Anomali Cyber Watch: APT33 Employs New FalseFont Backdoor, Play Ransomware Impacted Around 300 Organizations, and More


The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Backdoors, Data breach, Infostealers, Iran, Malvertising, Phishing, Ransomware, Ukraine, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
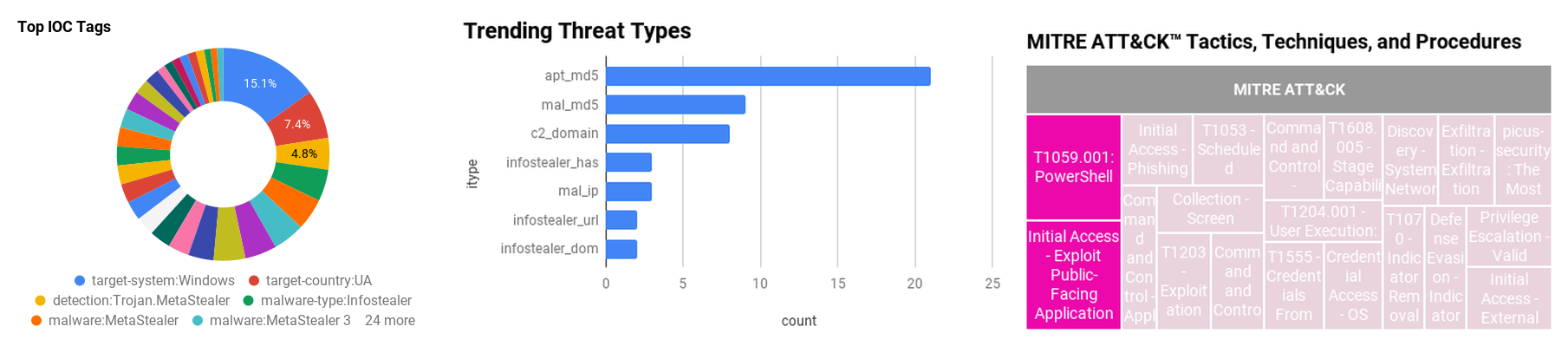
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Threat Actor 'UAC-0099' Continues to Target Ukraine
(published: December 21, 2023)
The threat actor UAC-0099 has been exploiting a high-severity flaw in WinRAR (CVE-2023-38831) to deliver the LonePage malware in attacks against Ukraine, as reported by Deep Instinct. When users expect to open a benign file from a ZIP attachment, they inadvertently execute malicious code from a specially-placed CMD file with a matching name. UAC-0099 began exploiting the vulnerability several days after the patch in August 2023, most likely creating its CMD files in an automated fashion. The group has been targeting Ukraine since mid-2022, including Ukrainian employees working for companies outside of Ukraine. In addition to ZIP files, the group uses various phishing attachments, including HTA and RAR SFX with LNK file attachments. Some phishing attacks involve the use of fabricated court summons to bait targets in Ukraine. After the first stage, the core infection remains the same — PowerShell and the creation of a scheduled task that executes the VBS malware dubbed LonePage.
Analyst Comment: The WinRAR exploitation is especially problematic as WinRAR requires a manual update. Users and network defenders need to ensure the use of the latest version of WinRAR. All known host-based indicators associated with this UAC-0099 campaign are available in the Anomali platform for retrospective analysis.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Phishing [T1566] | [MITRE ATT&CK] T1059.001: PowerShell | [MITRE ATT&CK] T1053 - Scheduled Task/Job | [MITRE ATT&CK] Command and Control - Application Layer Protocol: Web Protocols [T1071.001] | [MITRE ATT&CK] Collection - Screen Capture [T1113] | [MITRE ATT&CK] T1203 - Exploitation For Client Execution
Tags: actor:UAC-0099, vulnerability:CVE-2023-38831, target-software:WinRAR, malware:LonePage, target-country:UA, file-type:CMD, file-type:DOCX.LNK, file-type:HTA, file-type:LNK, file-type:SFX, file-type:VBS, file-type:ZIP, target-system:Windows
Peach Sandstorm Targets Defense Industrial Base with New FalseFont Backdoor
(published: December 21, 2023)
Microsoft researchers have detected the Iranian cyber-espionage group APT33 (Elfin, HOLMIUM, Peach Sandstorm, and Refined Kitten) using a newly developed backdoor malware named FalseFont to attack defense contractors globally. The FalseFont backdoor provides remote access to compromised systems, file execution, and file transfer to its command-and-control servers. Microsoft first observed this malware strain in the wild in early November 2023.
Analyst Comment: Throughout 2023, APT33 waged at least two campaigns affecting the defense industry. Network defenders are advised to reset credentials for targeted accounts, revoke session cookies, and secure accounts and endpoints using multi-factor authentication. Indicators associated with FalseFont are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] Command and Control - Standard Application Layer Protocol [T1071]
Tags: malware:FalseFont, malware-type:Backdoor, detection:Backdoor:MSIL/FalseFont.A!dha, actor:APT33, actor:Peach Sandstorm, actor:Refined Kitten, actor:HOLMIUM, target-industry:Defense Industrial Base, target-industry:Defense
New MetaStealer Malvertising Campaigns
(published: December 19, 2023)
The MetaStealer commodity infostealer has gained popularity since its release in March 2022. Primarily distributed through malspam and cracked software using stolen YouTube accounts, it has more recently appeared in malvertising campaigns. The latest campaign, detected by Malwarebytes researchers in November - December 2023, delivered MetaStealer 3.X via at least two different Google search ads for Notepad++ and AnyDesk. The campaign featured two infection chains, one with and one without an intermediary PowerShell script.
