Anomali Cyber Watch: China-Sponsored UNC3886 Had Zero-Day Access to VMWare ESXi Hosts, ColdRiver Authored First Custom Backdoor, and More


The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Backdoors, China, Data leak, Infostealers, Password spraying, Phishing, Pirated software, Russia, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
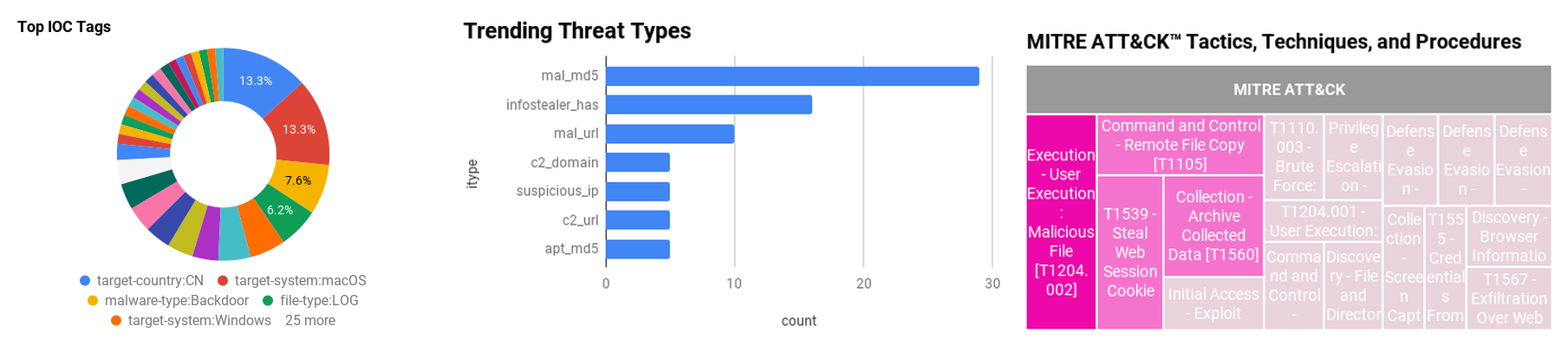
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Chinese Espionage Group UNC3886 Found Exploiting CVE-2023-34048 Since Late 2021
(published: January 19, 2024)
The China-sponsored group UNC3886 has been exploiting a critical vCenter Server vulnerability (CVE-2023-34048) as a zero-day since late 2021, as discovered by Mandiant researchers. While the vulnerability was patched in October 2023, the group had exploited it for approximately a year and a half. The group used this vulnerability to breach vCenter servers and deploy backdoors on ESXi hosts. Additionally, they exploited another VMware Tools authentication bypass vulnerability (CVE-2023-20867) to escalate privileges, harvest files, and exfiltrate them from guest VMs. The group primarily targets organizations in the defense, government, telecom, and technology sectors in the United States and the Asia–Pacific region.
Analyst Comment: UNC3886 continues to demonstrate advanced capabilities similar to its past reverse-engineering of various FortiOS parts. VMware users are advised to update to the latest version of vCenter.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105]
Tags: actor:UNC3886, vulnerability:CVE-2023-34048, vulnerability:CVE-2023-20867, malware:VIRTUALPITA, malware:VIRTUALPIE, malware-type:Backdoor, source-country:CN, target-software:vCenter Server, target-system:ESXi
Microsoft Actions Following Attack by Nation State Actor Midnight Blizzard
(published: January 19, 2024)
Microsoft has reported a breach of its corporate email accounts by a Russian state-sponsored hacking group known as Midnight Blizzard (APT29, Cozy Bear, and Nobelium). The breach was detected on January 12th, 2024, but the initial attack occurred in November 2023. Midnight Blizzard used a password spray attack to access a legacy non-production test tenant account, which was not protected with two-factor or multi-factor authentication. The actors then used this account to access a small percentage of Microsoft's corporate email accounts for over a month. The breached accounts included members of Microsoft's leadership team and employees in the cybersecurity and legal departments. The group specifically targeted email accounts for information related to Midnight Blizzard itself. Microsoft is still investigating the breach and has stated that it has not had a material impact on the company's operations.
Analyst Comment: Defense-in-depth is the best way to ensure safety from APTs. Defense-in-depth involves the layering of defense mechanisms. This can include network and endpoint security, social engineering training (such as training exercises to help detect phishing emails) for staff and robust threat intelligence capabilities. Network defenders should disable unused accounts and make sure user account controls are restricted on a need-to-access basis.
