Anomali Cyber Watch: Updated Payload Targets Cisco IOS XE, OilRig Sends C2 Commands via Email, and More


The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Backdoors, DLL side-loading, Infostealers, Phishing, PowerShell scripts, and Zero-day vulnerabilities. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
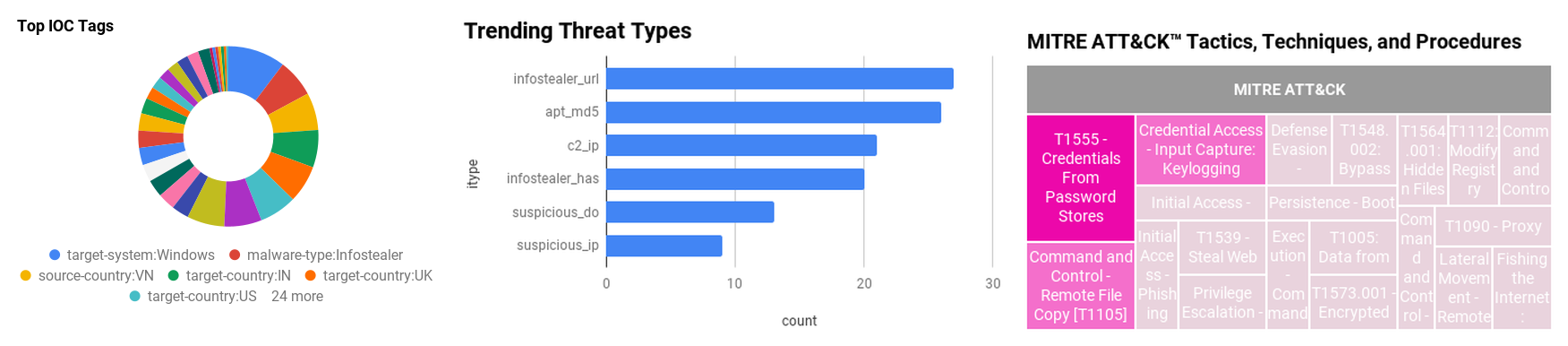
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
Active exploitation of Cisco IOS XE Software Web Management User Interface vulnerabilities
(last updated: October 23, 2023)
Starting September 18, 2023, a series of cyber attacks exploited zero-day vulnerabilities in the Web User Interface (Web UI) feature of Cisco Internetworking Operating System (IOS) XE software. The initial unusual behavior case was opened with Cisco on September 28, advisory was published on October 16, and fixes started to roll out on October 22, 2023. The first vulnerability (CVE-2023-20198) allows the initial access and a local user creation. The second (CVE-2023-20273) allows elevated privilege to root and writing the implant to the file system. Researchers were able to detect over 50,000 infected devices but after October 20, 2023, the observed number started to drastically drop as the attackers updated the payload to include a preliminary check for the HTTP Authorization header.
Analyst Comment: If you have Cisco IOS XE device(s) with ip http server or ip http secure-server configured, apply the available security patches. It is crucial to check if any suspicious user account was created on your systems. Suspicious network indicators used in the deployment of these exploits are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190]
Tags: target-software:Cisco IOS XE, vulnerability:CVE-2023-20198, vulnerability:CVE-2023-20273, vulnerability-type:Zero-day, vulnerability-type:RCE, vulnerability-type:Privilege escalation, technique:User creation
DarkGate Malware Campaign
(published: October 23, 2023)
An unidentified Vietnamese cybercrime group has employed phishing archive lures, disguising them as job offers and salary details, to target users in India, the UK, and the US. Between August and September 2023, researchers from WithSecure uncovered that this group utilized similar lures and delivery methods to install various commodity infostealer malware, including DarkGate, Ducktail, Lobshot, and Redline stealer. These separate attacks were linked through identifiable metadata in the PDF, LNK, and MSI files. These infections allowed the attackers to gain control of the target machines, exfiltrate credentials, with a specific emphasis on Facebook business accounts, and execute fraudulent ad campaigns.
