Anomali Cyber Watch: LockBit Disrupts US Subsidiary of Largest Chinese Bank, Sandworm Causes Another Blackout in Ukraine, and More


The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, DDoS, Ransomware, Russia, Vulnerabilities, and Zero-day exploitation. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
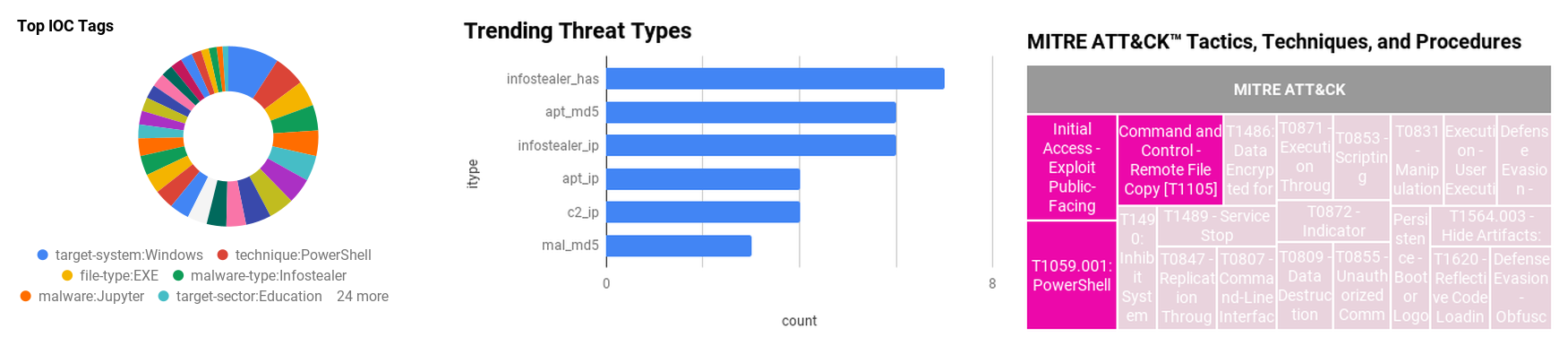
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
CitrixBleed' Linked to Ransomware Hit on China's State-Owned Bank
(published: November 10, 2023)
On November 8, 2023, ICBC Financial Services, a US subsidiary of Industrial and Commercial Bank of China (ICBC), was hit by a disruptive ransomware attack. Trades going through ICBC were not settled due to the attack and affected market liquidity, forcing the company to use unconventional USB stick transactions. The attack was attributed to the Russia-based LockBit ransomware group that took responsibility for the incident but tried to downplay its Russian origin by claiming affiliates in different countries including China. Security researcher Kevin Beaumont has discovered a potential attack vector: a Citrix NetScaler box at ICBC Financial Services that was not patched for the CitrixBleed (CVE-2023-4966) vulnerability as of November 6, 2023.
Analyst Comment: The US Cybersecurity and Infrastructure Security Agency directs to patch CVE-2023-4966 immediately amid reports of mass-exploit activity and estimated 5,000 organizations with exposed unpatched systems. Aligning patch and vulnerability processes to cyber threat intelligence significantly enhances the precision and priority of managing your security posture versus emerging threats from exploited vulnerabilities. Organizations keen to understand and maintain grip across their external attack surface are invited to use the Anomali Attack Surface Management service.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] T1486: Data Encrypted for Impact | [MITRE ATT&CK] T1490: Inhibit System Recovery
Tags: actor:LockBit, malware-type:Ransomware, malware:LockBit, vulnerability:CitrixBleed, vulnerability:CVE-2023-4966, target-software:Citrix NetScaler
ChatGPT: OpenAI Attributes Regular Outages to DDoS Attacks
(published: November 10, 2023)
The artificial intelligence (AI) application ChatGPT experienced recurring outages due to a distributed denial of service (DDoS) attack. The disruptions affected the ChatGPT interface, the associated API, all OpenAI API services, Labs, and Playground. The hacktivist group Anonymous Sudan claimed responsibility for the DDoS attacks, citing OpenAI's cooperation with Israel and the use of AI in weapon development as motives. Anonymous Sudan is likely affiliated with the Russian hacking group Killnet.
