Weekly Threat Briefing: Data Breach Exposes Trade Secrets of Carmakers GM, Ford, Tesla, Toyota

The intelligence in this week’s iteration discuss the following threats: APT, Data breach, Data leak, Malspam, Phishing, Ransomware, Spear phishing, Targeted attacks, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
CSE Malware Zlab – Chinese APT27’s Long-term Espionage Campaign in Syria is Still Ongoing (July 23, 2018)
Researchers from CSE Cybsec Z-Lab analyzed a public repository found by ESET security researcher Lukas Stefanko that contained some Android applications. The researchers’ analysis of a folder in the repository revealed that it contained an Android spyware associated to the Chinese Advanced Persistent Threat (APT) group “APT27” (Emissary Panda). The repository and its malware were identified to be targeting Syria, which is a known target for APT27.
Click here for Anomali recommendation
Data Breach Exposes Trade Secrets of Carmakers GM, Ford, Tesla, Toyota (July 21, 2018)
Security researchers at UpGuard CyberRisk uncovered that sensitive documents from over 100 different manufacturing companies were exposed on a publicly accessible server. The breach occurred through Level One Robotics where an rsync server allowed unrestricted access to secretive data. Over 157 gigabytes of data including trade secrets from corporations like GM, Telsa, and Toyota could be found if someone knew where to look. It is unclear whether any data was obtained by threat actors at the time of this article’s publication.
Click here for Anomali recommendation
Unit 42 Finds New Mirai and Gafgyt IOT/Linux Botnet Campaigns (July 20, 2018)
Palo Alto Networks Unit 42 researchers have published a report discussing multiple malware campaigns in which the malware is based off of the publicly available source code of the “Mirai” and “Gafgyt” Distributed Denial-of-Service (DDoS) malware. Researchers analyzed three campaigns. The first campaign is using the “Omni” malware, which is a Mirai variant, that was found to be using two exploits, registered as “CVE-2018-10561” (authentication bypass) and “CVE-2018-1562” (command injection). The second campaign involves the “Okane” malware that conducts brute force attacks that target “Camtron IP” cameras, “Control4” devices, and “ADC FlexWave Prism” devices that use default credentials. The third campaign that was analyzed was the “Hakai” malware, which is based off of Gafgyt, that was found to be launching Layer 7 (HTTP flood) DDoS attacks.
Click here for Anomali recommendation
Singapore Health Services Data Breach Exposes Info on 1.5 Million People (July 20, 2018)
The personal information of over 1.5 million patients of Singapore Health Services for the past three years was compromised following a data breach. The attackers deliberately targeted data regarding health information of the Singapore Prime Minister Lee Hsien Loong. The stolen data includes national registration identity numbers, names, birthdates, addresses, gender, and race information. Medication lists of at least 160,000 patients were also compromised. The attack is reported to have taken place between June 27, 2018 to July 4, 2018. It is believed to have been a state-sponsored attack, though there is no physical evidence to corroborate this.
Click here for Anomali recommendation
Microsoft Reveals First Known Russian Hacking Attempt Aimed at 2018 Midterms (July 19, 2018)
On Thursday July 19, 2018, Microsoft executive John Burt revealed at an election panel held the Aspen Security that Microsoft had detected the first known cyberattacks on U.S. election campaigns in 2018. Microsoft’s security team identified “a series” of phishing emails, which mimicked themes used in such emails from the 2016 election cycle, that were sent to 2018 midterm candidates. The emails bore resemblance to spear phishing emails that were distributed by the Russian Advanced Persistent Threat (APT) group “APT28” (Fancy Bear). Burt also said “we did discover that a fake Microsoft domain had been established as the landing page for phishing attacks,” and that the data indicated that at least three candidates were being targeted. Microsoft was able to take down the domain to stop this phishing campaign.
Click here for Anomali recommendation
Group-IB Investigating a New Daring Attack by MoneyTaker: Hacker Try to Steal $1 mln from the Bank (July 19, 2018)
The financially-motivated threat group “MoneyTaker” has been found to have launched an attack on the Russian bank “PIR Bank,” according to Group-IB researchers. MoneyTaker was able to steal funds worth approximately $1 million USD through the Russian Central Bank’s Automated Workstation client on July 3, 2018. The Central Bank’s Automated Workstation client is an interbank fund transfer system that is similar to the Society for Worldwide Interbank Financial Telecommunication (SWIFT) network. The Russian newspaper “Kommersant” reported that MoneyTake was able to steal around $920,000 USD, conservatively. Since this is the amount the bank gave to the newspaper, it is possible the actual amount is larger.
