Anomali Cyber Watch: Lazarus Exploited Admin-to-Kernel Zero-Day, Fancy Bear Has Been Using Compromised Ubiquiti EdgeRouters, and More


The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Backdoors, Botnets, Phishing kits, Rootkits, Smishing, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
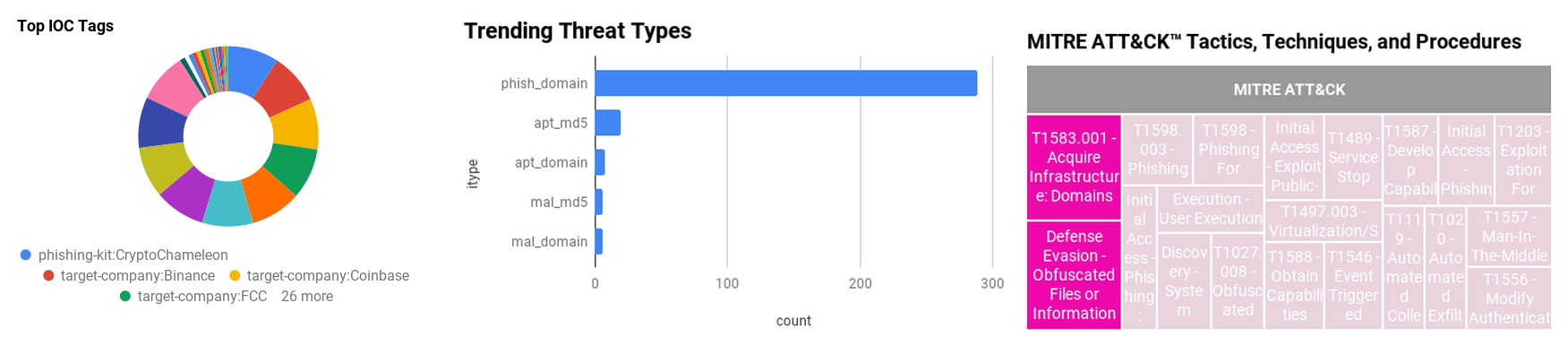
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
CryptoChameleon: New Phishing Tactics Exhibited in FCC-Targeted Attack
(published: February 29, 2024)
A new phishing kit named CryptoChameleon is being used to target Federal Communications Commission (FCC) employees and users of cryptocurrency platforms such as Binance, Coinbase, Gemini, Kraken, and Trezor. The attackers use a complex phishing and social engineering attack, which consists of email, SMS, and voice phishing, to deceive victims into entering sensitive information on the phishing pages. The attackers register domains that closely resemble those of legitimate entities and may call, email, or SMS the target, pretending to be customer support, directing them to the phishing site to recover their accounts. The phishing kit allows the attackers to interact with the victims in real-time to facilitate scenarios such as asking for additional authentication in case multi-factor authentication (MFA) codes are required to take over the target's account.
Analyst Comment: Users should be extra cautious when considering acting upon unsolicited messages and logging into their financial accounts on mobile devices. All known network indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure. The Anomali Premium Domain Monitoring service notifies customers regarding the registration of potential phishing domains.
MITRE ATT&CK: [MITRE ATT&CK] T1583.001 - Acquire Infrastructure: Domains | [MITRE ATT&CK] T1598.003 - Phishing for Information: Spearphishing Link | [MITRE ATT&CK] T1598 - Phishing For Information
Tags: phishing-kit:CryptoChameleon, target-company:FCC, target-company:Binance, target-company:Coinbase, target-company:Gemini, target-company:Kraken, target-company:Trezor, target-industry:Cryptocurrency, target-country:US
The Art of Domain Deception: Bifrost's New Tactic to Deceive Users
(published: February 29, 2024)
A new Linux variant of the Bifrost remote access trojan (RAT) has been analyzed by Palo Alto Networks. To avoid detection, the malware uses stripped binaries, employs RC4 encryption to encrypt collected victim data, and communicates with download.vmfare[.]com, a domain typosquatting VMware. Bifrost was first identified in 2004 and allows an attacker to gather sensitive information. From October 2023 to January 2024, a notable spike in Bifrost’s Linux variants was observed. The infrastructure identified for the x86 version of Bifrost was also hosting an ARM version.
Analyst Comment: A notable spike in Bifrost’s Linux variants and the drive to expand targeting and stealthiness of the malware are raising concerns among security experts and organizations. All known indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Phishing: Spearphishing Attachment [T1566.001] | [MITRE ATT&CK] Execution - User Execution [T1204] | [MITRE ATT&CK] Discovery - System Network Configuration Discovery [T1016] | [MITRE ATT&CK] T1583.001 - Acquire Infrastructure: Domains | [MITRE ATT&CK] T1027.008 - Obfuscated Files or Information: Stripped Payloads | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information [T1027]
Tags: malware:Bifrost, malware-type:RAT, malware:Bifrose, detection:Backdoor.Linux.Bifrose, technique:Stripped-payloads, encryption:RC4, impersonating:VMware, target-architecture:ARM, target-architecture:x86, target-system:Linux
Lazarus and the FudModule Rootkit: Beyond BYOVD with an Admin-to-Kernel Zero-Day
(published: February 28, 2024)
North Korea-sponsored Lazarus Group, exploited a zero-day vulnerability in the Windows AppLocker driver to gain kernel-level access and disable security tools. This allowed them to switch away from noisy BYOVD techniques. The vulnerability, now tracked as CVE-2024-21338, was detected by Avast analysts and reported to Microsoft, leading to a fix being issued as part of the February 2024 Patch Tuesday. The Lazarus Group used this exploit to create a read/write kernel primitive in an updated version of its FudModule rootkit, which features significant enhancements in stealth and functionality. Avast also discovered a previously undocumented remote access trojan (RAT) used by the Lazarus Group.
