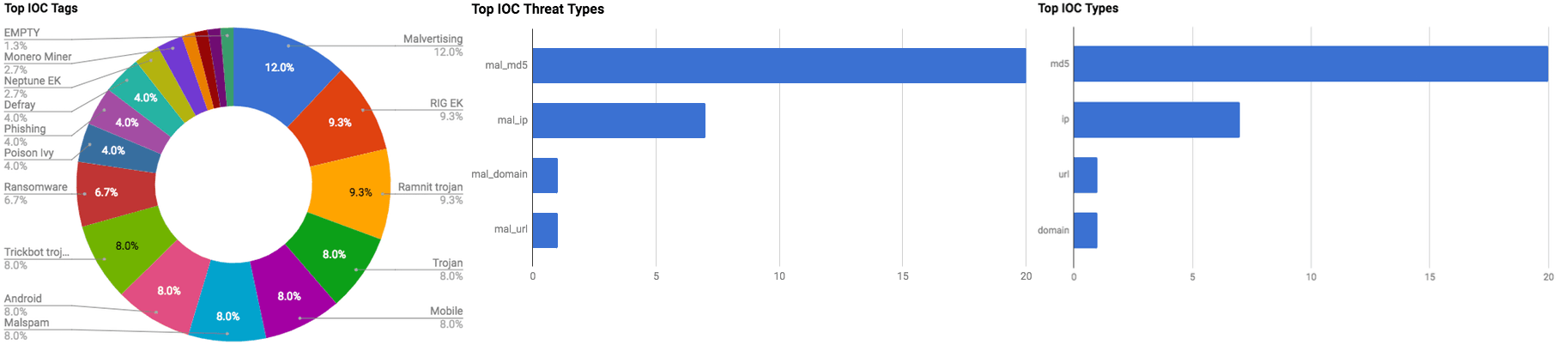

The intelligence in this week’s iteration discuss the following threats: APTs, Cybercriminals, Data leaks, Exploit kits, Malspam, Malware, Mobile, Ransomware, Vulnerabilities. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
US Arrests Chinese Man Involved With Sakula Malware Used in OPM and Anthem Hacks (August 26, 2017)
The U.S. Federal Bureau of Investigation has arrested an individual believed to be associated with the Advanced Persistent Threat (APT) group "Deep Panda." Additionally, the bureau believes that the suspect, Yu Pingan, is associated with the "Sakula" malware that was used in attacks against U.S. companies including the Office of Personnel Management (OPM) and Anthem Health Insurance.
Recommendation: Defense in depth (layering of security mechanisms, redundancy, fail safe defense processes) is the best way to ensure safety from APTs, including a focus on both network and host based security. Prevention and detection capabilities should also be in place. Furthermore, all employees should be educated on the risks of phishing, how to identify such attempts.
Tags: APT, Crybercriminal
New Arena Crysis Ransomware Variant Released (August 25, 2017)
A new variant of the "Crysis" ransomware has been discovered in the wild by security researcher Michael Gillespie. As of this writing, it is unknown how the malware is being distributed, but in previous campaigns threat actors compromised Remote Desktop Services and manually installed Crysis. This variant is capable of encrypting mapped network drives and unmapped network shares and appends ".arena" to each encrypted file.
Recommendation: Ransomware is a continually evolving threat. It is paramount to have a comprehensive and tested backup solution in place. In the unfortunate case a reproducible backup is not in place, make sure to check for a decryptor before considering payment; avoid payment at all costs. Ransomware should be reported to law enforcement agencies who are doing their best to track these actors and prevent ransom from being a profitable business for cyber criminals.
Tags: Ransomware, Crysis variant, Arena
New EMPTY CryptoMix Ransomware Variant Released (August 25, 2017)
The security researchers "MalwareHunterTeam" have discovered a new variant of the CryptoMix ransomware called "EMPTY," named after the text it appends to encrypted files. The file encryption is the same as previous versions, however, there is a new ransom note that contains new email contacts for victims.
Recommendation: Ransomware is a continually evolving threat. It is paramount to have a comprehensive and tested backup solution in place. If a reproducible backup is not available, there may a decryptor available that can assist in retrieving encrypted files. Additionally, educate your employees about the dangers of downloading applications when they are not offered from the website of the official provider/developer.
Tags: Ransomware, CryptoMix variant, EMPTY
Defray – New Ransomware Targeting Education and Healthcare Verticals (August 24, 2017)
A new ransomware family, dubbed "Defray" has been discovered to be targeting specific sectors in two separate campaigns, according to Proofpoint researchers. In August 2017, actors used the Defray ransomware in phishing emails with malicious Microsoft Word attachments that targeted the education and healthcare sectors in one campaign, and manufacturing and technology sectors in another campaign. The campaigns primarily target entities in the U.K. and U.S., and the ransom note demands $5,000 USD for the decryption key.
