Anomali Reports: Analyse Splunk Events To See If You've Been Breached
Anomali Reports analyses your companies IT activity against millions of Indicators of Comprimise (IOCs) stored in Threatstream. In this post I'll show you how to use Anomali Reports with Splunk in 3 simple steps.
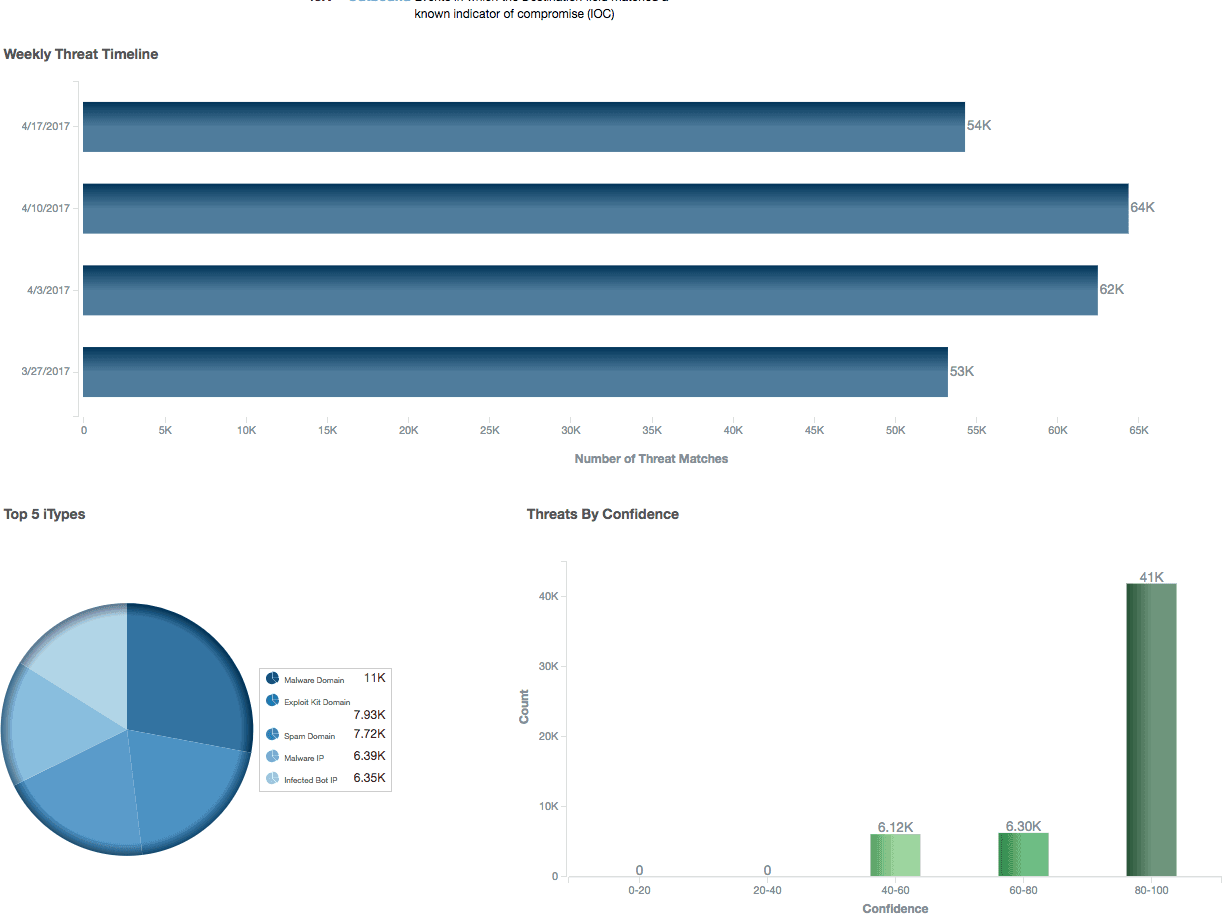