Analyst Comment: The Lazarus Group remains persistent in its prolific attacks, whether politically or financially motivated. Avast YARA rule for the latest FudModule variant is available in the Anomali platform for detection and historical reference.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] T1489 - Service Stop | [MITRE ATT&CK] T1497.003 - Virtualization/Sandbox Evasion: Time Based Evasion
Signatures: YARA Rule: Fudmodule_v2_sequences
Tags: actor:Lazarus, malware:FudModule, malware-type:Rootkit, malware-type:RAT, vulnerability:CVE-2024-21338, threat-type:Zero-day, source-country:KP, technique:Thread suspension, target-software:AppLocker, target-system:Windows
Russian Cyber Actors Use Compromised Routers to Facilitate Cyber Operations
(published: February 27, 2024)
Russia-sponsored group Fancy Bear (APT28, Forest-Blizzard) has been using compromised Ubiquiti EdgeRouters to carry out cyber operations from early 2022 to December 2023. The Federal Bureau of Investigation (FBI) together with its partners across multiple countries have outlined the use of zero-day vulnerability, CVE-2023-23397, to install tools on these compromised routers. Fancy Bear used a Mirai-based Moobot OpenSSH trojan, and custom credential-stealing Python scripts. The operations included building botnets, stealing credentials, collecting NTLMv2 digests, and proxying malicious traffic. Additionally, the attackers used compromised Ubiquiti EdgeRouters as a C2 infrastructure for MASEPIE backdoors deployed on other systems.
Analyst Comment: Network defenders can use the FBI-created Yara rule below to locate credential-stealing Python on compromised EdgeRouters. All known network indicators associated with this campaign are available in the Anomali platform, and customers are advised to block them on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1588 - Obtain Capabilities | [MITRE ATT&CK] T1546 - Event Triggered Execution | [MITRE ATT&CK] T1587 - Develop Capabilities | [MITRE ATT&CK] Initial Access - Phishing [T1566] | [MITRE ATT&CK] T1203 - Exploitation For Client Execution | [MITRE ATT&CK] T1119 - Automated Collection | [MITRE ATT&CK] T1020 - Automated Exfiltration | [MITRE ATT&CK] T1557 - Man-In-The-Middle | [MITRE ATT&CK] T1556 - Modify Authentication Process | [MITRE ATT&CK] T1584 - Compromise Infrastructure
Signatures: YARA Rule: APT28_core_scripts
Tags: actor:Fancy-Bear, malware:Moobot, malware-type:OpenSSH-trojan, malware-type:Botnet, malware:MASEPIE, malware-type:Backdoor, vulnerability:CVE-2023-23397, source-country:RU, actor-identity:GRU, actor-identity:GTsSS, actor:APT28, actor:Forest-Blizzard, open-port:4443, open-port:10081, target-system:Linux, target-system:EdgeRouters
GTPDOOR - A Novel Backdoor Tailored for Covert Access over the Roaming Exchange
(published: February 27, 2024)
Security researcher HaxRob identified a new Linux backdoor dubbed GTPDOOR, designed to be deployed in telecom networks adjacent to GPRS roaming exchanges (GRX). The malware has reverse shell functionality and uses the GPRS Tunnelling Protocol (GTP) for C2 communications. This backdoor is attributed to the cyberespionage group LightBasin (UNC1945), previously associated with attacks on the telecom sector and the abuse of the GTP protocol for traffic encapsulation. The malware changes its process name to [syslog] and utilizes the magic packet technique by opening a raw socket to receive UDP messages. It can be probed from an external network, and if active, it returns a crafted empty TCP packet.
Analyst Comment: Network defenders can identify GTPDOOR using the available YARA signature and examining possible raw sockets open on the potentially affected system. All known network indicators associated with this campaign are available in the Anomali platform, and customers are advised to block them on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1036.004 - Masquerading: Masquerade Task Or Service | [MITRE ATT&CK] Command and Control - Standard Application Layer Protocol [T1071] | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information [T1027]
Signatures: YARA Rule: Linux_Malware_GTPDOOR_v1v2
Tags: malware:GTPDOOR, malware-type:Backdoor, malware-type:Reverse-shell, actor:LightBasin, actor:UNC1945, target-industry:Telecom, technique:Rekeying, technique:Magic-packet, abused:GTP-protocol, target-system:RHEL, target-system:Linux
FEATURED RESOURCES




