Splunking The Modern Honey Network: Community Data (Part 4)
In this post I am going to give you a brief insight into the data that was reported back from the MHN honeypots in January 2017 (all 85 million of them!)
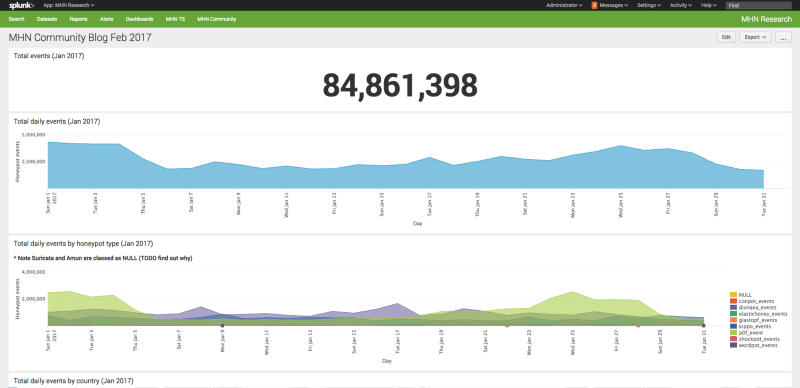

<p>Over the last 3 weeks, I’ve looked at: <a href="https://www.anomali.com/blog/splunking-the-modern-honey-network-getting-value-from-your-honeypots-data-p">ingesting Modern Honey Network data into Splunk</a>, <a href="https://www.anomali.com/blog/splunking-the-modern-honey-network-adding-context-using-threat-feeds-part-2">adding context to MHN data using threat feeds</a>, and <a href="https://www.anomali.com/blog/splunking-the-modern-honey-network-honeypot-alert-automation-part-3">creating alerts using MHN data</a>.</p><p>In this post I am going to give you a brief insight into the data that was reported back from the MHN honeypots in January 2017.</p><h2>About MHN Community Data</h2><p>The MHN Server reports anonymised attack data back to a central Anomali datastore. <a href="https://github.com/threatstream/mhn/blob/master/README.md">You can control what data from your honeypots is shared</a>. After some analysis we also incorporate some MHN Community data into a threat feed in our <a href="https://www.anomali.com/products/threatstream">Anomali Threatstream platform</a>. Hint: <a href="https://ui.threatstream.com/store">you can find it in the App Store</a>.</p><p><img alt="" src="https://cdn.filestackcontent.com/IRNlwu76Qv26psaI1z6U" style="width: 800px; height: 197px;"/></p><p>We provide access to the MHN Community data for those who are sharing honeypot data with us. <a href="https://github.com/threatstream/mhn/wiki/Getting-Access-to-the-MHN-Community-Data">You can read more about gaining access to the data here</a>.</p><h2>MHN Community Data Stats</h2><h3>Overview</h3><p><img alt="" src="https://cdn.filestackcontent.com/QFjN2mitQv28d4rNPD8c" style="width: 800px; height: 380px;"/></p><p>There were almost 85 million distinct honeypot events. We saw peak attack volume on January 1st where 4.32 million events were reported. This fell to an 1.8 million on the January 6th (the 3rd lowest volume by day — only January 30th and 31st saw fewer events).</p><h3>Honeypot Types</h3><p><img alt="" src="https://cdn.filestackcontent.com/wKM7YaVR5qFhES1Nw9WQ" style="width: 800px; height: 241px;"/></p><p>Digging slightly deeper, the p0f honeypots produce the most events.</p><p><img alt="" src="https://cdn.filestackcontent.com/ZkJnRACS4ifdOl6I0vQ0" style="width: 705px; height: 527px;"/></p><p>The table above shows events received by each distinct p0f honeypot. You’ll notice one p0f honeypot accounts for almost 11 million events alone — over 30% of all p0f events (there were 35.2 million p0f events in total).</p><h3>Honeypot Source IPs</h3><p>The source IP seen most across our honeypot network in January 2017 was 144.217.68.19 (almost 322,000 distinct events across 50+ honeypots). However, looking at individual attack data, 309,000 of these were against a single honeypot.</p><p><img alt="" src="https://cdn.filestackcontent.com/mLK8d0SHSwSxlSQ3ZVYd" style="width: 700px; height: 525px;"/></p><p>There are a number of internal IPs (10.x) in the top 20 shown below which are probably the result of local honeypot testing (note: a single internal IP is likely reporting data from a high number of distinct sources).</p><p><img alt="" src="https://cdn.filestackcontent.com/E7GDfncsT5e6a8XvvejC" style="width: 800px; height: 491px;"/></p><p>Digging deeper on the top IP, 144.217.68.19, in the <a href="https://ui.threatstream.com/">Threatstream platform</a> the IP is listed as an IOC by 4 threat feeds reported as a phishing IP, brute force IP, and a scanning IP (unsurprising it is reported as a scanning IP given number of events).</p><h2>Further reading</h2><p><a href="https://github.com/threatstream/mhn">The MHN documentation</a> is the perfect starting point if you’re interested in gaining access to the MHN Community data or want to learn more about how data sharing work.</p><h2>Exploring The Modern Honey Network</h2><p>This is the last in the series of Splunking the Modern Honey Network posts. <a href="https://www.anomali.com/blog/category/modern-honey-network">You can find them all, and all our previous MHN posts on the Anomali Blog</a>.</p>
FEATURED RESOURCES

Anomali Cyber Watch
Anomali Cyber Watch: LockBit 5.0, Chrome Zero-Day CVE-2026-2441, Infostealer Targets OpenClaw, and more
LockBit 5.0 Ransomware Targets Windows, Linux, and VMware ESXi in Active Campaigns. Google Patches Actively Exploited Chrome Zero-Day CVE-2026-2441. Infostealer Targets OpenClaw Configuration Files to Capture Credentials and User Context. And more...

Anomali Cyber Watch
Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more
Zero-Click Remote Code Execution Flaw Affects Claude Desktop Extensions. Threat Actors Exploit SolarWinds Web Help Desk Vulnerabilities to Deploy Velociraptor. Fake 7-Zip Site Distributes Trojanized Installer Converting Systems to Proxy Nodes. ZeroDayRAT Commercial Mobile Spyware Targets Android and iOS. And more..

Anomali Cyber Watch
Anomali Cyber Watch: Notepad++ Attack, RAT Uses Hugging Face, Microsoft Office Flaw and more
Notepad++ Supply Chain Attack Delivers Chrysalis Backdoor. Android RAT Uses Hugging Face Platform to Host Malicious Payloads. Fancy Bear Exploits Microsoft Office Flaw in Ukraine. Nitrogen Ransomware Decryptor Fails Due to Coding Error. And more...

