Anomali ThreatStream Next-Gen
Continuously curated threat intelligence that enriches security data, sharpens detections, and informs agentic SOC actions.
Why ThreatStream Next-Gen
WHY THREATSTREAM NEXT-GEN
300x Faster detection and investigation
Analysts pivot across years of data and intelligence in seconds.
96% Reduced time for threat investigations
Context-driven prioritization reduces false positives and alert fatigue.
50% analyst time saved with operationlized intel
Threat intel informs every stage of the SOC workflow, not just reports.
Built for Security Operations — Not Threat Research
Most threat intelligence platforms are designed to collect indicators. ThreatStream Next-Gen ensures intelligence is applied where decisions are made, not buried in separate tools.
It transforms raw threat data into real-time context that drives detection, investigation, and response.
Curated, confidence-scored threat intelligence
maintained continuously — not static feeds.
Native enrichment of security telemetry and alerts
in real time.
Context that travels with every alert and investigation
eliminating swivel-chair analysis.
Intelligence outputs designed for automation and agentic AI
not manual triage.
CORE CAPABILITIES
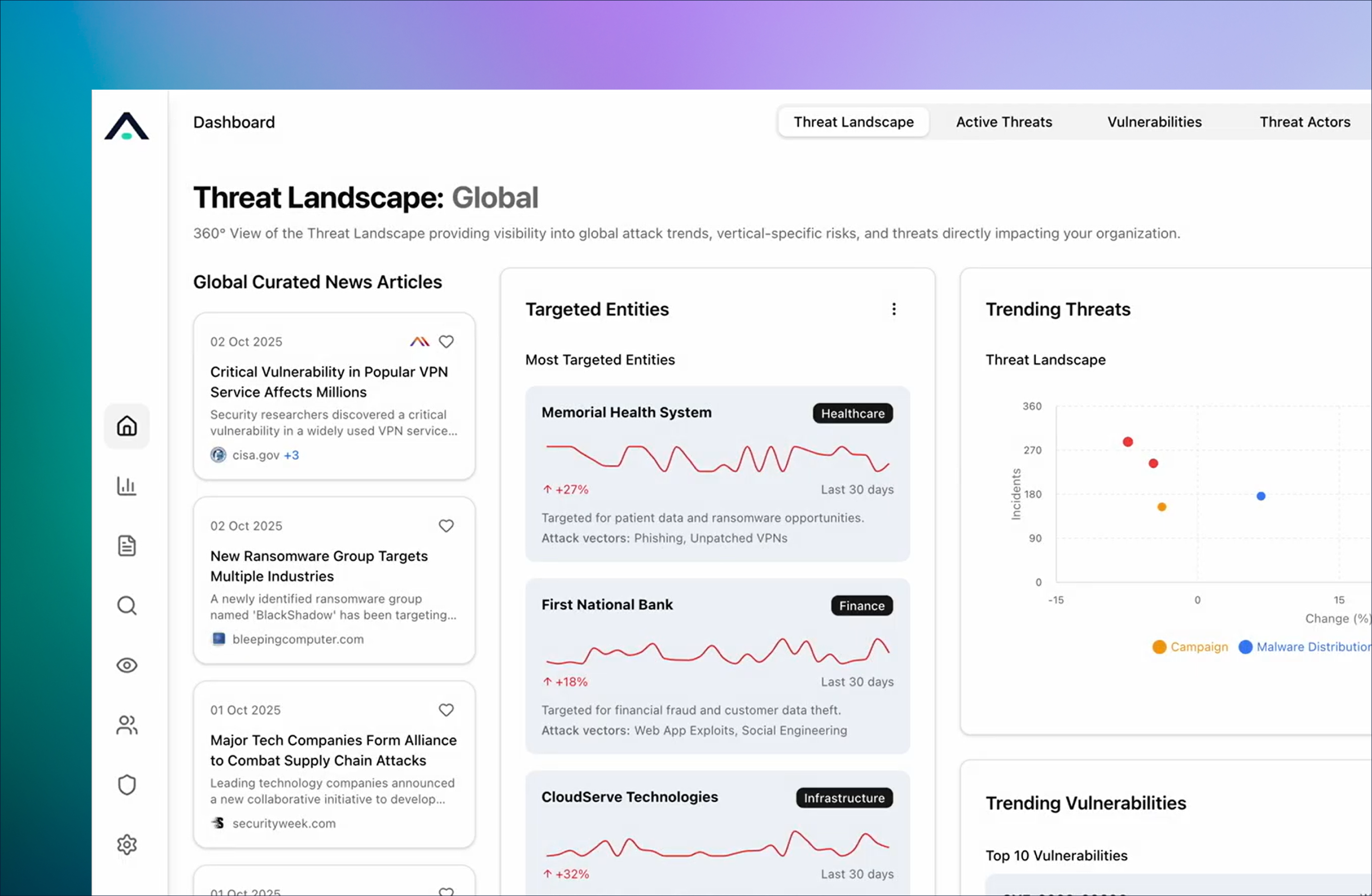
Curated Threat Intelligence
High-confidence indicators sourced, scored, and maintained continuously.
