Anomali Cyber Watch: Volt Typhoon Maintained Access to US Critical Infrastructure, New MoqHao Variants Launch Automatically, and More.


The various threat intelligence stories in this iteration of the Anomali Cyber Watch discuss the following topics: APT, Backdoors, China, Proxying, Smishing, Vulnerabilities, and Worms. The IOCs related to these stories are attached to Anomali Cyber Watch and can be used to check your logs for potential malicious activity.
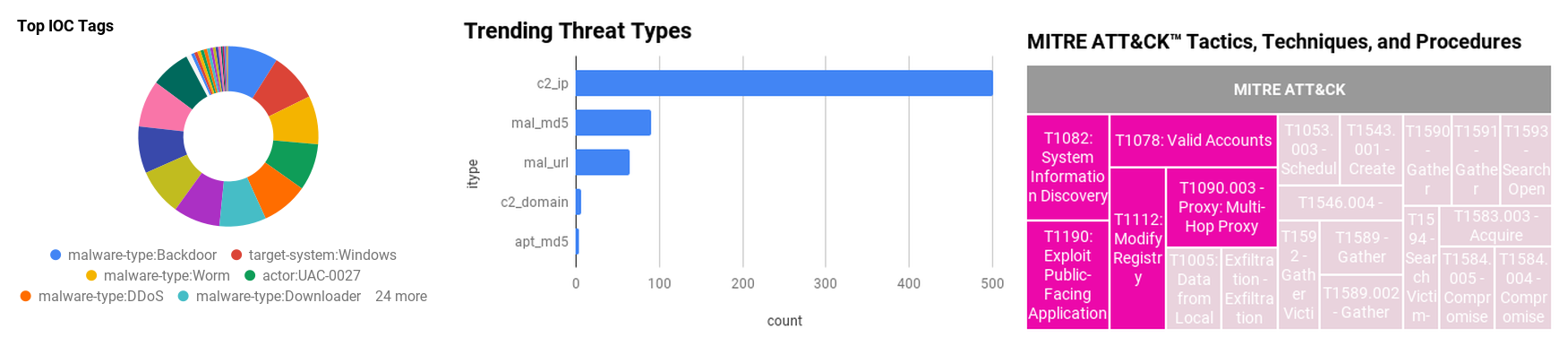
Figure 1 - IOC Summary Charts. These charts summarize the IOCs attached to this magazine and provide a glimpse of the threats discussed.
Trending Cyber News and Threat Intelligence
New MacOS Backdoor Written in Rust Shows Possible Link with Windows Ransomware Group
(published: February 8, 2024)
Bitdefender has discovered a new macOS backdoor written in Rust, dubbed RustDoor. This malware has been circulating since November 2023. RustDoor impersonates Visual Studio and supports both Intel and Arm architectures. RustDoor has the ability to harvest and exfiltrate files, as well as gather details about the infected machine. This backdoor employs four persistence mechanisms: cronjobs, LaunchAgents, modifying the ~/.zshrc file, and adding the binary to the dock. Bitdefender has identified several variants of the malware, all featuring the same backdoor functionality but with minor variations. While the exact attribution is incomplete, three out of the four RustDoor C2 servers have been previously associated with ALPHV/BlackCat ransomware campaigns targeting Windows clients.
Analyst Comment: Users should install only updates from the official channels, and treat social media and advertisement links with additional suspicion. Organizations that publish applications for their customers are invited to use Anomali Premium Digital Risk Protection to discover rogue, malicious apps impersonating your brand that security teams typically do not search or monitor. All known indicators associated with RustDoor are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Picus: The System Information Discovery Technique Explained - MITRE ATT&CK T1082 | [MITRE ATT&CK] T1005: Data from Local System | [MITRE ATT&CK] Exfiltration - Exfiltration Over C2 Channel [T1041] | [MITRE ATT&CK] T1053.003 - Scheduled Task/Job: Cron | [MITRE ATT&CK] T1543.001 - Create or Modify System Process: Launch Agent | [MITRE ATT&CK] T1546.004 - Event Triggered Execution: Unix Shell Configuration Modification
Tags: malware:RustDoor, detection:Trojan.MAC.RustDoor, malware-type:Backdoor, actor:ALPHV, technique:cronjobs, technique:LaunchAgents, language:Rust, target-system:MacOS
PRC State-Sponsored Actors Compromise and Maintain Persistent Access to U.S. Critical Infrastructure
(published: February 7, 2024)
The U.S. security agencies and their Five Eyes alliance partners have issued a joint advisory regarding activity of the China-sponsored Volt Typhoon (BRONZE SILHOUETTE, Dev-0391, Insidious Taurus, UNC3236, Vanguard Panda, and Voltzite) group. Volt Typhoon is likely seeking to position itself on IT networks for potential disruptive or destructive cyberattacks against US critical infrastructure. The group has compromised the IT environments of multiple US critical infrastructure organizations, primarily in the communications, energy, transportation, and water and wastewater industries. The group uses living off the land (LOTL) techniques, which allows them to camouflage their malicious activity with typical system and network behavior. Observed activities included exploiting publicly-facing vulnerabilities, implanting Fast Reverse Proxy (FRP), and leveraging Mimikatz, Impacket, and PSExec. Volt Typhoon has maintained access and footholds within some victim IT environments for at least five years.
