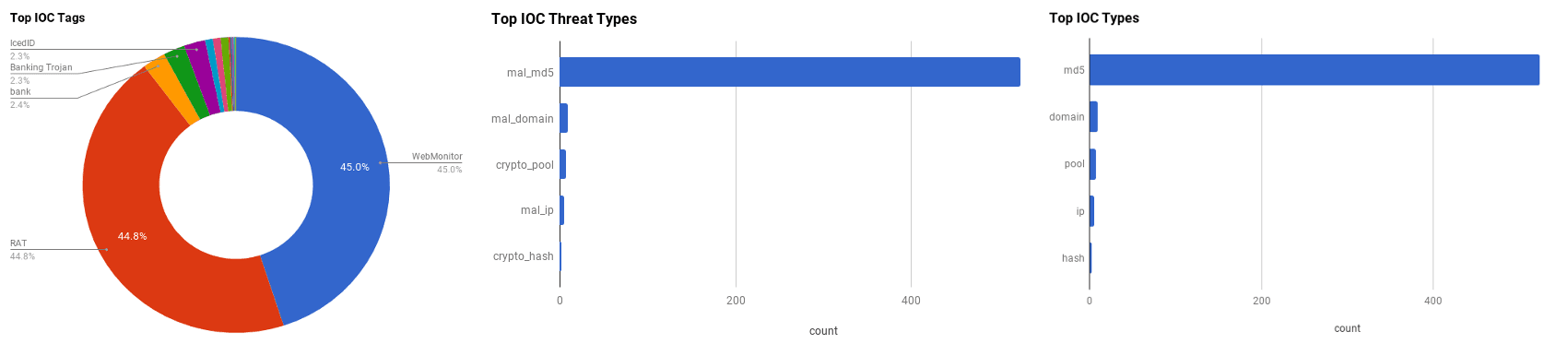

The intelligence in this week’s iteration discuss the following threats: Account Breaches, Cisco Smart Install, IcedID Banking Trojan, IIS Cryptojacking, Operation Parlament, Spear Phishing and WebMonitor RAT. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
Windows Servers Targeted for Cryptocurrency Mining via IIS Flaw (April 16, 2018)
An Internet Information Services (IIS) 6.0 vulnerability is being exploited by threat actors to mine the "Electroneum" cryptocurrency. The buffer overflow vulnerability, registered as "CVE-2017-7269," has also been exploited to mine the "Monero" cryptocurrency and install malware. The exploit being used in this campaign is the same as the originally published proof of concept, but with the shellcode swapped out to execute the new commands. Two commands are executed. The first command is used to stop the "Internet Connection Firewall," to ensure outgoing communication is not blocked. The second uses a technique called "Squiblydoo" to bypass software whitelisting protection by executing commands from a legitimate binary that downloads the attacker's scripts and executes them. Persistence is maintained via a service, which is executed on startup.
Click here for Anomali recommendation
Vulnerability Spotlight: Multiple Vulnerabilities in Moxa EDR-810 Industrial Secure Router (April 13, 2018)
A number of serious vulnerabilities in the "Moxa EDR-810" industrial secure router have been revealed by the Cisco Talos team. The vulnerabilities range from command injection, denial of service, and cleartext password transmission. Moxa has released an updated version of the router firmware to address these vulnerabilities.
Click here for Anomali recommendation
Say "Cheese": WebMonitor RAT Comes with C2-as-a-Service (C2aaS) (April 13, 2018)
The creator of the malware "Webmonitor RAT" has added new features to their malware, according to Palo Alto researchers. The new feature offers a "Command and Control (C2) as a Service" (C2aaS) to its customers, meaning that there is no need for the customer to set up their own C2 server. The tool claims to be a legitimate remote administration utility, but contains many malicious features, and also has a high detection rate from anti-virus vendors. There have been thousands of observed WebMonitor infection attempts on targets.
