Using ThreatStream Indicators of Compromise with AWS GuardDuty
GuardDuty threat lists allow ThreatStream users to import known malicious IP addresses from the ThreatStream platform to generate findings of threats in their AWS account. Let me show you how.
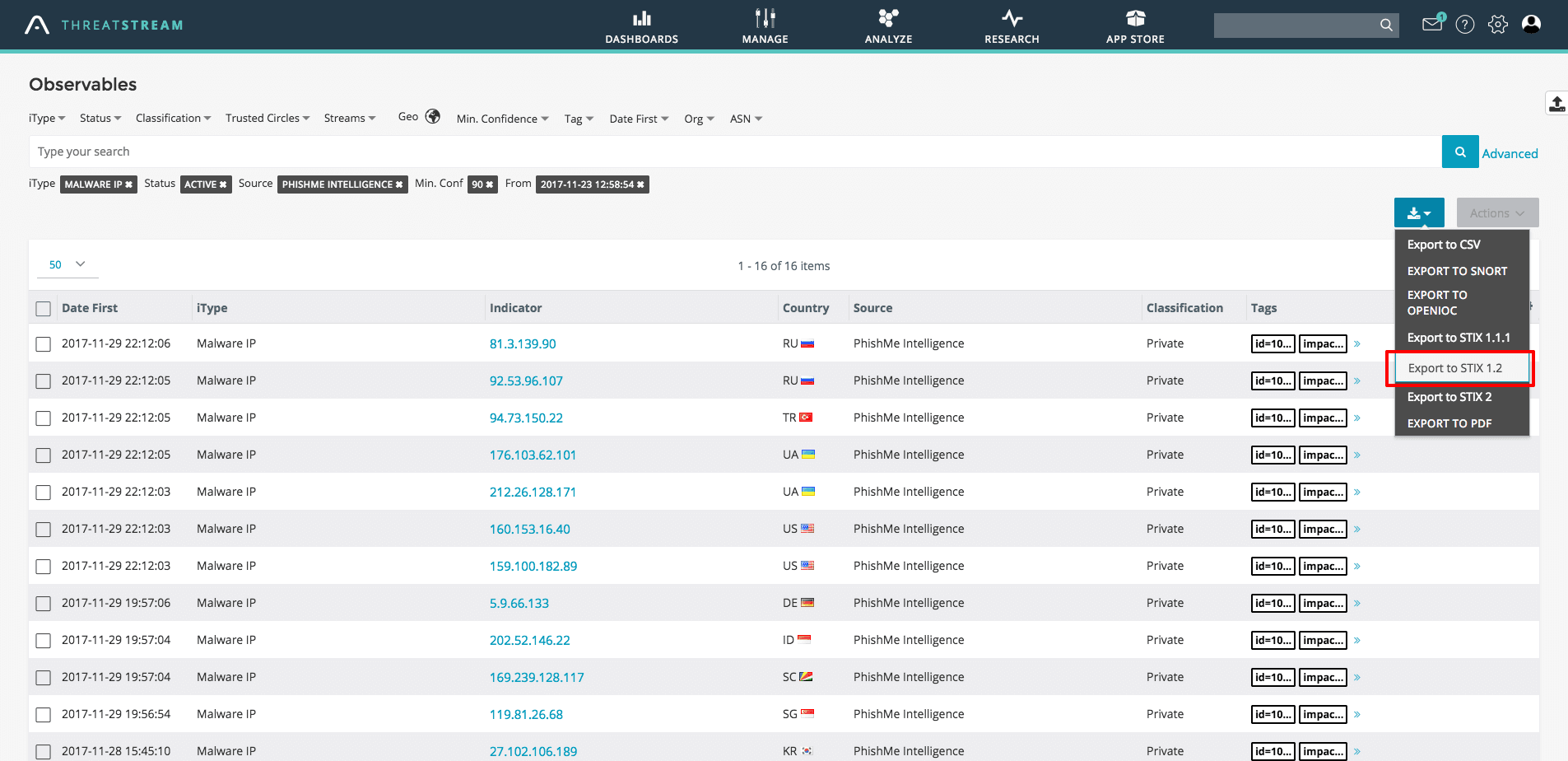

