Weekly Threat Briefing: WannaCry Hero Arrested, One of Two Charged with Distribution of Kronos Malware
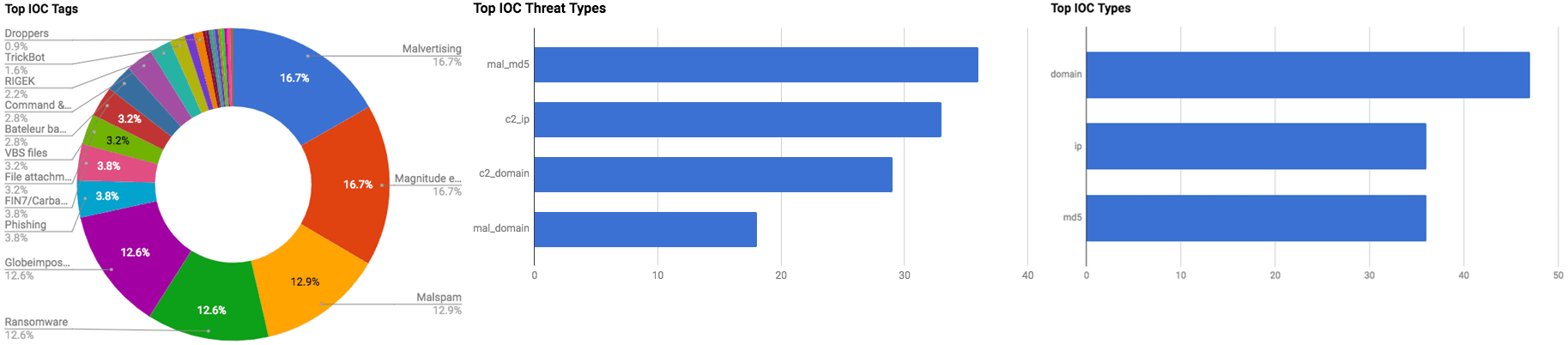

The intelligence in this week’s iteration discuss the following threats: APT, Data Breach, Exploit Kits, Malspam, Mobile, Phishing, Ransomware, and Spyware. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
Campaign Leads to RIG EK and Fake Flash Player Update Site. RIG Drops URLZone and Fake Flash Player Update Drops a Miner (August 7, 2017)
Researchers have discovered that the RIG Exploit Kit (EK) campaign is redirecting users to malicious locations that drop the "URLZone" banking trojan. Other instances in this campaign present users with fake Adobe Flash Player updates when video streaming websites are visited in attempts to trick the user that the update is needed to properly view the video. The malware downloaded via the fake Flash update was identified to be "XMRig CoinMiner." The malware is being distributed via redirection attacks that lead to the RIGEK.
Recommendation: Exploit kits, in general, are a common threat because they are often easily available to threat kits for purchase on underground forums. The kits, put together by skilled actors, are then sold to criminal groups as easily deployable exploitation frameworks. Users should be educated on how to browse the web as safely as possible, and to report any suspicious symptoms observed on their devices to IT/secops immediately. Additionally, web browsers should be kept up-to-date and any suspicious activity should be reported to the appropriate personnel.
Tags: RIGEK, Adobe Flash Player
Smoke Loader Adds Additional Obfuscation Methods to Mitigate Analysis (August 4, 2017)
According to PhishLabs, the malware downloading module, "Smoke Loader" (Dofoil), has received some updates by its creators. The malware has been upgraded to include new and more complex anti-analysis features such as checking the infected host for indicators related to malware analysis techniques. Smoke Loader has been offered for sale on underground forums since at least 2011, and it is known primarily for dropping the RIG exploit kit on infected machines to download additional malware.
Recommendation: Exploit kits have become one of the most common types of crimeware currently available to the less than sophisticated threat actor. The kits, put together by skilled actors, are then sold to criminal groups as easily deployable exploitation frameworks. The best protection from exploit kits is through employee education in combination with keeping web browsing software (including extensions such as flash and java) up to date at all times, as well as operating system software. Users should be educated on how to browse the web as safely as possible, and to report any suspicious symptoms observed on their devices to IT/secops immediately. In the case of a compromise by Rig, the infected system must be wiped and reformatted.
