Anomali Cyber Watch: Lazarus Adopts DLang Programming Language, Krasue Facilitates Covert Access on Infected Linux, and More


The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: Anti-analysis techniques, APT, North Korea, RATs, Rootkits, Russia, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
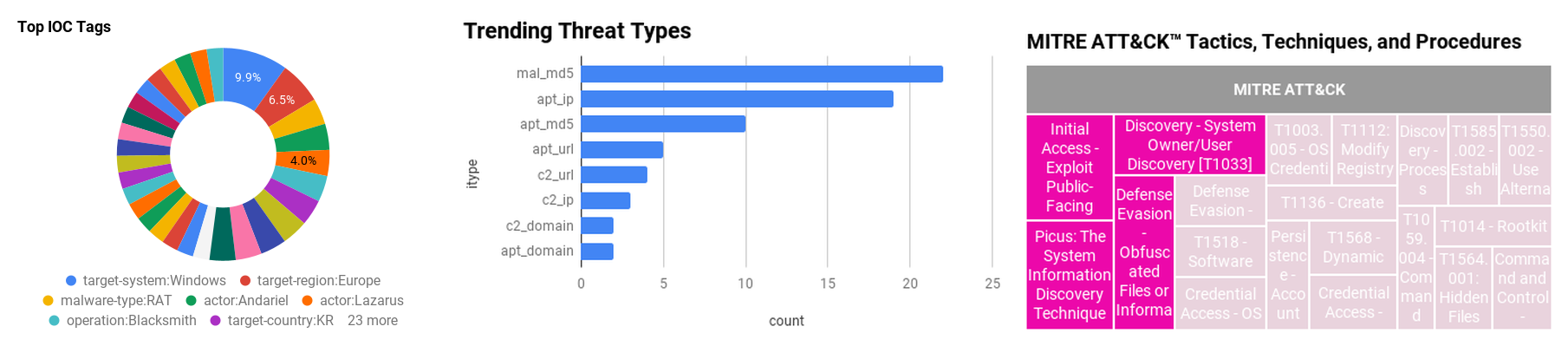
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Operation Blacksmith: Lazarus Targets Organizations Worldwide Using Novel Telegram-Based Malware Written in DLang
(published: December 11, 2023)
The Andariel subgroup of the North Korea-sponsored Lazarus group has launched a new campaign called Operation Blacksmith. According to Talos, this campaign has targeted manufacturing, agricultural, and physical security companies globally, exploiting their vulnerable infrastructure with publicly disclosed vulnerabilities such as Log4Shell (CVE-2021-44228). This campaign employs three new DLang-based malware families, one downloader (BottomLoader) and two remote access trojans (DLRAT and NineRAT). One of these RATs, NineRAT, uses Telegram bots as its C2 channel for accepting commands, communicating their outputs, and facilitating inbound and outbound file transfers. This campaign also delivers the custom-made proxy tool HazyLoad, previously attributed to Andariel.
Analyst Comment: The Lazarus group has shown a shift in tactics, switching to non-traditional programming frameworks and relying on multiple RATs for maintaining access to the compromised network. All known indicators associated with Operation Blacksmith are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] Defense Evasion - Indicator Removal: File Deletion [T1070.004] | [MITRE ATT&CK] Picus: The System Information Discovery Technique Explained - MITRE ATT&CK T1082 | [MITRE ATT&CK] T1518 - Software Discovery | [MITRE ATT&CK] Credential Access - OS Credential Dumping [T1003] | [MITRE ATT&CK] T1003.005 - OS Credential Dumping: Cached Domain Credentials | [MITRE ATT&CK] T1112: Modify Registry | [MITRE ATT&CK] T1136 - Create Account | [MITRE ATT&CK] Persistence - Account Manipulation [T1098] | [MITRE ATT&CK] Discovery - System Owner/User Discovery [T1033]
Tags: actor:Lazarus, actor:Andariel, operation:Blacksmith, abused:Telegram, language:DLang, malware-type:RAT, malware:NineRAT, malware:DLRAT, malware-type:Downloader, malware:BottomLoader, malware:HazyLoad, malware-type:Proxy, vulnerability:CVE-2021-44228, vulnerability:Log4Shell, target-industry:Manufacturing, target-industry:Agriculture, target-industry:Physical security, target-country:KR, target-region:South America, target-region:Europe, file-type:D, file-type:EXE, file-type:URL, target-system:Windows
Analyzing AsyncRAT's Code Injection into aspnet_compiler.exe Across Multiple Incident Response Cases
(published: December 11, 2023)
AsyncRAT is a remote access trojan (RAT) with capabilities such as keylogging and remote desktop control. It is capable of gathering client information, including usernames, computer information, installed antivirus software, and installed cryptocurrency wallets. Trend Micro researchers have discovered a new campaign abusing aspnet_compiler.exe (legitimate Microsoft binary for precompiling ASP.NET web applications) to inject the AsyncRAT payload. The use of Dynamic DNS by threat actors to swiftly change the IP address associated with a domain name makes it difficult for security systems to detect and block malicious activities.