Recommendation: Always run antivirus and endpoint protection software to assist in preventing ransomware infection. Maintain secure backups of all your important files to avoid the need to consider payment for the decryption key. Emails received from unknown sources should be carefully avoided, and attachments and links should not be followed or opened. Your company should sustain policies to consistently check for new system security patches. In the case of ransomware infection, the affected systems should be wiped and reformatted, even if the ransom is paid. Other machines on the same network should be scanned for other potential infections.
Tags: Ransomware, Defray
New Multi-Platform Malware/Adware Spreading Via Facebook Messenger (August 24, 2017)
Kaspersky Labs researchers have discovered a new malware campaign that is being spread via "Facebook Messenger." Researchers note that initial distribution of the malware is conducted through Messenger via links that lead to a Google document. The document purports to be a playable movie that uses an image from the user’s Facebook profile. If the fake movie is clicked, it redirects to a set of websites that enumerates the user’s browser, operating system, and other information. As of this writing, it is unknown how exactly the malware is actually spreading via Messenger, but it is possible it is spreading through clickjacking, hijacked browsers, or stolen Facebook credentials.
Recommendation: Messages that attempt to redirect a user to link should be viewed with scrutiny, especially when they come from individuals with whom you do not typically communicate. Education is the best defense. Inform your employees on the dangers of phishing, specifically, how they can take place in different forms of online communications, and whom to contact if a phishing attempt is identified.
Tags: Malware, Adware
WAP-billing Trojan-Clickers on the Rise (August 24, 2017)
Threat actors behind mobile trojans that steal money have been discovered to be using the "WAP-billing" (Wireless Application Protocol) mobile payment system, according to Kaspersky Labs researchers. Researchers note that other variants of the identified families, "Ubsod" and "Autosus," were also executing other malicious payloads in addition to stealing money. Additionally, the malware is capable of executing commands in the device shell, sending SMS messages, stealing credentials and credit card data via overlays, and showing advertisements.
Recommendation: Always keep your mobile phone fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. In addition, it is important to review the permission the application will request and comments from others who have downloaded the application. Furthermore, it is paramount that mobile devices be kept up-to-date with the latest security patches and employ trusted antivirus software.
Tags: Android, Mobile, Trojan
ziVA: Zimperium’s iOS Video Audio Kernel Exploit (August 23, 2017)
An iOS audio kernel exploit has been discovered by Zimperium researchers that they claim should work on all iOS devices running iOS 10.3.1 or earlier. In total, seven vulnerabilities were found that are associated with memory corruption. Some of the vulnerabilities can be exploited to gain kernel access to a device. Any iOS device running version 10.3.1 or earlier should be updated as soon as possible if they have not been already.
Recommendation: Mobile devices should be kept up-to-date at all times to provide the most recent security patches. In this case, the proof of concept code has been released which increases the likelihood that threat actors will attempt to exploit the vulnerabilities in the wild.
Tags: iOS, Vulnerability
Deep Analysis of New Poison Ivy Variant (August 23, 2017)
Fortinet Labs researchers have identified a phishing campaign that is distributing a new variant of the "Poison Ivy" malware. The actors behind this campaign are using malicious PowerPoint file attachments titled "Payment_Advice.ppsx." If the file is opened, a prompt will appear that attempts to trick the user into running the external program by purporting that the user is enabling Adobe Flash Player. The malware uses anti-analysis and evasion techniques such as checking registry locations for analysis tools and using legitimate Microsoft processes to conduct malicious activity.
Recommendation: All employees should be educated on the risks of phishing, specifically, how to identify such attempts and whom to contact if a phishing attack is identified. It may also be useful for employees to stop using email attachments, in favor of a cloud file hosting service like Box or Dropbox.
Tags: Malware, Poison Ivy
BEC Campaigns Target Organizations Across Sectors Using Credential Phishing (August 23, 2017)
A Business Email Compromise (BEC) campaign has been ongoing by a threat actor from March 28, 2017 to at least August 8, 2017, according to Flashpoint researchers. Researchers state that this campaign had a low detection rate because of its simplistic tactics. The threat actors sent out approximately 73 PDF documents in phishing emails that purport to be a "secure online document." If the PDF is opened, a recipient would be presented with a prompt to view a secure online document. The prompt leads recipients to a fake webpage of the targeted organization and requests that work credentials be entered.
Recommendation: It is important that your company institute policies to educate your employees on phishing attacks. Specifically, how to identify such attacks and whom to contact if a phishing email is identified. Furthermore, maintain policies regarding what kind of requests and information your employees can expect to receive from colleagues and management.
Tags: BEC, Phishing, Credential theft
Bankbot Dropper Hiding on Google Play (August 22, 2017)
An application in the Google Play store called "Earn Real Money Gift Cards" has been identified to contain the "Bankbot" trojan, according to SfyLabs researchers. Another application, from the same developer, was identified to be a dropper for the Bankbot trojan called, "Bubble Shooter Wild Life." The Bubble Shooter application requires the user to enable it as an Accessibility Service, which will then display a screen that purports to be a Google update. Researchers note that the dropper application appears to be in development because it’s ability to install malicious APKs is currently disabled in the source code.