Operational Enrichment
Apply intelligence to logs, alerts, and events in real time.
Threat Context That Travels
Intelligence follows alerts and investigations — no swivel-chair analysis.
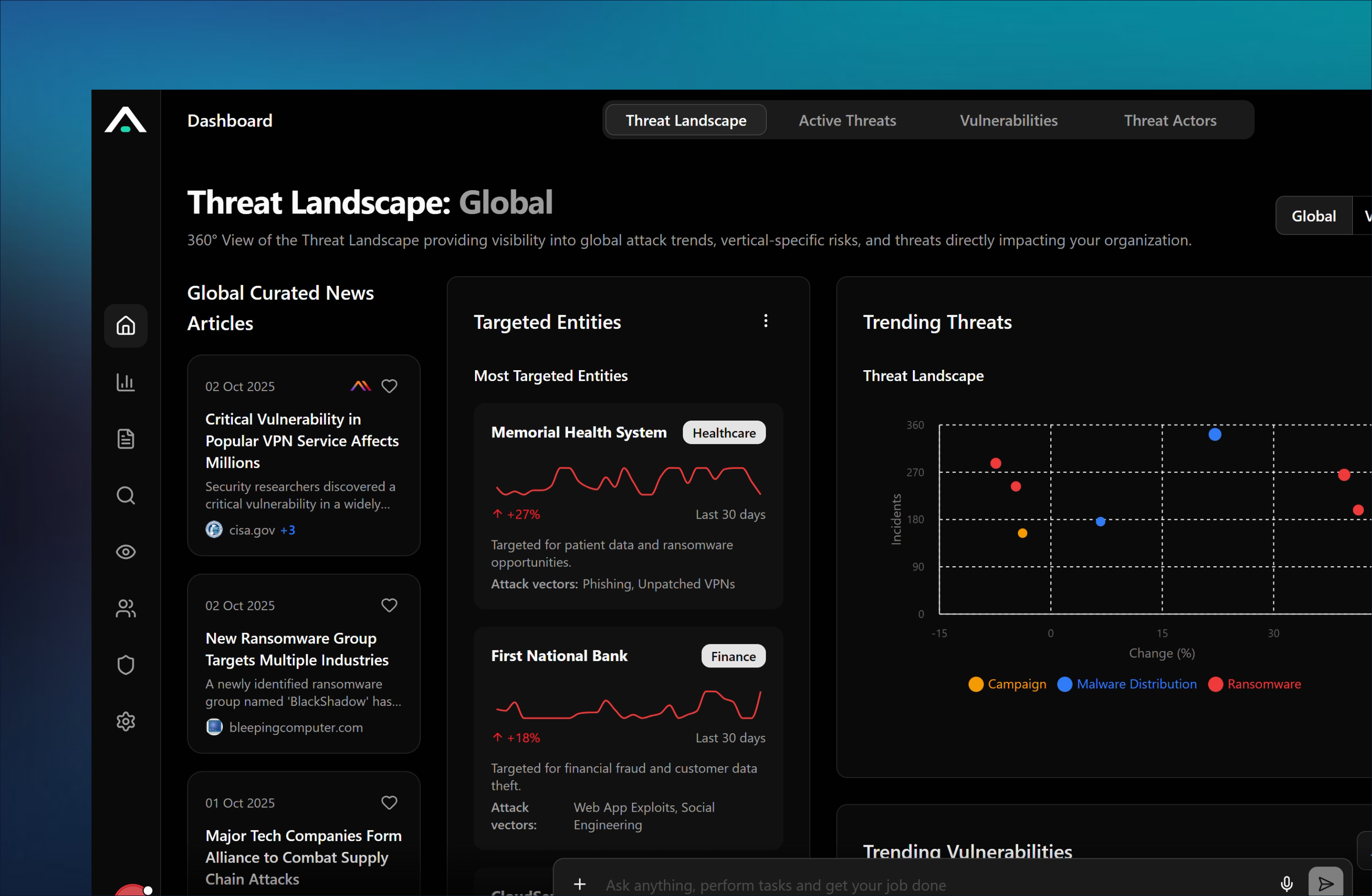
Intelligence-Driven Prioritization
Focus analysts on threats that matter to your environment.
