The New and Improved Anomali Threatstream Splunk App
We’re thrilled to announce the new and improved Anomali Threatstream Commercial Splunk App 6.0. In this post, I want to cover some of the cool new features we added in this release -- Enterprise Security integrations, supercharged searches, context relevant threat intelligence, customised dashboards...).
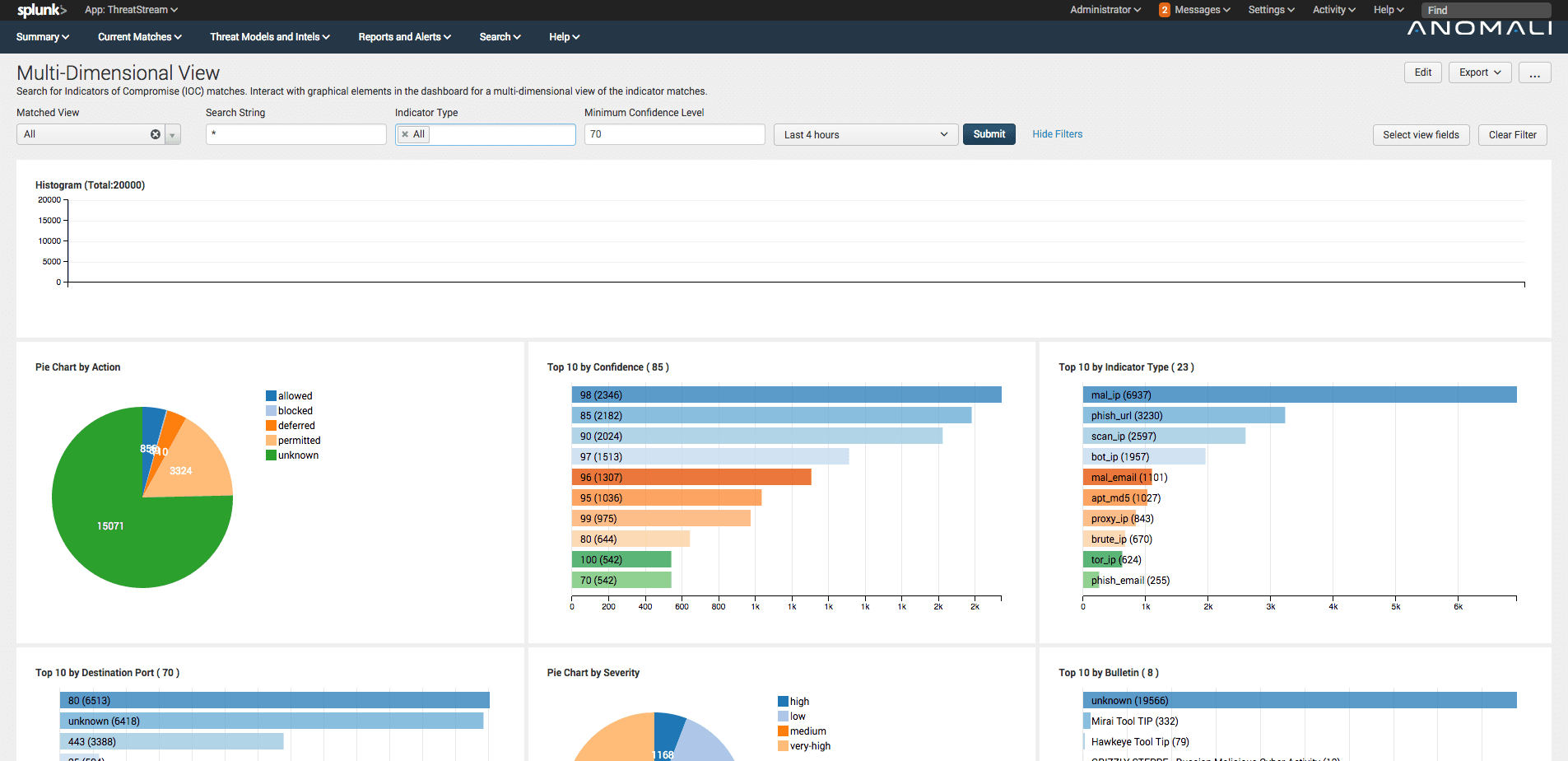

<p>Over the past few months I have had the opportunity to talk to so many Anomali customers using our <a href="https://splunkbase.splunk.com/app/3443/">Splunk Commercial App</a> to seamlessly match their data against Threatstream Indicators of Compromise (IOCs). It has been great to see the excitement around the dashboards and insights our app offers that have been able to immediately identify malicious activity then significantly reduce the investigation and troubleshooting time for analysts.</p><p>Though the variation of how users interact and use Splunk Apps for security, fraud, and compliance use-cases vary significantly -- after all, no organisation is identical. As such, we've received lots of customer feedback for new features (<a href="mailto:splunk@anomali.com?subject=Please%20build%20this...">email us your requests</a>).</p><p>Today we’re thrilled to announce the new and improved Anomali Threatstream Commercial Splunk App 6.0. In this post, I want to cover some of the cool new features we added in this release.</p><h2>Expanded context-relevant threat intelligence</h2><p><img alt="Expanded context-relevant threat intelligence" src="https://cdn.filestackcontent.com/wl3llKkiT2uwzt729rMc"/></p><p>Threatstream users know and love the context provided for each IOC, including actor and threat bulletin information. We've now added actor and threat bulletin information to our Splunk App. <strong>You can now understand if you're suffering a more serious targeted attack from known advisories to help you better prioritise matches</strong>.</p><h2>Enhanced and Updated Dashboards</h2><h2><img alt="Enhanced and Updated Dashboards" src="https://cdn.filestackcontent.com/QqxeGxcwS3mPaGr4Oyut"/></h2><p>To help users investigate IOC matches we've included lots of new dashboards and views, including the ability to filter and pivot on panels. Ultimately, you want to review IOC matches as quickly and accurately as possible. <strong>We've reduced the number of steps required for you to analyse any potential threats</strong>.</p><h2>Integration with Splunk Enterprise Security</h2><p><img alt="" src="https://cdn.filestackcontent.com/otbf2eG4Qd675UnLNMFt"/></p><p>Splunk's Enterprise Security App is one of the most widely used SIEM products on the market today. Many of our customers utilise the app's Incident Review functionality. To avoid disrupting existing workflows, <strong>users can now lookup events that triggered a notable event against IOCs, all within Splunk's Enterprise Security App.</strong></p><h2>Supercharged searches</h2><h2><img alt="Supercharged searches" src="https://cdn.filestackcontent.com/IG8XTvGxTIOXlGmwaPVA"/></h2><p>All our IOCs are now stored in Splunk KV Stores. <em>I won't bore you with the technical details here</em>, the important thing is you'll now see matches are performed much faster than in previous iterations of our app. <strong>You can now respond to incidents as they happen</strong>.</p><h2>Available to download now...</h2><p>Threatstream users can download the updated Anomali Threatstream Splunk Commercial App via <a href="https://ui.threatstream.com/downloads">the Threatstream download page here</a>.</p><p><a href="mailto:splunk@anomali.com?subject=Please%20build%20this...">Let us know what you want us to build next</a>...</p>
FEATURED RESOURCES

Anomali Cyber Watch
When “Quiet" Means Pre-Positioned: Why Iranian Cyber Threats Are More Dangerous Than Headlines Suggest

Anomali Cyber Watch


