
The intelligence in this week’s iteration discuss the following threats: Bitpaymer, Cobian RAT, KHRAT, Locky Ransomware, Malspam, Sarahah, Turla and WireX. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
US Government Site Was Hosting Ransomware (September 1, 2017)
On Wednesday, August 31, 2017, researcher Ankit Anubhav tweeted out that the U.S. Federal Communications Commission's (FCC) website was hosting a malicious JavaScript downloader. It was discovered that the downloader was contained in a .zip archive that included obfuscated PowerShell led to installations of the "Cerber" ransomware. As of this writing, it is uncertain how the website was hosting malware, although some researchers contend that it was caused by an issue in the FCC's API.
Recommendation: Sometimes webmasters discover that one of their sites has been compromised months after the initial infection. Websites, much like personal workstations, require constant maintenance and upkeep in order to adapt to the latest threats. In addition to keeping server software up to date, it is critical that all external facing assets are monitored and scanned for vulnerabilities. The ability to easily restore from backup, incident response planning, and customer communication channels should all be established before a breach occurs.
Tags: Website, Ransomware
Locky Ransomware Attacks Ramp Up (August 31, 2017)
AppRiver have identified a new malspam campaign that is on a significant scale in which actors are distributing the "Lukitus" variant of the "Locky" ransomware. Researchers state that over a period of 24 hours approximately 23 million spam emails were distributed. The messages were found to use the following subject lines: documents, images, photo, pictures, please print, and scans. The emails come with zip attachment that contains a Visual Basic Script (VBS) contained in a secondary zip file. If the attachment is clicked, the VBS file begins a downloader that pulls down Locky.
Recommendation: Ransomware is a continually evolving threat. It is paramount to have a comprehensive and tested backup solution in place. In the unfortunate case a reproducible backup is not in place, make sure to check for a decryptor before considering payment; avoid payment at all costs. Ransomware should be reported to law enforcement agencies who are doing their best to track these actors and prevent ransom from being a profitable business for cyber criminals.
Tags: Malspam, Ransomware, Locky, Lukitus
Cobian RAT – A Backdoored RAT (August 31, 2017)
A new Remote Access Trojan (RAT) called, "Cobian," is being offered for free on various underground markets, according to Zscaler researchers. Cobian has a backdoor module that allows a threat actor to take full control of all machines that have used the builder kit to create malicious payloads. In this context, an actor could have full control of machines infected with Cobian. The malware is being distributed through a .zip archive that impersonates a Microsoft Excel spreadsheet icon.
Recommendation: Ensure that your company's firewall blocks all entry points for unauthorized users, and maintain records of how normal traffic appears on your network. Therefore, it will be easier to spot unusual traffic and connections to and from your network to potentially identify malicious activity.
Tags: RAT, Cobian
Updated KHRAT Malware Used in Cambodia Attacks (August 31, 2017)
An updated version of the KHRAT Remote Access Trojan (RAT) has been identified to be targeting Cambodian citizens, according to Palo Alto Unit 42 researchers. KHRAT is distributed via spear phishing emails that contain a Microsoft Word attachment that requests macros to be enabled because the user's Office version is not compatible with the document. KHRAT is capable of logging keystrokes, remote shell access, and taking screenshots.
Recommendation: It is important that your company institute policies to educate your employees on phishing attacks. Specifically, how to identify such attacks and whom to contact if a phishing email is identified. Additionally, ensure that your company's firewall blocks all entry points for unauthorized users, and maintain records of how normal traffic appears on your network. Therefore, it will be easier to spot unusual traffic and connections to and from your network to potentially identify malicious activity.
Tags: Spear phishing, RAT, KHRAT
Locky Ransomware Adds Anti Sandbox Feature (August 31, 2017)
A new version of the "Locky" ransomware has been discovered to contain an ant-sandbox feature, according to Malwarebytes researcher Marcelo Rivero. Locky is being distributed by spam campaigns that contain malware embedded Microsoft Word documents. Interestingly, the malware will not begin its infection until after a user clicks the enable content on the document, and after the document is closed. The text on the document claims that content editing needs to be enabled in order to view the document. Actors are expecting the user to close the document once no other content becomes viewable.
Recommendation: Always be on high alert while reading email, in particular when it has attachments, attempts to redirect to a URL, comes with an urgent label, or uses poor grammar. Use anti-spam and antivirus protection, and avoid opening email from untrusted or unverified senders. Additionally, it is important to have a comprehensive and tested backup solution in place for the unfortunate case of ransomware infection.
Tags: Spam, Ransomware, Locky
Gazing at Gazer: Turla's New Second Stage Backdoor (August 30, 2017)
The Advanced Persistent Threat (APT) group, "Turla," has created a new sophisticated piece of malware, according to ESET researchers. The malware, dubbed "Gazer," has been discovered inside consulates and embassies throughout Eastern Europe. Gazer has been active since 2016 and specifically targets Windows machines. The malware is distributed via spear phishing emails and operates as a backdoor that is capable of activity monitoring and remote code execution.
