Anomali Cyber Watch: Sea Turtle Adopted Open-Source Linux Tools, AsyncRAT Delivered by GIF Attachments, and More


The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Cryptocurrency, Domain generation algorithm, Malspam, Middle East, North Korea, Social engineering, Phishing, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
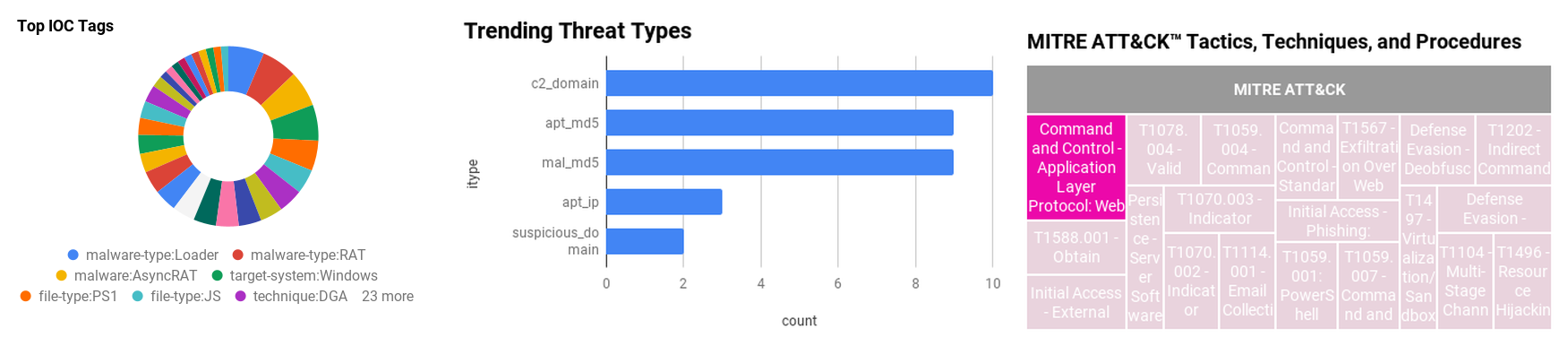
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
KyberSlash Attacks Put Quantum Encryption Projects at Risk
(published: January 7, 2024)
Multiple implementations of the Kyber key encapsulation mechanism, part of the National Institute of Standards and Technology (NIST) selection used for quantum-safe encryption, have been found vulnerable to two vulnerabilities known as KyberSlash (KyberSlash1 and KyberSlash2). These vulnerabilities could potentially allow the recovery of secret keys due to timing-based attacks arising from specific division operations in the Kyber decapsulation process. It enables attackers to analyze the execution time and derive secrets that could compromise the encryption. Some popular projects using implementations of Kyber include Mullvad VPN and Signal messenger.
Analyst Comment: Efforts are underway to patch the vulnerabilities, with some projects already fully patched and others still in the process. The pqcrypto-kyber library was patched downstream in Signal on January 5, 2024.
Tags: vulnerability:KyberSlash, vulnerability:KyberSlash1, vulnerability:KyberSlash2, vulnerability-type:Timing-based, vulnerability-type:Secret-key-leakage, target-software:Kyber, target-software:Mullvad-VPN, target-software:Signal
Turkish Espionage Campaigns in the Netherlands
(published: January 5, 2024)
Active since at least 2017, the Turkey-sponsored Sea Turtle (SILICON, Cosmic Wolf) cyberespionage group has primarily focused on organizations in Europe, the Middle East, and North Africa, intercepting internet traffic to victim websites and potentially gaining unauthorized access to government networks and other organizations. In 2021-2023, Hunt & Hackett researchers detected multiple Sea Turtle campaigns targeting various entities in the Netherlands, including telecommunication companies, media outlets, ISPs, IT service providers, and Kurdish websites. In 2023, the actors compromised cPanel accounts and used SSH to deploy an open-source reverse TCP shell named SnappyTCP. They used the NoHup tool for persistence, and removed indicators by unsetting the command history (Bash) and MySQL history file, and overwriting Linux system logs. Sea Turtle finished the attack with creating a copy of an email archive exfiltrating it to the public web directory of a website.
