Anomali Cyber Watch: Infostealers Target Google Oauth MultiLogin Endpoint, Kimsuky Adopts Chrome Remote Desktop C2 Communication, and More


The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Data destruction, Cookie regeneration, North Korea, Russia, Ukraine, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
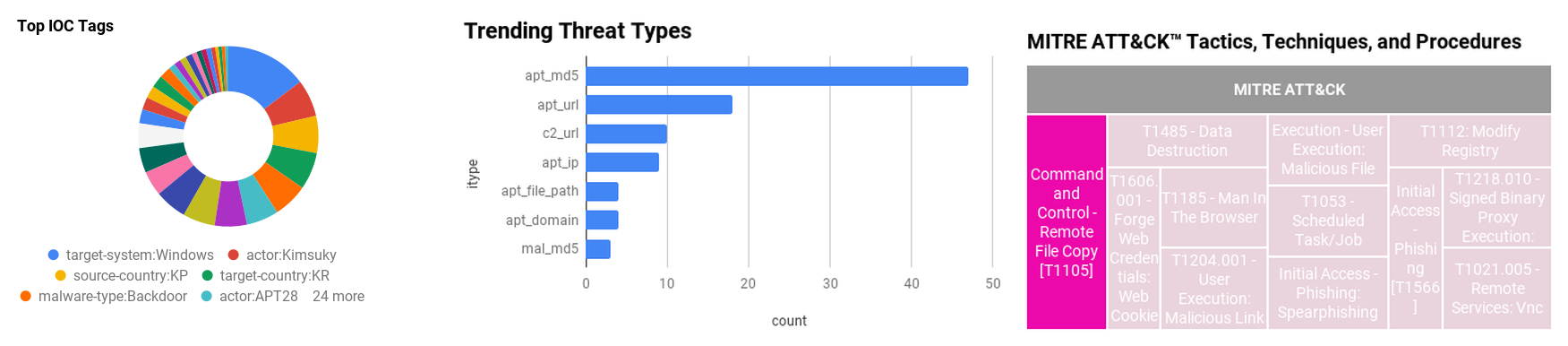
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Russian Hackers Wiped Thousands of Systems in KyivStar Attack
(published: January 4, 2024)
The Security Service of Ukraine has reported that Russia-sponsored Sandworm group was behind the December 2023 cyberattack on Kyivstar, Ukraine's largest telecommunications service provider. The actors had breached Kyivstar's network in May 2023, got the full access no later than November 2023, and launched the data destruction attack in December 2023. The group used unidentified tools to wipe all systems on the telecom operator's core network, causing a significant disruption to the country's civilian population. Sandworm-controlled Telegram persona Solntsepek took the responsibility for the attack claiming that they wiped 10,000 computers and thousands of servers on Kyivstar's network.
Analyst Comment: This attack is a continuation of Sandworm targeting Ukrainian telecom such as prior breaching of 11 Ukrainian telecommunications service providers since May 2023. A defense in depth approach can assist in creating a proactive stance against threat actors attempting to destroy data. Critical systems should be segregated from each other to minimize potential damage, with any attack surfaces closely monitored for malicious activity. A strong and enforced backup policy will assist in a fast recovery of compromised systems.
MITRE ATT&CK: [MITRE ATT&CK] T1485 - Data Destruction
Tags: actor:Sandworm, actor:Solntsepek, source-country:RU, target-country:UA, technique:Data-destruction, target-company:Kyivstar
Compromising Google Accounts: Malwares Exploiting Undocumented OAuth2 Functionality for Session Hijacking
(published: December 29, 2023)
CloudSEK researchers discovered a critical exploit affecting an undocumented Google Oauth endpoint named "MultiLogin". This exploit allows threat actors to continuously generate Google cookies, ensuring persistent access to Google services even after a user changes their password. The exploit was first released by a developer/threat actor PRISMA on a Telegram channel in October 2023. From November to December 2023, it was integrated by a significant number of commodity infostealers: Lumma, Meduza, Rhadamanthys, RisePro, Stealc, and WhiteSnake. Lumma Infostealer's approach involves manipulating the token:GAIA ID pair, a critical component in Google’s authentication process, and using SOCKS proxies to circumvent Google’s IP-based restrictions on cookie regeneration.
Analyst Comment: As threat actors strive to develop new ways to ensure persistence and continuous access to compromised systems and accounts. As commodity infostealers are delivered by varying sets of techniques it is important to keep your systems updated and stay vigilant to social engineering.
