Heads Up! A Phishing Attack Early Warning System
Get the Anomali's curated threat intelligence in Splunk so you can be prepared for the next phishing attack on your network.
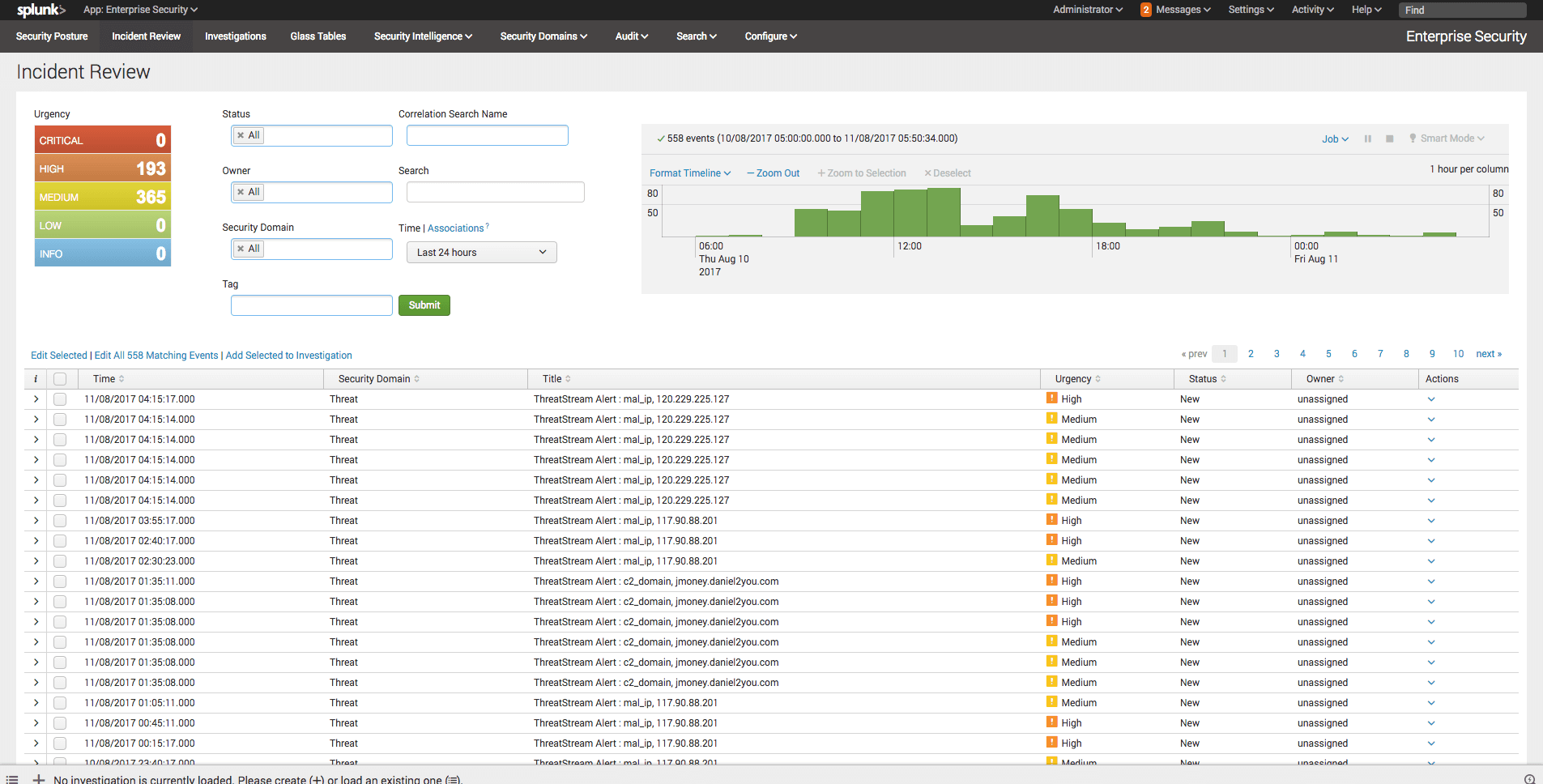