Analyst Comment: Cybercrime marketplaces enable threat actors to swiftly shift between different malware-as-a-service offerings, while security researchers can employ metadata and other tactics, techniques, and procedures (TTPs) to trace the attackers across various attack chains. All known indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Initial Access - Phishing [T1566] | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] T1555 - Credentials From Password Stores | [MITRE ATT&CK] T1539 - Steal Web Session Cookie
Tags: source-country:VN, target-industry:Digital marketing, target-identity:Facebook business user, malware:DarkGate, malware:Ducktail stealer, malware:Lobshot, malware:Redline stealer, malware-type:Infostealer, malware-type:RAT, target-country:UK, target-country:US, target-country:IN, impersonated:Corsair, abused:Google Drive, abused:Dropbox, open-port:2351, file-type:DOCX, file-type:EXE, file-type:LNK, file-type:MSI, file-type:PDF, file-type:RAR, file-type:SCR, file-type:VBS, file-type:ZIP, target-system:Windows
Double Trouble: Quasar RAT's Dual DLL Sideloading in Focus
(published: October 20, 2023)
A new campaign utilizes malicious MSI files and chained DLL side-loading to deliver QuasarRAT, a lightweight remote administration tool that has been available on GitHub since at least 2014. This tool is capable of various functions such as gathering system data, running applications, transferring files, recording keystrokes, taking screenshots or camera captures, recovering system passwords, and overseeing operations like File Manager, Startup Manager, Remote Desktop, and executing shell commands. In October 2023, Uptycs researchers discovered a new multi-stage infection chain delivering QuasarRAT following the DLL sideloading utilizing two commonly-trusted Microsoft files: ctfmon.exe and calc.exe. The initial malicious MSI file contained a malicious DLL and ctfmon.exe renamed to eBill-997358806.exe to prompt execution and DLL side-loading. Decryption of the resource data of the malicious DLL leads to FileDownloader.exe being injected into regasm.exe and unzipping files for the second DLL side-loading. Calc.exe side-loads the malicious Secure32.dll leading to the delivery of the QuasarRAT payload via process hollowing of a second regasm.exe instance.
Analyst Comment: The use of two DLL side-loading attacks in one infection chain can arguably be described as a dual DLL sideloading technique. The complex attack chain even in a context of the commodity malware may indicate an advanced threat actor. Indicators associated with this QuasarRAT campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Privilege Escalation - Hijack Execution Flow: DLL Side-Loading [T1574.002] | [MITRE ATT&CK] Defense Evasion - Masquerading [T1036] | [MITRE ATT&CK] T1548.002: Bypass User Access Control | [MITRE ATT&CK] Persistence - Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder [T1547.001] | [MITRE ATT&CK] Execution - Command and Scripting Interpreter: Windows Command Shell [T1059.003] | [MITRE ATT&CK] T1555 - Credentials From Password Stores | [MITRE ATT&CK] T1005: Data from Local System | [MITRE ATT&CK] T1573.001 - Encrypted Channel: Symmetric Cryptography | [MITRE ATT&CK] T1564.001: Hidden Files and Directories | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] Credential Access - Input Capture: Keylogging [T1056.001] | [MITRE ATT&CK] T1112: Modify Registry | [MITRE ATT&CK] Command and Control - Standard Non-Application Layer Protocol [T1095] | [MITRE ATT&CK] Command and Control - Non-Standard Port [T1571] | [MITRE ATT&CK] T1090 - Proxy | [MITRE ATT&CK] Lateral Movement - Remote Services: Remote Desktop Protocol [T1021.001] | [MITRE ATT&CK] Fishing the Internet: LOLBin Attacks With Scheduled Tasks (T1053.005) and How To Detect Them | [MITRE ATT&CK] T1553.002 - Subvert Trust Controls: Code Signing | [MITRE ATT&CK] Picus: The System Information Discovery Technique Explained - MITRE ATT&CK T1082 | [MITRE ATT&CK] T1614 - System Location Discovery | [MITRE ATT&CK] Discovery - System Network Configuration Discovery [T1016] | [MITRE ATT&CK] Discovery - System Owner/User Discovery [T1033] | [MITRE ATT&CK] T1552.001 - Unsecured Credentials: Credentials In Files | [MITRE ATT&CK] T1125 - Video Capture
Tags: technique:DLL side-loading, malware:QuasarRAT, malware:CinaRAT, malware:Yggdrasil, abused:calc.exe, abused:ctfmon.exe, abused:regasm.exe, technique:Process hollowing, file-type:BAT, file-type:DLL, file-type:EXE, file-type:MSI, target-system:Windows
Crambus: New Campaign Targets Middle Eastern Government
(published: October 19, 2023)
The OilRig (APT34, Crambus, Helix Kitten) Iranian-sponsored group has targeted a number of countries in the Middle East, as well as Albania and the USA. Symantec researchers have discovered an eight-month-long attack against an unnamed government in the Middle East. From February to September 2023, the group had deployed four custom malwares. Backdoor.Tokel is used to execute arbitrary PowerShell commands and download files, Trojan.Dirps - to enumerate files and run PowerShell commands, Infostealer.Clipog - to steal clipboard data and logs keystrokes, and Backdoor.PowerExchange - to use an Exchange Server to receive PowerShell commands via specially-crafted emails, write files, and steal data. OilRig has also used Mimikatz to dump credentials, and were enabling remote access by modifying Windows firewall rules and using Plink to enable remote access via RDP and modifications in port-forwarding.
