

Introduction
Security teams adopted the Security Information and Event Management (SIEM) as the central hub for all things security - including collection, correlation, and analysis of log data and alerts for security and compliance purposes. The problem, as is the case with any major technology, is that traditional SIEMs were not built to be the one-stop shop for modern security challenges. We work with security teams every day grappling with the increasing demands for logging performance and scalability in today's dynamic threat landscape, not to mention the ability to integrate with ever-changing security tools.
As tools change, and adversaries operate at an unprecedented pace, organizations must prioritize capabilities that facilitate rapid threat identification and response across the organization - and they have to do this in a way that doesn’t disrupt the investments they’ve made, in both people and technology.
We've had the same mission from day 1: Finding malicious actors within your environment using the world's largest and best repository of "known bad" activity patterns and intelligence. The technology landscape has changed with cloud adoption and fragmented data sets, making it siloed, voluminous, expensive, and specialized to interact with. To continue our mission, we are aggregating and bringing all of your data in one place at a very reasonable price point.
Legacy SIEMs: High Costs, High Complexity
Search timeouts, scalability issues, and limited CTI utilization leave legacy platforms built on data architecture with a lot to be desired when it comes to core security functions like threat detection and incident response. Not to mention, most legacy platforms require copious modules and disparate systems to achieve optimal functionality.
Index-based searching highlights challenges as log volumes and the number of log sources increase. Growing indexes can impede search speed, making it challenging to identify and thwart threats effectively.
On top of it all, legacy SIEMs come with exorbitant costs - and for good reason, as many were not built as a cloud-first platform in today’s landscape. The expense associated with logging everything often forces organizations to selectively log data, leading to blind spots and missed attacks. Moving data to Anomali - especially the high-value security data, like endpoint, firewall, and network traffic, offers a cost-effective solution, potentially saving up to 75% compared to legacy SIEMs and their non-cloud native storage capabilities.
Adding a modern platform to address core SIEM use cases
Legacy SIEMs can provide tremendous value, but oftentimes with the aforementioned challenges attached. Embracing a hybrid model with Anomali delivers outstanding performance and low latency, reducing incident response times and fortifying overall security.
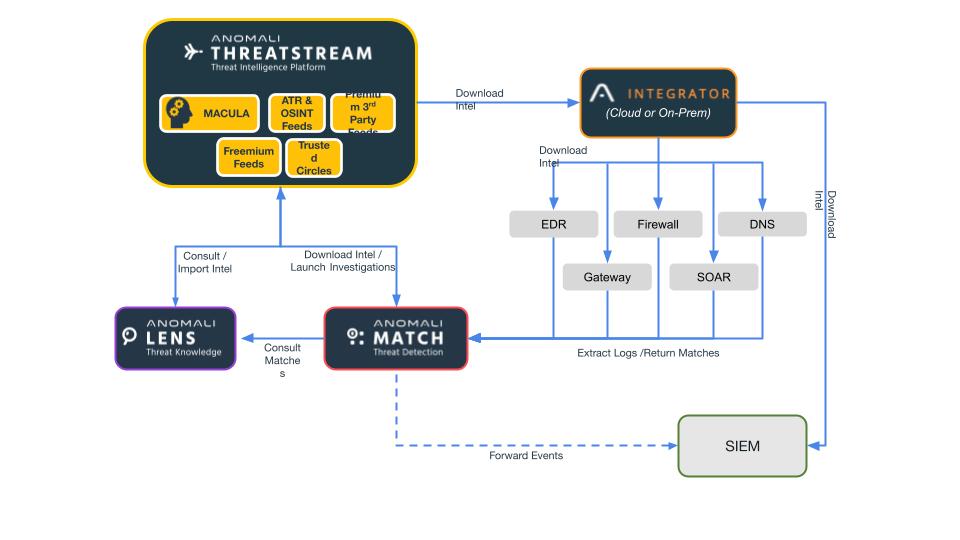
Anomali: Ideal for Today's Toughest SIEM Use Cases
The Anomali Platform, evolving from the industry-leading Threat Intelligence Platform, emerges as a contemporary log management platform that excels in storing, analyzing, and swiftly accessing data at scale. Its rapid search capabilities, real-time alerting, CTI database, and customizable dashboards make it optimal for various security use cases.
Key SIEM Use Cases that Anomali Can Solve
Threat Hunting with all available Threat Intelligence
Anomali Log Management provides the speed, scale, and querying flexibility essential for proactive threat hunting. Its query language supports Natural Language Search (available in a variety of languages), empowering security teams to optimize searches and swiftly pinpoint threats. Integration with the largest repository of Indicators of Compromise (IOCs) adds valuable context to threat hunts.