Analyst Comment: OpenAI has since resolved the issue. Denial-of-service attacks can potentially cost your company loss in revenue because severe attacks can shut down online services for extended periods of time. Organizations should implement DDoS protection measures and put in place a business continuity plan in the unfortunate case that your company is the target of a significant DDoS attack.
MITRE ATT&CK: [MITRE ATT&CK] T1489 - Service Stop
Tags: actor:Anonymous Sudan, actor:xAnonymousSudan, actor:Storm-1359, actor:KillNet, technique:DDoS, target-company:OpenAI, target-brand:ChatGPT, threat-type:Hacktivism
Sandworm Disrupts Power in Ukraine Using a Novel Attack Against Operational Technology
(published: November 9, 2023)
The Russia-sponsored group, Sandworm, targeted an electrical substation in Ukraine, causing a brief power outage in October 2022. Mandiant researchers describe the attack as a multi-event cyber attack that used a novel technique to impact industrial control systems (ICS). The exact initial vector used for the attack is unclear, but the intrusion is thought to have occurred around June 2022. Sandworm actors gained access to the OT environment through a hypervisor that hosted a supervisory control and data acquisition (SCADA) management instance for the victim's substation environment. The attackers first abused CD-ROM autorun setting to launch ISO image file and used OT-level living-off-the-land technique: they issued Supervisory Control Implementation Language (SCIL) commands via the scilc.exe native utility of the end-of-life MicroSCADA control system version that allowed default access to the SCIL-API. Two days later Sandworm deployed a new variant of CaddyWiper in the victim's IT environment.
Analyst Comment: Since 2014, Sandworm has been targeting OT systems and is likely capable of quickly developing similar capabilities against other OT systems from different manufacturers around the world. Network defenders should update their MicroSCADA to supported versions, and configure authentication requirements and a least privilege permission design. It is important to harden your OT systems with measures including disabling autorun for inserted CD-ROMs, and limit external SCIL-API programs execution. Detection rules and indicators associated with this OT attack are available in the Anomali platform for detection and historical reference.
MITRE ATT&CK: [MITRE ATT&CK] T0847 - Replication Through Removable Media | [MITRE ATT&CK] T0807 - Command-Line Interface | [MITRE ATT&CK] T0871 - Execution Through Api | [MITRE ATT&CK] T0853 - Scripting | [MITRE ATT&CK] T0872 - Indicator Removal On Host | [MITRE ATT&CK] T0809 - Data Destruction | [MITRE ATT&CK] T0855 - Unauthorized Command Message | [MITRE ATT&CK] T0831 - Manipulation Of Control
Signatures: YARA Rules: M_Methodology_MicroSCADA_SCILC_Strings | M_Hunting_MicroSCADA_SCILC_Program_Execution_Strings | M_Methodology_MicroSCADA_Path_Strings| M_Hunting_VBS_Batch_Launcher_Strings| M_Hunting_APT_Webshell_PHP_NEOREGEORG| M_Hunting_GOGETTER_SystemdConfiguration_1
Sigma Rule: MicroSCADA SCILC Command Execution
Tags: actor:Sandworm, target-country:UA, source-country:RU, target-sector:Critical infrastructure, target-industry:Energy, malware:CADDYWIPER, malware-type:Wiper, malware:Neo-REGEORG, malware-type:Webshell, malware:GOGETTER, malware-type:Tunneling, malware:TANKTRAP, abused:MicroSCADA, target-software:MicroSCADA control system, language:C, language:SCIL, file-type:BAT, file-type:ISO, file-type:TXT, file-type:BAT, target-system:Windows, target-system:OT, target-system:SCADA
SysAid On-Prem Software CVE-2023-47246 Vulnerability
(published: November 8, 2023)
SysAid, a provider of IT service management solutions, has disclosed a zero-day vulnerability (CVE-2023-47246) in its on-premise software. The vulnerability was actively exploited, leading to unauthorized access and control over the affected system. The threat actor, identified as the Clop (DEV-0950, Lace Tempest) ransomware group, uploaded a webshell and other payloads into the webroot of the SysAid Tomcat web service. The attacker then used a PowerShell script to execute a malware loader named user.exe, which loaded the GraceWire trojan.
