Anomali Unified Security Data Lake
Always-hot security telemetry enriched with threat intelligence and built to drive agentic workflows across detection, investigation, and response.
Why UNIFIED SECURITY DATA LAKE
Why UNIFIED SECURITY DATA LAKE
Why UNIFIED SECURITY DATA LAKE
300x Faster detection and investigation
Analysts pivot across years of data and intelligence in seconds.
96% Reduced time for threat investigations
Context-driven prioritization reduces false positives and alert fatigue.
50% analyst time saved with operationlized intel
Threat intel informs every stage of the SOC workflow, not just reports.
60% reduced siem bill and operational cost
Eliminate SIEM tax and manual effort while scaling data retention.
Built for Security Operations — Not Just Storage
Most data lakes are designed to retain logs. The Anomali Unified Security Data Lake is designed to operate security.
Complete, always accessible telemetry
across cloud, endpoint, network, identity, and applications.
Security-native normalization and correlation
not generic log indexing.
Native threat intelligence enrichment
applied at ingest and search time through native integration with ThreatStream Next-Gen.
Operational outputs
designed to support agentic AI workflows across detection, investigation, and response.
Capabilities
Always-On Security Data
Search years of telemetry at live-event speed — no cold storage, no delays, no blind spots.
Unified Operational Visibility
Correlate cloud, endpoint, network, identity, and application data into a single operational view, enriched with real-time threat intelligence.
Investigation-Ready at Scale
High-performance indexing and analytics support deep hunts, instant pivots, and sustained SOC operations.
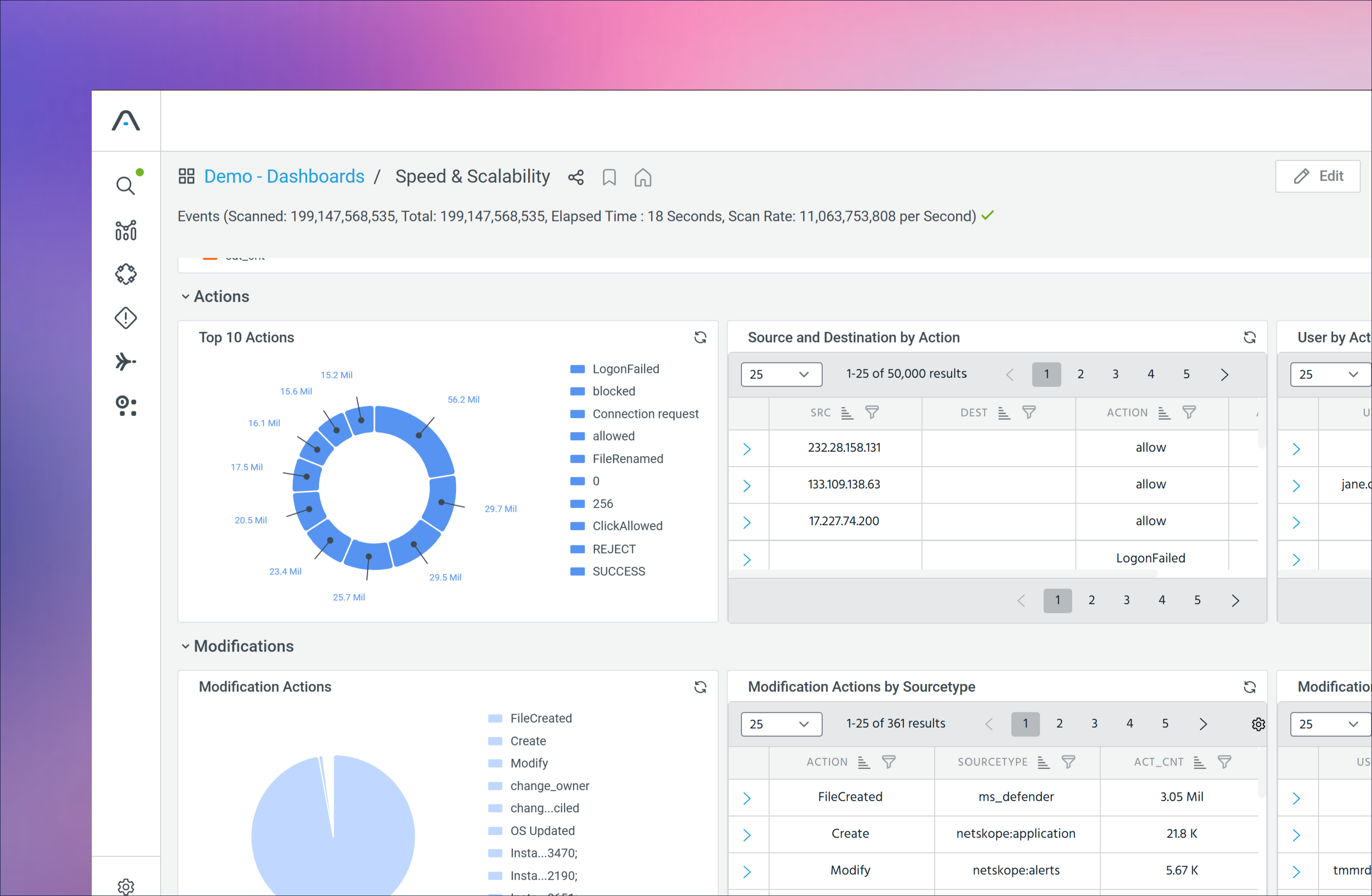
Built for Intelligent Automation
Clean, complete, contextual data ensures downstream analytics, automation, and AI workflows operate with accuracy and confidence.