Analyst Comment: Network defenders should apply patches for internet-facing systems prioritizing networking appliances from Fortinet, Ivanti Connect Secure, NETGEAR, Citrix, and Cisco. For critical systems, such as industrial control systems, measure the baseline of normal operations and network traffic, and triage anomalies. Host-based indicators for reverse proxy tools associated with Volt Typhoon campaigns are available in the Anomali platform for ongoing infections and historical reference.
MITRE ATT&CK: [MITRE ATT&CK] T1592 - Gather Victim Host Information | [MITRE ATT&CK] T1589 - Gather Victim Identity Information | [MITRE ATT&CK] T1589.002 - Gather Victim Identity Information: Email Addresses | [MITRE ATT&CK] T1590 - Gather Victim Network Information | [MITRE ATT&CK] T1591 - Gather Victim Org Information | [MITRE ATT&CK] T1593 - Search Open Websites/Domains | [MITRE ATT&CK] T1594 - Search Victim-Owned Websites | [MITRE ATT&CK] T1583.003 - Acquire Infrastructure: Virtual Private Server | [MITRE ATT&CK] T1584.005 - Compromise Infrastructure: Botnet | [MITRE ATT&CK] T1584.004 - Compromise Infrastructure: Server | [MITRE ATT&CK] T1587.004 - Develop Capabilities: Exploits | [MITRE ATT&CK] T1588.005 - Obtain Capabilities: Exploits | [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] Initial Access - External Remote Services [T1133] | [MITRE ATT&CK] picus-security: The Most Used ATT&CK Technique — T1059 Command and Scripting Interpreter | [MITRE ATT&CK] T1059.001: PowerShell | [MITRE ATT&CK] T1059.004 - Command and Scripting Interpreter: Unix Shell | [MITRE ATT&CK] Picus: T1047 Windows Management Instrumentation of the MITRE ATT&CK Framework | [MITRE ATT&CK] Privilege Escalation - Valid Accounts [T1078] | [MITRE ATT&CK] Privilege Escalation - Exploitation for Privilege Escalation [T1068] | [MITRE ATT&CK] T1006 - Direct Volume Access | [MITRE ATT&CK] T1070.009 - Indicator Removal: Clear Persistence | [MITRE ATT&CK] Defense Evasion - Indicator Removal: Clear Windows Event Logs [T1070.001] | [MITRE ATT&CK] Defense Evasion - Indicator Removal: File Deletion [T1070.004] | [MITRE ATT&CK] T1036.005 - Masquerading: Match Legitimate Name Or Location | [MITRE ATT&CK] T1112: Modify Registry | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information: Software Packing [T1027.002] | [MITRE ATT&CK] T1218 - Signed Binary Proxy Execution | [MITRE ATT&CK] T1110.002 - Brute Force: Password Cracking | [MITRE ATT&CK] T1555 - Credentials From Password Stores | [MITRE ATT&CK] T1555.003 - Credentials from Password Stores: Credentials From Web Browsers | [MITRE ATT&CK] Credential Access - OS Credential Dumping: LSASS Memory [T1003.001] | [MITRE ATT&CK] Credential Access - OS Credential Dumping: NTDS [T1003.003] | [MITRE ATT&CK] T1552 - Unsecured Credentials | [MITRE ATT&CK] T1552.004 - Unsecured Credentials: Private Keys | [MITRE ATT&CK] T1087.001 - Account Discovery: Local Account | [MITRE ATT&CK] Discovery - Application Window Discovery [T1010] | [MITRE ATT&CK] Discovery - Browser Information Discovery [T1217] | [MITRE ATT&CK] Discovery - File and Directory Discovery [T1083] | [MITRE ATT&CK] Discovery - Network Service Discovery[T1046] | [MITRE ATT&CK] T1120 - Peripheral Device Discovery | [MITRE ATT&CK] T1069 - Permission Groups Discovery | [MITRE ATT&CK] Discovery - Process Discovery [T1057] | [MITRE ATT&CK] T1012: Query Registry | [MITRE ATT&CK] T1518 - Software Discovery | [MITRE ATT&CK] Picus: The System Information Discovery Technique Explained - MITRE ATT&CK T1082 | [MITRE ATT&CK] T1614 - System Location Discovery | [MITRE ATT&CK] T1016.001 - System Network Configuration Discovery: Internet Connection Discovery | [MITRE ATT&CK] Discovery - System Owner/User Discovery [T1033] | [MITRE ATT&CK] T1007 - System Service Discovery | [MITRE ATT&CK] T1124 - System Time Discovery | [MITRE ATT&CK] T1563 - Remote Service Session Hijacking | [MITRE ATT&CK] Picus: T1021 Remote Services of the MITRE ATT&CK Framework | [MITRE ATT&CK] Lateral Movement - Remote Services: Remote Desktop Protocol [T1021.001] | [MITRE ATT&CK] T1550 - Use Alternate Authentication Material | [MITRE ATT&CK] T1078.004 - Valid Accounts: Cloud Accounts | [MITRE ATT&CK] Collection - Archive Collected Data [T1560] | [MITRE ATT&CK] T1560.001 - Archive Collected Data: Archive Via Utility | [MITRE ATT&CK] T1074 - Data Staged | [MITRE ATT&CK] Collection - Screen Capture [T1113] | [MITRE ATT&CK] Command and Control - Encrypted Channel [T1573] | [MITRE ATT&CK] Command and Control - Remote File Copy [T1105] | [MITRE ATT&CK] T1090 - Proxy | [MITRE ATT&CK] T1090.001 - Proxy: Internal Proxy | [MITRE ATT&CK] T1090.003 - Proxy: Multi-Hop Proxy | [MITRE ATT&CK] Exfiltration - Exfiltration Over Alternative Protocol [T1048]
Tags: actor:Volt-Typhoon, actor:Vanguard-Panda, actor:BRONZE-SILHOUETTE, actor:Dev-0391, actor:UNC3236, actor:Voltzite, actor:Insidious-Taurus, source-country:CN, target-country:US, target-industry:Critical-infrastructure, target-industry:Communications, target-industry:Energy, target-industry:Transportation, target-industry:Water, target-industry:Wastewater, tool:Mimikatz, tool:Fast-reverse-proxy, tool:PSExec, tool:Putty, technique:LOTL, target-system:Windows
Raspberry Robin Keeps Riding The Wave Of Endless 1-Days
(published: February 7, 2024)
Check Point researchers have analyzed the evolution of the Raspberry Robin worm, a malware first reported in 2021. The worm is part of a larger malware ecosystem and acts as an initial access broker for additional malware deployment by other crime groups. Raspberry Robin has been updated with new features and sandbox evasion techniques. The worm added hooking check, NtTraceEvent hooking, Shutdown evasion, Remote Desktop evasion, and UWF filter evasion. The authors of Raspberry Robin have been acquiring local privilege escalation (LPE) exploits following the public disclosure of vulnerabilities. The speed of exploit adoption is increasing, with CVE-2021-1732 being incorporated a year after disclosure, CVE-2023-29360 in two months, and CVE-2023-36802 the very next month. Raspberry Robin recent campaigns are characterized by the use of Discord to host malicious files, and V3 domains Onion domains for C2 communication.