<p><a href="https://www.anomali.com/blog/category/weekly-threat-briefing">You're probably familiar with Anomali's Threat Bulletins</a>. If not, go and have a read of our most recent one covering "TODO." Threat Bulletins provide information about an event to derive information detailing the tactics, techniques, and procedures used by the attacker. This helps you to create profiles of the actors or groups and find new attacks with their associated indicators. All these efforts can be leveraged together to help make better decisions on how to protect your network should adversaries turn their attention to you.</p><p>Threat Bulletins can be viewed in a number of ways; via the ThreatStream user interface, downloadable PDFs, or through our Anomali ThreatStream Splunk App.</p><p>Earlier this month I spoke to a customer who are heavy users of our Splunk App and were noticing a lot of phishing attempts on their employees. Using the Anomali Splunk App, they were able to see that their email logs regularly matched known phishing threat indicators.</p><p>In addition to educating their staff, "DO NOT click on links in emails," and using the Anomali Splunk App they also wanted advanced warning about future phishing attempts in their threat workflow -- predominantly Splunk's Enterprise Security Incident Review dashboard.</p><p>As users of the Anomali Splunk App they were already consuming Threat Bulletins into Splunk, so it was just a case of integrating them into ES. Why add them into ES? Splunk's ES Incident Review dashboard was a first-line for their SecOps team, displayed on a big screen in their SOC. Therefore, adding Threat Bulletins to appear in this view meant they would see them immediately and take prompt action when needed. To do this we created Notable Events from Threat Bulletins related to phishing campaigns.</p><p>The setup was relatively easy. In fact, I covered the steps <a href="https://www.anomali.com/blog/threatstream-matches-as-notable-events-in-splunk-heres-how">in a previous post examining how you could create Splunk ES Correlation Searches and Notable events</a>. Without going over all the steps again, replace the necessary steps "Building a Correlation Search" and "Add Notable Event Action" with the configuration below. Once created you'll start to see Threat Bulletins appear as Notable Events in ES.</p><h2>Building a Correlation Search</h2><h2><img alt="" src="https://cdn.filestackcontent.com/SjTG8QTPQRygODZHAgWi" style="height: 310px; width: 600px;"/></h2><p><code>Search Name: Phishing Email Threat Bulletin<br/> Application Context: Enterprise Security<br/> Dispatch Context: Enterprise Security<br/> Description: Phishing Email Threat Bulletins<br/> Search: | inputlookup tm_tipreport where name=[Email]* | addinfo | where _time>=info_min_time AND (_time<=info_max_time OR info_max_time="+Infinity") | table _time, id, name, link<br/> Time Range Earliest: -2h@h<br/> Time Range Latest: -1h@h<br/> Cron Schedule: 45 * * * *<br/> Scheduling: Continuous<br/> Window duration: 600s </code></p><p>Note the key part of the search; "| inputlookup tm_tipreport where name=[Email]*", where the search limits results to Threat Bulletins whose name contains the word "Email". You can modify this text search as needed.</p><h2>Add Notable Event Action</h2><p><img alt="" src="https://cdn.filestackcontent.com/tT6S6KDFR9u2SxzRLUiI" style="width: 600px; height: 292px;"/></p><p>I've added some default configuration settings, such as severity, for the Notable Event. All of this can be amended, if required:</p><p><code>Title: Phishing Email Bulletin: $name$<br/> Description: Anomali Threat Bulletin<br/> Security Domain: Threat<br/> Threat Severity: high<br/> Default Owner: (leave as system default)<br/> Default Status: (leave as system default)<br/> Drill-down name: search bulletin $name$<br/> Drill-down search: | inputlookup tm_tipreport where id=$id$<br/> Drill-down earliest offset: $info_min_time$<br/> Drill-down latest offset: $info_max_time$</code></p><h2>What next?</h2><p>In this post and <a href="https://www.anomali.com/blog/threatstream-matches-as-notable-events-in-splunk-heres-how">my last</a> I've given some example searches of how to use Anomali's threat intelligence inside of Splunk's Enterprise Security app. If you're feeling brave; why not create your own? You can start with small changes to my examples, perhaps instead of monitoring phishing email Threat Bulletins, you could monitor for Threat Bulletins that have "Malware" in their name.</p><p>Alternatively, start creating or customising your own dashboards in the Anomali ThreatStream Splunk app using Splunk's flexible user interface options</p><p>Not an Anomali ThreatStream Splunk App user yet? <a href="https://www.anomali.com/community/anomali-splunk-app">Hear more about why so many of our customers are using it...</a></p>
FEATURED RESOURCES

Anomali Cyber Watch
When “Quiet" Means Pre-Positioned: Why Iranian Cyber Threats Are More Dangerous Than Headlines Suggest

Anomali Cyber Watch