<p><a href="https://www.anomali.com/products">Anomali Reports</a> analyses your companies IT activity against millions of Indicators of Comprimise (IOCs) stored in Threatstream. Each week a Threat Analysis report is automatically generated for you to review. Reports are delivered via web and email and they highlight the most critical security incidents, alerting you to potential security breaches and attacks in process.</p><p>You can use Anomali Reports with lots of data sources with Anomali Link. We also have a number of SIEM integrations including Arcsight, QRadar, and Splunk too. In this post I'll show you how to use Anomali Reports with Splunk in 3 simple steps.</p><p style="text-align: center;"><img alt="" src="https://cdn.filestackcontent.com/32jV0hchQkOvTc8S3hpz"/></p><h3>1. Sign up for a free Anomali Reports account</h3><p><img alt="" src="https://cdn.filestackcontent.com/0pYEsAMiRCWTHKgJiEBt"/></p><p>You can sign up for a free account at: <a href="https://reports.anomali.com/registration" target="_blank">https://reports.anomali.com/registration</a></p><p>Once you've signed up you'll be assigned a username and API key.</p><h3>2. Download and configure the Anomali Link Splunk App</h3><p>You can download the latest version of the Anomali Link Splunk App from: <a href="https://splunkbase.splunk.com/app/3151/" target="_blank">https://splunkbase.splunk.com/app/3151/</a></p><p>Once downloaded, install the app on a standalone Splunk Search Head in the normal way. Once installed on Splunk you will be prompted to configure the settings for the app.</p><p><img alt="" src="https://cdn.filestackcontent.com/5UG9fR72Td6sFhGDSQc6"/></p><p>Select "Anomali Reports" as the destination.</p><p><img alt="" src="https://cdn.filestackcontent.com/JiGZsAUSMG902euYjnzA"/></p><p>If you are a Splunk Enterprise Security customer or a Anomali Threatstream Customer (with the Threatstream Splunk App installed) you can use the relevant data model. Otherwise select "Do not use any data model". Selecting this option relies on your Splunk events being tagged with either tag=web or tag=network. <a href="https://docs.splunk.com/Documentation/Splunk/6.6.0/Knowledge/Abouttagsandaliases" target="_blank">Read more about configuring Splunk tags here</a>.</p><p><img alt="" src="https://cdn.filestackcontent.com/BFYP6DMQ3uFlCa5emyyQ"/></p><p>You must then add the "Username" and "API Key" generated during step 1 when you created your account. Leave the other fields as the defaults.</p><p><img alt="" src="https://cdn.filestackcontent.com/z8HIs7qnTsqg3LM4qDeL"/></p><p>Finally, test the connection between Splunk and Anomali Reports works correctly by selecting "Check Anomali Link Status" on https://reports.anomali.com/report-download . You should see a success message like the screenshot above.</p><h3>3. Your first report, of many</h3><p><img alt="" src="https://cdn.filestackcontent.com/Dao88oXATLXOQ8PeAT0W"/></p><p>Splunk events will now be sent to Anomali Reports for matching against known threats. All you need to do is sit tight, we'll email you when your report is ready. You'll be able to view it online or download it in PDF and CSV formats to share.</p><p>Your Threat Analysis Report will contain potential threats we've identified within your environment including:</p><ul><li>Malware domains and hashes</li><li>C2 domains</li><li>DDOS IPs</li><li>+ much more</li></ul><h3>Need some help?</h3><p>If you have any questions or suggestions about Anomali Reports, please do let me know via the Anomali Forum: <a href="https://forum.anomali.com/" target="_blank">https://forum.anomali.com/</a></p><p>If you're not a Splunk user, sign up for a free Anomali Reports account for detailed instructions on connecting to other data sources and SIEM integrations: <a href="https://reports.anomali.com/registration" target="_blank">https://reports.anomali.com/registration</a></p>
FEATURED RESOURCES

Anomali Cyber Watch
When “Quiet" Means Pre-Positioned: Why Iranian Cyber Threats Are More Dangerous Than Headlines Suggest

Anomali Cyber Watch