Analyst Comment: The Raspberry Robin worm is evolving and becoming stealthier, making it a significant threat in the cyber landscape. Keep your systems updated. All known indicators associated with this campaign are available in the Anomali platform and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Execution - User Execution: Malicious File [T1204.002] | [MITRE ATT&CK] Privilege Escalation - Hijack Execution Flow: DLL Side-Loading [T1574.002] | [MITRE ATT&CK] T1497 - Virtualization/Sandbox Evasion | [MITRE ATT&CK] T1090.003 - Proxy: Multi-Hop Proxy
Tags: malware:Raspberry-Robin, detection:Trojan.Wins.RaspberryRobin, malware-type:Worm, actor:EvilCorp, actor:TA505, abused:Discord, abused:TOR,vulnerability:CVE-2021-1732, vulnerability:CVE-2023-29360, vulnerability:CVE-2023-36802, vulnerability-type:LPE, file-type:DLL, file-type:EXE, file-type:RAR, target-system:Windows
MoqHao Evolution: New Variants Start Automatically Right after Installation
(published: February 7, 2024)
McAfee researchers have discovered a new variant of the MoqHao (XLoader, Wroba) Android malware. This malware is operated by a financially motivated threat actor named Roaming Mantis. The latest variant of this malware is likely targeting Asia (Japan, India, and South Korea) and Europe (France and Germany). The malware is primarily distributed through SMS text containing a URL shortener link that leads to a site delivering an Android APK installation file. Recent variants of XLoader can automatically launch after installation, running stealthily in the background to siphon sensitive user information. The malware impersonates the Chrome web browser by using Unicode characters in app names to visually appear as “Chrome,” tricking users into approving risky permissions.
Analyst Comment: Users should receive training to identify social engineering techniques and smishing messages. Avoid installing applications resulting from clicking on unsolicited links. All known host-based indicators associated with the latest MoqHao campaign are available in the Anomali platform for retrospective analysis.
MITRE ATT&CK: [MITRE ATT&CK] T1533 - Data From Local System | [MITRE ATT&CK] T1636.004 - Protected User Data: Sms Messages | [MITRE ATT&CK] T1437.001 - Application Layer Protocol: Web Protocols
Tags: malware:MoqHao, malware:XLoader, malware:Wroba, detection:Android/MoqHao, actor:Roaming Mantis, target-region:Asia, target-region:Europe, target-country:JP, target-country:IN, target-country:KR, target-country:FR, target-country:DE, impersonated:Chrome, abused:Pinterest, technique:Smishing, technique:WebSocket, target-system:Android
UAC-0027: DirtyMoe (PurpleFox) Infected over 2000 Computers in Ukraine
(published: January 31, 2024)
The Ukrainian government's Computer Emergency Response Team (CERT-UA) has been assisting a state enterprise following a mass infection of computer systems by the DirtyMoe (PurpleFox) malware. DirtyMoe, a modular Windows botnet malware, was first spotted in 2018. It can be used as a downloader, offers its operators backdoor and rootkit capabilities, and can also act as a distributed denial of service (DDoS) bot. DIRTYMOE acts as a worm, self-propagating using valid credentials and/or trying to exploit both local and external computers. The incident in Ukraine, attributed to previously unknown actor UAC-0027, affected at least 2,000 computers. During January 20-31, 2024, about 20 new C2 IP addresses were added daily, totaling 486 C2 IPs, with the vast majority belonging to compromised equipment located in China.
Analyst Comment: Network defenders can monitor for suspicious outgoing connections made to "high" (10000+) network ports. After cleaning, to avoid DIRTYMOE re-infection, enable the firewall on Windows and block incoming traffic from ports 135, 137, 139, and 445. All known indicators associated with this DIRTYMOE campaign are available in the Anomali platform, and customers are advised to block these on their infrastructure.
MITRE ATT&CK: [MITRE ATT&CK] Execution - User Execution [T1204] | [MITRE ATT&CK] Defense Evasion - Obfuscated Files or Information [T1027] | [MITRE ATT&CK] Defense Evasion - Deobfuscate/Decode Files or Information [T1140] | [MITRE ATT&CK] Privilege Escalation - Valid Accounts [T1078] | [MITRE ATT&CK] Initial Access - Exploit Public-Facing Application [T1190] | [MITRE ATT&CK] T1112: Modify Registry
Tags: malware:DirtyMoe, malware:PurpleFox, malware-type:Backdoor, malware-type:DDoS, malware-type:Downloader, malware-type:Rootkit, malware-type:Worm, actor:UAC-0027, target-country:UA, open-port:135, open-port:137, open-port:139, open-port:445, target-system:Windows
FEATURED RESOURCES




