Weekly Threat Briefing: Weak Passwords Let a Hacker Access Internal Sprint Staff Portal

The intelligence in this week’s iteration discuss the following threats: APT, Backdoor, Cyberespionage, Data breach, Data leak, Ransomware, Spearphishing, Targeted attacks, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Weak Passwords Let a Hacker Access Internal Sprint Staff Portal (August 26, 2018)
The American telecommunications company, Sprint, has been found to have a security issue with their staff login page. An unnamed security researcher identified that by using two sets of data that contained “easy-to-guess usernames and passwords,” he was able to gain access to Sprint’s staff portal. This allowed the researcher to navigate to other pages on the portal that contained customer data because the portal did not use two-factor authentication. The first set of credential data used granted access to a prepaid Sprint employee portal as well as Sprint subsidiaries Boost Mobile and Virgin Mobile. The second data set was used to gain access to parts of the website where customer information was stored. Access to this portal could allow an actor to not only access to Personally Identifiable Information, but also the ability to change plans and add-ons, replenish an account, and swap devices, among others. Moreover, the researcher discovered that anyone could attempt to login to the internal customer portal with the only perquisite being the targeted Sprint account phone number. The second piece of data needed to login is the customer account PIN that the researcher found could be attempted unlimited times, which opens the login to unlimited brute-force attack attempts.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Brute Force (T1110)
Back To School: COBALT DICKENS Targets Universities (August 24, 2018)
Iranian Advanced Persistent Threat (APT) group, COBALT DICKENS, has been discovered to be targeting university login pages for 76 universities in at least 14 Western countries such as Australia, Canada, China, Israel, Japan, Switzerland, Turkey, the UK, and the US. The goal is to obtain unauthorised access to credentials to then gain access to resources. The campaign utilised a fake login page where once they had entered in their credentials, they were taken to the legitimate website where they were logged into a valid session. Most of the fake domains resolved to the same IP address and Domain Name System (DNS) server. This is similar to older campaigns conducted by COBALT DICKENS where they attempted to obtain credentials through phishing to steal intellectual property from specific targets such as libraries.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Input Capture (T1056) | [MITRE ATT&CK] Valid Accounts (T1078)
Millions of Texas Voter Records Exposed Online (August 24, 2018)
A New Zealand-based data breach hunter, known by alias “Flash Gordon,” discovered a single file on an unsecured server that contained 14.8 million records associated to registered voters in the state of Texas. Other researchers analyzed the data and believe that the data was likely compiled by a “Republican-focused” data analytics firm called Data Trust. The publicly accessible data consists dozens of fields some of which include address, gender, name, and multiple years of voting history. Researchers note that much of the leaked data was already publicly accessible and other fields can be purchased, but the voting history and social security numbers are private.
Click here for Anomali recommendation
T-Mobile Hacked — 2 Million Customers' Personal Data Stolen (August 23, 2018)
Mobile telecommunications provider, T-Mobile, announced that they had suffered a security breach on August 20th. This allowed for customer data such as names, billing zip codes, phone numbers, email addresses, account numbers, and account types to be accessible by unauthorised users. Approximately two million T-Mobile customers are likely impacted by this breach. It is believed that threat actors used an API key to access the servers. Fortunately, no financial information was thought to be leaked according to the company. The API key that was used has since been shut down.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Credential Dumping (T1003) | [MITRE ATT&CK] Hooking (T1179)
Unencrypted Laptop Exposes Personal Details Of 37,000 Eir Customers, Faulty Security Update Blamed (August 23, 2018)
Irish Telecommunications operator, Eir, unintentionally exposed the details of at least 37,000 customers after an employee’s unencrypted laptop was stolen outside one of their offices. The company blamed a faulty security update as the reason behind the laptop being unencrypted despite containing thousand’s of customers’ data. Eir said that the security update rendered the laptop unencrypted though it is unclear how that occurred. The company believes that the laptop will most likely be wiped and resold for a profit by the unknown thief rather than for the purpose of stealing customer data.
