Anomali Cyber Watch: Three Wipers Targeting Israel, macOS Malware Disguised as Code Challenge by Lazarus, and More


The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Data wiping, Iran, Israel, North Korea, Proxy botnet, Russia, and Vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
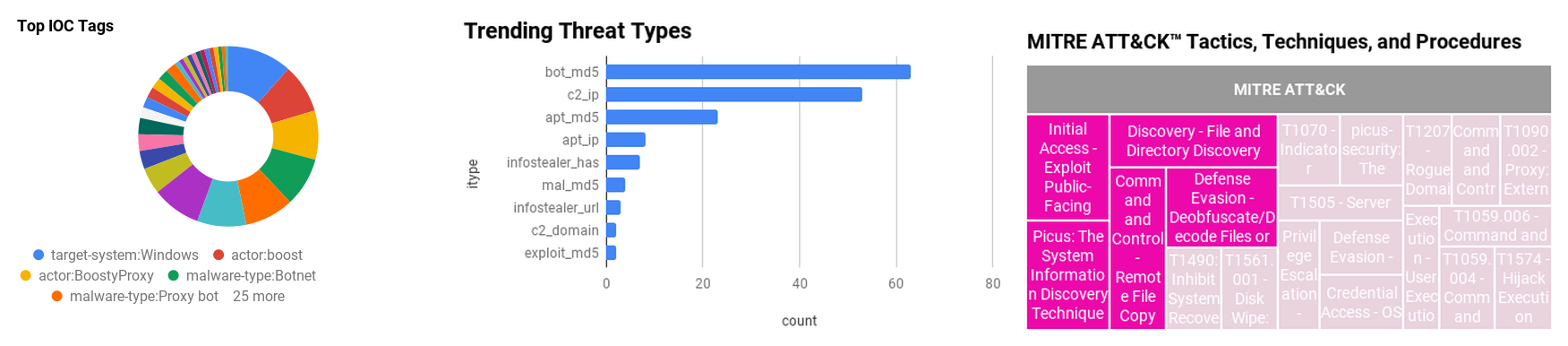
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Agonizing Serpens (Aka Agrius) Targeting the Israeli Higher Education and Tech Sectors
(published: November 6, 2023)
An Iran-sponsored group known as Agonizing Serpens (Agrius, BlackShadow, DEV-0022, and Pink Sandstorm) has targeted higher education and technology industries in Israel. Palo Alto Networks researchers have uncovered a series of complex exfiltration and data-wiping cyberattacks that began in January 2023 and continued into October 2023. The attack started by deploying ASPXSpy webshell variants to vulnerable web servers, and using publicly-available scanners (Nbtscan, NimScan, and WinEggDrop) to map the network. Agonizing Serpens used dumping the SAM file, Mimikatz, SMB password brute force, and SMB password spraying to obtain credentials. Lateral movement and data exfiltration was achieved with publicly available tools such Plink, Putty, and WinSCP. To steal information from databases and other critical servers the group deployed sqlextractor, a custom tool that extracts sensitive personal data (emails, full addresses, ID numbers, and passport scans) from SQL databases. The group showed a level of persistency trying to overcome protection measures by deploying additional data wipers (MultiLayer Wiper, PartialWasher Wiper, and BFG Agonizer Wiper) and EDR bypass tools and techniques (trying to block XDR service auto-start functionally and making two attempts of the bring-your-own-vulnerable-driver attack).
Analyst Comment: All devices should be kept up-to-date with the latest software versions and protections against ProxyShell and ProxyLogon vulnerabilities should be ensured. Network defenders should aim at preventing the execution of known malware and monitoring for suspicious behavior patterns. All known indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] T1490: Inhibit System Recovery | [MITRE ATT&CK] T1561.001 - Disk Wipe: Disk Content Wipe | [MITRE ATT&CK] T1070 - Indicator Removal On Host
Tags: actor:Agonizing Serpens, source-country:IR, target-country:IL, malware:Nbtscan, malware:NimScan, malware:WinEggDrop, malware:Mimikatz, malware:Plink, malware:Putty, malware:WinSCP, malware:sqlextractor, malware:MultiLayer Wiper, malware:PartialWasher Wiper, malware:BFG Agonizer Wiper, actor:Agrius, target-industry:Education, target-industry:Tech, technique:BYOVD, target-system:Windows
Looney Tunables Vulnerability Exploited by Kinsing
(published: November 3, 2023)
Kinsing actors are known to quickly adopt newly-disclosed vulnerabilities to cryptojack cloud environments. Aqua Security researchers have observed the group exploiting a recently-disclosed Linux privilege escalation flaw, Looney Tunables (CVE-2023-4911). This is the first documented active exploitation of this high-severity vulnerability residing in the glibc dynamic loader. The initial access was acquired via automated exploitation of the PHPUnit vulnerability (CVE-2017-9841). To exploit Looney Tunables, Kinsing manually crafted and tested shell commands, a new pattern of behavior for this group. The attackers are also expanding their cloud-native attacks by extracting credentials from the Cloud Service Provider. In the observed case, those were associated with the AWS instance identity and credentials associated with the instance metadata service (Temporary Security Credentials, IAM Role Credentials, and Instance Identity Tokens).
