Anomali Cyber Watch: Red Alert Compromised Amid Hamas Attack, Qakbot Operators Continue with Other Malware, and More


The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Botnets, China, Double extension, Hamas, Israel, Ransomware, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
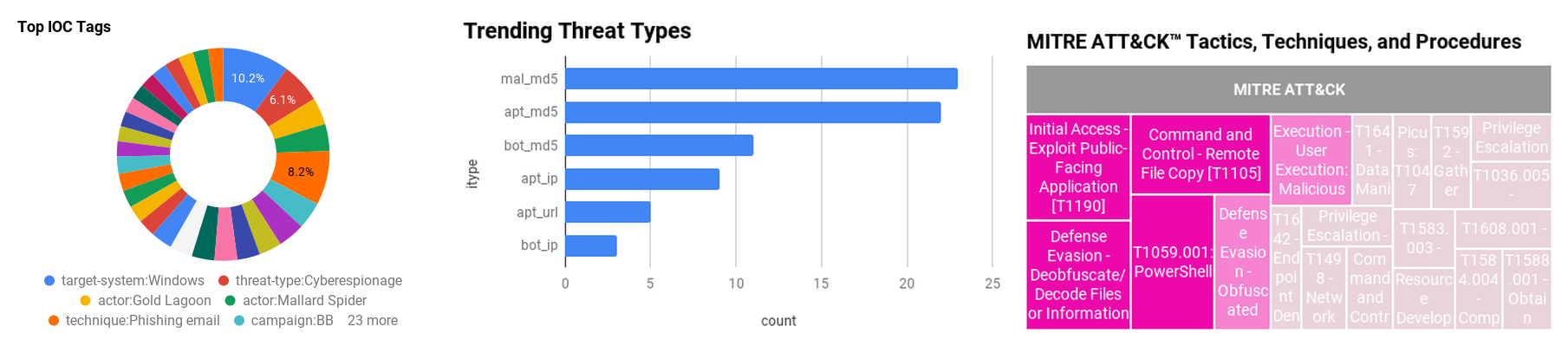
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Hackers Send Fake Rocket Alerts to Israelis via Hacked Red Alert App
(published: October 9, 2023)
The Red Alert app, which was sending real-time alerts to Israelis about incoming rockets, was targeted by a cyberattack from Pro-Palestinian hackers known as AnonGhost. The hackers exploited an API vulnerability within the app, allowing them to send spam messages to some users. The attack also included fabricated messages about a "nuclear bomb" attack on Israel. The hackers claimed that the attack also disconnected users' phones from the internet and rendered them unusable, but these claims remain unverified. The effects of this cyberattack on October 7-8, 2023 coincided with Hamas attacking Israel and both sides engaging in cyber warfare alongside military kinetic actions.
Analyst Comment: This story highlights potential threats and attacks that can arise based on current political geopolitical developments. Therefore, awareness of tension between countries and governments can potentially grant some insight as to where attacks may originate. It is crucial to identify critical infrastructure and secure it with heightened monitoring and protection measures.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] T1641 - Data Manipulation | [MITRE ATT&CK] T1642 - Endpoint Denial Of Service
Tags: actor:AnonGhost, target-country:IL, target-region:Middle East, Hamas, target-software:Red Alert, vulnerability-type:API, target-system:iOS, target-system:Android
IZ1H9 Campaign Enhances Its Arsenal with Scores of Exploits
(published: October 9, 2023)
A new Mirai-based DDoS botnet campaign dubbed IZ1H9 has been detected in September 2023 by Fortinet researchers. IZ1H9 added a significant number of new exploit payloads. It targets vulnerabilities in D-Link devices (CVE-2015-1187, CVE-2016-20017, CVE-2020-25506, and CVE-2021-45382), Geutebruck IP camera (CVE-2021-33544/33548/33549/33550/33551/33552/33553/33554), Korenix JetWave (CVE-2023-23295), Netis WF2419 router (CVE-2019-19356), Sunhillo SureLine (CVE-2021-36380), TOTOLINK routers (CVE-2022-40475/25080/25079/25081/25082/25078/25084/25077/25076/38511/25075/25083), TP-Link Archer AX21/AX1800 (CVE-2023-1389), Yealink Device Management (CVE-2021-27561/27562), Zyxel EMG3525/VMG1312 (/bin/zhttpd/ component vulnerability), and uses an unattributed exploit targeting “/cgi-bin/login.cgi” and injecting a payload in the “key” parameter. The injected payload gets a shell script downloader “l.sh”. The script is being executed and deletes logs. It then downloads and executes various bot clients covering various Linux architectures. Finally, it alters the device's iptables rules to obstructs network connections on multiple ports, including standard ones for HTTP, HTTPS, and SSH. The resulting botnet is used for large-scale DDoS attacks and expanding by using pre-set login credentials for brute-force attacks.
