Threat Intelligence Sharing
Who’s Sharing Threat Intelligence?
There are many ways to derive value out of cyber threat intelligence (CTI), whether it be through a full threat intelligence platform, ingesting threat feeds, or simply leveraging threat intelligence features found in common security tools. One of the less adopted ways to benefit from threat intelligence is to share this information with other groups, which helps to reduce incident response time, enact preventative measures, and strengthen the security posture of the organizations involved.
Industry-centric and government-led initiatives have led to a dramatic increase in the sharing of threat intelligence between governments, private organizations, and industries. Some of these include Information Sharing and Analysis Centers (ISACs), Information Sharing and Analysis Organizations (ISAOs), industry groups, holding companies, and other threat intel sharing communities seeking to power secure collaboration:

What are the Types of Threat Intelligence Sharing?
There are two types of sharing, each defined by who is sharing the information.
Unidirectional threat intelligence sharing
With unidirectional threat intelligence sharing, one entity produces and shares cybersecurity intelligence that others consume, and those consuming the intelligence do not contribute in return. Examples of unidirectional threat intelligence sharing include:
- Open-source intelligence, which might involve ingesting an open-source threat intelligence feed or downloading a publicly available report covering a recent attack that contains indicators and methods used.
- Closed-source reports and feeds
Bidirectional threat intelligence sharing
With bidirectional sharing, cyber threat intelligence is sent down to be consumed but can also be ingested from member organizations. Although sharing is allowed and encouraged in these programs, there is no guarantee that every security team involved will share anything.
Concerns Around Sharing Threat Intel
Although threat intelligence is undoubtedly valuable, there are a few common concerns preventing organizations from engaging in sharing:
Privacy and liability concerns
These can be overcome through a more accurate perception of sharing cybersecurity intelligence, protective clauses in legal agreements, recent legislation, or care in what is being shared.
- Scrubbing data for private information or sensitive corporate information before sharing is a good idea regardless of the type of sharing involved.
- The Cybersecurity Information Sharing Act of 2015 (CISA) has provisions to address concerns around privacy and liability. Some of these protections are contingent on certain stipulations being met. As always, proper legal advice is highly recommended to understand how CISA may apply to specific situations.
“There is nothing of value to contribute”
These can be overcome through a more accurate perception of sharing intelligence, protective clauses in legal agreements, recent legislation, or care in what is being shared.
Lack of expertise
Even if you are not a trained professional, adding whatever context, observed attack details, and if possible, analysis developed by those on staff is still beneficial to the community.
Fear of revealing an organization has been hacked
The fear of sharing breach details more broadly than with the entities absolutely necessary is common but can be remedied by following best practices while sharing.
Steps to Start Sharing Threat Intelligence
Whether your organization is already actively sharing intelligence or hasn’t begun doing so yet, here are some tips on where to get started or ways to enhance sharing that is already happening:
Tools and communities
Choose appropriate tools and communities to share threat intelligence. Possible options are:
- Email, which is the easiest starting point
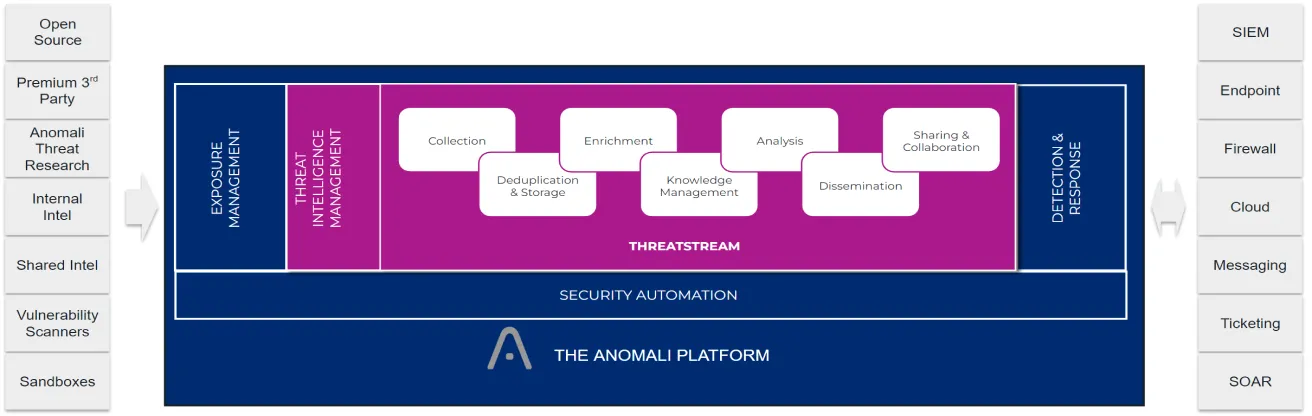
- Tools such as Anomali STAXX, a free solution offered by Anomali that supports sharing indicators through STIX and TAXII
- ISACs and other industry organizations, which normally have mechanisms in place for sharing
- Ad hoc sharing with local entities or partners in other industries
- Anomali ThreatStream users already have a very robust solution to share indicators and other intelligence with other organizations or create their own sharing communities
Share and contribute
Sharing observed adversary behaviors, additional context, attacks seen, or details from incident response are great places to start. Don’t worry if there isn’t much in the way of analysis added to what is shared initially.
Share outside your vertical
Look for opportunities to share with organizations outside of your vertical, including localized entities such as Fusion Centers. As always, working closely with legal teams/lawyers to draw up appropriate agreements to facilitate sharing between the entities is highly recommended.
Share hunting & defense techniques
The more we share, the harder it becomes for the bad guys. Consider sharing:
- Threat hunting details such as searches, specific log entries, etc.
- Successful defense techniques or rules such as YARA rules, snort signatures, Bro rules, and scripts.
Share breach details
Pushing out breach details quickly could mean the difference in someone else being breached and being able to stop it quickly. Also, it could bring lots of assistance in terms of additional intelligence and quicker answers to incident response challenges thanks to the additional resources from other organizations.
Want to Know More About Threat Intelligence Sharing?
Download the whitepaper to learn about the history of threat intelligence sharing, best practices, concerns, and more.