Recommendation: Defense in depth (layering of security mechanisms, redundancy, fail safe defense processes) is the best way to ensure safety from APTs, including a focus on both network and host based security. Prevention and detection capabilities should also be in place. Furthermore, all employees should be educated on the risks of phishing, how to identify such attempts.
Tags: APT, Turla, Gazer, Backdoor
Inside the Massive 711 Million Onliner Spambot Dump (August 30, 2017)
Security researcher Troy Hunt has published a report regarding a large publicly available database. The database contains a significant amount of emails addresses number in the hundreds of millions. Some of the email addresses are listed with corresponding passwords. The addresses are used to send spam from the bot called, "Onliner Spambot," according to Hunt and another researcher and collaborator, Benkow moʞuƎq.
Recommendation: Always be cautious while reading email, in particular when it has attachments or comes with an urgent label or poor grammar. Use anti-spam and antivirus protection, and avoid opening email from untrusted or unverified senders. Additionally, the significant amount of compromised email addresses is due cause for concern, and it may be appropriate for your company to change corporate and personal email passwords.
Tags: Onliner Spambot, Compromise, Email addresses
Bitcoin Exchanges in South Korea Hacked and North Korea is the Prime Suspect (August 29, 2017)
South Korea's Cyber Warfare Research Center has revealed that at least one South Korean Bitcoin exchange was breached. South Korea believes that the Democratic People's Republic of Korea (DPRK) is likely responsible and that the compromise was accomplished via "a social engineering email campaign." Researchers contend that the DPRK is targeting Bitcoin exchanges in response to the recent sanctions imposed against it. It may also be possible that financial institutions will become more frequent targets by DPRK actors.
Recommendation: Members of the financial services industry should be aware they are specifically targeted by malware due to the nature of their business. Never open files from unverified sources, and be aware of other infections vectors such as email attachments and infected websites.
Tags: Threat group, Theft
FBI/IRS-Themed Email Scam Spreads Ransomware (August 29, 2017)
The U.S. Internal Revenue Service (IRS) has issued a warning stating that malicious actors are impersonating them in a new phishing campaign. The email purports that the IRS is sending a Federal Bureau of Investigation (FBI) questionnaire because of changes that were made to American tax laws on June 21, 2017. If the document attachment is downloaded, the email recipient will be infected with ransomware.
Recommendation: The impersonation of government agencies continues to be an effective spear phishing tactic. All users should be informed of the threat phishing poses, and how to safely make use of email. In the case of infection, the affected system should be wiped and reformatted, and if at all possible the ransom should not be paid. Implement a backup solution for your users to ease the pain of losing sensitive and important data.
Tags: Phishing, Ransomware
Beware of Hurricane Harvey Relief Scams (August 29, 2017)
The U.S. Federal Trade Commission (FTC) issued an alert on August 28, 2017, warning consumers to be cautious of an increase in charity scams. The FTC is warning that individuals who wish to donate to assist charities, such as in response to Hurricane Harvey, to check if the online location is legitimate by using evaluation websites that they recommend. The U.S. Computer Emergency Readiness Team (US-CERT) is also reminding individuals that threat actors will often use a natural disaster theme in their phishing campaigns.
Recommendation: All employees should be educated on the risks of phishing, specifically, how to identify such attempts and whom to contact if a phishing attack is identified. It may also be useful to inform employees that after a natural disaster or major political event threat actors will theme their malicious activity about what just occurred.
Tags: Charity scams, Natural disaster
Jimmy Nukebot: From Neutrino With Love (August 29, 2017)
The actors behind the "NeutrinoPOS" banking trojan have rewritten their malware, according to Kaspersky Labs researchers. The actors restructured the main body by moving the functions to modules. This causes the malware, dubbed "Jimmy," to be more difficult to analyze because identifying which processes will stop the malware from stealing financial data is more complicated. However, the functionality to steal financial information, such as credit card data from the memory of the infected device, has been removed. The trojan will now receive modules from a remote node needed to accomplish malicious tasks.
Recommendation: Customer facing companies that store credit card data must actively defend against Point-of-Sale (POS) threats and stay on top of industry compliance requirements and regulations. All POS networks should be aggressively monitored for these type of threats. In the case of FastPoS infection, the affected networks should be repopulated, and customers should be notified and potentially offered fraud protection to avoid negative media coverage and reputation.
Tags: Jimmy trojan, POS, Credit card theft
Ransomware Behind NHS Lanarkshire Cyber-Attack (August 28, 2017)
NHS Lanarkshire, the health board responsible for the health care of approximately 650,000 people, has confirmed that it was infected with ransomware on August 25, 2017. As a result, NHS Lanarkshire had to cancel some procedures and appointments as staff worked over the weekend to restore their systems and services. The ransomware was identified to be a variant of "Bitpaymer" and it requested $300 USD per infected machine for the decryption key.