Analyst Comment: The Mirai botnet takes advantage of internet connected devices which have been lazily configured, leaving the door wide open to the world. Any device connecting to the internet should be regarded as a security risk, and default usernames and passwords should be deactivated. Organizations and defenders should be aware of all their internet facing assets and have them under strict monitoring. All known indicators associated with this Internet of Things botnet campaign are available in the Anomali platform and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] Privilege Escalation - Valid Accounts [T1078] | [MITRE ATT&CK] T1498 - Network Denial Of Service | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information [T1027] | [MITRE ATT&CK] Defense Evasion - Deobfuscate/Decode Files or Information [T1140] | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105]
Tags: campaign:IZ1H9, malware:Mirai, malware-type:DDoS botnet, technique:Valid credentials, technique:Brute force, vulnerability:CVE-2023-1389, vulnerability:CVE-2023-23295, vulnerability:CVE-2021-45382, vulnerability:CVE-2022-40475, vulnerability:CVE-2022-25080, vulnerability:CVE-2022-25079, vulnerability:CVE-2022-25081, vulnerability:CVE-2022-25082, vulnerability:CVE-2022-25078, vulnerability:CVE-2022-25084, vulnerability:CVE-2022-25077, vulnerability:CVE-2022-25076, vulnerability:CVE-2022-38511, vulnerability:CVE-2022-25075, vulnerability:CVE-2022-25083, vulnerability:CVE-2019-19356, vulnerability:CVE-2021-36380, vulnerability:CVE-2021-33544, vulnerability:CVE-2021-33548, vulnerability:CVE-2021-33549, vulnerability:CVE-2021-33550, vulnerability:CVE-2021-33551, vulnerability:CVE-2021-33552, vulnerability:CVE-2021-33554, vulnerability:CVE-2021-33553, vulnerability:CVE-2021-27561, vulnerability:CVE-2021-27562, vulnerability:CVE-2015-1187, vulnerability:CVE-2016-20017, vulnerability:CVE-2020-25506, target-device:D-Link, target-device:Netis WF2419, target-device:Sunhillo SureLine, target-device:Geutebruck, target-device:TP-Link Archer AX21, target-device:Korenix JetWave, target-device:TOTOLINK router, target-system:Yealink Device Management, target-type:IoT, target-system:Linux
Chinese State-Sponsored Cyber Espionage Activity Targeting Semiconductor Industry in East Asia
(published: October 6, 2023)
EclecticIQ researchers have discovered a China-sponsored cyberespionage campaign that is likely targeting the semiconductor industry in Mandarin/Chinese speaking East Asian regions, including Taiwan, Hong Kong, and Singapore. The exact identity of the attackers is unknown, but their tactics, techniques, and procedures overlap with those of three China-sponsored groups, APT27 (Budworm, LuckyMouse), Carderbee, and most of all, with RedHotel. One loader used in the campaign was a variant of the previously-described HyperBro loader with a Taiwan Semiconductor Manufacturing (TSMC) decoy lure. Another loader was functionally similar, but used Windows NTAPI undocumented functions and a different shellcode decryption routine to decrypt and load the Cobalt Strike shellcode. Another newly-discovered malware dubbed ChargeWeapon is a GO-based backdoor designed to extract victim network and device data.