No Tradeoffs. Choose Your Deployment.
Optimize existing SIEMs or replace them entirely without sacrificing performance, retention, or investigative depth.
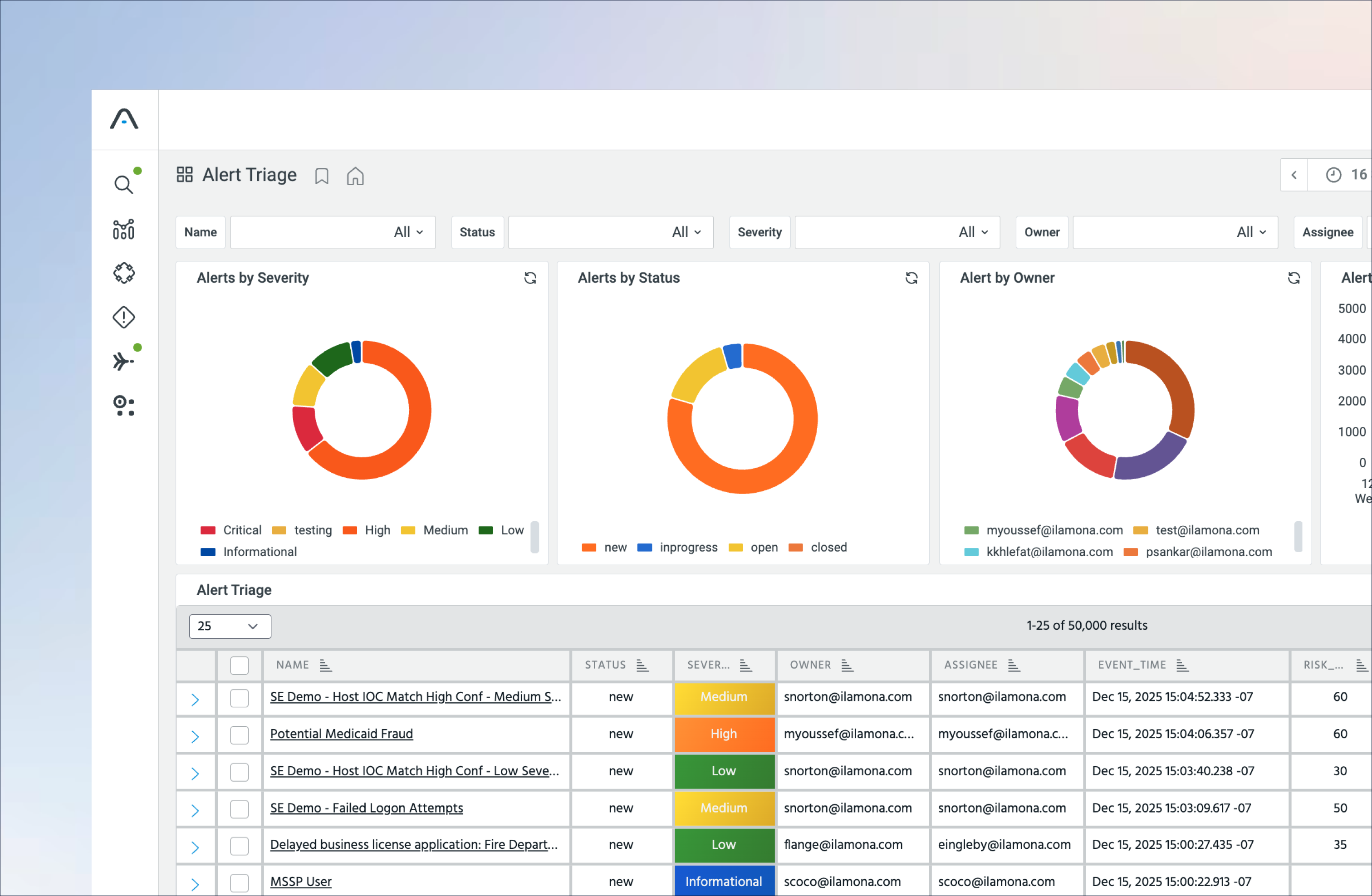
AI-Ready Insights Powered by Complete Data
Act faster, investigate smarter, and respond with confidence.
How it works
1. Ingest
Collect telemetry from cloud, endpoints, networks, identity systems, and applications.
2. Normalize and Enrich
Clean, enrich, and index every event for immediate correlation and investigation.
3. Search, Investigate, Respond
Enable fast investigations, analytics, and automated workflows using complete historical data.
TOP USE CASEs
Threat Hunting with Historical Clarity
Investigate across months or years of telemetry with full context and enriched intelligence.
Customer Proof
“Before Anomali, we had tons of information without context. We had to look through thousands of alerts quickly just to see what stood out and then react to those. Anomali enabled us to spend less time dealing with noise, and more time focusing on critical issues.”
- Devin Ertel, CISO, Blackhawk Network Holdings
The Data Foundation for Modern Security Operations
Retain more. Search faster. Investigate with confidence.