Recommendation: Always keep your mobile phone fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. In addition, it is important to review the permission the application will request and comments from others who have downloaded the application. Furthermore, it is paramount that mobile devices be kept up-to-date with the latest security patches and employ trusted antivirus software.
Tags: Android, Mobile, Bankbot, Trojan
Hiking Club Malvertisements Drop Monero Miners Via Neptune Exploit Kit (August 22, 2017)
Since July 16, 2017, Trend Micro researchers have observed changes in a malvertising campaign that leads users to the Neptune Exploit Kit (EK). The changes consist of new payloads dropped by Neptune, different Uniform Resource Identifier (URI) patterns, and abusing legitimate popup advertisement services that redirect to fake advertisements. The fake advertisements imitate legitimate sources and if clicked, will redirect to Neptune which then checks the Adobe Flash versions and will attempt to exploit vulnerable versions of Flash or Internet Explorer.
Recommendation: Malvertising and exploit kits techniques are often updated by threat actors, therefore, keeping software updated with the latest security patches is critical for users and enterprises. This includes both the operating system and all applications being used. Make sure there is a security system in place that can proactively provide a comprehensive defense against attackers targeting new vulnerabilities.
Tags: Malvertising, Neptune, Exploit kit, Monero, Malware
Igexin Advertising Network Put User Privacy at Risk (August 21, 2017)
The advertising Software Development Kit (SDK) called, "Lgexin," has the ability to spy and gather data on Android users who have downloaded applications that contain the kit, according to Lookout researchers. Lgexin has been identified in approximately 500 applications in the Google Play store, and the applications have been downloaded approximately 500 million times. Researchers note that the malicious activity can be altered at any time and that the SDK is capable of stealing device information as well as incoming calling numbers and call times. Google Play has since removed the applications that contained this feature.
Recommendation: Always keep your mobile phone fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. In addition, it is important to review the permission the application will request and comments from others who have downloaded the application. Furthermore, it is paramount that mobile devices be kept up-to-date with the latest security patches and employ trusted antivirus software.
Tags: Mobile, Data theft
Online Hotel Booking Service Allegedly Exposed Sensitive Data (August 21, 2017)
Kromtech researchers have discovered a publicly accessible Amazon Web Services (AWS) database that may be associated with the online group hotel booking service company, "Groupize." The database required no login or passwords to access the data that researchers state shows how "the discount hotel business model works in detail." Besides business models, other data consisted of payment information such as credit card numbers, expiration date, and CVV codes, among other data.
Recommendation: Always make sure your cloud storage is properly configured. Experts have been warning companies that Amazon S3 buckets are too often misconfigured. Leaked data can be used by extortionists in an attempt to make money. Ensure that any cloud storage services you use are properly configured to only allow access to trusted and authorized users. Require multi-factor authentication for access to the most sensitive materials you store.
Tags: Misconfigured database, Data leak
Malspam Continues Pushing Trickbot Banking Trojan (August 21, 2017)
The Trickbot banking trojan is continuing to be distributed by threat actors via financially-themed malspam, according to researchers. The actors are using email addresses that appear to be associated with NatWest Bank via typosquatting their email address. The message purports that the recipient’s August 2017 financial statement is available for download in the attached Microsoft Word attachment. If the attachment is downloaded and macros are enabled, the macro will generate a URL to retrieve the Trickbot binary.
Recommendation: All employees should be educated on the risks of malspam, and how to identify such attempts. Poor grammar and urgent content are often indicators of these type of attacks. Additionally, messages that request a recipient to open a file attachment should also be avoided.
Tags: Malspam, Trickbot trojan, Malware
Seamless Campaign Uses RIG EK to Drop Ramnit Trojan (August 21, 2017)
Researchers have discovered a malvertising campaign that uses the RIG Exploit Kit (EK) to infect users with the Ramnit banking trojan. If a user clicks on a malvertisement and visits the website, they will be directed to a location that hosts a script that will then point to a RIG EK iframe. The exploit kit then attempts to use an Adobe Flash Player exploit to install a Ramnit payload.
Recommendation: Malvertising and exploit kits techniques are often updated by threat actors, therefore, keeping software updated with the latest security patches is critical for users and enterprises. This includes both the operating system and all applications being used. Make sure there is a security system in place that can proactively provide a comprehensive defense against attackers targeting new vulnerabilities.
Tags: RIG, Exploit kit, Ramnit trojan, Malware
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
CrySiS Tool TIP
CrySiS is a Ransomware variant that first appeared in early 2016. The CrySiS ransomware is commoditized and distributed amongst forums to many actors. Distribution and delivery of the CrySiS ransomware is left to the actor who has purchased the malware. In the summer of 2016 Trend Micro reported that CrySiS was delivered to hosts in the Southern Pacific region (Australia and New Zealand) via RDP-brute force attacks. As of mid-2016 the builder for CrySiS leaves the PDB-path of C:crysisReleasePDBpayload.pdb as an artifact within the unpacked binary. Additionally the encrypted files are renamed using the pattern of filename.ext.id-UNIQUEID.emailAddr.newext as described below.
Tags: CrySiS
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