MITRE ATT&CK: [MITRE ATT&CK] T1110.003 - Brute Force: Password Spraying | [MITRE ATT&CK] Privilege Escalation - Valid Accounts [T1078]
Tags: actor:Cozy Bear, actor:Midnight Blizzard, actor:APT29, actor:Nobelium, source-country:RU, technique:Brute-force, technique:Password-spraying, target-company:Microsoft
Russian Threat Group COLDRIVER Expands Its Targeting of Western Officials to Include the Use of Malware
(published: January 18, 2024)
The Russia-sponsored ColdRiver (BlueCharlie, Callisto, SEABORGIUM, and Star Blizzard) group has been mostly focused on credential phishing activities against Ukraine, NATO countries, academic institutions and NGOs. Google researchers have identified its first custom malware dubbed SPICA. This Rust-based backdoor has been used since at least November 2022. The social engineering technique to deliver SPICA includes phishing emails with PDF documents that appear to be encrypted. When recipients reply that they cannot read the documents, they are sent a link to download a supposed PDF decryptor, which is actually a backdoor malware. The malware allows the hackers to run arbitrary shell commands, steal browser cookies, upload and download files, and exfiltrate documents.
Analyst Comment: Potentially-targeted users are encouraged to enable enhanced safety settings for their browsers and ensure that all devices are updated. Do not automatically trust prompts to download additional software such as “decryptors.” As with all unexpected/solicited email or other communications, users should independently verify the sender, the message and the attachment. All known network indicators associated with this campaign are available in the Anomali platform, and customers are advised to block them on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1204.001 - User Execution: Malicious Link | [MITRE ATT&CK] Execution - User Execution: Malicious File [T1204.002] | [MITRE ATT&CK] Command and Control - Application Layer Protocol: Web Protocols [T1071.001] | [MITRE ATT&CK] T1539 - Steal Web Session Cookie | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] Collection - Archive Collected Data [T1560] | [MITRE ATT&CK] Discovery - File and Directory Discovery [T1083]
Tags: malware:SPICA, malware-type:Backdoor, actor:COLDRIVER, actor:UNC4057, actor:Star Blizzard, actor:Callisto, actor:TA446, actor:TAG-53, actor:BlueCharlie, source-country:RU, target-country:UA, target-organization:NATO, target-industry:Defense, target-industry:NGO, language:Rust, open-port:3000, file-type:EXE, file-type:PDF, file-type:ZIP, target-system:Windows
New Malware Embedded in Pirated Applications
(published: January 18, 2024)
Jamf researchers have discovered a stealthy macOS backdoor hidden in trojanized applications hosted on Chinese websites. The malware uses hidden files, obfuscation, and system file names. Each pirated application has a malicious library loaded by the application that acts as a dropper. It downloads a custom backdoor based on the Khepri open-source malware. Another binary downloaded by the malicious library acts as a persistent downloader. The targeting, modified load commands and attacker infrastructure is similar to the ZuRu malware originally discovered in 2021, but additional research is needed for precise attribution.
Analyst Comment: The campaign demonstrates the existing risk for the macOS platform from pirated applications and the increased frequency of attackers using a malicious library placed within a modified application to compromise users. Enterprises and users should avoid the assumption that all Macs are inherently safe and should use software that both detects and blocks threats on macOS. Educate your users on only using trustworthy and verified sources for applications. All known network indicators associated with this campaign are available in the Anomali platform, and customers are advised to block them on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Execution - User Execution: Malicious File [T1204.002] | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information [T1027] | [MITRE ATT&CK] Defense Evasion - Deobfuscate/Decode Files or Information [T1140] | [MITRE ATT&CK] Defense Evasion - Masquerading [T1036]
Tags: malware:ZuRu, malware:Khepri, malware-type:Backdoor, malware-type:Downloader, malware-type:Dropper, target-country:CN, target-region:Hong-Kong, file-type:DYLIB, file-type:LOG, file-type:Mach-O, target-system:macOS
JAVA-Based Sophisticated Stealer Using Discord Bot as EventListener
(published: January 18, 2024)
Trellix researchers have discovered a new Java-based malware, NS-STEALER. Since at least mid-November 2023, this infostealer has been spread via ZIP archives disguised as cracked software. Once deployed, it saves screenshots, cookies, credentials, and autofill data stolen from over two dozen web browsers. It also collects system information, a list of installed programs, Discord tokens, and Steam and Telegram session data. The stolen information is then sent to a Discord Bot channel. The malware is highly sophisticated and can quickly steal information from systems with Java Runtime Environment.
Analyst Comment: Given its capabilities, NS-STEALER has the potential to become a more significant threat in the future. As long as individuals continue to download cracked software, threat actors will continue using it as a distribution method. Your company should restrict these types of downloads, supply legitimate software, and educate your employees about these risks. All known network indicators associated with this campaign are available in the Anomali platform, and customers are advised to block them on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Execution - User Execution: Malicious File [T1204.002] | [MITRE ATT&CK] Collection - Screen Capture [T1113] | [MITRE ATT&CK] T1539 - Steal Web Session Cookie | [MITRE ATT&CK] T1555 - Credentials From Password Stores | [MITRE ATT&CK] Discovery - Browser Information Discovery [T1217] | [MITRE ATT&CK] Collection - Archive Collected Data [T1560] | [MITRE ATT&CK] T1567 - Exfiltration Over Web Service
Tags: malware:NS-STEALER, detection:Malware.Binary.jar, malware-type:Infostealer, abused:Discord, language:Java, file-type:JAR, file-type:ZIP, target-system:Windows
FEATURED RESOURCES