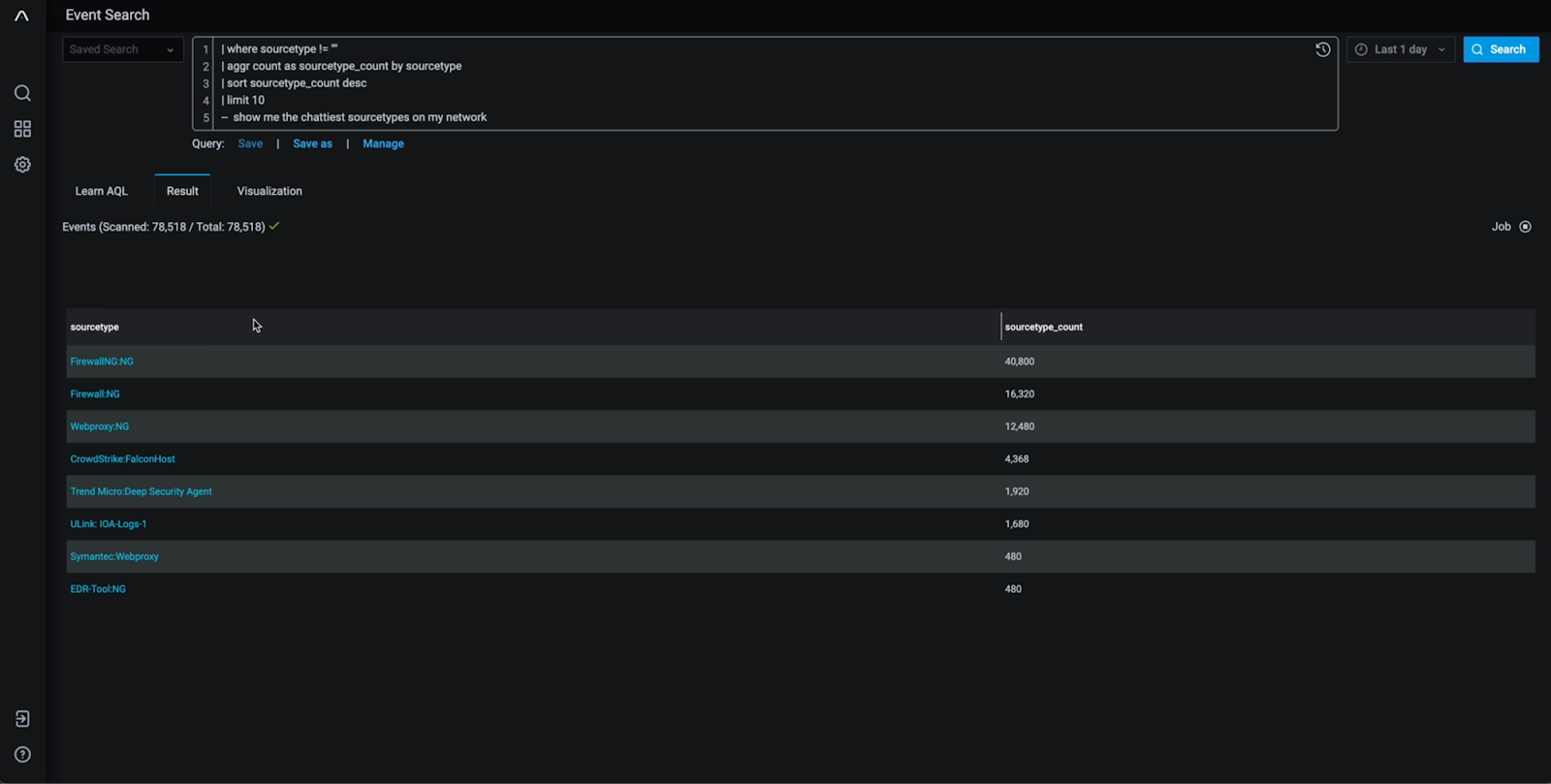
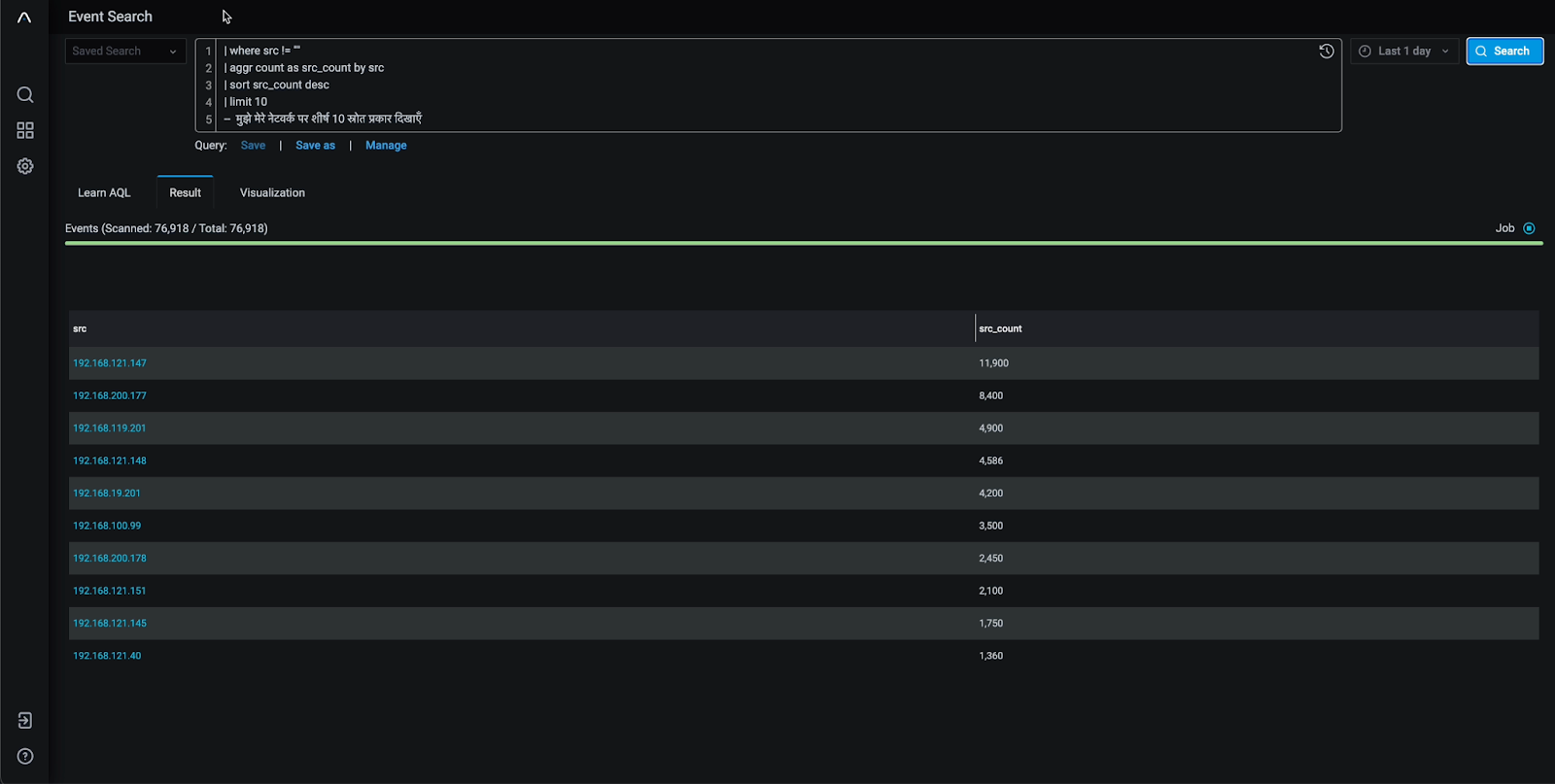
Incident Response and Forensics
In incident response scenarios, time is of the essence. Anomali Log Management facilitates effective incident response and forensics by offering cost-effective, long-term data retention. Its scalability allows organizations to log even the chattiest datasets, taking heavy lifting off of the SIEM while providing a comprehensive dataset for investigating attacks, determining root causes, and reconstructing events. Findings from a recent stress test of the Anomali Platform showed that users could query over a petabyte of data and receive results in 3-4 minutes.