Analyst Comment: Sea Turtle activity often remains under the radar. The abuse of open-source tools makes the attribution harder. All known network indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1588.001 - Obtain Capabilities: Malware | [MITRE ATT&CK] Initial Access - External Remote Services [T1133] | [MITRE ATT&CK] T1078.004 - Valid Accounts: Cloud Accounts | [MITRE ATT&CK] T1059.004 - Command and Scripting Interpreter: Unix Shell | [MITRE ATT&CK] Persistence - Server Software Component: Web Shell [T1505.003] | [MITRE ATT&CK] T1070.003 - Indicator Removal on Host: Clear Command History | [MITRE ATT&CK] T1070.002 - Indicator Removal on Host: Clear Linux Or Mac System Logs | [MITRE ATT&CK] T1114.001 - Email Collection: Local Email Collection | [MITRE ATT&CK] Command and Control - Application Layer Protocol: Web Protocols [T1071.001] | [MITRE ATT&CK] Command and Control - Standard Non-Application Layer Protocol [T1095] | [MITRE ATT&CK] T1567 - Exfiltration Over Web Service
Tags: actor:Sea-Turtle, source-country:TR, target-country:NL, malware:SnappyTCP, malware-type:Reverse-TCP-shell, tool:Adminer, tool:NoHup, tool:Socat, actor:Teal-Kurma, actor:Marbled-Dust, actor:SILICON, actor:Cosmic-Wolf, target-industry:Government, target-identity:Kurdish, target-identity:PKK, target-industry:Telecommunication, target-industry:ISP, target-industry:IT-service-providers, target-industry:NGO, target-industry:Media, target-industry:Entertainment, target-region:Europe, target-region:Middle-East, target-region:North-Africa, technique:Island-hopping, technique:Traffic-redirection, technique:Man-in-the-middle, open-port:443, target-system:Linux, target-system:Unix
AsyncRAT Loader: Obfuscation, DGAs, Decoys and Govno
(published: January 5, 2024)
Often abused by threat actors, AsyncRAT is an open-source remote access tool (RAT) for Windows, with functions for remote command execution, keylogging, data exfiltration, and dropping additional payloads. Since February 2023, a specific campaign delivering the AsyncRAT remote access trojan has been targeting select individuals and companies, according to ATT researchers. The attacks begin with a malicious email carrying a GIF attachment that leads to an SVG file that downloads obfuscated JavaScript and PowerShell scripts. The loader communicates with the C2 server and conducts several unique anti-virtualization calculations to serve AsyncRAT or a decoy. The threat actor used 300 unique samples of the loader in the past 11 months, each with minor alterations in the code structure, obfuscation, and variable names and values. An additional C2 infrastructure was discovered that is recycled every week and relies on a domain generation algorithm (DGA) to calculate a domain name based on the current date.
Analyst Comment: It is important to study malicious infrastructure and DGAs to identify them when threat actors come back with a new attack. All known indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Phishing: Spearphishing Attachment [T1566.001] | [MITRE ATT&CK] T1059.001: PowerShell | [MITRE ATT&CK] T1059.007 - Command and Scripting Interpreter: Javascript | [MITRE ATT&CK] Defense Evasion - Deobfuscate/Decode Files or Information [T1140] | [MITRE ATT&CK] T1202 - Indirect Command Execution | [MITRE ATT&CK] T1497 - Virtualization/Sandbox Evasion | [MITRE ATT&CK] Defense Evasion - Virtualization/Sandbox Evasion: System Checks [T1497.001] | [MITRE ATT&CK] Command and Control - Application Layer Protocol: Web Protocols [T1071.001] | [MITRE ATT&CK] T1104 - Multi-Stage Channels | [MITRE ATT&CK] T1496 - Resource Hijacking
Tags: malware:AsyncRAT, malware-type:RAT, malware-type:Loader, technique:DGA, file-type:GIF, file-type:JS, file-type:SVG, file-type:PS1, target-system:Windows
Web3 Security Firm CertiK's X Account hacked to Push Crypto Drainer
(published: January 5, 2024)
The X (Twitter) account of blockchain security firm CertiK was compromised in a social engineering attack, redirecting its 343,000 followers to a malicious website promoting a cryptocurrency wallet drainer. The attackers used a hacked account associated with a well-known media to carry out the phishing attack. After a short conversation, CertiK received an alleged interview scheduling request where the destination domain was typosquatted with a different (.FI) top level domain.
Analyst Comment: The company deleted the malicious tweet 15 minutes after it was posted and is currently investigating the incident. This attack is part of a larger ongoing social engineering campaign that has compromised many other accounts. Companies need to be vigilant and take necessary precautions to secure their social media accounts. Users should be aware of financial scams and use the general principle “If it sounds too good to be true, it probably is.”
MITRE ATT&CK: [MITRE ATT&CK] T1204.001 - User Execution: Malicious Link
Tags: impersonated:Calendly, technique:Crypto-draining, technique:Social-engineering, technique:Typosquatting, target-industry:Blockchain, target-industry:Cryptocurrency
SpectralBlur
(published: January 3, 2024)
The North Korea-sponsored threat group APT38 (BlueNoroff, Stardust Chollima) has introduced a new backdoor dubbed SpectralBlur targeting macOS users. Cybersecurity researcher Greg Lesnewich has been monitoring SpectralBlur since August 2023 and discovered significant similarities with another APT38 macOS malware, KANDYKORN (SockRacket). The SpectralBlur backdoor communicates via sockets wrapped in RC4 and can be instructed to upload/download files, run a shell, update its configuration, delete files, and sleep.
Analyst Comment: SpectralBlur is part of a growing trend of macOS-targeted malware. YARA rules and host-based indicators associated with these APT38 backdoors are available in the Anomali platform for detection and historical reference.
MITRE ATT&CK: [MITRE ATT&CK] T1573.001 - Encrypted Channel: Symmetric Cryptography | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] T1497.003 - Virtualization/Sandbox Evasion: Time Based Evasion | [MITRE ATT&CK] Defense Evasion - Indicator Removal: File Deletion [T1070.004]
Signatures: YARA Rule: APT_NK_TA444_SpectralBlur
Tags: malware:SpectralBlur, malware-type:Backdoor, malware:KANDYKORN, malware:SockRacket, actor:APT38, actor:BlueNoroff, actor:TA444, actor:Coperenicum, actor:Stardust Chollima, source-country:KP, target-system:macOS
FEATURED RESOURCES

The Silence Before the Storm: Why Saudi Arabia's Financial Sector Faces Its Most Dangerous Cyber Threat Window in a Decade



