Weekly Threat Briefing: Vulnerabilities In mPOS Devices Could Lead To Fraud And Theft

The intelligence in this week’s iteration discuss the following threats: Backdoor, Banking trojan, Cryptominer, Data breach, Malvertising, Phishing, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Vulnerabilities In mPOS Devices Could Lead To Fraud And Theft (August 10, 2018)
Researchers with Positive Technologies uncovered several vulnerabilities in mobile point-of-sale (mPOS) machines that could allow threat actors to steal card data and defraud customers. These vulnerabilities affect mPOS devices including companies like PayPal, Square, SumUp, and iZettle. Since the mPOS uses Bluetooth data to the payment provider’s server, threat actors can intercept the transaction and manipulate the amount value. Threat actors can also authorize a different amount of money without the customer being aware. The devices are also vulnerable to remote code execution attacks where threat actors can then gain access to the entire operating system of the card reader. Threat actors can also send arbitrary code that could fraudulently inform a customer that a payment was declined so they make multiple payments or influence users to utilize more vulnerable payment methods like magstripe.
Click here for Anomali recommendation
AWS Employee Flub Exposes S3 Bucket Containing GoDaddy Server Configuration and Pricing Models (August 9, 2018)
Researchers at UpGuard Cyber Risk Team discovered a publicly accessible Amazon S3 bucket for the company GoDaddy that contained sensitive company information such as configurations for thousands of systems as well as documents with information regarding pricing. The breach was caused by an employee misconfiguring the AWS bucket while working with a customer. It appears this specific employee did not adhere to the best practices with this specific bucket. According to a GoDaddy spokesperson, the documents exposed in this breach were speculative models and did not actually reflect current work between Amazon and GoDaddy.
Click here for Anomali recommendation
Project:rosenbridge (August 9, 2018)
Project:rosenbridge on GitHub has revealed a hardware backdoor in desktop, laptop and embedded x86 processors. This backdoor allows ring 3 code, user space, to get around processor predictions to freely read and write ring 0 data, kernel space. While this backdoor can be closed, it is automatically enabled by default in certain systems. The rosenbridge backdoor is enabled by a model-specific-register control bit and then toggled with a launch instruction which can then feed commands formatted with x86 instructions. The core then executes these commands which bypasses all memory protections and privilege checks. This backdoor is more deeply embedded into the processor which grants it access to the CPU’s memory as well as its register file and execution pipeline. The backdoor affects VIA C3 CPUs like processors geared toward industrial automation, point-of-sale, ATMs, and healthcare hardware, on top of individual consumers desktops and laptops.
Click here for Anomali recommendation
"Hidden Bee" Miner Uses Malvertising To Lure Victims (August 8, 2018)
Security researchers at MalwareBytes found a malware that specifically targets a vulnerability in Flash Player to target victims from Asian countries. The attackers use malvertising on adult sites to redirect them to an exploit kit landing page to then install a cryptomining bot. This campaign does not use a standard PE file for the payload, and instead uses a multiple-stage custom executable format to download retrievable LUA scripts. The exploit kit uses encryptions and key exchanges with the backend server to be able to deploy their malware on the target’s machine. They utilise block Base64 that is encrypted with RC4 and Rabbit algorithms. Since the malware is encrypted, the threat actors use their own private RSA key to decrypt the server. It is noted that despite a reduction in threat actors employing exploit kits to conduct malware campaigns, some actors are still adapting them in order to continue to conduct similar attacks.
Click here for Anomali recommendation
Critical Security Flaws In OpenEMR Left 90 Million Medical Records Vulnerable (August 8, 2018)
Security researchers have found several vulnerabilities within the medical data software OpenEMR, which allowed for approximately 90 million medical records accessible to threat actors. Vulnerabilities such as portal authentication bypass, SQL injection instances, several instances of remote code execution, unauthenticated information disclosure, unrestricted file upload, unauthenticated administrative actions, and CSRF to RCE proof of concept were discovered in the software. In total, twenty different vulnerabilities were uncovered with eighteen of them being considered a high severity level. Once notified about these vulnerabilities, OpenEMR agreed to patch these bugs and then have the researchers publish their findings. This is not the first time this specific software company has had several security vulnerabilities. In 2017, they also had many bugs that could have allowed for data to be vulnerable to breaches.