Analyst Comment: Extracting cloud credentials for follow-on attacks is a significant shift from previously-observed Kinsing patterns and may indicate an increased threat to cloud-native environments. Network defenders should keep their systems patched with the latest security patches, including those addressing PHPUnit (CVE-2017-9841) and Looney Tunables (CVE-2023-4911). Adjust authorization and authentication policies according to the principle of least privilege. Monitor for manual command executions, attempts to access or enumerate Cloud Service Provider credentials, and the execution of known malicious scripts. All known indicators associated with this exploitation attack are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] picus-security: The Most Used ATT&CK Technique — T1059 Command and Scripting Interpreter | [MITRE ATT&CK] T1505 - Server Software Component | [MITRE ATT&CK] Privilege Escalation - Exploitation for Privilege Escalation [T1068] | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information [T1027] | [MITRE ATT&CK] Credential Access - OS Credential Dumping [T1003] | [MITRE ATT&CK] Picus: The System Information Discovery Technique Explained - MITRE ATT&CK T1082 | [MITRE ATT&CK] Discovery - File and Directory Discovery [T1083]
Tags: vulnerability:Looney Tunables, vulnerability:CVE-2023-4911, actor:Kinsing, target-software:PHPUnit, vulnerability:CVE-2017-9841, malware-type:Reverse shell, language:Perl, language:PHP, language:JavaScript, target-system:Linux
Unveiling Socks5Systemz: The Rise of a New Proxy Service via PrivateLoader and Amadey
(published: November 2, 2023)
A proxy botnet named Socks5Systemz has been infecting computers globally through the PrivateLoader and Amadey loaders, with a current count of 10,000 infected devices. The top eight most affected countries are, in order, India, Brasil, Colombia, South Africa, Bangladesh, Argentina, Angola, and the US. The malware turns infected computers into traffic-forwarding proxies for malicious, illegal, or anonymous traffic, which is then sold to subscribers via the BoostyProxy (boost) persona. The botnet has been active since at least 2016 and Bitsight researchers assess with medium confidence that it is operated out of Russia. The underlying infrastructure contained at least 53 servers in France, Bulgaria, Netherlands, and Sweden. Those included backconnect, custom DNS, online C2 resolution, proxy bot, and proxy checker servers. The actor-controlled DNS servers are used to resolve any domain to a valid C2 server.
Analyst Comment: The botnet has a significant impact on internet security and unauthorized bandwidth hijacking. All known indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] T1207 - Rogue Domain Controller | [MITRE ATT&CK] Defense Evasion - Deobfuscate/Decode Files or Information [T1140] | [MITRE ATT&CK] Command and Control - Encrypted Channel [T1573] | [MITRE ATT&CK] T1090.002 - Proxy: External Proxy
Tags: malware:Socks5Systemz, malware-type:Botnet, malware-type:Proxy bot, actor:boost, actor:BoostyProxy, malware:PrivateLoader, malware:Amadey, source-country:RU, open-port:1074, file-type:DLL, file-type:EXE, target-system:Windows
Elastic Catches DPRK Passing out KANDYKORN
(published: October 31, 2023)
The North Korea-sponsored Lazarus group has been identified as using a new macOS malware, KANDYKORN, in attacks against blockchain engineers. The attackers impersonated members of the blockchain engineering community on a public Discord server and used private messages to trick targets into downloading a ZIP archive containing the malicious Python code. The attack chain consisted of multiple stages involving loaders and droppers – including custom SUGARLOADER and HLOADER – and attempts to reflectively load KANDYKORN into memory on a macOS endpoint. The malware supports multiple capabilities such as harvesting information, listing directories and running processes, downloading and uploading files, archiving directories and exfiltrating them, killing processes, executing commands using a terminal, spawning a shell, downloading a configuration from the server, sleeping, and exiting. The campaign is still active and is traced back to April 2023.