Analyst Comment: The Iranian espionage group OilRig continues to pose a significant threat to organizations worldwide, particularly in the Middle East. Network defenders are advised to establish a baseline for typical running processes and monitor for remote access patterns that are not common in the organization. All known indicators associated with this campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] T1059.001: PowerShell | [MITRE ATT&CK] Command and Control - Encrypted Channel: Asymmetric Cryptography [T1573.002] | [MITRE ATT&CK] T1555 - Credentials From Password Stores | [MITRE ATT&CK] Credential Access - Input Capture: Keylogging [T1056.001] | [MITRE ATT&CK] Credential Access - OS Credential Dumping [T1003] | [MITRE ATT&CK] T1572 - Protocol Tunneling | [MITRE ATT&CK] Privilege Escalation - Valid Accounts [T1078]
Tags: actor:OilRig, malware:PowerExchange, malware:Backdoor.Tokel, malware-type:Backdoor, malware:Trojan.Dirps, malware-type:Trojan, malware:Infostealer.Clipog, malware-type:Infostealer, malware:Mimikatz, malware-type:Credential dumping, malware:Plink, malware-type:Tunneling, target-region:Middle East, source-country:IR, target-industry:Government, actor:Crambus, actor:APT34, actor:Crambus, actor:Helix Kitten, technique:PowerShell, technique:RDP, technique:Proxy, file-type:EXE, file-type:PS1, target-system:Windows
Hamas Application Infrastructure Reveals Possible Overlap with TAG-63 and Iranian Threat Activity
(published: October 19, 2023)
Active since at least 2011, Hamas-linked cyber espionage group TAG-63 (AridViper, APT-C-23, Desert Falcon), has targeted a wide range of entities globally, including government, military, financial, media, education, energy, and research and policy entities. The group is known for using the Micropsia malware and some specific domain registration techniques such as use of English-language names. Record Future analysts were able to find infrastructure overlap between TAG-63 and the Hamas’s al-Qassam Brigades Android application shared in October 2023. The analysis suggests that Hamas may be working with groups or individuals outside of Gaza, potentially including in Iran, to keep its news site available online. Researchers have uncovered previously-undetected website spoofing the World Organization Against Torture (OMCT), but the exact attack chain is not currently known.
Analyst Comment: Infrastructure overlap confirms that TAG-63 shares infrastructure resources with the rest of the Hamas organization. Many organizations can be potentially under attack in relation to the military conflict in the Middle East. The risks range from simple website defacements to advanced cyberespionage intrusions. Suspicious indicators associated with the researched TAG-63/Hamas infrastructure are available in the Anomali platform.
MITRE ATT&CK: [MITRE ATT&CK] T1583.001 - Acquire Infrastructure: Domains | [MITRE ATT&CK] T1498 - Network Denial Of Service
Tags: actor:TAG-63, malware:Micropsia, actor:Giant's-PS, technique:Defacing, technique:DDoS, actor:AridViper, actor:APT-C-23, actor:Desert Falcon, actor:Hamas, actor:al-Qassam Brigades, actor:Islamic Revolutionary Guard Corps, source-region:Gaza, source-country:IR, source-country:PS, target-country:IL, target-country:PS, target-industry:Government, target-industry:Defense, target-industry:Military, target-industry:Financial, target-industry:Media, target-industry:Education, target-industry:Energy, target-industry:Research
FEATURED RESOURCES

The Silence Before the Storm: Why Saudi Arabia's Financial Sector Faces Its Most Dangerous Cyber Threat Window in a Decade