Click here for Anomali recommendation
Salesforce API Error Left Data Accessible (August 7, 2018)
Due to an error in a marketing cloud API key, company Salesforce could have been victim to third parties accessing or corrupting their data. A code change during a Marketing Cloud release from June 4, 2018, until July 7, caused a small group of the REST API calls to improperly retrieve and overwrite data from one customer account to the next. While no malicious actions have been observed according to Salesforce, a security researcher at CipherCloud stated that the company has appeared to be unable to provide login data to show who had accessed the potentially compromised data and when. The breach had only been notified to individual customers via email by Salesforce.
Click here for Anomali recommendation
Bitcoin Stealer Malware Takes $60K Using Clipboard Modification Method (August 7, 2018)
Researchers at Fortiguard Labs have reported that there has been a new malware campaign that has been dubbed “Bitcoin Stealer”. It has already stolen approximately $60,000 in Bitcoin from various victims. This attack utilizes an executable that allows the threat actor to hijack the infected machine’s clipboard content to see if there is any sign of a Bitcoin address. If it finds a Bitcoin address, the “Bitcoin Stealer” replaces the address with a different address that contains similar strings at the beginning and end of the wallet address, which allows the malware to inject itself into the Bitcoin transactions and trick users into sending cryptocurrency to the threat actor’s wallet instead.
Click here for Anomali recommendation
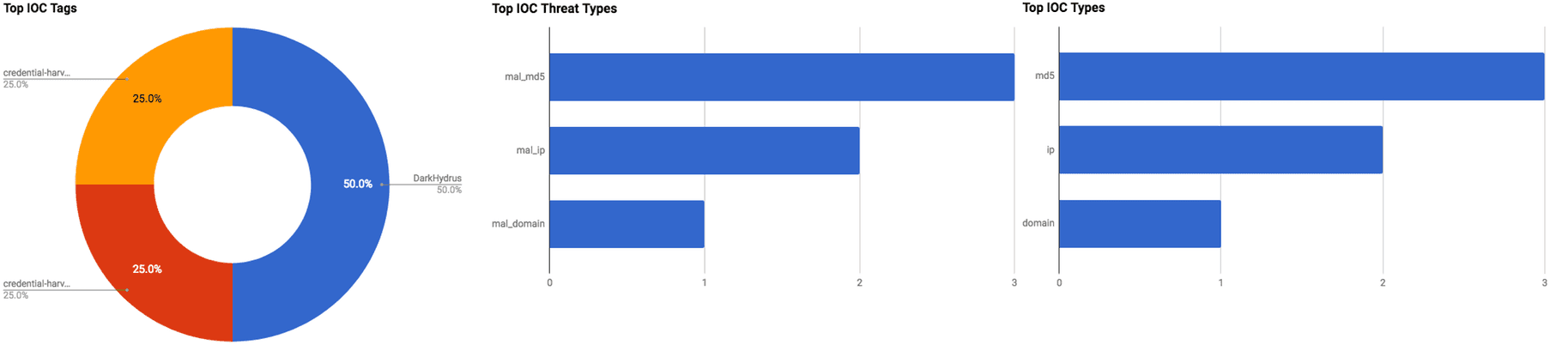
DarkHydrus Uses Phishery To Harvest Credentials In The Middle East (August 7, 2018)
A new threat group called “DarkHydrus” has been observed by security researchers at Palo Alto Networks to be engaging in a credential harvesting campaign on top of their known method of spearphishing to deliver PowerShell payload. This group has been observed to target government entities and educational institutions in the Middle East. This credential harvesting attack utilized phishing emails that contained a malicious Microsoft Office document with an “attachedTemplate” download request within it. If users clicked the template download within the document, they would be prompted with a login box asking for their credentials to proceed further. Those user credentials would then be sent to a command and control (C2) server where the threat actors could then obtain those credentials for future use. The group has been using the Phishery tool that is accessible via open-source networks which suggest to researchers that there may be more attacks by this group in the near future.