Click here for Anomali recommendation
Black Hat USA Attendees Details Exposed Online Due To Leaky API (August 23, 2018)
An independent security researcher who attended Black Hat USA 2018, a cybersecurity conference held in Las Vegas, discovered a leaky API key that allowed access to data associated to all Black Hat attendees. The leak originated from the NFC name tags that all attendees wore that had a scannable code for marketing reasons. The data contained names, email addresses, company names, job titles, and contact numbers. The security researcher downloaded a tag reader on his mobile phone and decompiled the application. Here, he discovered an API endpoint in the code which he could exploit and pull data from. He notified the ITN team from Black Hat and they patched the API key issue.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Credential Dumping (T1003) | [MITRE ATT&CK] Brute Force (T1110)
Operation AppleJeus: Lazarus Hits Cryptocurrency Exchange With Fake Installer And MacOS Malware (August 23, 2018)
The North Korean Advanced Persistent Threat (APT) group, Lazarus Group, has begun to target cryptocurrency exchanges and financial technology companies in a newly identified campaign. They have also developed malware that targets macOS and is in the processes of developing malware for Linux. This specific campaign uses a legitimate-looking cryptocurrency trading application by fake company, Celas Limited, that is trojanized from initial installation on both WindowsOS and macOS. After the initial installation, the user is sent an application update via email, which is actually contains malware to drop a Fallchill backdoor on the machine. This backdoor allows Lazarus to then have complete control over the infected machine and its network.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Third-party Software (T1072) | [MITRE ATT&CK] Execution through API (T1106) | [MITRE ATT&CK] Custom Command and Control Protocol (T1094)
Darden Reports Possible Data Breach At Cheddar's Scratch Kitchen (August 22, 2018)
Darden Restaurants Inc., the company that owns a variety of chain restaurants, such as The Olive Garden, announced that guest data from Cheddar’s Scratch Kitchen restaurants in 23 different US states was compromised. The breach happened on a legacy network system of the chain, which has now been disabled and replaced to a new and more secure network. Approximately 567,000 payment card numbers were most likely exposed in the incident that were used between November 3, 2017 and January 2, 2018 at the chain. Darden has employed a third-party cyber forensics firm to investigate the incident.
Click here for Anomali recommendation
Turla: In And Out Of Its Unique Outlook Backdoor (August 22, 2018)
The Advanced Persistent Threat (APT) group, Turla (also known as Snake or Uroburos), has been utilising a distinct backdoor to steal sensitive communications from officials of at least three European countries: Germany and two unnamed post-Soviet Union countries, as well as defence contractors. The APT group was discovered by German officials to have installed a backdoor on several computers to first compromise the German Federal College of Public Administration and then the German Foreign Office in March 2017. The backdoor is particularly interesting as it does not exploit vulnerabilities in PDF readers or Microsoft Outlook, but rather it subverts Microsoft Outlook’s Messaging Application Programming Interface (MAPI) to gain access to targets’ mailboxes. This backdoor does not use a Command and Control (C2) server but operates through the emails. Specifically, through crafted PDF attachments that carry out specific commands. The backdoor is a Dynamic Link Library (DLL) module that is installed using legitimate Windows commands, which ensures the backdoor is activated anytime Outlook is launched. Even if email addresses from the APT group are blocked, the backdoor can be updated to receive commands from any new email address so long as it contains a PDF with commands.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] AppInit DLLs (T1103) | [MITRE ATT&CK] Component Object Model Hijacking (T1122)
Hacker Holds The Data Of 20,000 Superdrug Customers To Ransom (August 22, 2018)
The UK health and beauty retailer, Superdrug announced that it suffered a data breach which resulted in over 20,000 customers’ details including names, addresses, dates of birth, phone numbers, and point balances being compromised. An unknown threat actor contacted the retailer and claimed to have stolen the data and attempted to ransom the credentials for payment unsuccessfully. So far, Superdrug has verified that 386 accounts were compromised. The company stated that there was no evidence to suggest the company’s internal systems were compromised, but rather it is most likely that repeat customer credentials used on other websites were then used to compromise Superdrug accounts. It is believed that no financial data was obtained in the breach.