MITRE ATT&CK: [MITRE ATT&CK] T1606.001 - Forge Web Credentials: Web Cookies | [MITRE ATT&CK] T1185 - Man In The Browser
Tags: technique:Forge-Web-Credentials:Web-Cookies, technique:Session-hijacking, technique:Cookie-regeneration, target-software:Google-OAuth2-MultiLogin, malware:Lumma, malware:Rhadamanthys, malware:Stealc, malware:Meduza, malware:RisePro, malware:WhiteSnake, malware-type:Infostealer, actor:PRISMA
GootLoader Infection
(published: December 29, 2023)
Active since late 2020, GootLoader is a first-stage downloader and a multi-payload malware platform available on an access-as-a-service basis. On December 29, 2023, Malware Traffic Analysis revealed the infection chain for a new GootLoader incident that involved Google Search SEO and a fake forum page. A visitor is prompted to download a ZIP archive containing the malicious JavaScript file. The actor actively used suggestive file names for mimicking and enticing user actions. GootLoader used scheduled task as a persistence method.
Analyst Comment: Users should be taught to be cautious with downloading archives, executable files and scripts from the Internet. GootLoader infection can lead to a variety of threats including ransomware. All known network indicators associated with this incident are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1204.001 - User Execution: Malicious Link | [MITRE ATT&CK] Execution - User Execution: Malicious File [T1204.002] | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] T1053 - Scheduled Task/Job
Tags: malware:GootLoader, malware-type:Downloader, technique:Scheduled-task, file-type:JS, file-type:ZIP, target-system:Windows
APT28: From Initial Access to Attacking a Domain Controller in an Hour
(published: December 28, 2023)
The Ukrainian Computer Emergency Response Team has detected a new phishing campaign linked to the Russia-sponsored Fancy Bear (APT28) group. The campaign, which took place between December 15 and 25, 2023, used phishing emails to encourage recipients to click on a link, which then redirected them to malicious web resources. These resources used JavaScript to drop a Windows shortcut file that triggered an infection chain for a new Python malware downloader called MASEPIE. The malware modifies the Windows Registry and adds a deceptively named file to the Windows Startup folder, establishing persistence on the infected device. The attack also used a set of PowerShell scripts named STEELHOOK to steal data from Chrome-based web browsers, and a C#-based backdoor dubbed OCEANMAP.
Analyst Comment: Users should use caution when receiving unsolicited documents: examine domain and file names, detect and avoid files with double extensions such as .PDF.LNK (extensions could be separated by multiple spaces). Indicators associated with this Fancy Bear campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Phishing: Spearphishing Link [T1566.002] | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] T1112: Modify Registry
Tags: actor:Fancy-Bear, actor:APT28, malware:MASEPIE, malware-type:Downloader, malware:STEELHOOK, malware-type:Infostealer, malware:OCEANMAP, malware-type:Backdoor, source-country:RU, target-country:UA, file-type:EXE, file-type:LNK, file-type:PDF.LNK, file-type:PS1, file-type:TXT, target-system:Windows
Trend Analysis on Kimsuky Group’s Attacks Using AppleSeed
(published: December 28, 2023)
Active since 2013, North Korea-sponsored Kimsuky group has been targeting entities in South Korea before expanding its focus to other regions in 2017. The group has been using spearphishing attacks to deliver AppleSeed and a modified Meterpreter backdoors, and VNS tools such as TightVNC and TinyNuke. Since 2021, Kimsuky has used multiple versions of their custom AppleSeed backdoors, adding new features in 2022-2023. Kimsuky has adopted a newer AppleSeed version dubbed AlphaSeed, started using a dedicated dropper to install it, added an argument check for the installation via the Regsvr32 process, and switched from RDP to Chrome Remote Desktop C2 communication.
Analyst Comment: Defense-in-depth (layering of security mechanisms, redundancy, fail-safe defense processes) is the best way to ensure safety from APTs, including a focus on both network and host-based security. All employees should be educated on the risks of spearphishing and how to identify such attempts. All known indicators associated with the latest Kimsuky campaigns are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Phishing [T1566] | [MITRE ATT&CK] T1218.010 - Signed Binary Proxy Execution: Regsvr32 | [MITRE ATT&CK] T1021.005 - Remote Services: Vnc
Tags: actor:Kimsuky, malware:AppleSeed, malware-type:Backdoor, detection:Backdoor/Win.AppleSeed, malware:AlphaSeed, detection:Backdoor/Win.AlphaSeed, malware:Meterpreter, malware:TinyNuke, detection:Trojan/Win.VNC, detection:Trojan/Win.TinyNuke, source-country:KP, target-country:KR, abused:Chrome-Remote-Desktop, language:C++, language:Golang, file-type:DAT, file-type:DB, file-type:DLL, file-type:GO, target-system:Windows
FEATURED RESOURCES




