Proactively Monitor Your Network Against Attacks Using Our FREE Threat Intelligence in Splunk
The ThreatStream Community Splunk App can get you started with Anomali's powerful Threat Intelligence, allowing you to proactively monitor your network and protect against attacks.
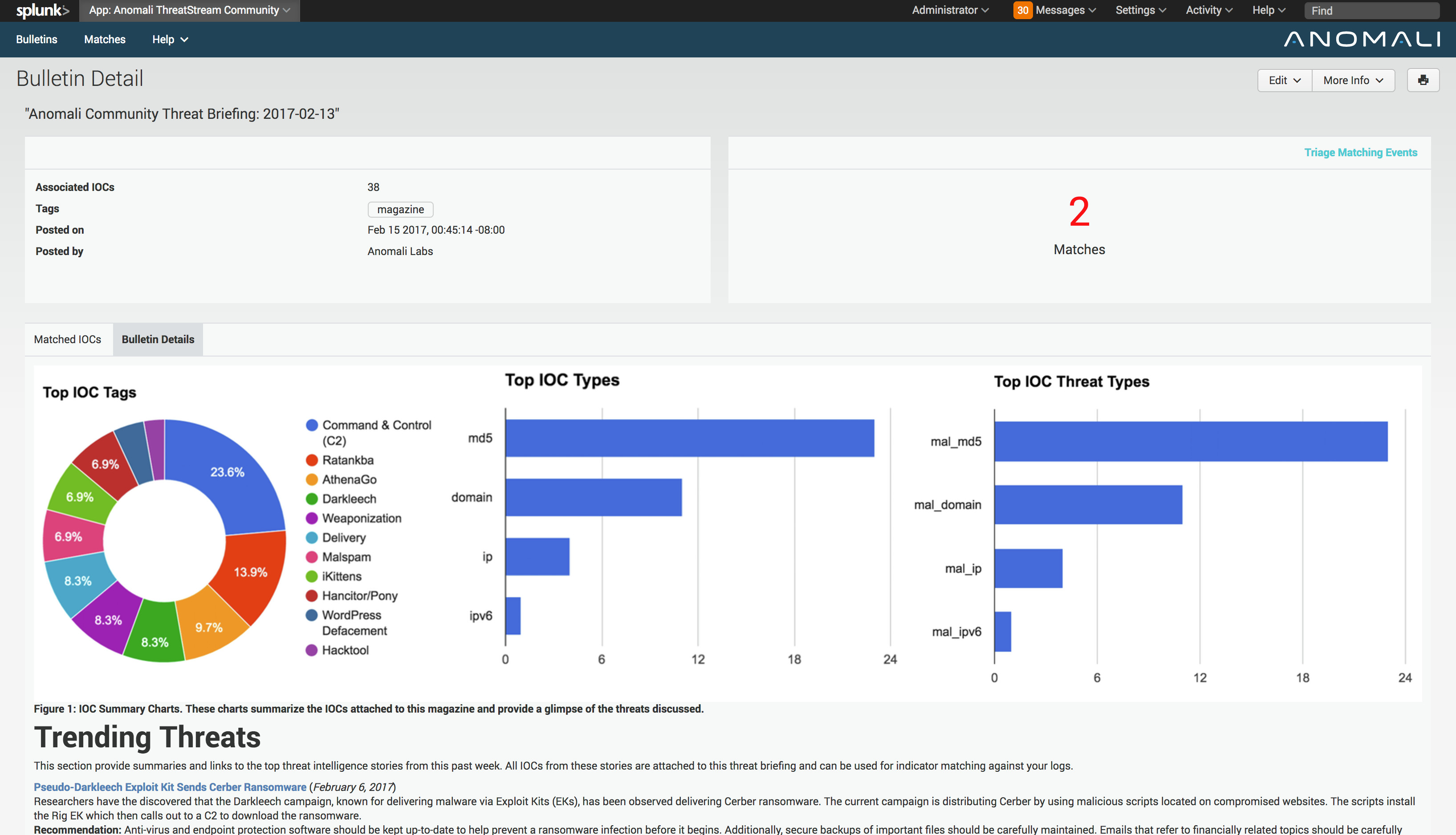

