Weekly Threat Briefing: US State Governments Receive Malware-Laden CDs From China Via Snail Mail
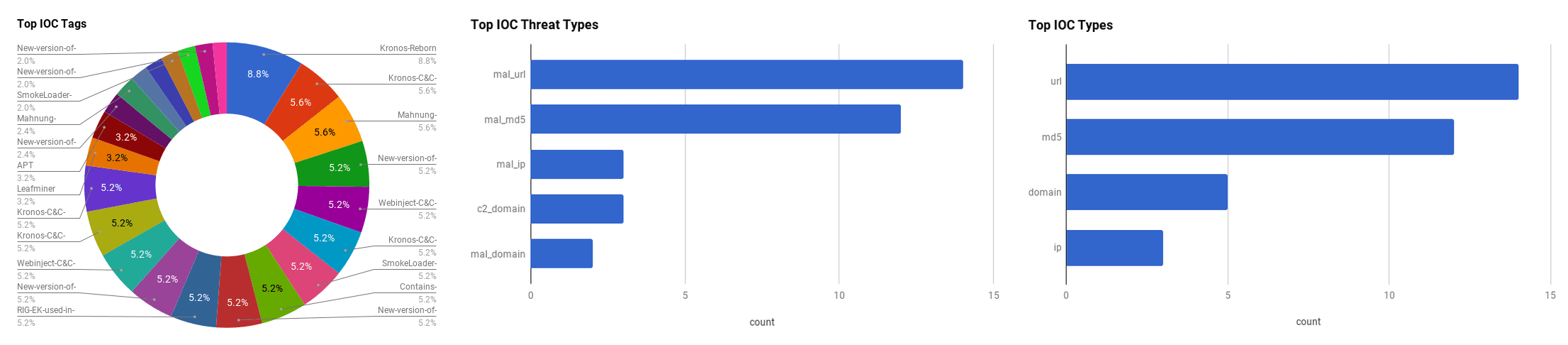

The intelligence in this week’s iteration discuss the following threats: APT34, Hide n Seek Botnet, LeafMiner, Macro Enabled Malspam, Phishing, and QUADAGENT. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
US State Governments Receive Malware-Laden CDs From China Via Snail Mail (July 30, 2018)
The State Department of Cultural Affairs has received snail mail letters from an unknown sender in China that contained CDs filled with malware and notes that were written in confusing English. The letters are suspected to have been sent to various local and state-level government departments, and the Multi-State Center for the Distribution and Analysis of Information (MS-ISAC) has issued a non-public statement notifying the offices to not do anything with the CDs. It is unclear if any of the CDs have been placed into any government machines and used at the time of this publication.
Click here for Anomali recommendation
US Shipping Giant COSCO Reportedly Hit By Destructive Ransomware (July 26, 2018)
The US-branch of Chinese shipping company, COSCO, has released a statement saying that it experienced a “network breakdown” on July 24, 2018. Internal emails suggest that it was a ransomware infection, and the company is warning employees to not open any suspicious emails and conduct a comprehensive scan of the network. The US-branch is said to have had their email systems, WAN, and VPN gateways compromised in the infection. This has forced the US-branch to have its network connection suspended to avoid further infection while an investigation into the matter is underway.
Click here for Anomali recommendation
New Exploit Kit Delivers Bootkit and Cryptocurrency-mining Malware via Encrypted TCP Tunnel (July 26, 2018)
A new Exploit Kit (EK), dubbed "Underminer" or "Hidden Bee," has been discovered attempting to exploit a number of known vulnerabilities ("CVE-2015-5119" and "CVE-2018-4878" in Flash player, and "CVE-2016-0189" in Internet Explorer) for the purpose of deploying a bootkit and cryptocurrency miner. A variant of the EK was first detected in late 2017 after infecting some 500,000 machines, that are mainly located in Asia. Unsuspecting users are enticed with malvertisements to websites that attempt to exploit the vulnerabilities on a client’s system. RSA encryption is used to encrypt payloads while the RC4 or Rabbit stream ciphers are used to encrypt traffic between the infected host and C2 server. Use of asymmetric encryption, (also used by Angler, Nuclear and Astrum EKs) impedes the ability of researchers to track online activity and reverse engineer the payloads.
