Anomali Cyber Watch: Lumma Stealer Waits for Human Mouse Movements, LitterDrifter USB Worm Spreads beyond Ukraine, and More


The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Infostealers, Phishing, Ransomware, Russia, Social Engineering, Ukraine, and Worms. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
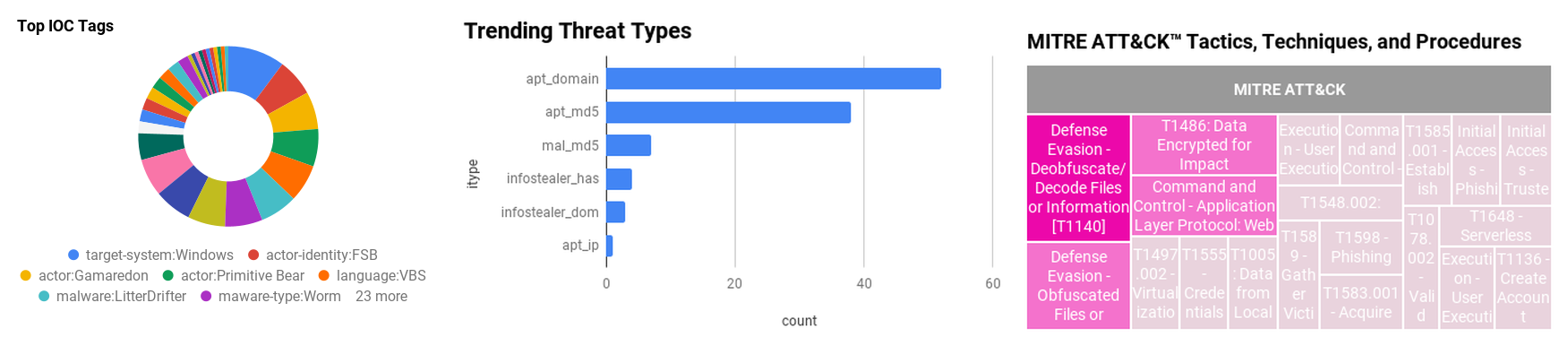
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Unveiling LummaC2 Stealer’s Novel Anti-Sandbox Technique: Leveraging Trigonometry for Human Behavior Detection
(published: November 20, 2023)
The LummaC2 (Lumma Stealer) infostealer, written in the C programming language, has been sold in underground forums since December 2022. Its latest version, LummaC2 v4.0 has received updates that make it harder to analyze. The malware uses XOR encryption, dynamic configuration files, and enforces threat actors to use a crypter for their builds. LummaC2 v4.0 also uses trigonometry to analyze mouse movements. In order to detonate LummaC2 v4.0, mouse movement must be continuous (5 different positions will be captured in approximately 0.25 seconds) and smooth (angles between the vectors formed by these positions cannot exceed 45 degrees).
Analyst Comment: Commodity infostealers remain a significant, evolving threat. It is important to teach your users basic online hygiene and phishing awareness. All known indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1497.002 - Virtualization/Sandbox Evasion: User Activity Based Checks | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information [T1027] | [MITRE ATT&CK] Defense Evasion - Deobfuscate/Decode Files or Information [T1140] | [MITRE ATT&CK] T1555 - Credentials From Password Stores | [MITRE ATT&CK] T1005: Data from Local System
Tags: malware:LummaC2 v4.0, malware:Lumma Stealer, malware-type:Infostealer, technique:Control Flow Flattening, technique:User Activity Based Checks, threat-type:Malware-as-a-Service, target-system:Windows
Malware Spotlight – Into The Trash: Analyzing LitterDrifter
(published: November 17, 2023)
The Russia-sponsored group Gamaredon has been observed spreading a worm dubbed LitterDrifter via USB drives. The group, active since 2014, primarily targets Ukraine and has continued to conduct multiple campaigns against Ukrainian targets. LitterDrifter is written in VBS and has two main functionalities: automatic spreading over USB drives, and communication with a broad, flexible set of C2 servers. For each logical drive detected, the spreader generates an LNK file with a random name chosen from an array of lures in English and Ukrainian. Check Point researchers have found indications that LitterDrifter has spread beyond its intended targets in Ukraine and affected Chile, Germany, Hong Kong, Poland, USA, and Vietnam.
