Anomali Cyber Watch: China-Sponsored Group Exploits Ivanti Devices, RE#TURGENCE Targets MSSQL Servers to Deliver MIMIC Ransomware, and More


The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, China, Cryptocurrency drainers, Infostealers, Turkey, Vulnerabilities, and Webshells. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
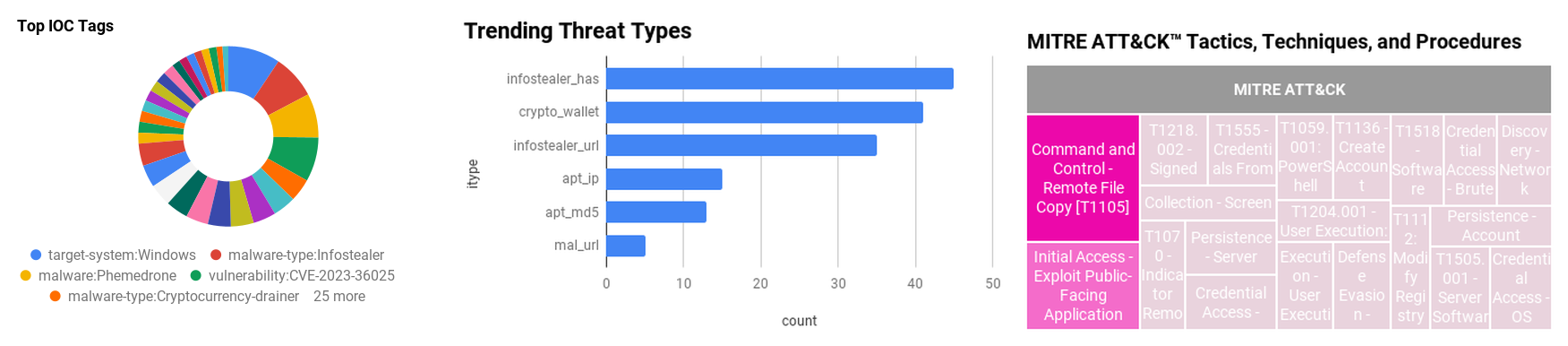
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
CVE-2023-36025 Exploited for Defense Evasion in Phemedrone Stealer Campaign
(published: January 12, 2024)
The Windows Defender SmartScreen Bypass vulnerability (CVE-2023-36025) was patched by Microsoft in November 2023, but an increasing number of campaigns have incorporated this vulnerability into their attack chains, facilitated by the circulation of demos and proof-of-concept codes on social media. Trend Micro researchers have documented its exploitation by the Phemedrone Stealer campaigns. This C#-based open-source infostealer targets web browsers, cryptocurrency wallets, and messaging apps, stealing data and sending it to the attackers via Telegram or their command-and-control server. CVE-2023-36025 allows threat actors to craft URL files that download and execute malicious scripts that bypass the Windows Defender SmartScreen warning and checks. Threat actors employ MITRE ATT&CK technique T1218.002, by abusing the Windows Control Panel process binary to execute DLL files masquerading as CPL files.
Analyst Comment: The existence of public proof-of-concept exploit code for CVE-2023-36025 on the web heightens the risk for organizations that have not updated their software. Evidence of in-the-wild exploitation led to the Cybersecurity and Infrastructure Security Agency (CISA) adding it to the Known Exploited Vulnerabilities list. Network defenders should apply the latest Windows security updates. All known indicators associated with this Phemedrone Stealer campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1218.002 - Signed Binary Proxy Execution: Control Panel | [MITRE ATT&CK] T1555 - Credentials From Password Stores | [MITRE ATT&CK] Collection - Screen Capture [T1113]
Tags: malware:Phemedrone, malware-type:Infostealer, vulnerability:CVE-2023-36025, abused:Telegram, language:C#, file-type:CPL, file-type:DLL, file-type:EXE, file-type:GIT, file-type:PDF, file-type:TXT, file-type:URL, file-type:ZIP, target-system:Windows
Active Exploitation of Two Zero-Day Vulnerabilities in Ivanti Connect Secure VPN
(published: January 10, 2024)
Volexity has discovered an active exploitation of two zero-day vulnerabilities in Ivanti Connect Secure VPN devices. An authentication-bypass vulnerability (CVE-2023-46805) was chained with a command-injection vulnerability (CVE-2024-21887) to achieve unauthenticated remote code execution. The attacker was found placing custom webshells (GLASSTOKEN, COMPLYSHELL) on multiple internal and external-facing web servers. Since at least early December 2023, the attacker has used the vulnerabilities to steal configuration data, modify existing files, download remote files, and reverse tunnel from the ICS VPN appliance via the publicly available PySoxy SOCKS5 proxy tool. Volexity attributes this activity to an unknown China-sponsored group, which it tracks under the alias UTA0178.
