Anomali Cyber Watch: Iran-Linked Cyber Av3ngers Target US Water Utility, Gaza Cybergang Ports SysJoker to Rust, and More


The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Backdoors, Fake browser updates, Hamas, Infostealers, Iran, Malvertising, North Korea, and Remote access trojans. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
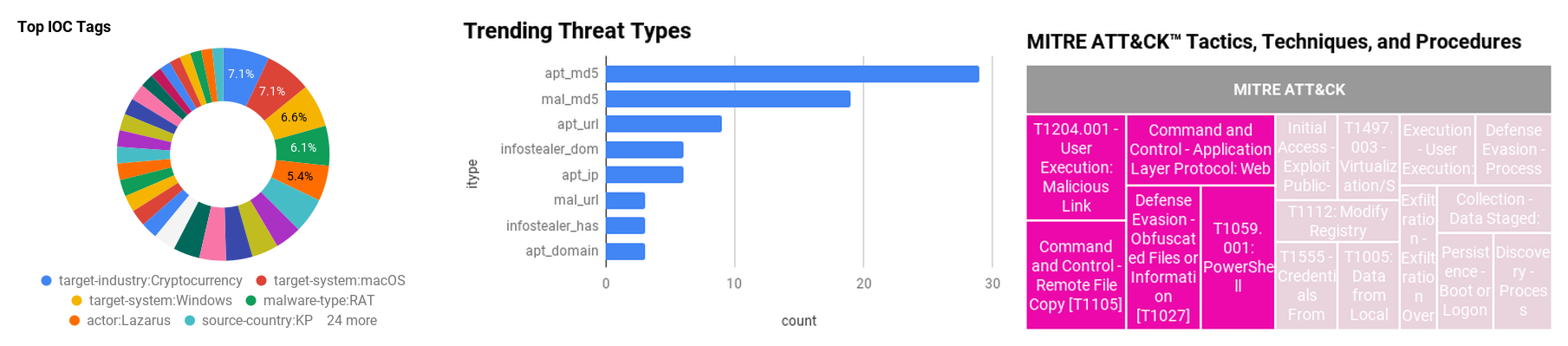
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
DPRK Crypto Theft | macOS RustBucket Droppers Pivot to Deliver KandyKorn Payloads
(published: November 27, 2023)
In 2023, North Korean-sponsored threat actors engaged in two significant cyber campaigns, RustBucket and KandyKorn, both targeting macOS systems. The multi-stage RustBucket campaign featured the use of SwiftLoader, a second-stage malware posing as a PDF Viewer within lure documents. Meanwhile, the five-stage KandyKorn campaign focused on blockchain engineers of a crypto exchange platform, employing Python scripts to deploy malware that seized control of the host's Discord app. Notably, in November 2023, SentinelOne researchers observed a fusion of elements from both campaigns, where SwiftLoader droppers were used to deliver the KANDYKORN RAT.
Analyst Comment: The cyber landscape in North Korea appears to have evolved into a more streamlined organization with shared tools and targeting strategies. For organizations in finance, blockchain, or those more likely to be targeted by government-sponsored attackers, implementing a defense-in-depth approach is crucial. Non-Windows users should remain vigilant against emerging malware threats. All known indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1204.001 - User Execution: Malicious Link | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] Command and Control - Application Layer Protocol: Web Protocols [T1071.001] | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information [T1027]
Tags: campaign:RustBucket, malware-type:Dropper, malware:SwiftLoader, malware:KandyKorn, malware-type:RAT, malware:SUGARLOADER, malware:HLOADER, malware:ObjCShell, source-country:KP, actor:Lazarus, actor:BlueNoroff, target-industry:Cryptocurrency, file-type:LOG, file-type:LOCK, file-type:Mach-O, file-type:TMP, file-type:ZIP, target-system:macOS
Hackers Hijack Industrial Control System at US Water Utility
(published: November 27, 2023)
The Municipal Water Authority of Aliquippa in Pennsylvania confirmed that threat actors took control of a system associated with a booster station that monitors and regulates water pressure. An Iran-linked hacktivist group, Cyber Av3ngers, has claimed responsibility for the attack. The group appears to have targeted an industrial control system (ICS) made by Israeli company Unitronics. Unitronics Vision programmable logic controllers (PLCs) with an integrated human-machine interface have been known to be affected by critical vulnerabilities. Cyber Av3ngers have been targeting the water supply industry before, but the group is known to exaggerate the impact of their attacks.