Built for Automation and AI
Intelligence outputs designed to power analytics, automation, and agentic SOC workflows.
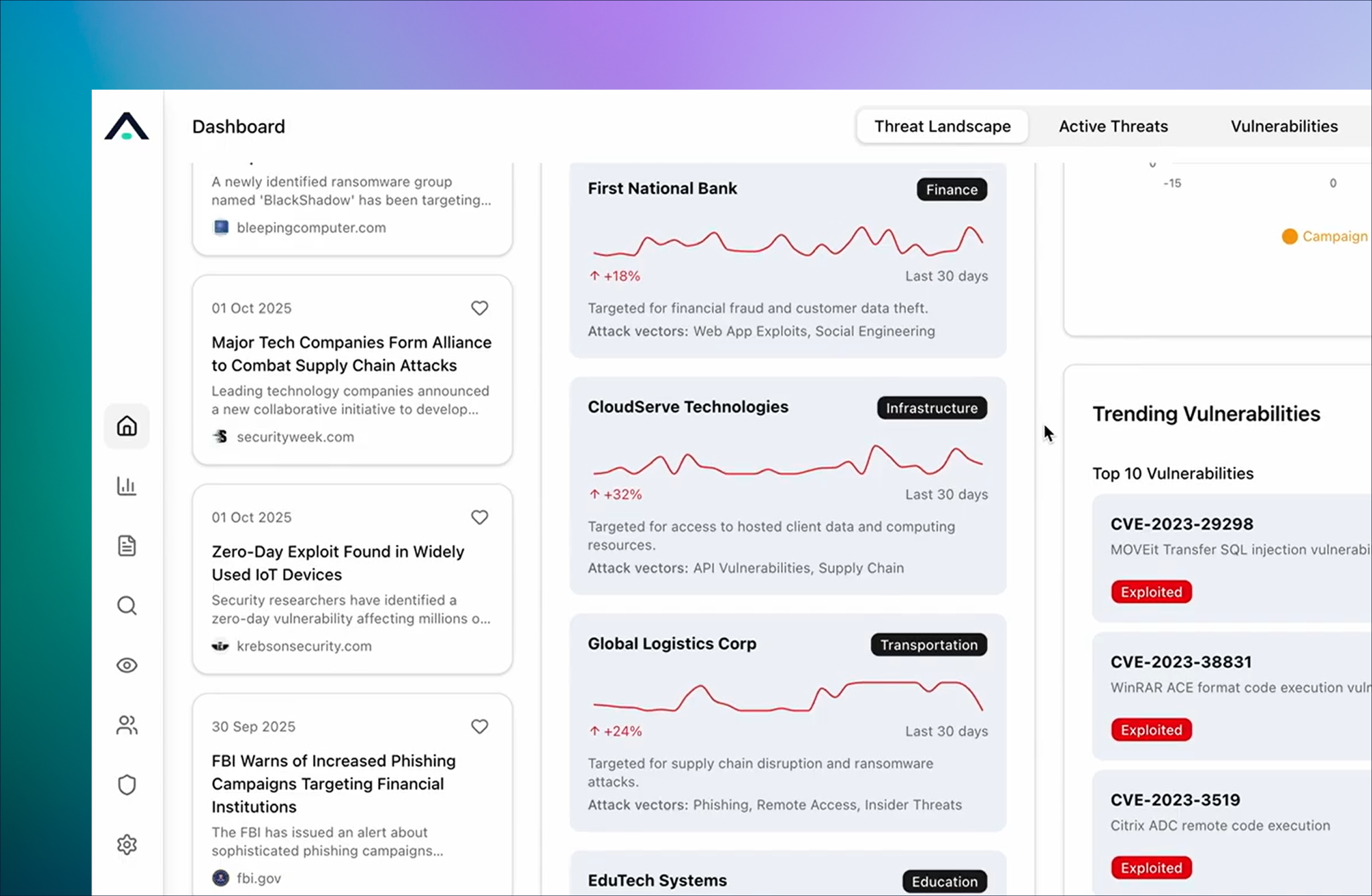
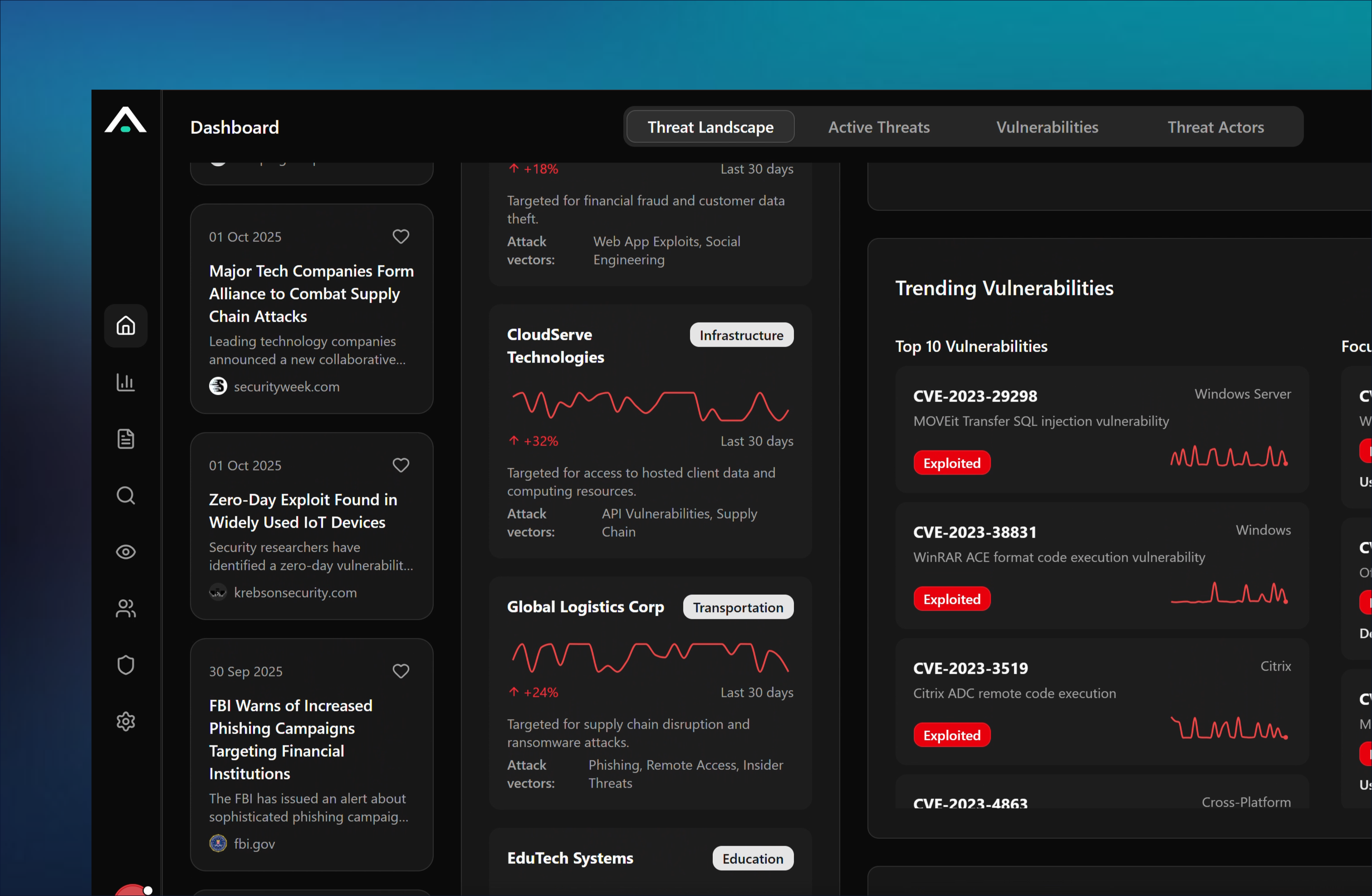
AI-Ready Insights Powered by Threat Intelligence
Act faster, investigate smarter, and respond with confidence.
How it works
1. Collect & Curate
Aggregate and score intelligence from global sources.
2. Enrich & Contextualize
Apply intelligence to security telemetry and alerts.
3. Inform Action
Feed enriched context into detection, investigation, and response workflows.
USE CASEs
Customer Proof
“Anomali has been one of the only platforms we’ve seen that allows us to tag our own intelligence, apply confidence ratings, and collaborate with other intel sources to get a better picture of the attacker infrastructures, etc. at play in cyber attacks.”
- Cybersecurity Specialist, Transportation industry
Operationalize Threat Intelligence
Deliver context where decisions are made.