Analyst Comment: AsyncRAT is a significant threat with capabilities such as keylogging and remote desktop control. Proactive threat detection and prevention should include user education, email security, robust monitoring, and considering partial restrictions for the execution of VBScript and PowerShell scripts. All known indicators associated with this AsyncRAT campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1568 - Dynamic Resolution | [MITRE ATT&CK] Credential Access - Input Capture: Keylogging [T1056.001] | [MITRE ATT&CK] Discovery - Process Discovery [T1057] | [MITRE ATT&CK] Picus: The System Information Discovery Technique Explained - MITRE ATT&CK T1082 | [MITRE ATT&CK] Discovery - System Owner/User Discovery [T1033]
Tags: malware:AsyncRAT, malware-type:RAT, abused:aspnet_compiler.exe, open-port:4782, open-port:6666, file-type:BAT, file-type:EXE, file-type:PS1, file-type:TXT, file-type:VBS, target-system:Windows
Fighting Ursa Aka APT28: Illuminating a Covert Campaign
(published: December 7, 2023)
The Russia-sponsored group Fancy Bear (APT28, Fighting Ursa, Forest Blizzard) has been exploiting a zero-click vulnerability in Microsoft Outlook (CVE-2023-23397). A specially-crafted email results in a relay attack using Windows NTLM authentication protocol. Outlook sends an NTLM authentication message to an actor-controlled remote file share allowing them to impersonate the target and access the target's network. Palo Alto Networks researchers have analyzed over 50 samples, targeting at least 30 organizations in 14 countries, focusing on those related to energy production and distribution, oil and gas pipelines, and government ministries. The group is targeting intelligence regarding NATO, Ukraine, and its allies such as Jordan and UAE. The attacks have been carried out in three waves, the first one, exploiting it as a zero-day vulnerability from March to December 2022, and the most recent occurring in September and October 2023.
Analyst Comment: High risk organizations and nations using Microsoft Outlook should patch CVE-2023-23397 immediately and ensure appropriate configuration to defend against future attacks. All known network indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1585.002 - Establish Accounts: Email Accounts | [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] T1550.002 - Use Alternate Authentication Material: Pass The Hash
Tags: actor:Fancy Bear, actor:APT28, vulnerability:CVE-2023-23397, target-software:Microsoft Outlook, source-country:RU, target-region:Europe, target-country:UA, target-country:US, target-country:BG, target-country:CZ, target-country:IT, target-country:JO, target-country:LT, target-country:LU, target-country:ME, target-country:PL, target-country:RO, target-country:SK, target-country:TR, target-country:AE, target-organization:NATO, target-organization:NATO Rapid Deployable Corps, target-industry:Government, target-industry:Energy, target-industry:Transportation, target-industry:Telecommunications, target-industry:Information technology, target-industry:Military industrial base,actor:Fighting Ursa, actor:Forest Blizzard, technique:NTLM relay attack, actor-identity:GRU, actor-identity:Unit 26165, abused:Ubiquiti, target-system:Windows
Curse of the Krasue: New Linux Remote Access Trojan targets Thailand
(published: December 7, 2023)
Group-IB researchers have discovered a new remote access trojan (RAT) dubbed Krasue that has been targeting Linux systems of Thai telecommunications companies since 2021. The RAT includes seven variants of a rootkit that supports multiple Linux kernel versions (2.6x/3.10.x). This rootkit portion is based on 3 different open-source LKM rootkits (Diamorphine, Rooty, and Suterusu) and shares unique similarities with the XorDdos Linux trojan. The rootkit uses system call hooking, function call hooking, conceals its own presence, hooks the `kill()` syscall, network-related functions and file listing operations, hides certain ports (52695 to 52699), files and directories (beginning with “auwd” and “vmware_helper). Krasue makes several attempts to contact hardcoded internal IP addresses over port 52699 and then uses RTSP (Real-Time Streaming Protocol) to contact its external master C2 IP address.
Analyst Comment: The initial vector and the scope of Krasue’s campaigns are still being investigated. Network defenders should monitor for anomalous RTSP traffic. YARA rules and indicators associated with the Krasue RAT are available in the Anomali platform for detection and historical reference.
MITRE ATT&CK: [MITRE ATT&CK] T1059.004 - Command and Scripting Interpreter: Unix Shell | [MITRE ATT&CK] T1014 - Rootkit | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information: Software Packing [T1027.002] | [MITRE ATT&CK] T1564.001: Hidden Files and Directories | [MITRE ATT&CK] Command and Control - Application Layer Protocol: Web Protocols [T1071.001] | [MITRE ATT&CK] Command and Control - Encrypted Channel [T1573]
Signatures: YARA Rules: linux_trojan_unpacked_krasue | linux_rootkit_krasue
Tags: malware:Krasue, malware-type:RAT, malware-type:Rootkit, malware:XorDdos, target-country:TH, target-industry:Telecom, protocol:RTSP, encryption:tiny-AES, technique:UPX packer, technique:System call hooking, technique:Function call hooking, impersonated:VMware driver, open-port:554, open-port:52699, file-type:ELF, target-system:Linux
Getting Gooey with GULOADER: Deobfuscating the Downloader
(published: December 5, 2023)
The GuLoader (CloudEyE) downloader has been updated with new obfuscation techniques that make its analysis more challenging and time-consuming. Recent changes to the malware include an improvement of an anti-analysis technique centered around its Vectored Exception Handling (VEH) capability. In the last few months, Elastic Security researchers have observed GuLoader VEH getting two new exceptions: EXCEPTION_PRIV_INSTRUCTION and EXCEPTION_ILLEGAL_INSTRUCTION. It gives GuLoader the ability to intercept and handle exceptions before they are routed through the standard exception process.
Analyst Comment: Malware researchers may use shellcode patching against some of the GuLoader anti-analysis techniques. The YARA rule and indicators associated with the GuLoader downloader are available in the Anomali platform.
MITRE ATT&CK: [MITRE ATT&CK] T1106: Native API | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information: Software Packing [T1027.002]
Signatures: YARA Rule: Windows_Trojan_Guloader
Tags: malware:GuLoader, malware:CloudEyE, malware-type:Downloader, EXCEPTION_PRIV_INSTRUCTION, EXCEPTION_ILLEGAL_INSTRUCTION, technique:Vectored Exception Handling, target-system:Windows
FEATURED RESOURCES