Click here for Anomali recommendation
Operation Parliament, Who Is Doing What? (April 12, 2018)
Kaspersky Labs researchers have been tracking a series of attacks, mostly targeting the Middle East and North Africa, carried out by an unknown threat actor. The targets include many high profile entities such as election commissions, intelligence agencies, military, ministries, parliaments, and state officials. The attacks are conducted via spear phishing that attempts to drop a remote shell for the attackers. The malware has taken great care to verify that it is on a target machine before finishing infection, protecting their Command and Control (C2) infrastructure. The group deploys a number of false flags to confuse attribution.
Click here for Anomali recommendation
Great Western Railway Warns of Great Western Password Reuse: Brits Told to Reset Logins (April 11, 2018)
The Great Western Rail (GWR) in the United Kingdom is urging customers to change their passwords after observing a successful attack that broke into approximately 1,000 accounts. The attack leveraged credentials that had been leaked on the web from other accounts; these leaked credentials were then used to test as a login for GWR. This resulted in the compromise of accounts for users with poor password practices. GWR has reset all customers passwords as a precaution.
Click here for Anomali recommendation
Microsoft Fixes 66 Bugs In April Patch Tuesday Release (April 10, 2018)
This month's Microsoft "Patch Tuesday" addresses 66 bugs, of which 26 are rated critical. Patches were made for products including Internet Explorer, Microsoft Edge, Microsoft Office, Adobe Flash, Visual Studio, and ChakraCore.
Click here for Anomali recommendation
IcedID Banking Trojan Teams up with Rovnix for Distribution (April 10, 2018)
There has been an increase in the number of infections by the "IcedID" banking trojan, according to Cisco Talos researchers. Originally IcedID was distributed by the "Emotet" trojan, but more recently it is being distributed via the "Rovnix" trojan, which itself is being distributed via emails with attached documents with malicious macros. Talos researchers note that the spear phishing emails are extremely targeted. Examples include an email sent to an employee of a city in the U.S. state of Arkansas that referenced a meeting relevant to city business. Another email sent to an electrical company in North Carolina included the name of a local engineering company. IcedID contains a minimalist code injection technique to inject code, without the need to start the target process in a suspended state, into "svchost.exe".
Click here for Anomali recommendation
FakeUpdates' campaign leverages multiple website platforms (April 10, 2018)
Malwarebytes researchers have observed a malware campaign delivering fake updates that infect victims computers with various malware. The campaign distributes malicious JavaScript files via compromised websites. The compromised websites are exploited via outdated Content Management Systems (CMSs) that are vulnerable to malicious code injection. When a user visits one of the compromised sites, an injected JavaScript file loads a new template over the page claiming they are using an old version of Adobe Flash Chrome, or Firefox and starts the download of a fake update, disguised as a JavaScript file. This file is heavily obfuscated and contains multiple methods at sandbox and virtual machine detection. It will use WScript.Network and Windows Management Instrumentation (WMI) to collect system information before deciding to deliver the final payload. The final payload is a malicious binary dropped in the %temp% folder. which is Researchers have observed both the "Chtonic" banking malware and "NetSupport Remote Access Tool" being dropped.
Click here for Anomali recommendation
Death in paradise: 'Cyber attack' takes out national government's IT (April 10, 2018)
The network of the Government of Sint Maarten has been put offline for a week due to a "cyber attack". The exact nature of the attack is unknown but many of the government offices are closed, including the civil registry. A recovery process is undergoing.
Click here for Anomali recommendation
Action Required to Secure the Cisco IOS and IOS XE Smart Install Feature (April 9, 2018)
Cisco has released a security advisory detailing vulnerabilities relating to the Smart Install feature and two vulnerabilities relating to the March 2018 release of the Cisco IOS and IOS XE Software. The "Cisco Smart Install Protocol" advisory details the potential misuse that allows a remote actor to change the startup-config file and force a reload of the device, load a new IOS image on the device, and execute high-privilege CLI commands on switches running Cisco IOS and IOS XE Software. The other advisories detail the two vulnerabilities, in Cisco IOS and IOS XE Software, registered as "CVE-2018-0171" and "CVE-2018-0156".
Click here for Anomali recommendation
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