Analyst Comment: The intrusion was quickly detected and the compromised system was disabled. Cyberattacks on the water sector and industrial control systems are not uncommon, so it is important to have detection and response capabilities in place. Network defenders should not rely on obscurity of their ICS/PLC/OT systems and implement necessary patch and network segmentation management.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190]
Tags: target-country:US, source-country:IR, actor:Cyber Av3ngers, target-system:Unitronics Vision, target-system:PLC, target-sector:Critical infrastructure, target-industry:Water supply
Israel-Hamas War Spotlight: Shaking the Rust off SysJoker
(published: November 23, 2023)
The SysJoker malware, linked to a Hamas-affiliated threat actor Gaza Cybergang (Molerats), has undergone significant changes. It has shifted from C++ to the Rust programming language and started using OneDrive instead of Google Drive for storing dynamic C2 URLs. Check Point researchers were able to connect the malware to targeted attacks during the Israel-Hamas conflict. Additionally in the past, a number of SysJoker tactics, techniques, and procedures (TTPs) were observed during Operation Electric Powder, a series of attacks against Israeli organizations between 2016-2017. Both campaigns used API-themed URLs and implemented PowerShell script commands in a similar fashion including the Run registry value manipulation.
Analyst Comment: Behavior detection is important for targeted, evolving threats like SysJoker. Network defenders should have advanced logging and detection capabilities for Windows Command Line and PowerShell events, as well as for Run registry modifications. Indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1497.003 - Virtualization/Sandbox Evasion: Time Based Evasion | [MITRE ATT&CK] T1112: Modify Registry | [MITRE ATT&CK] T1059.001: PowerShell | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105]
Tags: malware:SysJoker, malware-type:Backdoor, actor-identity:Hamas, target-country:IL, operation:Electric Powder, actor:Gaza Cybergang, actor:Molerats, detection:Backdoor.Wins.Sysjoker.ta, detection:Backdoor.Win.SysJoker.H, detection:Backdoor.WIN32.SysJoker, abused:OneDrive, language:C++, language:Rust, file-type:EXE, target-system:Windows
Atomic Stealer Distributed to Mac Users via Fake Browser Updates
(published: November 21, 2023)
In September 2023, Atomic Stealer (AMOS), a popular stealer for macOS, was spreading via malvertising. In November 2023, the delivery switched to a fake browser update chain known as 'ClearFake'. This is a significant development as it marks the first time a major social engineering campaign, previously reserved for Windows, has branched out to macOS. The malware is distributed through compromised websites and steals credentials and files that can be monetized or used for further attacks.
Analyst Comment: Mac users should remain vigilant and employ web protection tools to thwart the malicious infrastructure linked to this threat actor. It is crucial for users to verify the domain address before undertaking high-impact activities, such as downloading a browser update (ensure use of official update channels!). All identified indicators associated with this campaign can be found in the Anomali platform, and customers are recommended to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1204.001 - User Execution: Malicious Link | [MITRE ATT&CK] T1555 - Credentials From Password Stores | [MITRE ATT&CK] T1005: Data from Local System | [MITRE ATT&CK] Command and Control - Application Layer Protocol: Web Protocols [T1071.001]
Tags: malware:Atomic Stealer, malware:AMOS, malware-type:Infostealer, target-industry:Cryptocurrency, campaign:ClearFake, technique:Fake browser update, file-type:DMG, target-system:macOS
NetSupport RAT: The RAT King Returns
(published: November 20, 2023)
The NetSupport Manager software, originally designed for remote systems management, has been repurposed as a remote access trojan (RAT) to infiltrate systems and use them as a launching point for subsequent attacks. VMware researchers have observed an uptick in infections related to NetSupport RAT in recent weeks. The majority of these infections were from the Education, Government, and Business Services sectors. The attackers narrowed their delivery to deceptive websites and fake browser updates. The target is tricked to download a malicious JavaScript file. The following infection chain includes obfuscated PowerShell commands, and downloading additional binaries in a ZIP archive.
Analyst Comment: Users should be educated on safe ways to update their software and signs of a malicious update. Network defenders should monitor for suspicious PowerShell events such as invoked by JavaScript files mimicking a browser update. Host-based indicators associated with the recent NetSupport RAT campaigns are available in the Anomali platform for retrospective analysis.
MITRE ATT&CK: [MITRE ATT&CK] Execution - User Execution: Malicious File [T1204.002] | [MITRE ATT&CK] T1059.001: PowerShell | [MITRE ATT&CK] Defense Evasion - Process Injection [T1055] | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information [T1027] | [MITRE ATT&CK] Exfiltration - Exfiltration Over C2 Channel [T1041] | [MITRE ATT&CK] Collection - Data Staged: Local Data Staging [T1074.001] | [MITRE ATT&CK] Persistence - Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder [T1547.001] | [MITRE ATT&CK] Discovery - Process Discovery [T1057]
Tags: malware:NetSupport, malware-type:RAT, target-industry:Education, target-industry:Government, target-industry:Business Services, actor:TA569, file-type:DLL, file-type:EXE, file-type:JS, file-type:ZIP, target-system:Windows
FEATURED RESOURCES

The Silence Before the Storm: Why Saudi Arabia's Financial Sector Faces Its Most Dangerous Cyber Threat Window in a Decade



