Anomali Cyber Watch: Lazarus Unveils SIGNBT Backdoor, StripedFly Framework Exploiting EternalBlue for 7 Years, and More


The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Belarus, Cross-Site Scripting attacks, Data destruction, EternalBlue, Kazakhstan, North Korea, Phishing, and Zero-day vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
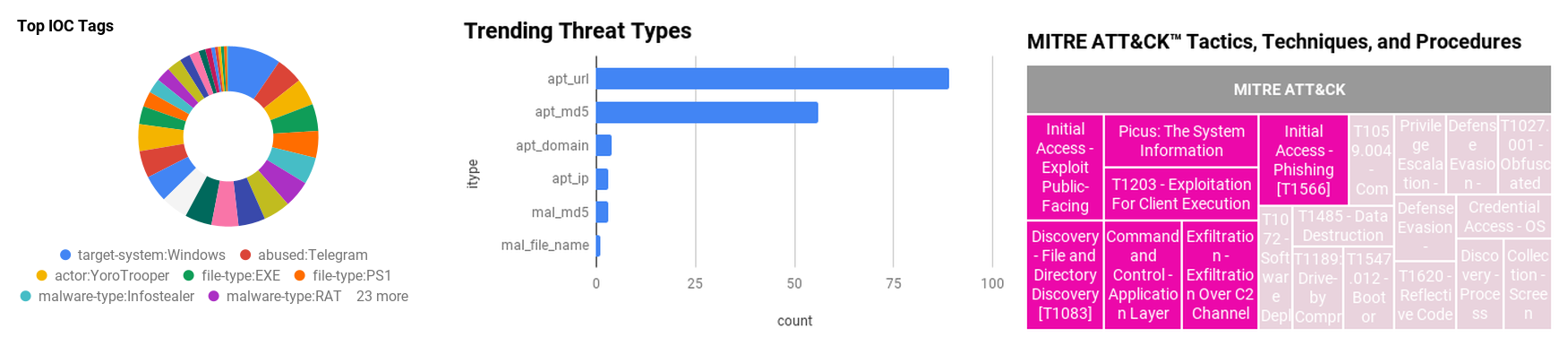
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
BiBi-Linux: A New Wiper Dropped By Pro-Hamas Hacktivist Group
(published: October 30, 2023)
A new malware wiper dubbed BiBi-Linux is being used to target Linux systems of Israeli companies. Security Joes researchers have discovered a sample of BiBi-Linux: an x64 ELF executable, coded in C/C++ and compiled using the GCC compiler. The malware does not exfiltrate data or drop a ransom note, instead, it destroys data by overwriting files with a buffer of random data. BiBi-Linux can completely wipe a compromised device's operating system if run with root privileges. It also has an option of quiet run and corrupting only folders selected by the attacker. The malware uses multiple threads and a queue system for improved speed and effectiveness.
Analyst Comment: Active military conflicts, such as between Ukraine and Russia, or like in this case, Israel and Hamas, increase the risk of wiper malware. Host-based indicators associated with BiBi-Linux are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] T1059.004 - Command and Scripting Interpreter: Unix Shell | [MITRE ATT&CK] T1072 - Software Deployment Tools | [MITRE ATT&CK] Discovery - File and Directory Discovery [T1083] | [MITRE ATT&CK] Picus: The System Information Discovery Technique Explained - MITRE ATT&CK T1082 | [MITRE ATT&CK] T1485 - Data Destruction
Signatures: YARA Rule: BiBi_Linux_Wiper.