Click here for Anomali recommendation
BGP Hijacking Attacks Target US Payment Processors (August 7, 2018)
A Border Gateway Protocol (BGP) hijacking attack was discovered by company Oracle in mid-July. Threat actors would target authoritative DNS servers to create fake DNS responses that would go out to users attempting to access specific sites. The goal was to then redirect users to the threat actors site which could be a fake site with cryptominers embedded in it or a crypto-wallet setup to steal the victims’ money. The compromised DNS server would return those fake responses to the victim where the threat actor had set the time-to-live (TLL) value to approximately five days, in order to maximize the length of their attack. This allowed threat actors to hijack the website long after a user had initially accessed the malicious website. Oracle noted that the recent attacks had been against Vantiv, a US-based payment processing company, and organizations that utilized that vendor.
Click here for Anomali recommendation
New Method Simplifies Cracking WPA/WPA2 Passwords On 802.11 Networks (August 6, 2018)
A new technique to infiltrate WiFi routers has been uncovered by an independent security researcher that gains the Pairwise Master Key Identifier (PMKID) from a router using WPA/WPA2 security. This method simply requires a single frame which the threat actor can request from the AP since it is a regular part of the protocol. This new technique is effective on routers using 802.11i/p/q/r networks that have roaming enabled. This new technique extracts the Robust Security Network Information Element (RSN IE) from an Extensible Authentication Protocol over LAN (EAPOL) frame which allows the threat actor to then see the PKMID. This allows threat actors to hack into a WiFi router quicker since they would not have to wait for a user to associate with the access point to then obtain the four-way-handshake what is otherwise is required when bruteforcing they encryption key.
Click here for Anomali recommendation
Phishing Campaign Uses FTP Links To Deliver DanaBot Banking Trojan (August 6, 2018)
According to a report by Trustwave, threat actors have been launching a phishing campaign against Australian businesses using forged invoices from MYOB, a local accounting software company, in their emails. The email links, once clicked on, directed to a file transfer protocol (FTP) server that contained a version of the DanaBot malware. Threat actors could then use a command and control (C2) server to send data such as screenshots of infected machines covertly. Threat actors are especially targeting business employees in Australia, and utilize invoices since those are paid closer attention to by employees because of the potential ramifications of ignoring invoices.
Click here for Anomali recommendation
Ramnit Changes Shape With Widespread Black Botnet (August 6, 2018)
A recently discovered Black botnet campaign has been seen distributing the Ramnit malware. The campaign infected approximately 100,000 machines in the scope of two months through July 2018. Researchers at Check Point Research believe that this is just a precursor to a larger attack in the future. The Black botnet operation distributes the Ramnit malware through spamming users. Ramnit contains both information exfiltration capabilities, as well as backdoors infected machines. The backdoor specifically opens the compromised machine to another malware called Ngioweb which creates a multifunctional proxy server that uses its own binary with two layers of encryption. Researchers believe that these two malwares working together in this specific campaign could allow the threat actors the ability to create a large, multi-purpose proxy botnet that could have versatile uses to elicit an illegal profit and cause chaos on intended victims.
Click here for Anomali recommendation
Homebrew: Security Incident Disclosure (August 5, 2018)
A security researcher discovered on Jenkins a leaked personal access token with elevated permissions to Homebrew’s GitHub. This gave the researcher access to “git push” on Homebrew/brew and Homebrew/homebrew-core. Once Homebrew was notified of the leak, they revoked the credentials, replaced them within Jenkins, and re-secured the credentials so that they could not be leaked in the future. According to both GitHub and Homebrew, no packages were compromised and thus no action is required by users from this incident.
Click here for Anomali recommendation
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