Click here for Anomali recommendation
Vulnerability Spotlight: Foxit PDF Reader JavaScript Remote Code Execution Vulns (July 19, 2018)
Two Use-After-Free vulnerabilities within the Foxit PDF Reader application have been disclosed by Cisco Talos. The first vulnerability, CVE-2018-3924, originates in the JavaScript engine of the Foxit application. If a threat actor invokes the “mailForm” method of the active document, arbitrary code can be executed by a threat actor. The other vulnerability, CVE-2018-3939, is a user-after-free exploitable that could result in remote code execution. This specific vulnerability is with the utilisation of “createTemplate” in an active document which also results in arbitrary code execution.
Click here for Anomali recommendation
Hackers Breach Network of LabCorp, US' Biggest Blood Testing Laboratories (July 18, 2018)
The largest blood testing laboratory in the United States, LabCorp, released a statement that their IT network suffered a breach. As a result, they had to shut down multiple portions of its entire system in an attempt to contain the breach and prevent it from propagating within the expansive network. It is unclear if they have been able to fully restore their systems at the time of the article’s publication. This has the potential to have severe repercussions because LabCorp plays a crucial part in the United States’ healthcare infrastructure being the primary diagnostic laboratory used across the US for hospitals, physicians, and testing facilities.
Click here for Anomali recommendation
The Return of Fantomas, or How We Deciphered Cryakl (July 17, 2018)
Belgian police were able to take control of the Command and Control (C2) servers of the “Cryakl” ransomware in February 2018 and subsequently gave Kaspersky Lab researchers the private keys. The researchers used the keys to update the “RakhniDecryptor” tool to assist individuals who have been affected by the malware. Cryakl has been active since at least 2014 and is distributed via emails with malicious attachments. Identified malicious attachments observed to be used to distribute Cryakl include the following: JS script loading a trojan, Office document with a malicious macro, and a PDF document with a link to an executable.
Click here for Anomali recommendation
Blackgear Cyberespionage Campaign Resurfaces, Abuses Social Media for C&C Communication (July 17, 2018)
Trend Micro researchers have discovered new malicious activity associated to the cyberespionage group called “Blackgear” (also known as Topgear, Comnie). The group, whose activity dates back to at least 2008, is known to have targeted multiple countries in past campaigns such as Japan, South Korea, and Taiwan with a focus on public sector agencies, high-technology industries, and telecommunications companies. In recent campaigns attributed to Blackgear, the group has been deploying the “Marade” downloader and the “Protux” backdoor. Researchers found that Blackgear changed the Command and Control (C2) communication for said malware to use encrypted configurations on blog and social media posts rather than hardcoded inside the malware. This allows the group to change C2 infrastructure quickly in attempts to stay undetected. The malware was found to be delivered via spam emails that contain a malicious decoy document.
Click here for Anomali recommendation
Telefónica Breach Leaves Data on Millions Exposed (July 16, 2018)
The Spanish telecommunications company “Telefónica” has confirmed that it was the target of a cyber-attack on June 16, 2018. The attack resulted in a data breach in which unknown threat actors were able to access a variety of Personally Identifiable Information (PII) belonging to “Movistar” (Telefónica’s broadband, landline, and pay-television service) customers. The exposed data consists of associated banks, addresses, call records, names, national ID numbers, and telephone numbers, among others. The data was found to be downloadable as an unencrypted spreadsheet. This is important to note because now that the Global Data Protection Regulation (GDPR) law is in effect because it mandates that data must be protected by end-to-end encryption. Therefore, Telefónica may be subject to a significant fine and, at the very least, will be subject to customer notifications regarding the data breach and follow-up in a potentially expensive manner.
Click here for Anomali recommendation
Magniber Ransomware Improves, Expands Within Asia (July 16, 2018)
The threat actors behind the “Magnitude” Exploit Kit (EK) have added some changes to the EK’s custom ransomware called “Magniber,” according to Malwarebytes Labs researchers. Magniber was first observed being distributed in the wild by Magnitude in October 2017. Researchers found that the actors incorporated an Adobe Flash vulnerability, registered as “CVE-2018-4878,” in April 2018 and most recently incorporated an Internet Explorer (IE) vulnerability, registered as “CVE-2018-8174.” In addition to the IE exploit, the Magniber ransomware has new obfuscation techniques and no longer requires a Command and Control server or hardcoded key for encryption. Furthermore, Magniber used to primarily target users in South Korea, but it has now been observed to target other, unnamed, Asia Pacific countries
Click here for Anomali recommendation
New Andariel Reconnaissance Tactics Hint At Next Targets (July 16, 2018)
Trend Micro and IssueMakersLab researchers have produced a report detailing new reconnaissance tactics that they attribute to the threat group “Andariel Group.” The Andariel Group is known to be a branch of the Advanced Persistent Threat (APT) group “Lazarus Group” (also known as HIDDEN COBRA) that is attributed to the Democratic People’s Republic of Korea (DPRK) government. Researchers found that on June 21 the group had injected a script on to the website of a Korean non-profit organization that would collect visitor’s information entered into said website. The collected data consisted of browser type, Flash Player version, multiple ActiveX objects, Silverlight version, and system language. This reconnaissance campaign lasted until June 27, 2018.
