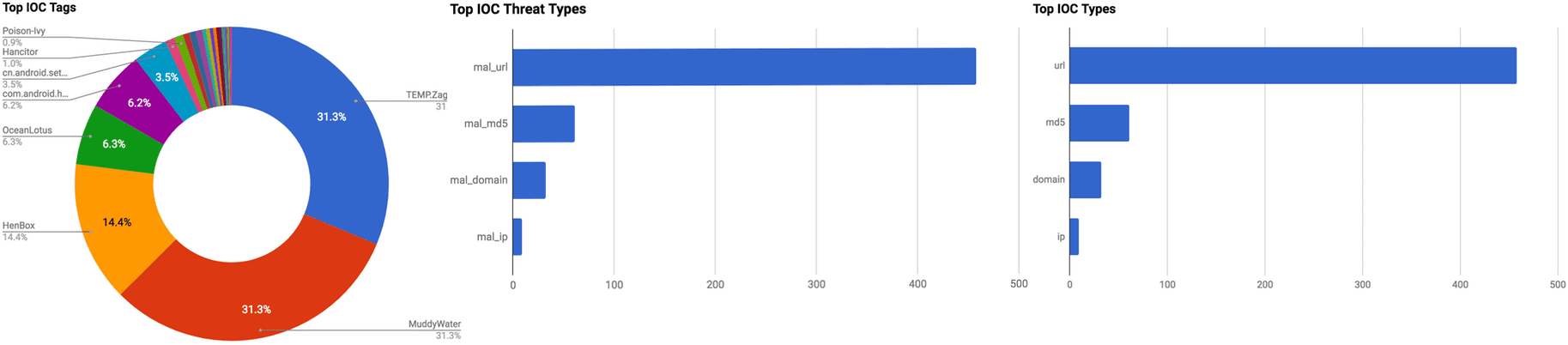

The intelligence in this week’s iteration discuss the following threats: APT28, Bitcoin Theft, Hancitor, Hanwha Camera Vulnerabilities, MuddyWater, OceanLotus, Samba Vulnerability and Sigma Ransomware. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
Malspam Delivers Pony and Loki-Bot (March 19, 2018)
Researchers have discovered a malspam campaign that is distributing the "Pony" downloader and the "Loki-Bot" banking trojan via malicious RTF documents. The emails purport that the attachment is a copy of a bank deposit. The documents exploit a Microsoft Office Memory Corruption vulnerability registered as "CVE-2017-11882" to fetch the Pony downloader. Pony is then used to download and install Loki-Bot, which is able to gain persistence on an affected machine by adding a registry key to the "%APPDATA%" folder.
Click here for Anomali recommendation
Zenis Ransomware Encrypts Your Data & Deletes Your Backups (March 16, 2018)
The security researcher known as "MalwareHunterTeam" has discovered a new ransomware family dubbed "Zenis." At the time of this writing, it is unknown how the threat actor(s) behind are distributing the ransomware, however, it may be possible that it is being delivered via compromised Remote Desktop services. Zenis, which has been observed to have infected multiple victims already, is not only capable of encrypting files with a custom encryption method but will also delete backups.
Click here for Anomali recommendation
Suspected Chinese Cyber Espionage Group (TEMP.Periscope) Targeting U.S. Engineering and Maritime Industries (March 16, 2018)
Activity of a suspected Chinese cyber espionage group has been unveiled by FireEye researchers. The group, dubbed "TEMP.Periscope" (Leviathan), has been active since at least 2013. Researchers have discovered that the group has been conducting a campaign against U.S. engineering and maritime entities involved in the South China Sea. The group has recently "re-emerged" with a revised toolkit. The initial vector the group uses is spear phishing emails with malicious documents levegering "CVE-2017-11882" to drop their malware.
Click here for Anomali recommendation
Sofacy Uses DealersChoice to Target European Government Agency (March 15, 2018)
On the 12th and 14th of March, Palo Alto researchers observed the Sofacy group (APT28) carrying out an attack on a European government agency using an updated version of the group's Adobe Flash exploitation framework called "DealersChoice." The updated DealersChoice will only run the Flash object when the target scrolls to the bottom of the three-page lure-document. Successful exploitation will lead to a secondary payload being downloaded.
Click here for Anomali recommendation
Hermes ransomware distributed to South Koreans via recent Flash zero-day (March 14, 2018)
The Korean Advanced Persistent Threat (APT) group "Group 123" was observed using an Adobe Flash zero-day exploit in the wild. The exploit, registered as "CVE-2018-4878," is now being used to distribute the "Hermes" ransomware to South Korean users. The exploits are being delivered via malicious Word documents that have the embedded Flash object.