Tags: malware:BiBi-Linux, malware-type:Wiper, target-country:IL, language:C, language:C++, file-type:OUT, file-type:x64 ELF, target-system:Linux
A Cascade of Compromise: Unveiling Lazarus’ New Campaign
(published: October 27, 2023)
In March-August 2023, the Lazarus group, a North Korea-sponsored threat group, was found to have exploited vulnerabilities in one high-profile software (unnamed) to target another software vendor (unnamed). The group has demonstrated a high level of sophistication, using advanced evasion techniques and introducing custom SIGNBT backdoor for victim control. The malware was delivered through unpatched legitimate software, likely using a publicly-known vulnerability. The actors used various persistence tactics including DLL side-loading and previously-observed use of spoolsv.exe to load malicious ualapi.dll at each system boot. Other malware found in memory included Lazarus’ prominent LPEClient, a tool known for victim profiling and payload delivery, that subsequently loaded credential dumping utilities.
Analyst Comment: The unnamed software vendor that developed the exploited software had been previously compromised by Lazarus several times. This recurring targeting suggests a likely objective of stealing source code or tampering with the software supply chain. All known indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1189: Drive-by Compromise | [MITRE ATT&CK] T1203 - Exploitation For Client Execution | [MITRE ATT&CK] T1547.012 - Boot or Logon Autostart Execution: Print Processors | [MITRE ATT&CK] Privilege Escalation - Hijack Execution Flow: DLL Side-Loading [T1574.002] | [MITRE ATT&CK] Defense Evasion - Deobfuscate/Decode Files or Information [T1140] | [MITRE ATT&CK] T1027.001 - Obfuscated Files or Information: Binary Padding | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information: Software Packing [T1027.002] | [MITRE ATT&CK] T1620 - Reflective Code Loading | [MITRE ATT&CK] Credential Access - OS Credential Dumping: LSASS Memory [T1003.001] | [MITRE ATT&CK] Discovery - Process Discovery [T1057] | [MITRE ATT&CK] Picus: The System Information Discovery Technique Explained - MITRE ATT&CK T1082 | [MITRE ATT&CK] Discovery - File and Directory Discovery [T1083] | [MITRE ATT&CK] Collection - Screen Capture [T1113] | [MITRE ATT&CK] Command and Control - Application Layer Protocol: Web Protocols [T1071.001] | [MITRE ATT&CK] T1132.002 - Data Encoding: Non-Standard Encoding | [MITRE ATT&CK] T1573.001 - Encrypted Channel: Symmetric Cryptography | [MITRE ATT&CK] Exfiltration - Exfiltration Over C2 Channel [T1041]
Tags: malware:SIGNBT, malware-type:Backdoor, malware:LPEClient, target-identity:Software vendor, file-name:ualapi.dll, file-type:DAT, file-type:DLL, file-type:EXE, target-system:Windows
StripedFly: Perennially Flying under the Radar
(published: October 26, 2023)
A sophisticated malware framework, dubbed StripedFly, that targets both Linux and Windows was initially misclassified as a cryptocurrency miner due to its less-obfuscated, Monero-mining module, according to Kaspersky researchers. StripedFly uses a custom EternalBlue SMBv1 exploit. This modular malware was first seen in Kaspersky telemetry in August 2017, but its PE timestamp patterns place its creation to April 2016, prior to Shadow Brokers releasing a leak containing the EternalBlue exploit. The malware also employs various methods for persistence and has a rich set of persistence mechanisms on Linux and Windows hosts. The malware is hosted on legitimate websites, disguised as firmware binaries. The malware communicates with a TOR network C2 server, and employs a unique, lightweight implementation of a TOR client. The Bitbucket repository download statistics shows almost 60,000 Windows victims From April to September 2023.