<p><a href="https://www.anomali.com/blog/malicious-actors-inside-your-network-heres-how-to-find-them">A few weeks ago I showed how to use the Anomali ThreatStream Splunk App to hunt known actors that had been observed trying to access your environment, and in some cases where they were already inside</a>.</p><p>For those who are not yet ThreatStream customers, do not fear. Our free ThreatStream Community Splunk App can get you started with Anomali's powerful Threat Intelligence, allowing you to proactively monitor your network and protect against attacks.</p><h2>View our Weekly Threat Bulletin reports</h2><h2><img alt="" src="https://cdn.filestackcontent.com/sWaj5oIT7mmzuwoM0Ufo" style="width: 600px; height: 344px;"/></h2><p><a href="https://www.anomali.com/blog/category/weekly-threat-briefing">You might have seen the weekly Threat Briefings our labs team posts on the blog</a>. Many ThreatStream and non-ThreatStream customers alike use these posts to stay on-top what's happening in the cyber security world (attackers, malware outbreaks, threats, etc).</p><p>If you're a Splunk user you can view these Threat Briefings without ever leaving Splunk in the ThreatStream Community App. </p><h2>Automated Threat Bulletin Matches</h2><h2><img alt="" src="https://cdn.filestackcontent.com/0APDoRzwRgyVWfkcVEy4" style="width: 600px; height: 344px;"/></h2><p>Not only can you view the downloaded Threat Bulletins, the ThreatStream Community App will also match your Splunk against the Indicators of Compromise (IOCs) linked to each Bulletin. IOCs include IPs, URLs, file hashes (malware), and compromised emails, for example. If you see one of these IOCs match against your Splunk logs, it can indicate a further investigation is needed.</p><h2>Match Against Millions of IOCs</h2><p><img alt="" src="https://cdn.filestackcontent.com/y0plK7gwTe6frbaUxJCg" style="width: 454px; height: 273px;"/></p><p>If you choose, you can also forward your Splunk logs into Anomali Reports to have them analysed against millions more IOCs. If you choose to upgrade to our ThreatStream Commercial Splunk App you can download these indicators directly into Splunk, and use with other Splunk Apps.</p><h2>See the App in Action</h2><p><iframe allowfullscreen="" frameborder="0" height="315" src="https://www.youtube.com/embed/0iMhCxBhdB4" width="560"></iframe></p><h2>Free Download on Splunkbase</h2><p>The Anomali Community App for Splunk combines the quality of Anomali’s threat intelligence with the depth of Splunk’s analytics to help organizations identify and respond to external security threats.</p><p><strong><a href="https://splunkbase.splunk.com/app/3443/">Download the ThreatStream Community Splunk App on Splunkbase here</a></strong>.</p>
FEATURED RESOURCES

Anomali Cyber Watch
Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more
Zero-Click Remote Code Execution Flaw Affects Claude Desktop Extensions. Threat Actors Exploit SolarWinds Web Help Desk Vulnerabilities to Deploy Velociraptor. Fake 7-Zip Site Distributes Trojanized Installer Converting Systems to Proxy Nodes. ZeroDayRAT Commercial Mobile Spyware Targets Android and iOS. And more..

Anomali Cyber Watch
Anomali Cyber Watch: Notepad++ Attack, RAT Uses Hugging Face, Microsoft Office Flaw and more
Notepad++ Supply Chain Attack Delivers Chrysalis Backdoor. Android RAT Uses Hugging Face Platform to Host Malicious Payloads. Fancy Bear Exploits Microsoft Office Flaw in Ukraine. Nitrogen Ransomware Decryptor Fails Due to Coding Error. And more...