Analyst Comment: Organizations using Ivanti Connect Secure, Ivanti Policy Secure, and ZTA gateways should implement Ivanti’s recommended mitigations and check for a potential prior compromise using indicators and signatures (available in the Anomali platform). Implement security patches once available. As Ivanti is working to fix over two dozen different systems and versions, it promises to start issuing security patches on the week of January 22, 2024 and finish by February 19, 2024. In addition, Volexity, and other Advisory, News, and Blog sources are available as RSS feeds, and for AutoLens+ subscribers these are also tagged and summarized.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] T1070 - Indicator Removal On Host | [MITRE ATT&CK] Persistence - Server Software Component: Web Shell [T1505.003] | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] Credential Access - Input Capture: Keylogging [T1056.001] | [MITRE ATT&CK] T1059.001: PowerShell
Signatures: YARA Rules: Apt_webshell_pl_complyshell | Apt_webshell_aspx_glasstoken | Webshell_aspx_regeorg | Hacktool_py_pysoxy
Tags: actor:UTA0178, vulnerability:CVE-2023-46805, vulnerability-type:Authentication-bypass, vulnerability:CVE-2024-21887, vulnerability-type:Command-injection, source-country:CN, malware:GLASSTOKEN, malware:COMPLYSHELL, malware-type:Webshell, malware:PySoxy, malware-type:SOCKS5-proxy, file-type:CGI, target-system:Ivanti-Connect-Secure-VPN, target-system:Ivanti-Policy-Secure
Thousands of Sites with Popup Builder Compromised by Balada Injector
(published: January 10, 2024)
Balada Injector was first observed by researchers at Dr. Web and has been operating since 2017, compromising more than 17,000 WordPress sites. Sucuri researchers have detailed the latest Balada Injector campaign, initiated in mid-December 2023. The actors weaponized a stored cross-site scripting (XSS) vulnerability (CVE-2023-6000) just two days after the publication on the respective security patch in the Popup Builder plugin version 4.2.3. The actors gained administrator access to over 7,100 sites, allowing them to install arbitrary plugins and create rogue Administrator users. The ultimate goal of the campaign is to insert a malicious JavaScript file to take control of the website and facilitate malicious redirects.
Analyst Comment: WordPress site administrators should update themes and plugins to the latest version to defend against similar exploitation. Check the wp_users table and the wp-content/plugins/ folder directly to monitor for signs of malicious WordPress admins and plugins. All known network indicators associated with this Balada Injector campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] T1136 - Create Account
Tags: malware:Balada-Injector, target-software:Popup-Builder, vulnerability:CVE-2023-6000, vulnerability-type:Stored-XSS, technique:Redirect, abused:CloudFlare, target-system:WordPress
Hundreds of Thousands of Dollars Worth of Solana Cryptocurrency Assets Stolen in Recent CLINKSINK Drainer Campaigns
(published: January 10, 2024)
On January 3, 2024, Mandiant’s X (Twitter) social media account was compromised and used to distribute links to a cryptocurrency drainer phishing page. Working with X, Mandiant regained control of the account and, based on their investigation found no evidence of malicious activity on, or compromise of, any Mandiant or Google Cloud systems related to the compromise of the X account. Subsequent investigation by Mandiant researchers profiled the CLINKSINK drainer-as-a-service operation and its 35 affiliates. The attackers were able to access the Mandiant’s X account when it was not protected by a second factor authentication. CLINKSINK has used phishing social media posts that redirect to pages impersonating legitimate cryptocurrency resources, such as Phantom, DappRadar, and BONK. These pages were loading malicious CLINKSINK JavaScript drainer (Chick Drainer, Rainbow Drainer) code to facilitate a connection to victim wallets and the subsequent theft of funds. Since December 31, 2023, the main wallet, which receives CLINKSINK affiliate payments (ranging from 5 to 25% of the stolen amount), has accumulated over $180,000 USD worth of Solana (SOL) and underlying tokens.