Analyst Comment: SysAid has urged all customers with on-prem server installations to update their systems to version 23.3.36, which remediates the identified vulnerability. Network defenders are advised to review JSP, WAR, and ZIP files within the SysAid webroot directory, especially the ones that contain file timestamps that differ from the rest of the SysAid installation files. Check for suspicious POST requests and abnormal PowerShell script execution activities. All known indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] T1059.001: PowerShell | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105]
Tags: target-software:SysAid On-Prem, vulnerability:CVE-2023-47246, vulnerability-type:Zero-day, malware:GraceWire, detection:Trojan:Win32/TurtleLoader, detection:Backdoor:Win32/Clop, detection:Ransom:Win32/Clop, malware-type:Webshell, technique:PowerShell, actor:DEV-0950, actor:Clop, actor:Lace Tempest, file-name:usersfiles.war, file-type:EXE, target-system:Windows
Jupyter Rising: An Update on Jupyter Infostealer
(published: November 6, 2023)
Active since late 2020, the Jupyter Infostealer (Polazert, Solarmarker, and Yellow Cockatoo) continues to be one of the top ten infections, according to VMWare telemetry. The malware was primarily targeting the Education and Health sectors. In October-November 2023, a growth in the Jupiter activity coincided with a new infection chain using PowerShell commands and signed malware binaries. Common Jupiter delivery methods are drive-by downloads, malicious websites, malvertising, and phishing emails. It has the ability to harvest credentials and establish encrypted C2 communication to exfiltrate data and execute arbitrary commands.
Analyst Comment: It is important to teach your users basic online hygiene and phishing awareness. Deploy antivirus solutions on your endpoints to detect and block malicious activity. Indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Execution - User Execution: Malicious File [T1204.002] | [MITRE ATT&CK] T1059.001: PowerShell | [MITRE ATT&CK] Defense Evasion - Process Injection [T1055] | [MITRE ATT&CK] Persistence - Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder [T1547.001] | [MITRE ATT&CK] T1564.003 - Hide Artifacts: Hidden Window | [MITRE ATT&CK] T1620 - Reflective Code Loading | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information [T1027] | [MITRE ATT&CK] Defense Evasion - Masquerading [T1036] | [MITRE ATT&CK] Defense Evasion - Indicator Removal: File Deletion [T1070.004] | [MITRE ATT&CK] T1112: Modify Registry | [MITRE ATT&CK] Picus: The System Information Discovery Technique Explained - MITRE ATT&CK T1082 | [MITRE ATT&CK] Discovery - File and Directory Discovery [T1083] | [MITRE ATT&CK] T1552.001 - Unsecured Credentials: Credentials In Files | [MITRE ATT&CK] T1005: Data from Local System | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] Defense Evasion - Indicator Removal: Clear Windows Event Logs [T1070.001] | [MITRE ATT&CK] Exfiltration - Exfiltration Over C2 Channel [T1041]
Tags: malware:Jupyter, malware-type:Infostealer, target-sector:Education, target-sector:Healthcare, technique:System.Reflection.Assembly Load, technique:PowerShell, technique:Signed malware, file-type:DAT, file-type:EXE, file-type:PDF, file-type:TMP, target-system:Windows
FEATURED RESOURCES