<p><a href="https://www.google.com/search?q=aws+reinvent&oq=aws+rei&aqs=chrome.0.69i59j69i57j0l4.1534j0j9&sourceid=chrome&ie=UTF-8">It has been a busy week for AWS at their re:Invent 2017 conference in Las Vegas</a>. <a href="https://aws.amazon.com/guardduty/">One of the new product launches that caught my eye yesterday was GuardDuty</a>, a managed threat detection service that continuously monitors for malicious or unauthorized behavior to help protect AWS accounts and workloads.</p><p>One way GuardDuty protects AWS environments is through the use of trusted IP lists and threat lists, the latter being particularly useful from a ThreatStream perspective. GuardDuty identifies suspected attackers by comparing threat lists against VPC Flow Logs, AWS CloudTrail event logs, and DNS logs in an AWS account. When a potential threat is detected, the service delivers a detailed security alert to the GuardDuty console and AWS CloudWatch Events. This makes alerts actionable and easy to integrate into existing event management and workflow systems.</p><p>GuardDuty threat lists allow ThreatStream users to import known malicious IP addresses from the ThreatStream platform to generate findings of threats in their AWS account. Let me show you how.</p><h2>Step One: Select and Export Indicators</h2><h2><img alt="" src="https://cdn.filestackcontent.com/80PB2nm8SXiE2CnTDqwd" style="width: 600px; height: 291px;"/></h2><p>Using ThreatStream's search functions it is possible to isolate specific indicators. For instance, you can use basic and advanced search operators to pick specific indicators based on information such as confidence, indicator type, ASN, or a specific tag. In the screenshot above I've used filters to limit the results to known malware IP's recently identified by PhishMe with a high confidence score. Currently GuardDuty only considers IP based indicators, therefore it is important to use a filter that only considers IP based indicator types.</p><p>After the results are returned you can export the results from ThreatStream. GuardDuty accepts either a simple list of IP's in a text file or structured IP lists in STIX 1.x format. As ThreatStream supports STIX 1.2 export, use this option.</p><h2>Step Two: Upload Indicators to S3</h2><h2><img alt="" src="https://cdn.filestackcontent.com/g7CvIpyuQeihE1weAf8O" style="width: 600px; height: 273px;"/></h2><p>Upload the downloaded XML file of indicators in STIX format to an S3 bucket in your AWS account. I created a new S3 bucket named "threatlists" to manage multiple threat list files. You might want to consider a static filename like "threatstream-indicators.xml" (versus the dynamic one created by the ThreatStream export) so that the S3 URL remains static if you append or modify the list of indicators within the file. <a href="http://docs.aws.amazon.com/guardduty/latest/ug/guardduty_upload_lists.html">Currently GuardDuty can support up to 6 threat lists</a>. As a result it makes sense to update a single file where possible. Make a note of the S3 URL as it will be required during step three.</p><h2>Step three: Add the Threat List to GuardDuty</h2><h2><img alt="" src="https://cdn.filestackcontent.com/dZhqxZWJTrqVbu6gn0im" style="width: 600px; height: 273px;"/></h2><p><a href="https://eu-west-1.console.aws.amazon.com/guardduty/home">Adding new threat lists can be done simply inside the GuardDuty console under "Lists"</a>. Creating a new threat list from the STIX file in the S3 bucket is simple; give the threat list an appropriate name, paste the S3 URL into the location field (why using a static URL is recommended), and select "Structured Threat Information Expression (STIX)" as the format.</p><p><img alt="" src="https://cdn.filestackcontent.com/LWssaYwwRUKGd2xzVxYN" style="width: 600px; height: 273px;"/></p><p>Once the threat list is added successfully, GuardDuty will begin using the contents of the file in the S3 bucket to compare against events in your AWS environment to deliver "findings" when a threat is observed.</p><h2>Anomali x AWS</h2><p>As GuardDuty grows you can expect to see much tighter integration with ThreatStream. If you're considering using GuardDuty alongside ThreatStream, or any Anomali products, please do send any questions you have my way via email: dgreenwood [-at-] anomali [-dot-] com</p>
FEATURED RESOURCES

Anomali Cyber Watch
When “Quiet" Means Pre-Positioned: Why Iranian Cyber Threats Are More Dangerous Than Headlines Suggest

Anomali Cyber Watch