Analyst Comment: Network defenders are encouraged to detect and investigate suspicious behavior including: a hidden executable creating and then immediately deleting a file within a temporary directory; a hidden file making an outbound network connection followed by the immediate download of an executable file; a macOS application binary being renamed to a hidden file name within the same directory, - and other EQL query suggestions by Elastic. YARA rules and indicators associated with this campaign are available in the Anomali platform.
MITRE ATT&CK: [MITRE ATT&CK] Execution - User Execution: Malicious File [T1204.002] | [MITRE ATT&CK] T1059.006 - Command and Scripting Interpreter: Python | [MITRE ATT&CK] T1059.004 - Command and Scripting Interpreter: Unix Shell | [MITRE ATT&CK] T1574 - Hijack Execution Flow | [MITRE ATT&CK] Defense Evasion - Deobfuscate/Decode Files or Information [T1140] | [MITRE ATT&CK] T1564.001: Hidden Files and Directories | [MITRE ATT&CK] Defense Evasion - Indicator Removal: File Deletion [T1070.004] | [MITRE ATT&CK] T1036.005 - Masquerading: Match Legitimate Name Or Location | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information: Software Packing [T1027.002] | [MITRE ATT&CK] T1620 - Reflective Code Loading | [MITRE ATT&CK] Discovery - File and Directory Discovery [T1083] | [MITRE ATT&CK] Discovery - Process Discovery [T1057] | [MITRE ATT&CK] Picus: The System Information Discovery Technique Explained - MITRE ATT&CK T1082 | [MITRE ATT&CK] T1560.003 - Archive Collected Data: Archive Via Custom Method | [MITRE ATT&CK] Collection - Data Staged: Local Data Staging [T1074.001] | [MITRE ATT&CK] Command and Control - Application Layer Protocol: Web Protocols [T1071.001] | [MITRE ATT&CK] T1008 - Fallback Channels | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] Exfiltration - Exfiltration Over C2 Channel [T1041]
Signatures: YARA Rule: MacOS_Trojan_KandyKorn_a7bb6944 | MacOS_Trojan_HLoader_a3945baf | MacOS_Trojan_SugarLoader_e7e1d99c.
Tags: actor:Lazarus, source-country:KP, malware:KANDYKORN, malware-type:RAT, malware:SUGARLOADER, malware:HLOADER, malware-type:Loader, intrusion-set:REF7001, target-identity:Blockchain engineer, target-industry:Blockchain, target-industry:Cryptocurrency, technique:Execution flow hijacking, technique:Reflective loading, technique:Fileless execution, language:Python, language:Swift, file-type:Mach-O, target-system:macOS
NodeStealer Attacks on Facebook Take a Provocative Turn – Threat Actors Deploy Malvertising Campaigns to Hijack Users’ Accounts
(published: October 31, 2023)
First discovered in January 2023, NodeStealer was an infostealer primarily designed to hijack cookie sessions from web browsers, and take over Facebook accounts. Its newer version dubbed NodeStealer 2.1 was analyzed by Bitdefender researchers. From October 10 to October 20, 2023, at least 10 compromised Facebook business accounts were used in the attacks, serving malicious ads. The malicious ads specifically targeted males aged 45 and above from Europe, Africa, and the Caribbean. Clicking on lewd ads downloads an archive from either Bitbucket or Gitlab repositories containing a malicious EXE file (NodeStealer 2.1) designed to steal browser cookies and passwords. The Ad reach analysis points to the extent of 100,000 potential malware downloads.
Analyst Comment: For robust protection against Nodestealer, maintain updated anti-malware software and practice good online hygiene. Avoid engaging with suspicious links or ads, especially those promoting the downloading of photo albums from Bitbucket, Gitlab, or Dropbox. Indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Execution - User Execution [T1204] | [MITRE ATT&CK] T1555 - Credentials From Password Stores | [MITRE ATT&CK] T1539 - Steal Web Session Cookie
Tags: malware:NodeStealer, malware-type:Infostealer, detection:Gen:Variant.FacebookAd, target-identity:Facebook user, target-region:Europe, target-region:Africa, target-region:Caribbean, technique:Malvertising, abused:Bitbucket, abused:Gitlab, file-type:ZIP, file-type:EXE, target-system:Windows
FEATURED RESOURCES




