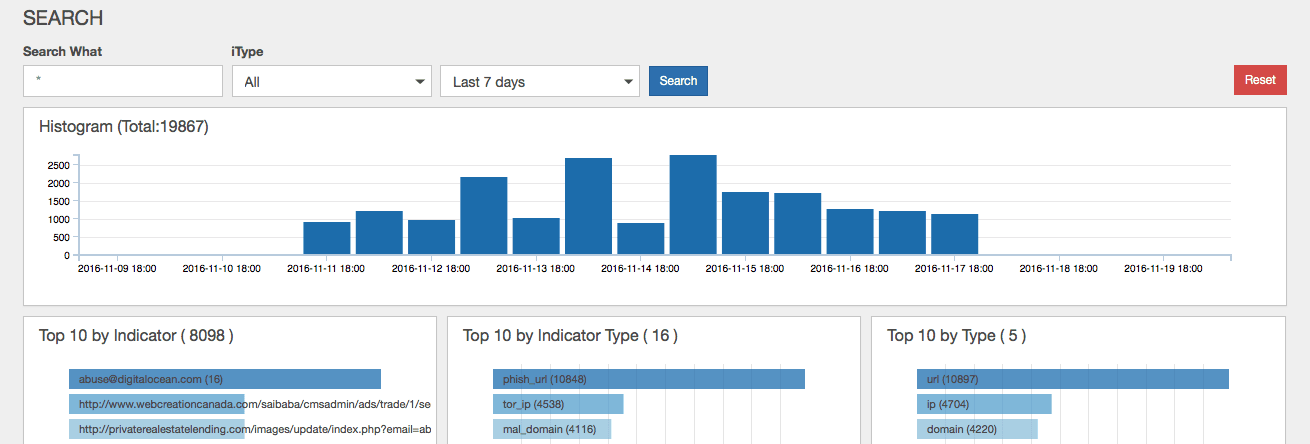

<p>In December of 2014, the Financial Services Information Sharing and Analysis Center (FS-ISAC) and Depository Trust and Clearing Corporation (DTCC) <a href="http://www.dtcc.com/news/2014/december/03/soltra" target="_blank">announced</a> the general availability of <a href="http://www.soltra.com" target="_blank">Soltra Edge</a>, a program designed to help facilitate the sharing of threat intelligence in a more organized and automated manner than over email or other manual methods. Soltra Edge leveraged STIX and TAXII standards to enable the sharing of threat intelligence between systems or between organizations. Soltra Edge saw strong adoption by over 2900 organizations in 77 countries looking to access and integrate valuable threat intelligence. I believe that the STIX and TAXII standards owe their popularity to Soltra Edge for helping to drive adoption and increase their visibility.</p><p>Last week the DTCC and FS-ISAC announced their decision to shut down development of Soltra Edge effective November 15, 2016. This will no doubt be tough on the organizations that have leveraged the platform and become dependent on STIX/TAXII feeds to enhance their threat intelligence collaboration.</p><p>Anomali has long supported seamless threat sharing and was a founding member of <a href="https://www.oasis-open.org" target="_blank">OASIS</a>, the body behind the STIX and TAXII standards. In light of the Soltra announcement Anomali has stepped forward to offer STAXX, a free solution that supports the STIX/TAXII standards. STAXX not only understands STIX/TAXII feeds but also provides powerful IOC searching and dashboards, all in an easy-to-use platform.</p><p><img alt="" src="https://cdn.filestackcontent.com/lhC4fhm9SHiQ5mlrqWvp"/></p><p style="text-align: center;"><em>Anomali STAXX IOC Search Dashboard</em></p><p>STAXX can be linked to the powerful ThreatStream investigation portal giving access to over a hundred additional feeds. With the ThreatStream integration STAXX provides a direct link to explore IOCs and identify threat actors, campaigns, TTPs and other associated indicators.</p><p><img alt="" src="https://cdn.filestackcontent.com/w3GtYdyaSmibzq4Lt1O1"/></p><p style="text-align: center;"><em>Anomali ThreatStream Investigation Portal</em></p><p>Available as an OVA download, STAXX can be up, running, and easily configured via an intuitive dashboard within minutes. STAXX builds on the promise of Soltra, offering ease of use, free license, on-premise deployment, and additionally, the ability to link to a free ThreatStream account. Anomali is pleased to offer STAXX to the Soltra community and hopes to carry forward the good work paved by Soltra in supporting the STIX and TAXII standards and promoting easy-to-use threat intelligence sharing and collaboration.</p><p>STAXX is now available as a free download at <a href="http://www.anomali.com/staxx">www.anomali.com/staxx</a>.</p>
FEATURED RESOURCES

Anomali Cyber Watch
Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more
Zero-Click Remote Code Execution Flaw Affects Claude Desktop Extensions. Threat Actors Exploit SolarWinds Web Help Desk Vulnerabilities to Deploy Velociraptor. Fake 7-Zip Site Distributes Trojanized Installer Converting Systems to Proxy Nodes. ZeroDayRAT Commercial Mobile Spyware Targets Android and iOS. And more..

Anomali Cyber Watch
Anomali Cyber Watch: Notepad++ Attack, RAT Uses Hugging Face, Microsoft Office Flaw and more
Notepad++ Supply Chain Attack Delivers Chrysalis Backdoor. Android RAT Uses Hugging Face Platform to Host Malicious Payloads. Fancy Bear Exploits Microsoft Office Flaw in Ukraine. Nitrogen Ransomware Decryptor Fails Due to Coding Error. And more...