Analyst Comment: CLINKSINK source code was likely leaked in December 2023 making the growth of the threat even more likely. Users are advised against participating in giveaway (airdrop) schemes and exposing their financial accounts online, as the risk outweighs the unlikely benefit. Organizations are advised to secure their social media and other exposed accounts with multi-factor authentication and a strong password. The available M_Utility_CLINKSINK_1 YARA rule can be used by threat hunting teams, but it needs additional testing before application in production environments and/or for blocking. In addition Mandiant Blog, along with other Advisory, News and Blog sources are available as RSS feeds, and for Anomali Copilot AutoLens+ subscribers these are also tagged and summarized.
MITRE ATT&CK: [MITRE ATT&CK] T1204.001 - User Execution: Malicious Link | [MITRE ATT&CK] Execution - User Execution [T1204] | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information [T1027] | [MITRE ATT&CK] T1518 - Software Discovery
Signatures: YARA Rule: M_Utility_CLINKSINK_1
Tags: actor:CLINKSINK, malware:Chick-Drainer, malware:Rainbow-Drainer, malware:CLINKSINK, malware-type:Cryptocurrency-drainer, actor:Rainbow, language:JavaScript, target-industry:Blockchain, target-industry:Cryptocurrency, impersonated:Phantom, impersonated:DappRadar, impersonated:BONK, target-software:Phantom-Desktop-Wallet, target-asset:Solana
New RE#TURGENCE Attack Campaign: Turkish Hackers Target MSSQL Servers to Deliver Domain-Wide MIMIC Ransomware
(published: January 9, 2024)
A sophisticated Turkey-based campaign, named RE#TURGENCE, has been discovered infiltrating Microsoft SQL (MSSQL) database servers across the United States, European Union, and Latin America. Securonix researchers analyzed a RE#TURGENCE incident, spanning from initial access to the deployment of Mimic ransomware, over the course of one month. The attackers exploit known critical vulnerabilities in MSSQL servers and use the enabled xp_cmdshell function to gain access and execute Windows Shell and obfuscated PowerShell scripts. The attackers deployed several additional tools, including AnyDesk, Cobalt Strike, Mimikatz, Sysinternals psexec, and The Advanced Port Scanner. The Mimic ransomware used in the attacks exploits the legitimate Everything app by VoidTools to locate and encrypt target files. The attackers also sell access to the compromised servers that were deemed not worthy of ransomware.
Analyst Comment: Organizations should monitor their database servers and ensure that enhanced telemetry is available to detect and prevent such attacks. Secure basic configurations and limit usage or disable the xp_cmdshell procedure to protect themselves (typically, it is disabled by default). All known network indicators associated with this campaign are available in the Anomali platform, and customers are advised to block them on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Credential Access - Brute Force [T1110] | [MITRE ATT&CK] Discovery - Network Service Discovery[T1046] | [MITRE ATT&CK] T1112: Modify Registry | [MITRE ATT&CK] Persistence - Account Manipulation [T1098] | [MITRE ATT&CK] T1505.001 - Server Software Component: Sql Stored Procedures | [MITRE ATT&CK] Credential Access - OS Credential Dumping [T1003] | [MITRE ATT&CK] T1110.001 - Brute Force: Password Guessing | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] T1572 - Protocol Tunneling | [MITRE ATT&CK] T1573.001 - Encrypted Channel: Symmetric Cryptography | [MITRE ATT&CK] Command and Control - Remote Access Software [T1219] | [MITRE ATT&CK] T1486: Data Encrypted for Impact | [MITRE ATT&CK] Execution - Command and Scripting Interpreter: Windows Command Shell [T1059.003]
Tags: campaign:RE#TURGENCE, malware:MIMIC, malware-type:Ransomware, malware:Cobalt-Strike, abused:AnyDesk, abused:Advanced-Port-Scanner, abused:Everything, abused:psexec, malware:Mimikatz, source-country:TR, target-country:US, target-region:European-Union, target-region:Latin-America, target-region:LATAM, target-system:MSSQL-server, technique:PowerShell, target-system:Windows
FEATURED RESOURCES