Click here for Anomali recommendation
Dangerous malware stealing bitcoin hosted on Download.com for years (March 14, 2018)
ESET researchers, after searching on the website "download[.]com," have discovered trojanized applications that steal bitcoin. The applications contain a simple dropper that extracts both the legitimate installer of the purported application and the malware to the temp folder, and both are subsequently executed. The malware copies itself to a different location in the "appdata" folder and adds itself to a registry key to maintain persistence. The malware simply checks copied text in the user's clipboard by regexing for a bitcoin address and replacing it with the attacker's Bitcoin address.
Click here for Anomali recommendation
Samba settings SNAFU lets any user change admin passwords (March 14, 2018)
A new security advisory has been released in regards to a vulnerability, registered as "CVE-2018-1057," discovered in Samba 4 Active Directory Domain Controller (AD DC), in which the LDAP server incorrectly validates permissions to modify passwords allowing any authenticated user to change any other users passwords, including admins and domain controllers.
Click here for Anomali recommendation
Hancitor: fileless attack with a DLL copy trick (March 13, 2018)
The "Hancitor" downloader is being delivered using a new technique for a fileless attack, according to Malwarebytes Labs researchers. The technique is conducted by copying the "kernel32.dll" library and using it to create a new malicious process, bypassing Ring 3 hook protections. The delivery is accomplished via malspam that prompts the recipient to download a Word document that masquerades as an invoice. The document contains a macro that, if enabled, copies malicious code into memory and creates a timer to execute the payload. The payload copies kernel32.dll into the users' temp folder as "krnl32.dll," and then uses the original kernel32 "LoadLibraryW" call to load it into memory. krnl32.dll is then used to create a new suspended "svchost.exe" process. "Process hollowing" is used to and replace svchost.exe with the malware, which completes the infection with the running malware.
Click here for Anomali recommendation
Iranian Threat Group Updates Tactics, Techniques and Procedures in Spear Phishing Campaign (March 13, 2018)
The Iranian Advanced Persistent Threat (APT) group "TEMP.Zagros" has been observed updating their Tactics, Techniques, and Procedures (TTPs) in a new spear phishing campaign, according to FireEye researchers. The group has been targeting government and defense entities in Central and Southwest Asia. The new TTP results in using the recently disclosed method, leveraging INF and SCT files for PowerShell code execution; previously this tactic involved using VBS and INI files. The PowerShell script, identified as "POWERSTATS" by FireEye, is a backdoor that can perform activities such as remote code execution, drive wiping, taking screenshots, and exfiltrating data.
Click here for Anomali recommendation
HenBox: The Chickens Come Home to Roost (March 13, 2018)
A new Android malware family, dubbed "HenBox," has been discovered by Unit 42 researchers. The malware appears to primarily target Muslims living in the "Xinjiang Uygur Autonomous Region" in Northwest China. The malware is being delivered via trojanised versions of VPN and Android system APKs applications located on third-party application stores. HenBox steals information from multiple applications including chat, communication, social media apps.
Click here for Anomali recommendation
OceanLotus ships new backdoor using old tricks (March 13, 2018)
ESET researchers have discovered a new backdoor being used by the Advanced Persistent Threat (APT) group called "OceanLotus." OceanLotus is a Chinese APT that targets corporate and government targets, particularly in Southeast Asia. The researchers believe that the dropper for this new backdoor was delivered via a "watering hole" attack. The dropper drops the backdoor in a number of steps designed to hide the true backdoor. These steps include a decoy updater, obfuscation, and junk code. The backdoor, once decrypted, fingerprints the system and sends data to its command and control server before waiting for additional commands.
Click here for Anomali recommendation
Sigma Ransomware Being Distributed Using Fake Craigslist Malspam (March 12, 2018)
The Sigma ransomware is being distributed via Craiglist-themed malspam in a new campaign; Craigslist is an American advertising and e-commerce website. The malicious emails pretend to be replies to postings for short term jobs called "Gigs" that claim to have contact information in the attached Word or Rich Text File document. The documents contain malicious macros that, when enabled, download and executes the "Sigma" ransomware. The ransomware initially demands $400 USD worth of Bitcoin for decryption, which then increases to $800 after 7 days.
Click here for Anomali recommendation
Somebody's watching! When cameras are more than just 'smart' (March 12, 2018)
Multiple vulnerabilities were found in a popular brand of smart camera, according to Kaspersky Lab ICS CERT researchers. The "Hanwha SmartCam" is a camera that captures video, has a motion sensor, night vision, and communicates with a cloud based service. The vulnerabilities found include: use of HTTP for firmware updates, feature of remote execution of commands with root privileges, authentication bypass, and restoration of camera password for the cloud account. The implications can lead to situations such as an actor taking control of any camera connected to the cloud and watch what is happening or using the camera for cryptocurrency mining.
Click here for Anomali recommendation
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