Analyst Comment: Network defenders should enable PowerShell module and script logging and consider blocking PowerShell usage for regular Windows users. Monitor for suspicious DLL side-loading activities, especially those under C:\ProgramData, involving mcods.exe and vfhost.exe. All known indicators associated with this campaign are available in the Anomali platform and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information [T1027] | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] Command and Control - Application Layer Protocol: Web Protocols [T1071.001] | [MITRE ATT&CK] T1059.001: PowerShell | [MITRE ATT&CK] Execution - User Execution: Malicious File [T1204.002] | [MITRE ATT&CK] Picus: T1047 Windows Management Instrumentation of the MITRE ATT&CK Framework | [MITRE ATT&CK] T1592 - Gather Victim Host Information | [MITRE ATT&CK] Privilege Escalation - Hijack Execution Flow: DLL Side-Loading [T1574.002] | [MITRE ATT&CK] T1036.005 - Masquerading: Match Legitimate Name Or Location | [MITRE ATT&CK] Defense Evasion - Deobfuscate/Decode Files or Information [T1140]
Signatures: Yara rule: RedHotel_ChargeWeapon_Sep22.
Tags: malware:ChargeWeapon, malware-type:Backdoor, malware:HyperBro, malware-type:Loader, malware:Cobalt Strike, source-country:CN, threat-type:Cyberespionage, actor:APT27, actor:Carderbee, actor:RedHotel, target-industry:Semiconductor, target-region:East Asia, target-country:HK, language:Golang, open-port:8443, impersonated:Taiwan Semiconductor Manufacturing, abused:AS-CHOOPA (Vultr), abused:Kaopu Cloud HK, file-type:DLL, file-type:EXE, target-system:Cobra DocGuard server, target-system:Windows
Operation Jacana: Foundling hobbits in Guyana
(published: October 5, 2023)
In February 2023, ESET researchers discovered a spearphishing campaign, named Operation Jacana, targeting a governmental entity in Guyana. The campaign is suspected (medium confidence) to be orchestrated by a China-aligned threat group, although no specific APT group has been linked to the attack. The attackers used a previously undocumented C++ backdoor, dubbed DinodasRAT, and the PlugX (Korplug) backdoor typically used by China-sponsored groups. The attackers used previously-compromised Vietnamese government domain to stage some of their malicious payloads. The Tiny Encryption Algorithm (TEA), and the SoftEther VPN client provide for stealthy C2 communication. The lateral movement attempts that followed the initial compromise included abuse of Impacket, or a similar WMI-based lateral movement tool.
Analyst Comment: Operation Jacana spearphishing lure topics show that the attackers are keeping track of the geopolitical activities of their victims. Many advanced attacks begin with basic techniques, such as unsolicited emails with malicious attachments that require the user to open them. It is important to teach your users basic online hygiene and phishing awareness. Monitor for executable files using double extension to masquerade as Microsoft Office files. All known indicators associated with Operation Jacana are available in the Anomali platform and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1583.003 - Acquire Infrastructure: Virtual Private Server | [MITRE ATT&CK] Resource Development - Develop Capabilities: Malware [T1587.001] | [MITRE ATT&CK] T1608.001 - Stage Capabilities: Upload Malware | [MITRE ATT&CK] T1584.004 - Compromise Infrastructure: Server | [MITRE ATT&CK] T1588.001 - Obtain Capabilities: Malware | [MITRE ATT&CK] T1588.002 - Obtain Capabilities: Tool | [MITRE ATT&CK] Initial Access - Phishing: Spearphishing Link [T1566.002] | [MITRE ATT&CK] T1059.001: PowerShell | [MITRE ATT&CK] Execution - Command and Scripting Interpreter: Windows Command Shell [T1059.003] | [MITRE ATT&CK] Execution - Command and Scripting Interpreter: Visual Basic [T1059.005] | [MITRE ATT&CK] T1106: Native API | [MITRE ATT&CK] T1204.001 - User Execution: Malicious Link | [MITRE ATT&CK] Execution - User Execution: Malicious File [T1204.002] | [MITRE ATT&CK] Defense Evasion - Deobfuscate/Decode Files or Information [T1140] | [MITRE ATT&CK] T1036.007 - Masquerading: Double File Extension | [MITRE ATT&CK] Defense Evasion - Indicator Removal: File Deletion [T1070.004] | [MITRE ATT&CK] T1564.001: Hidden Files and Directories | [MITRE ATT&CK] T1078.002 - Valid Accounts: Domain Accounts | [MITRE ATT&CK] T1053 - Scheduled Task/Job | [MITRE ATT&CK] Credential Access - OS Credential Dumping: NTDS [T1003.003] | [MITRE ATT&CK] Discovery - File and Directory Discovery [T1083] | [MITRE ATT&CK] T1012: Query Registry | [MITRE ATT&CK] Discovery - Process Discovery [T1057] | [MITRE ATT&CK] T1007 - System Service Discovery | [MITRE ATT&CK] Picus: The System Information Discovery Technique Explained - MITRE ATT&CK T1082 | [MITRE ATT&CK] Collection - Clipboard Data [T1115] | [MITRE ATT&CK] Collection - Screen Capture [T1113] | [MITRE ATT&CK] T1573.001 - Encrypted Channel: Symmetric Cryptography | [MITRE ATT&CK] Command and Control - Standard Non-Application Layer Protocol [T1095] | [MITRE ATT&CK] T1132 - Data Encoding | [MITRE ATT&CK] Exfiltration - Exfiltration Over C2 Channel [T1041]
Tags: campaign:Operation Jacana, target-country:Guyana, target-country:GY, source-country:CN, malware:DinodasRAT, malware-type:Backdoor, threat-type:Cyberespionage, target-industry:Government, abused:Impacket, abused:PowerShell, abused:SoftEther VPN, language:C++, encryption:TEA, file-type:DOC.EXE, file-type:DOCX.EXE, file-type:EXE, file-type:RAR, file-type:TXT, file-type:ZIP, target-system:Windows
Qakbot-Affiliated Actors Distribute Ransom Knight Malware Despite Infrastructure Takedown
(published: October 5, 2023)
From 2007 to late August 2023, threat actors tracked as Mallard Spider (Gold Lagoon) were managing the Qakbot malware operation until the FBI seized its C2 infrastructure. Talos researchers have discovered a connection between “AA” and “BB” campaigns distributing Qakbot and a new campaign distributing different malware that started in early August 2023 and continued after the FBI Qakbot takedown. Former Qakbot malware operators have been likely using their preexisting phishing email infrastructure to deliver LNK files, with themes of urgent financial matters. The final payloads include the Remcos backdoor and the Ransom Knight ransomware that was based on the Cyclops ransomware-as-a-service and is likely managed by a separate group.
Analyst Comment: Despite losing their C2 infrastructure and some cryptocurrency funds, former Qakbot operators appear to be continuing some of their phishing operations. Threat intelligence researchers continue to monitor for potential Qakbot comeback. Network defenders are advised to monitor for suspicious command execution in .LNK file process. All known indicators associated with this campaign are available in the Anomali platform and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Phishing [T1566] | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] T1059.001: PowerShell | [MITRE ATT&CK] T1021.002 - Remote Services: Smb/Windows Admin Shares | [MITRE ATT&CK] T1486: Data Encrypted for Impact
Tags: malware:Qakbot, detection:Lnk.Downloader.Qakbot, malware:Ransom Knight, detection:Win.Ransomware.Knight, malware:Cyclops, malware-type:Ransomware, malware:Remcos, detection:Win.Backdoor.Remcos, malware-type:Backdoor, actor:Mallard Spider, actor:Gold Lagoon, campaign:AA, campaign:BB, technique:Phishing email, open-port:80, file-type:DOCX.LNK, file-type:EXE, file-type:IMG.LNK, file-type:LNK, file-type:PDF.LNK, file-type:XLL, target-system:Windows
FEATURED RESOURCES