Click here for Anomali recommendation
Critical Flaws In Ghostscript Could Leave Many Systems At Risk Of Hacking (August 21, 2018)
A security researcher from Google Project Zero discovered a remote code execution (RCE) vulnerability in Ghostscript, an open-source interpreter for Adobe Systems' PostScript and PDF page description languages. This script has multiple -dSAFER sandbox bypass vulnerabilities that could allow for remote, unauthorised users to execute arbitrary commands into the system. A threat actor only has to send a malicious attachment containing a PDF, PS, EPS, or XPS file that leverages the Ghostscript, if opened, and allows the actor into the system. This is not the first time Ghostscript has had security issues, as in 2016 and April 2017 the same security researcher discovered similar, “high severity” vulnerabilities that were also seen in the wild. At the time of the writing of the article, a patch had yet to be released.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Exploitation of Remote Services (T1210)
Microsoft Disrupts APT28 Hacking Campaign Aimed At US Midterm Elections (August 21, 2018)
Mircosoft has shut down over 84 domains that were created by Russian Advanced Persistent Threat (APT) APT28 (also known as Fancy Bear) to influence the US midterm elections. The domains uncovered by Microsoft were to be utilised for a spear-phishing operation and were related to elected officials, politicians, political parties/groups, and think tanks to most likely influence the midterm elections. These observations are similar to tactics that Russian threat actors engaged in the 2016 US presidential elections.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing via Service (T1194)
Ryuk Ransomware: A Targeted Campaign Break-Down (August 20, 2018)
A targeted ransomware campaign has been observed attacking organisations worldwide, according to Check Point researchers. The ransomware, called “Ryuk,” specifically targets certain victims (who) and only encrypts crucial assets and resources in each targeted company. The malware has been linked to Lazarus Group, which is attributed to the Democratic People’s Republic of Korea (DPRK), since this ransomware looks extremely similar to HERMES ransomware that Lazarus Group is notable for using. This attack utilises extensive network mapping, and credential collection prior to each target-specific campaign rather than using mass spam campaigns and exploits to gain access. The malware asks for a ransom ranging between 15 and 20 Bitcoin (one Bitcoin equals approximately $6,612 USD), though it ranges depending on the victim. This suggests there might be at least two different offensive levels. The Bitcoin wallet address is unique per attack, making it difficult to track the money’s route, the threat actor’s activities, and illicit profit. So far, researchers assume that the threat actors behind this campaign have earned at least $640,000 USD and will most likely gain more.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Process Injection (T1055) | [MITRE ATT&CK] Registry Run Keys / Start Folder (T1060)
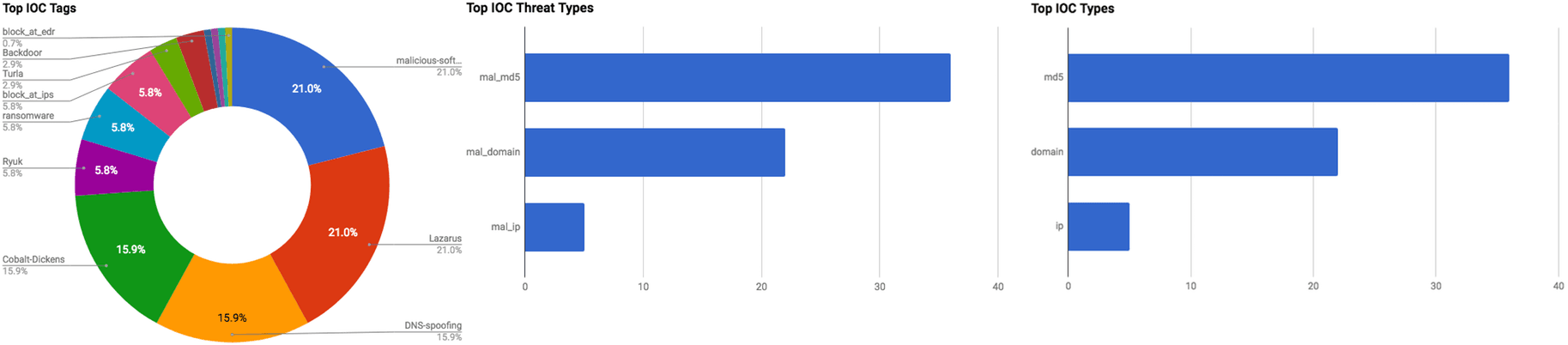
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial. Additional information regarding the threats discussed in this week’s Community Threat Briefing can be found below:
Turla The Advanced Persistent Threat (APT) group “Turla” is believed to be a Russian based group that has been active since at least 2007. Turla conducts cyber espionage against government entities around the world. The group is connected to the “Epic” cyber espionage campaign that targets government agencies around the globe, and is also connected to the Agent.btz worm that infected the network of the U.S. Department of Justice in 2008.
APT28 The Advanced Persistent Threat (APT) group “APT28” is believed to be a Russian-sponsored group that has been active since at least 2007. The group displays high levels of sophistication in the multiple campaigns that they have been attributed to, and various malware and tools used to conduct the operations align with the strategic interests of the Russian government. The group is believed to operate under the Main Intelligence Directorate (GRU), the foreign intelligence agency of the Russian armed forces.
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



