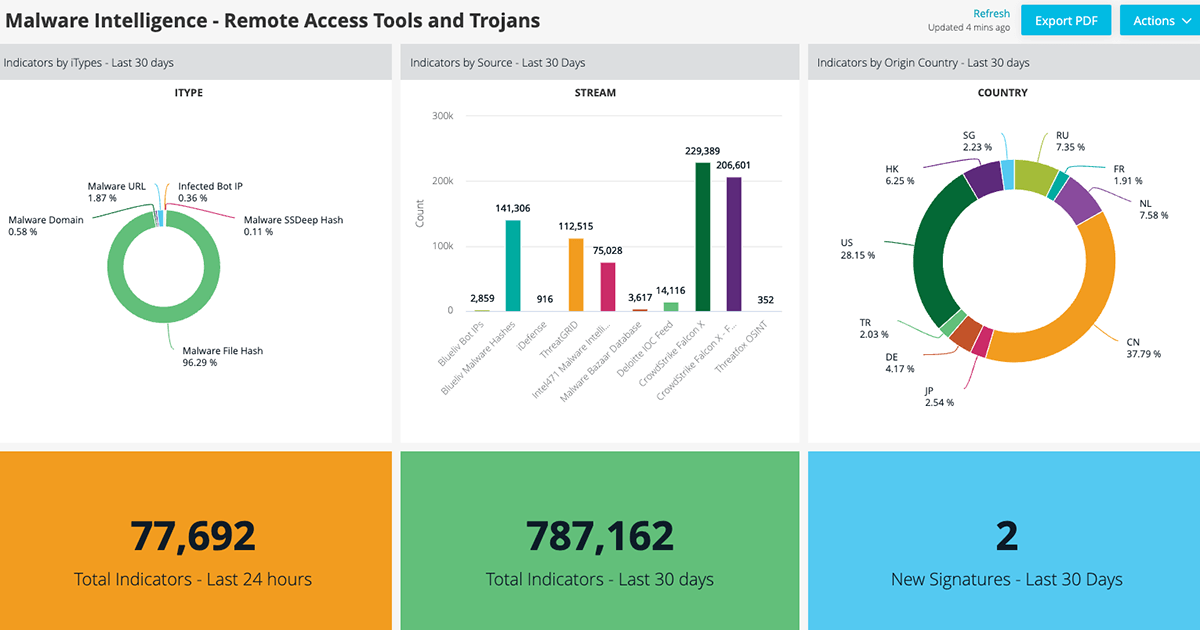

<p>Anomali Threat Research has released two, Malware Intelligence focused dashboards to assist cybersecurity and cyber threat intelligence professionals in organizing IOCs and strategic intelligence on relevant threats. These two dashboards are titled:</p> <ul> <li>Malware Intelligence - Ransomware</li> <li>Malware Intelligence - Remote Access Tools and Trojans</li> </ul> <p>Ransomware and remote access tools and trojans are malware types used by threat actors spanning all levels of sophistication, from cybercriminal to advanced persistent threat to nation-state. Ransomware threat actors continue to be highly active and generate significant amounts of illicit funds, and learning more about how these threat actors operate can assist in taking proactive measures against such attacks.</p> <p>Remote access tools are persistently abused by threat actors for malicious purposes. Knowing which tools the actors use and how they are used is important when making cybersecurity decisions to protect against this malware type; among numerous other variables.</p> <p>These Malware Intelligence dashboards help amalgamate relevant information into a centralized location to assist in providing crucial contextual information in addition to the most recent IOCs made available through commercial and open-source threat feeds that users manage on ThreatStream.</p> <p>Dashboards in ThreatStream provide a quick, digestible and timely source of key metrics on threat intelligence indicators. In ThreatStream you can access a number of different dashboard types: standard dashboards available out of the box; themed dashboards developed by the Anomali Threat Research Team; custom dashboards defined by by you; and specialized dashboards to support our Intelligence Initiatives or Lens+ specific data. From this month we greatly improve how an individual user can organize their dashboard views, enabling them to easily hide or show any dashboards available to them. Users show or hide any of the standard dashboards, as well as up to 10 other dashboards at any time. Management and ordering is now simplified so users can drag and drop visible dashboards to reorder according to priority and preference.</p> <h2>Key Capabilities</h2> <ul> <li>Users can now granularly manage their dashboards from across their organization and supplementary sources</li> <li>Dashboards can be drawn from a library created by / visible to the user</li> <li>Users can show / hide any standard ThreatStream dashboards</li> <li>User can develop up to 10 custom dashboards for display.</li> <li>Users will be able to drag and drop to edit the dashboard order and specify the user’s default dashboard (from April).</li> <li>Customers can still avail of the Custom and ATR themed dashboards as previously</li> </ul> <h2>Benefits</h2> <ul> <li>Easy management of the rich set of dashboards available in ThreatStream</li> <li>Quickly and easily access the right insights at the right time, in the right display order</li> <li>Note: This screen now uses our new user interface design style - we hope you like it!</li> </ul> <h2>Malware Intelligence - Ransomware</h2> <p>Pulls OSINT and primary intelligence feeds related to ransomware samples, actors who use ransomware, and TTPs associated with known ransomware families, among others, and displays the data in 10 widgets.</p> <p>Observables, IOCs, and threat models related to ransomware.</p> <p><img alt="Malware Intelligence - Ransomware Dashboard" src="https://cdn.filestackcontent.com/pPeFc8S5Qaa6bXKeDUu0"/></p> <h2>Malware Intelligence - Remote Access Tools and Trojans</h2> <p>Pulls OSINT and primary intelligence feeds related to remote access tool and trojan samples, actors who use these tools and trojans, and TTPs associated with known remote access tool and trojan families, among others, and displays the data in 10 widgets.</p> <p><img alt="Malware Intelligence - Remote Access Tools and Trojans Dashboard" src="https://cdn.filestackcontent.com/aQyqpOepRyIQwOaaJ9u0"/></p>
FEATURED RESOURCES

Anomali Cyber Watch
The Silence Before the Storm: Iran's Cyber War Has Moved From Warning to Confirmed Compromise

Anomali Cyber Watch


