How To Find Malicious Actors Inside Your Network
In the latest release of our Splunk ThreatStream App the addition of Threat Actor and Threat Bulletin information aims to simplify cyber security investigations.
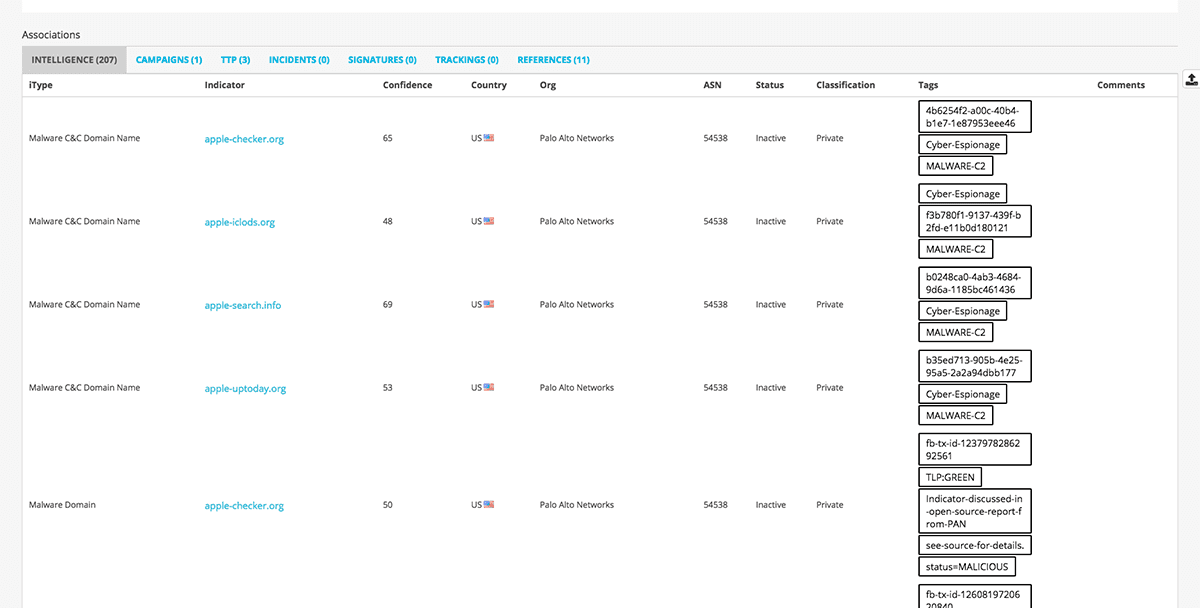

<p>As an analyst, context is key.</p><p>With hundreds, often thousands, of security incidents raised by modern SIEM products it can make the process of triaging the most serious of them incredibly difficult. Adding context to events that form a security incident can help investigations by reducing both time and effort. Sometimes looking at a Whois record on a domain can rule out a threat (<em>if only it was always that simple!</em>).</p><p>Anomali ThreatStream offers users access to millions of indicators and their associated context. <a href="https://www.anomali.com/blog/anomali-threatstream-splunk-app-v6-released">In the latest release of our Splunk ThreatStream App</a> the addition of Threat Actor and Threat Bulletin information aims to simplify security investigations. This post offers an introduction to the new functionality using some sample data (not related to Anomali).</p><h2>See through the noise, know where to focus</h2><p><img alt="" src="https://cdn.filestackcontent.com/OJua0kseSIixVkwEm5tb"/></p><p>The overview page of the Splunk ThreatStream App provides a great place to start an investigation. I can easily see the critical events that have matched ThreatStream Indicators of Compromise and how serious they are using the confidence and severity rankings assigned by ThreatStream. The app has identified 14 events in my Splunk logs that match known indicators associated with an actor named "Sofacy". These indicator matches are particularly interesting as it might indicate the organization is subjected to a more targeted campaign.</p><h2>Learn more about actors that are potentially inside your network</h2><h2><img alt="" src="https://cdn.filestackcontent.com/q2T0e0XfSamogqd8rUrH"/></h2><p>Drilling down on the actor "Sofacy" I can see all the known indicators associated to the Actor that have been seen in my environment as well as the aliases this Actor has been known by. I can see the tags associated with the Actor to give me an indication of what type of organizations they are targeting, for example; retail, banking, or technology companies. Before investigating further, lets first take a look at more information about the Actor in ThreatStream.</p><p><img alt="" src="https://cdn.filestackcontent.com/8I1uVUiyRd6BZJ3nVN7w"/></p><p>In the ThreatStream portal I can see the Sofacy team is an APT group of suspected Russian origin that has been operating since at least 2009. A detailed killchain analysis shows me how they tend to operate, in this case delivery is via malicious files in phishing emails that exploit 0-days. I can also see all the indicators associated with the actor Sofacy, campaigns they have been linked to and their Tactics, Techniques and Procedures (TTP's). Armed with this information I can continue my investigation in Splunk.</p><h2>Understand where an actor has been inside your network</h2><h2><img alt="" src="https://cdn.filestackcontent.com/aHeciZ1OTyCmWOZOOBge"/></h2><p>Knowing that Sofacy uses spearfishing campaigns to deliver exploits, I start by looking at email matches for this Actor. I can see 3 users in my organization have received numerous emails from known email addresses associated with Sofacy. All 3 malicious email addresses have a high confidence and severity score issued by ThreatStream which alerts me to a more serious threat. I can then drill down to search through my email logs in Splunk and see the content of messages sent from these addresses.</p><p><img alt="" src="https://cdn.filestackcontent.com/WG5zZiuhRZqpZTyeqf7i"/></p><p>I am also able to see if any malicious email attachments have been observed in my network, suggesting they have been opened. In fact, I can see 3 machines in my organization that have a file hash that matches a known malware file hash associated with Sofacy phishing emails. Upon further inspection in Splunk I can see these machines are owned by the users who received emails from the know malicious email addresses.</p><p>Using all of this data I can then decide upon the next steps to take; perhaps continuing to investigate further, quarantining these machines from the wider network, or blocking the destinations the malware is communicating with.</p><h2>Get started with ThreatStream today</h2><p>Within minutes I have been able to:</p><ul><li>Identify a potential Threat Actor in my network</li><li>Quickly research the Threat Actor including their behavior and motives</li><li>Understand the risk the Threat Actor poses</li><li>Assess where the Threat Actor has been inside my network</li></ul><p>And this is the start of what's possible. To learn more about how you can integrate Threat Intelligence with your SIEM head over to: <a href="https://www.anomali.com/products/threatstream">https://www.anomali.com/platform/threatstream</a>.</p>