Analyst Comment: StripedFly shares similarities with Equation Group’s malware and is related to a 2017 ransomware variant called ThunderCrypt, however, no attribution was conclusively made. As mining has a limited profitability, it is likely that the real purpose of the StripedFly framework is related to cyberespionage. All known indicators associated with this framework are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1090.003 - Proxy: Multi-Hop Proxy | [MITRE ATT&CK] T1210 - Exploitation Of Remote Services | [MITRE ATT&CK] T1496 - Resource Hijacking | [MITRE ATT&CK] T1112: Modify Registry
Tags: malware:StripedFly, malware-type:Modular framework, malware:ThunderCrypt, malware-type:Ransomware, technique:TOR, technique:SMBv1, vulnerability:EternalBlue, target-system:Windows, target-system:Linux
Winter Vivern Exploits Zero-Day Vulnerability in Roundcube Webmail Servers
(published: October 25, 2023)
Active since at least 2020, the Winter Vivern group has been aligned with the interests of Belarus and Russia, and according to ESET researchers, it is probably linked to the Belarus-sponsored MoustachedBouncer group. Since at least 2022, Winter Vivern has been actively targeting Zimbra and Roundcube email servers owned by governmental organizations. On October 11, 2023, the group started to exploit a then XSS zero-day vulnerability in Roundcube Webmail (CVE-2023-5631), targeting European government entities and think tanks. The group uses HTML email messages containing carefully crafted SVG documents to remotely inject arbitrary JavaScript code. The final JavaScript payload helps the threat actors to harvest and steal emails from compromised webmail servers.
Analyst Comment: On October 16, 2023, the Roundcube team released security updates to address the vulnerability (1.6.4, 1.5.5, and 1.4.15). Network defenders are advised to update their Roundcube Webmail to the latest available version as soon as possible. Indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1583.001 - Acquire Infrastructure: Domains | [MITRE ATT&CK] T1583.004 - Acquire Infrastructure: Server | [MITRE ATT&CK] T1587.004 - Develop Capabilities: Exploits | [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] Initial Access - Phishing [T1566] | [MITRE ATT&CK] T1203 - Exploitation For Client Execution | [MITRE ATT&CK] T1087.003 - Account Discovery: Email Account | [MITRE ATT&CK] T1114.002 - Email Collection: Remote Email Collection | [MITRE ATT&CK] Command and Control - Application Layer Protocol: Web Protocols [T1071.001] | [MITRE ATT&CK] Exfiltration - Exfiltration Over C2 Channel [T1041]
Tags: actor:Winter Vivern, exploit-type:Zero-day, vulnerability:CVE-2023-5631, vulnerability:CVE-2020-35730, vulnerability-type:XSS, target-region:Europe, target-system:RoundcubeWebmail server
Kazakhstan-Associated YoroTrooper Disguises Origin of Attacks as Azerbaijan
(published: October 25, 2023)
Between May and August 2023, Talos researchers have analyzed the fresh activity of YoroTrooper, a cyberespionage group likely based in Kazakhstan. The group has been active since June 2022 and has targeted multiple state-owned websites and government officials' accounts in the Commonwealth of Independent States (CIS) countries: Azerbaijan, Kyrgyzstan, Tajikistan, Uzbekistan, and, in one case, the Anti-Corruption Agency in Kazakhstan itself. YoroTrooper uses various tactics to obfuscate their operations, including using VPNs and naming conventions making their activities appear to originate from Azerbaijan. In addition to commodity and custom malware and scanning tools, YoroTrooper continues to rely heavily on phishing emails and credential harvesting. During the summer of 2023, the group abandoned previously-used commodity malware and started porting its payloads to different languages (for example, from Python to PowerShell and Golang).
Analyst Comment: YoroTrooper appears to be persistent in their quest to exfiltrate data from several governments. Their rapidly-evolving and flexible attack tactics require a defense-in-depth approach from the defenders. All known indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure. In addition Cisco Talos, along with other Advisory, News and Blog sources are available as RSS feeds, and for AutoLens+ subscribers these are also tagged and summarized.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Phishing [T1566] | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] T1584 - Compromise Infrastructure | [MITRE ATT&CK] T1005: Data from Local System
Tags: actor:YoroTrooper, source-country:KZ, target-region:Commonwealth of Independent States, target-country:AZ, target-country:KG, target-country:KZ, target-country:TJ, target-country:UZ, target-industry:Government, impersonated:Azerbaijan, abused:Acunetix, abused:Shodan, abused:Telegram, malware-type:Infostealer, malware-type:RAT, file-type:PS1, file-type:EXE, target-system:Windows
FEATURED RESOURCES