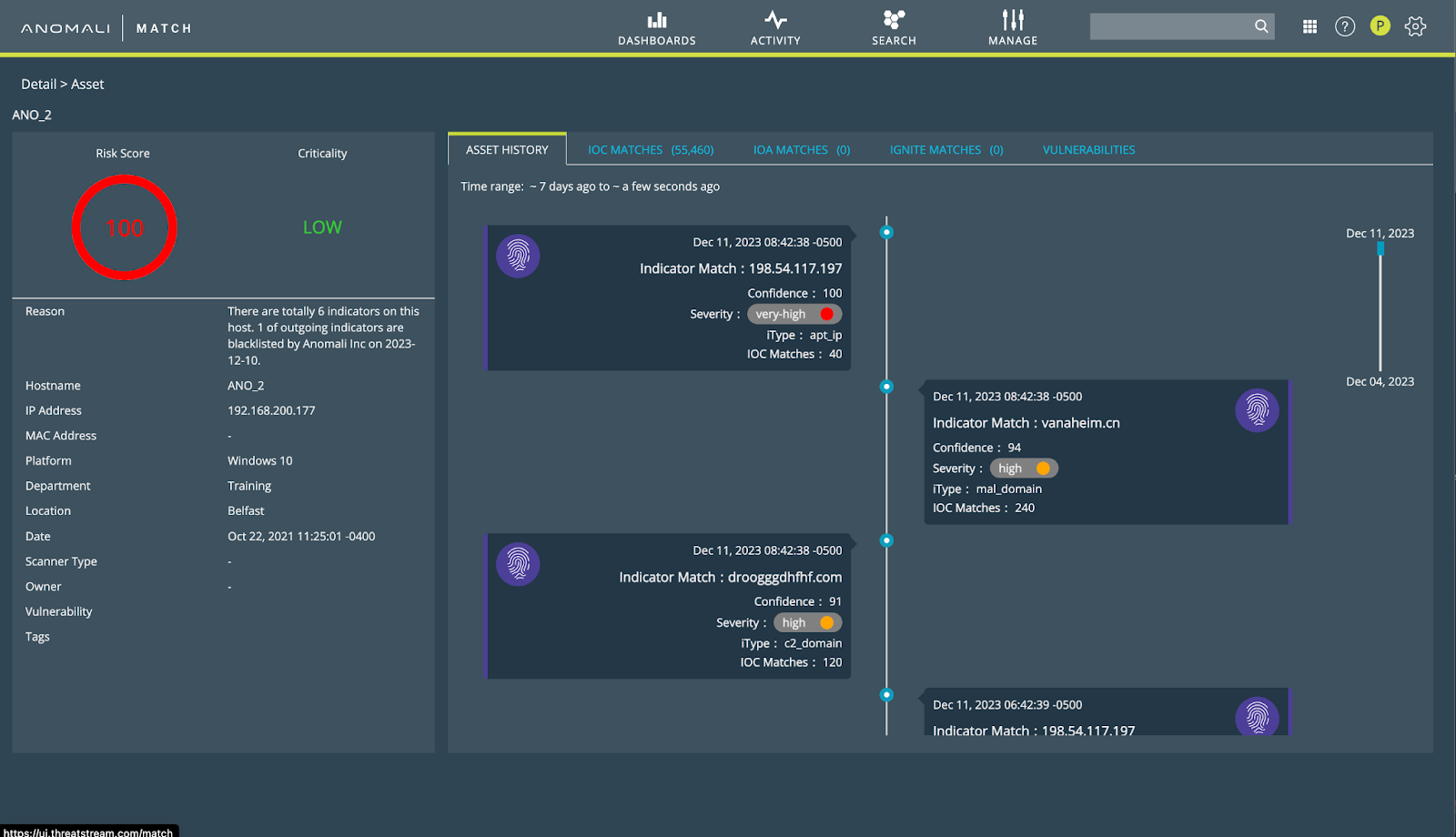
Data Retention and Backup
Anomali addresses compliance challenges by providing scalable, affordable long-term data storage. Organizations can meet evolving compliance requirements - implementing Anomali eliminates on-premise upkeep and costs, high costs of SIEM logging, and provides backup capabilities to ensure swift disaster recovery. Anomali Link supports easy collection and processing of regulated data from various sources, ensuring compliance without escalating costs, or compromising on data availability.
Workforce Utilization and Training
Built on the Anomali Query Language - users of the Anomali platform no longer need to rely on complex search queries and certifications. This means Tier One analysts can utilize Natural Language to ask questions like “Show me all hosts that have been affected by Killnet” and get results back within seconds. This also reduces the need for third-party engineering services that quickly inflate costs.
Dashboarding and Alerting - Data Visualization
Anomali offers real-time visibility into security status, enabling organizations to analyze trends, detect threats, and troubleshoot issues. Its streaming engine updates searches and dashboards upon data arrival, allowing instant anomaly detection. Customizable dashboards and pre-built options, as well as additional applications from the Anomali App Store enhance visualization and information sharing.

Conclusion
Through working with our customers and partners, we’ve found that security teams are looking for a better way to hunt and search their data, and leadership teams are looking to save dollars wherever they can. Anomali stands as a powerful and versatile tool for organizations seeking optimal speed, scale, and total cost of ownership to address their toughest SIEM use cases. We aim to enhance your security team’s performance with cloud-native search, and storage scalability, all while providing better economic outcomes.
FEATURED RESOURCES

When “Quiet" Means Pre-Positioned: Why Iranian Cyber Threats Are More Dangerous Than Headlines Suggest