Analyst Comment: Many advanced attacks start with basic techniques such as unwarranted email with malicious attachment that requires the user to open it and enable macroses. It is important to teach your users basic online hygiene and phishing awareness. Pay attention to suspicious files and consider displaying hidden files. All known network indicators associated with this LitterDrifter campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Defense Evasion - Deobfuscate/Decode Files or Information [T1140] | [MITRE ATT&CK] Execution - User Execution: Malicious File [T1204.002] | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105]
Tags: malware:LitterDrifter, maware-type:Worm, actor:Gamaredon, source-country:RU, target-country:UA, target-country:US, actor-identity:FSB, actor:Primitive Bear, abused:Telegram, language:VBS, file-type:LNK, target-system:Windows
A Deep Dive into Phobos Ransomware, Recently Deployed by 8Base Group
(published: November 17, 2023)
The 8Base group, which has been active since March 2022, primarily targets small and medium-sized businesses, with most victims located in the U.S. and Brazil. Cisco Talos has observed a surge in activity by 8Base, a ransomware group that uses a variant of the Phobos ransomware. The group's Phobos variants are typically distributed by SmokeLoader, a commodity loader. The ransomware component is embedded in its encrypted payloads, which are then decrypted and loaded into the SmokeLoader process' memory. The Phobos ransomware payload has a number of capabilities, including a user access control (UAC) bypass technique and reporting victim infections to an external URL. The same RSA key has been used to protect the encryption key in all samples of Phobos released since 2019, suggesting that obtaining the associated private key could enable decryption of all these samples.
Analyst Comment: Ransomware is a constantly evolving threat, and the most fundamental defense is having proper backup and restore processes in place that allows recovery without any need to decrypt the affected data. Data theft is containable through segmentation, encrypting data at rest, and limiting the storage of personal and sensitive data. Host-based indicators associated with this 8Base activity are available in the Anomali platform for retrospective analysis.
MITRE ATT&CK: [MITRE ATT&CK] T1486: Data Encrypted for Impact | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information [T1027] | [MITRE ATT&CK] Defense Evasion - Deobfuscate/Decode Files or Information [T1140] | [MITRE ATT&CK] T1548.002: Bypass User Access Control | [MITRE ATT&CK] Command and Control - Application Layer Protocol: Web Protocols [T1071.001]
Tags: malware:Phobos, malware-type:Ransomware, malware:SmokeLoader, malware-type:Loader, detection:Win.Packed.Zusy, detection:Win.Ransomware.8base, detection:Win.Downloader.Generic, detection:Win.Ransomware.Ulise, actor:8Base, technique:Bypass UAC, target-system:Windows
Scattered Spider
(published: November 16, 2023)
First discovered in 2022, Scattered Spider (Muddled Libra, Scatter Swine, Starfraud, and UNC3944) is known for its social engineering attacks targeting targets large companies and their contracted information technology (IT) help desks. Its major attacks on US organizations included MGM Resorts and Caesars Entertainment. The US Federal Bureau of Investigation and Cybersecurity and Infrastructure Security Agency documented Scattered Spider tactics, techniques, and procedures (TTPs) as recently as November 2023. The group has been increasingly aggressive in its social engineering and uses multiple social engineering techniques, especially phishing, push bombing, smishing, subscriber identity module (SIM) swap attacks, and even resorting to threats of physical violence. The group uses a number of commodity remote access tools, Mimikatz credential stealer, and the Ngrok tunneling tool. It can deploy infostealers: Raccoon Stealer, VIDAR Stealer, and WarZone, and engage in data theft for extortion. Finally, in mid-2023, Scattered Spider became a BlackCat/ALPHV ransomware affiliate.
Analyst Comment: Network defenders should regularly audit remote access tools on their network, and detect suspicious instances of only-in-memory loading. Consider implementing authentication resistant to phishing and not susceptible to push bombing (MFA fatigue) or SIM swap attacks. In addition, FBI/CISA, along with other Advisory, News and Blog sources are available as RSS feeds, and for AutoLens+ subscribers these are also tagged and summarized.