Click here for Anomali recommendation
DanaBot Riding Fake MYOB Invoice Emails (July 16, 2018)
A phishing campaign has been discovered impersonating the Australian software company “MYOB” (Mind Your Own Business). The emails purported to be from MYOB that claim that the recipient has a payment due and asks the recipient to “View Invoice.” If the View Invoice button is clicked, a zip archive is pulled down from what researcher believe to be a compromised FTP server of an unnamed Australian company. The zip archive contains a JavaScript downloader that requires the user to double-click to execute it. If executed, the JavaScript will launch a PowerShell command that would download the “DanaBot” malware. DanaBot is a banking trojan that was first discovered in May 2018 that focuses on stealing banking credentials that can be monetized in the future.
Click here for Anomali recommendation
Observed Threats
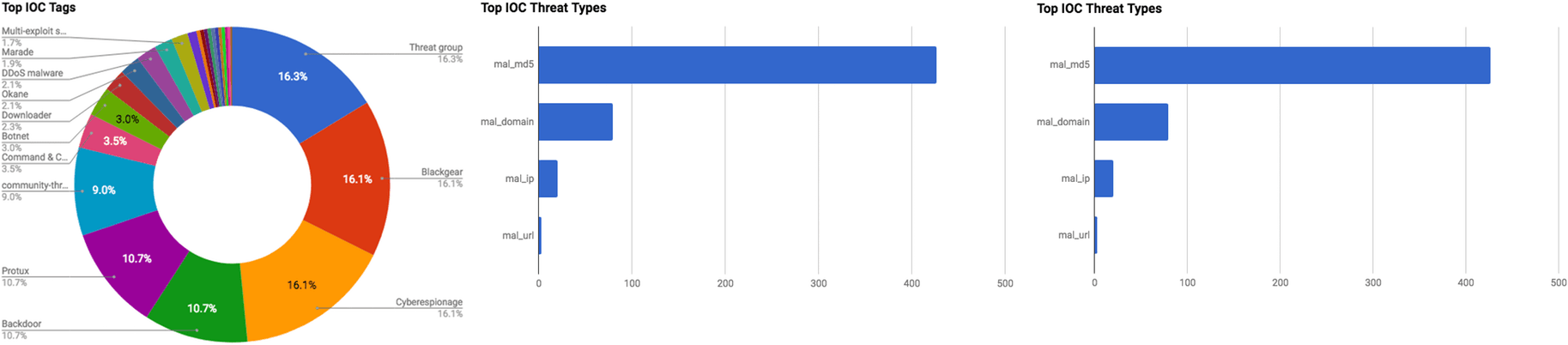
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. A ThreatStream account is required to view this section. Click here to request a trial.
APT28 The Advanced Persistent Threat (APT) group “APT28” is believed to be a Russian-sponsored group that has been active since at least 2007. The group displays high levels of sophistication in the multiple campaigns that they have been attributed to, and various malware and tools used to conduct the operations align with the strategic interests of the Russian government. The group is believed to operate under the Main Intelligence Directorate (GRU), the foreign intelligence agency of the Russian armed forces.
MoneyTaker Threat Group Targeting and Stealing Funds from Banks since 2016 A previously unknown, Russian-speaking threat group, dubbed “MoneyTaker,” is responsible for the theft of approximately $10 million USD from 18 banks, according to Group-IB researchers. The actors targeted ATMs operated by banks primarily located in the U.S. and Russia. The malicious activity is ongoing and is believed to have begun approximately 18 months ago. Researchers identified that the first attacks took place in the spring of 2016 against banks using the payment technology company “First Data’s” “STAR” network; STAR is a debit card processing and payment network. First Data has stated that “a number” of financial institutions on the STAR network had their credentials for administering debit cards compromised in early 2016. In addition, the company also said that it is actively investigating multiple incidents in which threat actors used the Society for Worldwide Interbank Financial Telecommunication (SWIFT) banking system to make illicit money transfers. However, the firm did not say if the SWIFT system was used during these incidents.
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