Click here for Anomali recommendation
Fake banking apps on Google Play leak stolen credit card data (July 26, 2018)
A set of fake banking applications has made its way onto the official “Google Play” store according to ESET researchers. The applications claimed to increase the credit card limit for users of three different Indian banks. The applications phish for credit card information and banking credentials using bogus forms. The phished information is sent to the attackers server. The listing on the attackers server was open to anyone with the link, amplifying the potential damage for victims as the sensitive information is available to anyone who happens to come across it.
Click here for Anomali recommendation
OilRig Targets Technology Service Provider and Government Agency with QUADAGENT (July 25, 2018)
Palo Alto Networks researchers have observed the “OilRig” APT group targeting a technology services provider and a government entity in the Middle East. The attacks used compromised email accounts to send spear phishing emails with an attachment that delivered a PowerShell based backdoor named “QUADAGENT.” The compromised email accounts belonged to an unnamed government agency based in the Middle East. The QUADAGENT backdoor will communicate with its command and control server via DNS tunneling, from which it receives additional PowerShell scripts to run. The PowerShell script is obfuscated with the open source tool named “Invoke-Obfuscation.”
Click here for Anomali recommendation
Leafminer: New Espionage Campaigns Targeting Middle Eastern Regions (July 25, 2018)
Symantec researchers have discovered a new threat actor group, dubbed “Leafminer,” that has been targeting various organizations in the Middle East since late 2017. Their primary targets have been financial, governmental, petrochemical, shipping, among others, based in Afghanistan, Bahrain, Egypt, Israel, Kuwait, Lebanon, Qatar, Saudi Arabia, and the United Arab Emirates. The threat group utilizes watering hole attacks on compromised web servers, pre-existing vulnerabilities in operating systems, and brute force attacks on logins with weak passwords. This threat group is extremely active and is suspected to be located in Iran based on the Iranian Farsi used in the list of intended targets discovered by researchers. The new Advanced Persistent Threat (APT) group is believed to be less experienced because they are capitalizing off more advanced groups’ Tactics, Techniques, and Procedures (TTPs) that are in the public domain and have poor operational security which led to their target list being leaked.
Click here for Anomali recommendation
Hackers Hiding Web Shell Logins in Fake HTTP Error Pages (July 24, 2018)
Threat actors have increased their usage of fake HTTP error documents to hide login forms for their web shells recently, according to security researcher, ‘nullcookies’. This type of attack is not new, but the frequency of the attack vector has substantially increased. This is an easy technique threat actors can use to upload malware, phishing script, or other software on a target’s system because potential targets cannot easily tell the error message is a fake.
Click here for Anomali recommendation
Kronos Reborn (July 24, 2018)
Researchers from Proofpoint have discovered a new version of the “Kronos” banking trojan in the wild. The banking trojan was observed being delivered via an multiple campaigns users, from Germany, Japan, and Poland, with malicious macro enabled Microsoft Word documents, RIG exploit kit. When macros are enabled in the malicious documents, it would download the new variant of Kronos and execute it. In some cases it used “Smoke Loader” as an intermediate. The major difference with the new version is that Kronos now uses Tor communications for command and control.
Click here for Anomali recommendation
Hide ‘N Seek Botnet Targets Smart Homes (July 24, 2018)
Security firm, Fortinet, has reported that the Hide ‘N Seek botnet has begun targeting vulnerabilities in IoT home devices. The malware, as of the publication of this article, has a configuration made up of 110 entries and 9 exploits, including an exploit for a HomeMatic Zentrale CCU2 remote execution code. The botnet has been known to infect home routers, IP cameras, AVTECH webcams, Cisco Linksys routers, and other devices. As of May 2018, it has infected over 90,000 unique IoT devices. Security researchers anticipate that there will be more functionalities added to the botnet including more publicly available exploits.
Click here for Anomali recommendation
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
APT34
The Advanced Persistent Threat (APT) group “APT34” is believed to be an Iranian-based group that has been active since at least 2014. APT34 conducts cyber espionage operations focused on reconnaissance that benefits Iranian nation-state interests. The group works on behalf of the Iranian government. APT34 use a mix of public and non-public tools. There is a possibility that APT34 may be related to the Iranian “Chafer” threat group outlined by Symantec in 2015 due to a shared server.
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