Tags: Smoke Loader, Malware
Cerber Ransomware Evolves Again, Now Steals From Bitcoin Wallets (August 3, 2017)
The threat actors behind the "Cerber" ransomware have once again updated their malware, according to Trend Micro researchers. In this iteration, Cerber has been updated to include the functionality of targeting Bitcoin, Electrum, and MultiBit wallets and stealing their contents. Additionally, this Cerber variant is also capable of stealing saved passwords in multiple web browsers including Internet Explorer, Google Chrome, and Mozilla Firefox. The malware is being distributed via an email with no content and a zip file attachment that will infect the recipient if opened.
Recommendation: All employees should be educated on the risks of malspam, and how to identify such attempts. Poor grammar and urgent content are often indicators of these type of attacks. Additionally, messages that request a recipient to open a file attachment should also be avoided.
Tags: Cerber, Ransomware
WannaCry Hero Arrested, One of Two Charged with Distribution of Kronos Malware (August 3, 2017)
The researcher who was praised for preventing further distribution of the "WannaCry" ransomware, was arrested by authorities in Las Vegas, Nevada, U.S. At the time of this writing, Marcus Hutchins has been indicted for creating the "Kronos" banking malware, and another unnamed individual indicted for offering it for purchase on various underground markets. Kronos is often distributed by exploit kits, and functions by using web-injections that imitate a legitimate website to steal user credentials.
Recommendation: Exploit kits have become one of the most common types of crimeware currently available to the less than sophisticated threat actor. The kits, put together by skilled actors, are then sold to criminal groups as easily deployable exploitation frameworks. The best protection from exploit kits is through employee education in combination with keeping web browsing software (including extensions such as flash and java) up to date at all times, as well as operating system software. Users should be educated on how to browse the web as safely as possible, and to report any suspicious symptoms observed on their devices to IT/secops immediately. In the case of a compromise, the infected system must be wiped and reformatted.
Tags: WannaCry, Researcher, Cybercrime
Ukrainian Firm Facing Legal Action for Damages Caused by NotPetya Ransomware (August 3, 2017)
A Ukrainian law firm, Justcutum Attorneys Association, is attempting to gather support from victims of the global NotPetya ransomware campaign for a collection lawsuit. As of this writing, the suit would be filed against the company responsible for MEDoc's accounting software, "Intellect-Service LLC." Researchers' subsequent investigation of the event revealed that Intellect-Service had not updated their servers since at least 2013. Additionally, Ukrainian authorities have stated that they have not arrested any of the company's staff, but charges may be filed in the future.
Recommendation: It is crucial that your company ensure that servers are always running the most current software version. In addition, your company should have policies in place in regards to the proper configurations needed for your servers in order to conduct your business needs safely. Furthermore, always practice Defense in Depth (don't rely on single security mechanisms - security measures should be layered, redundant, and failsafe). In the case of ransomware infection, the affected systems should be wiped and reformatted, even if the ransom is paid. Other machines on the same network should be scanned for other potential infections.
Tags: NotPetya, Ransomware, Legal action
Chrome Web Dev Plugin with 1m+ Users Hijacked, Crams Ads Into Browsers (August 2, 2017)
Chris Pederick, the developer of the "Web Developer" extension for Chrome, has discovered that his Google account has been the victim of a phishing attack by an unknown actor(s). Pederick is warning users of his tool to update to version 0.5 or later as soon as possible. The actor pushed an update, as version 0.4.9, to Web Developer's approximate 1,044,000 users that displays advertisements. The threat actor's version fetches JavaScript code from the web and forcibly displays advertisements and possibly other malicious functions.
Recommendation: Users who installed version 0.4.9 of Web Developer should update to version 0.5 or later as soon as possible, or uninstall the extension and install a fresh copy. Additionally, it may also be wise to change passwords used in your Chrome browser while the infected extension was in use.
