
Far from being just a buzzword, threat intelligence has proven to be a valuable asset to security teams. 78% of respondents polled from The Value of Threat Intelligence: Ponemon Study, stated that threat intelligence was critical for a strong security posture. One of the difficulties with threat intelligence isn’t necessarily recognizing its value, though - it’s getting started.
At Anomali we wanted to provide people with an easy-to-use tool for collecting and analyzing threat data, which is why we built STAXX. It’s a free TAXII client that allows you to subscribe to any STIX/TAXII feed and link to an online portal for investigations. In the past months we’ve made a lot of changes to ensure that STAXX has everything needed to start incorporating threat intelligence into their security systems. We've even upped our game by including our new Limo services to partner with our TAXII client.
Limo is a preconfigured set of intelligence feeds that STAXX users can access immediately upon download. It’s completely free, and provides information from our Weekly Threat Briefing, Anomali Labs data, and other open source intelligence feeds.
Below is a list of the current Limo feeds and a description of what they provide. If there’s something you think we missed or would like to see, feel free to let us know in our Forum. We’re always looking for feedback (even if it’s that you don’t like puns).
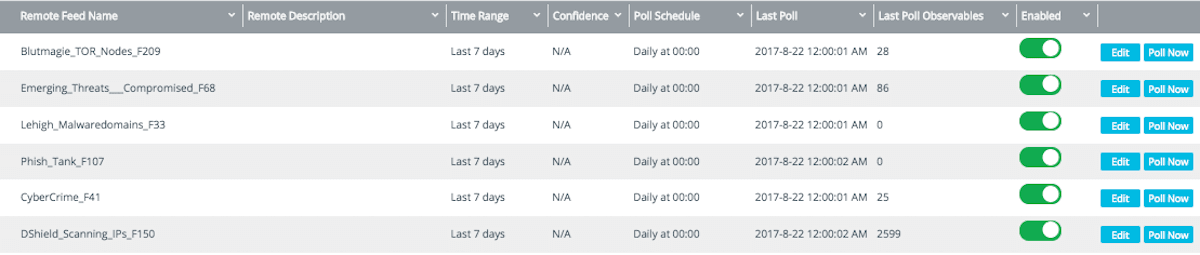
Anomali_Weekly_Threat_Briefing
This feed provides threat indicators from our Weekly Threat Briefings. Each briefing contains curated intelligence about the latest active threats in the news and around the world. A brief analysis from our Anomali Labs team provides some technical insight as to why these threats are relevant. With threat actors consistently altering their malicious tacitcs, keeping up-to-date on the most recent threats and vulnerabilities is critical. You can also subscribe to this information and receive email updates, or check back to our blog on Tuesday's.
Blutmagie_TOR_Nodes
Blutmagie_TOR_Nodes contains a list of exit nodes provided by the website Tor Network Status. Tor is used as a vector for cyber-attacks, and traffic to and from a Tor exit node could be an indication of an attack.
Emerging_Threats___Compromised
Bots, phishing sites, and hostile traffic – oh my! This Limo feed provides hosts published by Emerging Threats that are known to be significantly infected or hostile.
Lehigh_Malwaredomains
Lehigh_Malwaredomains specializes in providing domains that are known to be used to propagate malware and spyware, as published by the DNS-BH project.
Phish_Tank
This Limo feed provides phishing data from PhishTank, a free community site. Phishing is one of the most common and successful kind of attacks. Check out our blog, Teach a Man to Phish, to learn how your adversaries might try to trick you.
CyberCrime
Cybercrime-tracker.net provides Indicators of Compromise focused on banking malware such as Zeus, Pony, etc.
DShield_Scanning_Ips_F150
DShield is a community-based collaborative firewall log correlation system. It receives logs from volunteers worldwide and uses them to analyze attack trends. This Limo feed provides threat indicators for IP addresses that have been observed performing mass scanning activities, provided by Internet Storm Center.
Abuse_ch_Ransomware_Domains
Ransomware Tracker provides domain names that are associated with Ransomware, such as Botnet command and control (C&C) servers, distribution sites, and payment sites.
Abuse_ch_Ransomware_IPs
This feed is the same as above, but with IPs rather than domains. Remember with ransomware it doesn’t pay to pay – you’ll just get played.
Malware_Domain_List___Hotlist
This is a community-based malware domain list project with infromation from Malware Domain List.
Emerging_Threats_C_C_Server
This is a feed of the Emerging Threats’ command and control hosts.
We’ll be publishing a few how-to’s in future blogs to explain how you can take the information from these feeds and make it actionable. Subscribe to our blog to make sure you don’t miss out!
FEATURED RESOURCES

When “Quiet" Means Pre-Positioned: Why Iranian Cyber Threats Are More Dangerous Than Headlines Suggest