Analyst Comment: These malicious ads were reported and blocked, but the actors are expected to try a new way in. All known network indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1608.005 - Stage Capabilities: Link Target | [MITRE ATT&CK] T1204.001 - User Execution: Malicious Link | [MITRE ATT&CK] T1059.001: PowerShell | [MITRE ATT&CK] T1555 - Credentials From Password Stores
Tags: malware:MetaStealer, malware:MetaStealer 3, malware-type:Infostealer, detection:Trojan.MetaStealer, technique:Malvertising, technique:PowerShell, impersonated:AnyDesk, impersonated:Notepad++, open-port:1775, file-type:DLL, target-system:Windows
36 Million People Affected by Data Breach at Xfinity
(published: December 19, 2023)
Xfinity, a brand of Comcast Cable Communications, recently suffered a data breach where attackers gained access to 35.8 million customers' usernames and hashed passwords, potentially exposing other personal information. The attackers exploited the Citrix Bleed vulnerability (CVE-2023-4966), impacting NetScaler ADC and NetScaler Gateway appliances. The unauthorized access to Xfinity's internal systems occurred between October 16 and 19, 2023, within the narrow window between the announcement of the vulnerability and Xfinity's application of necessary mitigations. While Citrix Bleed is commonly associated with ransomware groups like LockBit and Medusa, it is unknown whether one of these groups was behind this specific attack.
Analyst Comment: Xfinity has notified customers and required them to reset their passwords. They also recommend enabling two-factor or multi-factor authentication. Organizations should adhere to vulnerability and patch management, particularly on systems and services exposed to the Internet. Consider system hardening, segmentation, monitor for registry changes, unauthorized RDP traffic, and enforce strong multifactor authentication (MFA) policies or passwordless sign-in methods.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190]
Tags: target-company:Comcast, target-company:Xfinity, vulnerability:Citrix Bleed, vulnerability:CVE-2023-4966, target-system:NetScaler ADC, target-system:NetScaler Gateway, incident-type:Data breach
#StopRansomware: Play Ransomware
(published: December 18, 2023)
The FBI, Cybersecurity and Infrastructure Security Agency (CISA), and the Australian Cyber Security Centre have provided details on the tactics, techniques, and procedures, along with indicators of compromise, used by the Play (Playcrypt) ransomware group. From June 2022 to October 2023, the group has impacted approximately 300 organizations, mainly businesses and critical infrastructure across North America, South America, and Europe. Play gains initial access through attacks on RDP and VPN infrastructure, exploiting valid accounts, and targeting public-facing applications, including known vulnerabilities in FortiOS (CVE-2018-13379 and CVE-2020-12812) and Microsoft Exchange (ProxyNotShell: CVE-2022-41040 and CVE-2022-41082). The group utilizes Cobalt Strike, SystemBC C2 frameworks, and the Plink tunneling tool. To evade detection, it employs GMER, IOBit, PowerTool, and PowerShell scripts targeting Microsoft Defender. Information gathering and credential theft involve tools like AdFind, Bloodhound, Mimikatz, and WinPEAS. The group follows a double-extortion model, encrypting systems after exfiltrating data, and exfiltrates stolen data using WinSCP. Final payloads are delivered via Group Policy Objects.
Analyst Comment: Network defenders should consider requiring multifactor authentication, maintaining offline backups of data, implementing a recovery plan, and keeping all operating systems, software, and firmware up to date. Host-based indicators associated with Play ransomware campaigns are available in the Anomali platform for ongoing infections and historical reference. In addition CISA Advisories, along with other Advisory, News and Blog sources are available as RSS feeds, and for AutoLens+ subscribers these are also tagged and summarized.
MITRE ATT&CK: [MITRE ATT&CK] Credential Access - OS Credential Dumping [T1003] | [MITRE ATT&CK] Discovery - System Network Configuration Discovery [T1016] | [MITRE ATT&CK] Exfiltration - Exfiltration Over Alternative Protocol [T1048] | [MITRE ATT&CK] picus-security: The Most Used ATT&CK Technique — T1059 Command and Scripting Interpreter | [MITRE ATT&CK] T1070 - Indicator Removal On Host | [MITRE ATT&CK] Defense Evasion - Indicator Removal: Clear Windows Event Logs [T1070.001] | [MITRE ATT&CK] Privilege Escalation - Valid Accounts [T1078] | [MITRE ATT&CK] Initial Access - External Remote Services [T1133] | [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] T1484 - Domain Policy Modification | [MITRE ATT&CK] T1484.001 - Domain Policy Modification: Group Policy Modification | [MITRE ATT&CK] T1486: Data Encrypted for Impact | [MITRE ATT&CK] T1518 - Software Discovery | [MITRE ATT&CK] Discovery - Software Discovery: Security Software Discovery [T1518.001] | [MITRE ATT&CK] T1552 - Unsecured Credentials | [MITRE ATT&CK] Collection - Archive Collected Data [T1560] | [MITRE ATT&CK] T1560.001 - Archive Collected Data: Archive Via Utility | [MITRE ATT&CK] T1562: Impair Defenses | [MITRE ATT&CK] T1562.001: Disable or Modify Tools | [MITRE ATT&CK] T1570 - Lateral Tool Transfer
Tags: malware:Play, malware-type:Ransomware, detection:Ransomware.Wins.PLAY, actor:Play ransomware, actor:Playcrypt, malware:Cobalt Strike, malware:SystemBC, target-system:FortiOS, vulnerability:CVE-2018-13379, vulnerability:CVE-2020-12812, target-software:Microsoft Exchange, vulnerability:ProxyNotShell, vulnerability:CVE-2022-41040, vulnerability:CVE-2022-41082, target-region:North America, target-region:South America, target-region:Europe, target-region:Australia, target-country:US, target-country:AU, target-system:Windows
FEATURED RESOURCES