Tags: Chrome extension, Breach
Enemy at the Gates: Reviewing the Magnitude Exploit Kit Redirection Chain (August 2, 2017)
Malwarebytes researchers have released information detailing the "Magnitude" exploit kit's redirection attacks over the past several months. Currently, Magnitude is being distributed via malvertising campaigns that drop the "Cerber" ransomware on targets primarily located in South Korea. The actors behind Magnitude are abusing the Real-time Bidding (RTB) process, used by advertising companies to auction on which advertisements will be displayed on a website, to display malicious advertisements. If the malvertisement is followed, users are screened at a gate that chooses on whether or not the user should proceed to the exploit kit. The gate, dubbed "Magnigate," performs additional checks on the user's information such as browser information, Internet Service Provider (ISP), IP address, geolocation, operating system, and user agent.
Recommendation: Users should be cautious when clicking on advertisements because as this story portrays, malicious advertisements can sometimes appear on legitimate online locations. However, clicking on such advertisements is not always required. If the advertised product is appealing, it would be safer to search for the product on the authentic websites of the company who is selling the product, or other trusted online shopping locations.
Tags: Exploit kit, Magnitude
Amazon Halts Sale of Android Blu Phone Amid Spyware Concerns (August 1, 2017)
Last week during a talk at the Black Hat security conference, Kryptowire researchers discussed how the "Blu" Android smartphone gathered Personally Identifiable Information (PII) on its users. Amazon responded by stating that Blu phones will be "unavailable for purchase on Amazon.com" and will remain so "until the issue is resolved." However, at the time of this writing, the phones are still available for purchase on Amazon.com. The issue resides in Blu's firmware utility, "Adups," that is created by "Shanghai Adups Technology." Kryptowire researchers discussed how Adups was collecting various data such as call history (accompanied with full phone numbers), International Mobile Equipment Identity (IMEI), Media Access Control address, and serial number. The collected data is then sent back to Shanghai Adups Technology's servers.
Recommendation: The threat of preinstalled threats has the possibility of hiding from even the most cautious of users; if the devices listed here are being used by your company, or for personal use, they should be properly wiped and restored. However, sometimes the operating system may have code that will reinfect the device. Additionally, it is important that mobile devices connecting to corporate and personal networks have trusted antivirus software installed that it always kept up-to-date.
Tags: Spyware, Blu, Mobile
TrickBot Comes with New Tricks – Attacking Outlook and Browsing Data (August 1, 2017)
The TrickBot Trojan has been updated recently with two new modules,. The first module "module.dll" is a large module written in C++. This module focuses on stealing data. It attempts to get the victim's website cookies, HTML5 local storage, browser history and grabs URL hits from a cache. Module.dll sets up a hidden desktop in order to have a workspace, to fingerprint browsers, that is not noticeable by the victim. The module contains a hardcoded HTML file with inline JavaScript that gets information on the browser's configuration. The module also has the ability to steal from locally stored databases by incorporating SQLite. The second module "outlook.dll" is written in Delphi. It attempts to steal Microsoft Outlook related data from registry keys.
Recommendation: Users should be cautious when clicking on advertisements, malicious advertisements can sometimes appear on legitimate online locations. Always keep your browser and operating system up to date, including any browser add-ons you may need (Flash, Java). Employ network as well as host based detection and prevention systems where possible.
Tags: Trickbot, Malware
Fin7/Carbanak Threat Actor Unleashes Bateleur JScript Backdoor (July 31, 2017)
The financially motivated Advanced Persistent Threat (APT) group, "FIN7," has been identified to have added a new JScript backdoor to their arsenal, according to Proofpoint researchers. The backdoor is called, "Bateleur," and comes with updated malicious macros that are being used to target U.S.-based restaurants. The malware is being distributed via phishing emails that claim that the attachment is a check that was discussed previously. The emails are being sent from Outlook and Gmail accounts that both claim that the attached document has been encrypted and requires content to be enabled in order to properly view the document.
Recommendation: Defense in depth (layering of security mechanisms, redundancy, fail safe defense processes) is the best way to ensure safety from APTs, including a focus on both network and host based security. Prevention and detection capabilities should also be in place. Furthermore, all employees should be educated on the risks of phishing, how to identify such attempts.