Recommendation: Maintain secure backups of all your important files to avoid the need to consider payment for the decryption key. Emails received from unknown sources should be carefully avoided, and attachments and links should not be followed or opened. Your company should sustain policies to consistently check for new system security patches. In the case of ransomware infection, the affected systems should be wiped and reformatted, even if the ransom is paid. Other machines on the same network should be scanned for other potential infections.
Tags: Cyber-attack, Ransomware
Tech Firms Team Up to Take Down "WireX" Android DDoS Botnet (August 28, 2017)
Multiple security and technology companies have released information regarding their combined work to dismantle a large mobile Distributed Denial-of-Service (DDoS) botnet. The botnet, "WireX," consisted of tens of thousands of compromised Android devices that were used to launch DDoS attacks against hospitality websites. Google has stated that they have identified approximately 300 applications in the Play Store related to the WireX bot and that they have been blocked. Additionally, Google also stated that they are in the process of removing the applications from all affected devices.
Recommendation: As this story portrays, sometimes malicious applications find their way into official stores, therefore, it is important to be skeptical of all applications, especially free applications. Websites and documents that request additional software is needed in order to access, or properly view content should be properly avoided. Additionally, mobile security applications provided from trusted vendors are recommended.
Tags: Mobile, Malware, WireX, DDoS botnet
Beware! Viral Sarahah App Secretly Steals Your Entire Contact List (August 28, 2017)
Security analyst, Zachary Julian, has discovered that the recently new anonymous messaging application "Sarahah" gathers users' contact lists. The contact lists, including phone numbers and email addresses, are surreptitiously uploaded to the company's servers. This upload is done when an Android or iOS user first downloads and installs the application. The creator of the application claims that this uploading was supposed to be used for a "find your friends" feature that was delayed and that this issue will be fixed in the next update.
Recommendation: Always keep your mobile phone fully patched with the latest security updates. Use the Google Play Store / Apple App Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. In addition, it is important to review the permission the application will request and comments from others who have downloaded the application. Furthermore, it is paramount that mobile devices be kept up-to-date with the latest security patches and employ trusted antivirus software.
Tags: Mobile, Data theft
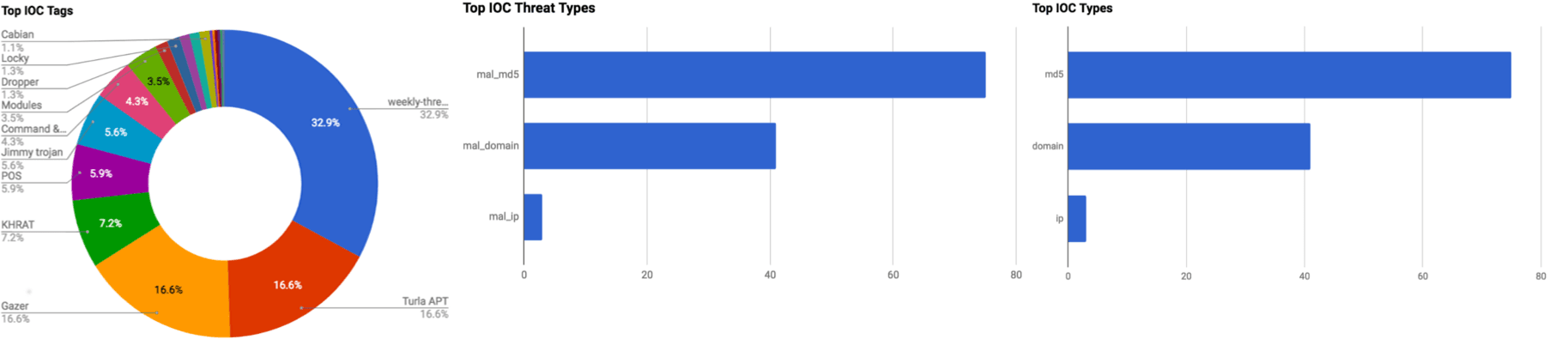
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
Locky Tool Tip
Locky is ransomware that is widely spread via phishing messages. Locky first appeared in early 2016. Locky is strongly correlated with the cyber criminal groups related to the dridex and necurs botnets. Multiple waves of Locky samples are distributed daily. The delivery mechanism has evolved over time. The delivery mechanism has been spam messages with executable attachments, MS Word document attachments using Macros to retrieve then execute Locky, and Zip files that extract JavaScript loaders that retrieve then execute Locky. Hosts compromised by Locky display a ransom-note with instructions on how to decrypt the encrypted files. Encrypted files are renamed .locky or .zepto.
Tags: Locky, Ransomware
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