MITRE ATT&CK: [MITRE ATT&CK] T1589 - Gather Victim Identity Information | [MITRE ATT&CK] T1598 - Phishing For Information | [MITRE ATT&CK] T1583.001 - Acquire Infrastructure: Domains | [MITRE ATT&CK] T1585.001 - Establish Accounts: Social Media Accounts | [MITRE ATT&CK] Initial Access - Phishing [T1566] | [MITRE ATT&CK] Initial Access - Trusted Relationship [T1199] | [MITRE ATT&CK] T1078.002 - Valid Accounts: Domain Accounts | [MITRE ATT&CK] T1648 - Serverless Execution | [MITRE ATT&CK] Execution - User Execution [T1204] | [MITRE ATT&CK] T1136 - Create Account | [MITRE ATT&CK] T1556.006 - Modify Authentication Process: Multi-Factor Authentication | [MITRE ATT&CK] Privilege Escalation - Valid Accounts [T1078] | [MITRE ATT&CK] T1484.002 - Domain Policy Modification: Domain Trust Modification | [MITRE ATT&CK] T1578.002 - Modify Cloud Compute Infrastructure: Create Cloud Instance | [MITRE ATT&CK] T1606 - Forge Web Credentials | [MITRE ATT&CK] T1621 - Multi-Factor Authentication Request Generation | [MITRE ATT&CK] T1552.001 - Unsecured Credentials: Credentials In Files | [MITRE ATT&CK] T1552.004 - Unsecured Credentials: Private Keys | [MITRE ATT&CK] Discovery - Browser Information Discovery [T1217] | [MITRE ATT&CK] T1538 - Cloud Service Dashboard | [MITRE ATT&CK] Discovery - File and Directory Discovery [T1083] | [MITRE ATT&CK] Discovery - Remote System Discovery [T1018] | [MITRE ATT&CK] T1539 - Steal Web Session Cookie | [MITRE ATT&CK] Picus: T1021 Remote Services of the MITRE ATT&CK Framework | [MITRE ATT&CK] T1213.003 - Data from Information Repositories: Code Repositories | [MITRE ATT&CK] T1213.002 - Data from Information Repositories: Sharepoint | [MITRE ATT&CK] T1074 - Data Staged | [MITRE ATT&CK] T1114 - Email Collection | [MITRE ATT&CK] T1530 - Data From Cloud Storage Object | [MITRE ATT&CK] Command and Control - Remote Access Software [T1219] | [MITRE ATT&CK] T1486: Data Encrypted for Impact | [MITRE ATT&CK] T1567.002 - Exfiltration Over Web Service: Exfiltration To Cloud Storage
Tags: actor:Scattered Spider, malware:BlackCat, malware-type:Ransomware, malware:WarZone, malware:Raccoon Stealer, malware:VIDAR Stealer, malware-type:Infostealer, malware:Mimikatz, malware-type:Credential stealer, malware:Ngrok, malware-type:Tunneling, technique:Phishing, technique:Smishing, technique:Typosquatting, actor:Starfraud, actor:UNC3944, actor:Scatter Swine, actor:Muddled Libra, target-system:Windows
TA402 Uses Complex IronWind Infection Chains to Target Middle East-Based Government Entities
(published: November 14, 2023)
TA402 (Frankenstein, Gaza Cybergang, Molerats, and WIRTE) is a Palestine-sponsored group active since at least 2020. Proofpoint researchers detected no change in targeting in July through October 2023, as TA402 continued its phishing attacks against government entities based in the Middle East and North Africa. The only observed influence of the Israel-Hamas conflict was the use of the topic for lure purposes. At the same time, its new infection chain became much more complex. The group started utilizing malicious Microsoft PowerPoint Add-in (PPAM) files, a new initial-access downloader dubbed IronWind, and moved from Dropbox links to XLL and RAR file attachments.
Analyst Comment: TA402’s sophistication and alignment with the interests of the Palestinian Territories makes it a growing threat in the Middle East and North Africa. The group may start playing a more active role in the Israel-Hamas war. Defense-in-depth approach should include the fact that your trusted email senders could be compromised and leveraged against your organization. A YARA rule and indicators associated with the recent TA402 activity are available in the Anomali platform for detection and historical reference.
MITRE ATT&CK: [MITRE ATT&CK] T1586.002 - Compromise Accounts: Email Accounts | [MITRE ATT&CK] Initial Access - Phishing: Spearphishing Attachment [T1566.001] | [MITRE ATT&CK] Privilege Escalation - Hijack Execution Flow: DLL Side-Loading [T1574.002] | [MITRE ATT&CK] Command and Control - Application Layer Protocol: Web Protocols [T1071.001]
Signatures: YARA Rule: TA402_PDB
Tags: actor:TA402, malware:IronWind, malware-type:Downloader, source-country:PS, target-region:Middle East and North Africa, actor:Gaza Cybergang, actor:Molerats, actor:WIRTE, actor:Frankenstein, file-type:DLL, file-type:EXE, file-type:PPAM, file-type:RAR, file-type:VBS, file-type:XLL, target-system:Windows
FEATURED RESOURCES

The Silence Before the Storm: Why Saudi Arabia's Financial Sector Faces Its Most Dangerous Cyber Threat Window in a Decade