Tags: FIN7/Carbanak, Bateleur backdoor, Phishing
HBO Hacked: Upcoming Episodes, Game of Thrones Data Leaked Online (July 31, 2017)
The American premium cable and satellite television network, HBO, has confirmed that it was breached by an unknown threat actor. The actor stole upcoming episodes for multiple shows including Ballers, Game of Thrones, and Room 104, that were then posted on a torrent website. Overall, the actor stole approximately 1.5 terabytes of data. The breach also included theft of HBO employee login credentials. Additionally, the actor(s) also stated that more episodes would be "coming soon."
Recommendation: Defense in depth (layering of security mechanisms, redundancy, fail safe defense processes) is the best way to ensure safety from threat actors, including a focus on both network and host based security. Prevention and detection capabilities should also be in place. Additionally, password should not be stored in unencrypted documents and the user of password managers can assist in protecting login credentials.
Tags: Data breach, HBO
A New Era in Mobile Banking Trojans (July 31, 2017)
Researchers from Kaspersky have found a new version of the mobile banking malware family Svpeng. The modifications include new keylogger functionality that records keystrokes made through Android accessibility services which also allows it to grant more permissions and prevent uninstallation attempts. If it is granted permission to use the accessibility services, it can gain access to the UI of other applications and obtain data. It takes screenshots every time the victims presses the button on the keyboard and uploads it to a Command and Control (C2) server. If an application such as a banking app does not allow screenshots to be taken, a phishing window is drawn over the top of the application. The application does not affect the device if the victim's language is in Russian, suggesting that Russian actors are behind the Trojan.
Recommendation: This Trojan is spread from malicious websites pretending to be a flash player. This Trojan even affects fully patched devices. Always use the Google Play Store to obtain your software, and avoid downloading applications, even if they appear legitimate, from third-party stores. In addition, it is important to review the permission the application will request and comments from others who have downloaded the application.
Tags: Trojan, Android, Svpeng, Accessibilty Services
Malspam Pushing Globeimposter Ransomware (July 31, 2017)
Researchers have identified a malspam campaign that is distributing "Globeimposter" ransomware. The spam emails claim that the attached zip file is a payment receipt. If the zip file is opened, a malicious VBS script will launch a process that infects the user with ransomware. Researchers note that the malware does not present the infected user with decryption instructions, and they believe it is because the threat actors behind the campaign made mistakes in the malicious code.
Recommendation: Always be on high alert while reading email, in particular when it has attachments, attempts to redirect to a URL, comes with an urgent label, or uses poor grammar. Use anti-spam and antivirus protection, and avoid opening email from untrusted or unverified senders.
Tags: Malspam, Ransomware, Globeimposter
Hackers Compromise Accounts of FireEye Threat Intelligence Analyst (July 31, 2017)
An unknown actor, claiming to be called the "37337 hacker," compromised several social media accounts belonging to a Senior Threat Analyst at FireEye, according to a statement made by the company. The actor stole limited information including a small Microsoft Outlook contact list, emails, and whitepaper documents written by Cylance researchers. The threat actor(s) claim that this breach was part of "Operation #LeakTheAnalyst." According to the actor(s), the objective of this campaign is to track analysts online and tarnish their reputation. Additionally, FireEye has stated that it does not appear their network was compromised.
Recommendation: It is important that your company and employees use different passwords for the different accounts that are being used. As this story portrays, previous breaches can allow actors to gain access to other accounts because users frequently use the same username and password combinations for multiple accounts. Furthermore, policies should be in place that require your employees to change their passwords on a frequent basis.
Tags: Threat actor, Breach
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
RIG exploit kit Tool Tip
The RIG exploit kit is a framework used to exploit client side vulnerabilities in web browsers. The RIG exploit kit takes advantage of vulnerabilities in Internet Explorer, Adobe flash, Java and Microsoft Silverlight. The RIG exploit kit was first observed in early 2014. The RIG exploit kit's objective is to upload malicious code to the target system. The RIG exploit kit is known to distribute ransomware, spambots and backdoors. Victims are redirected to the RIG exploit kit with a landing page coming from malvertising or compromised sites.
Tags: RIG, exploitkit
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



