Weekly Threat Briefing: Phishing Attack Uses Azure Blob Storage To Impersonate Microsoft
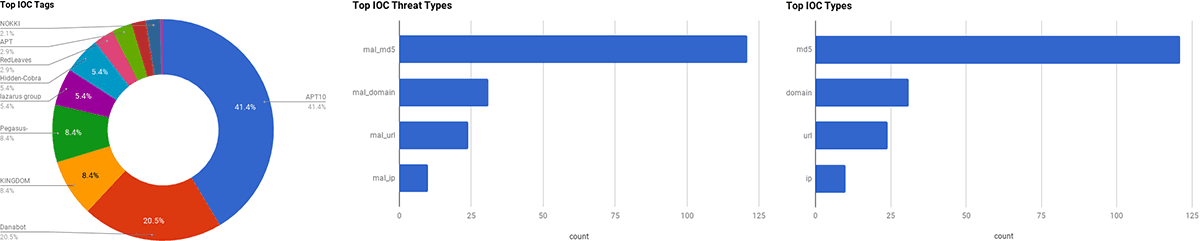

The intelligence in this week’s iteration discuss the following threats: APT38, Botnet, Data breach, Exploit kit, FIN7, Lazarus, Malware builder, Pegasus spyware, Spear phishing, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
PoC Attack Escalates MikroTik Router Bug To ‘As Bad As It Gets’ (October 7, 2018)
Security researchers from Tenable Research uncovered a new technique to exploit MikroTik routers utilising a vulnerability, registered as “CVE-2018-14847,” that had been previously patched. This vulnerability is an existing traversal bug in a system’s “Winbox,” which is a management component and Windows GUI application that MikroTik’s RouterOS software is on. This new attack technique exploits this vulnerability to allow unauthorised remote code execution. A threat actor can use the vulnerability to read and write files on a router after gaining illicit access to administrator credentials and can be utilised to get a root shell on the router. While a patch was released for this vulnerability in August 2018, approximately only 30% of routers were patched.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Graphical User Interface (T1061)
Gazorp Malware Builder Offers Free, Customized AZORult Attacks On The Dark Web (October 5, 2018)
Check Point researchers have discovered a new malware builder being sold on the Dark Web, called “Gazorp.” This malware builder allows for users to build samples of information-stealing trojan “AZORult” version 3.0 but requires users to create their own Command and Control (C2) server address to download the malware builder and help deploy the malware creation. On top of the usual keylogging abilities, Gazorp also includes a global heat map that provides country-by-country statistics and the ability to build a complex mutex base on several factors such as administrator, user, system, and guest authorities. Gazorp also includes a Telegram channel link that features the work of the Gazorp author to show users what they are currently working on to further develop the malware builder, as well as allows for users to make suggestions for the future versions and donations for the malware creators.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Custom Command and Control Protocol (T1094)
Viro Botnet Uses Spamming And Keylogging Capabilities To Spread Ransomware (October 4, 2018)
Security researchers at Trend Micro have observed a new ransomware campaign using the Viro Botnet to send malware to new victims via spam emails. The botnet is aimed at US citizens, but the ransom note is displayed in French after the user’s files are encrypted using RSA. The Viro botnet can utilise a victim’s email system contact list to spam potential new victims, as well as has keylogging abilities that can harvest credentials to send to the threat actor’s Command and Control (C2) server to download extra malware or files onto a victim’s machine. According to researchers, the C2 server appears to have been taken down, so it will no longer be able to encrypt user files even if they do get infected.
Click here for Anomali recommendation
Fallout Exploit Kit Now Installing The Kraken Cryptor Ransomware (October 4, 2018)
The “Fallout” exploit kit has been observed recently to be pushing the Kraken Cryptor ransomware, in lieu of the GandCrab ransomware that was previously tied to it. The exploit kit infects victims via compromised websites that redirect them through a series of gateways that ultimately take the user to a landing page where Fallout is hosted. The exploit kit then exploits a Windows VBScript vulnerability, registered as “CVE-2018-8174,” to install the “Kraken Cryptor” ransomware. This version of the ransomware encrypts the user’s files and creates random names with random extensions rather than using sequential numbers for file names and appending them with “Lock.onion.” The ransomware also creates a file about how to decrypt the files including the ransom amount of 0.256 BTC ($1676.52 USD). At the publication of this article, there is no way to decrypt the files for free.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Drive-by Compromise (T1189) | [MITRE ATT&CK] Scripting (T1064)
Pacific Northwest Burger Chain Hit By FIN7 (October 4, 2018)
Burger chain, Burgerville, announced that they had suffered a data breach affecting customer’s credit and debit card details used between September 2017 and September 2018. The breach has been attributed to Advanced Persistent Threat (APT) group “FIN7.” The chain was able to find the malware on their system after the FBI announced the arrest of three Ukrainian men tied to the group in August 2018. The chain believes that customer names, card numbers, expiration dates, and CVV numbers were compromised.
Click here for Anomali recommendation
Phishing Attack Uses Azure Blob Storage To Impersonate Microsoft (October 3, 2018)
A new Office 365 phishing campaign has been observed using the Microsoft Azure Blob storage. Threat actors are sending phishing emails containing a PDF attachment that pretends to be from a law firm in Denver, Colorado. The malicious document contains a button to download the PDF file that is supposed to be an unknown scanned document. If users click the “download” button, they are redirected to an HTML page (https://onedriveunbound80343.blob.core.windows.net) that appears to be an Office 365 login form stored on the Azure Blob storage. The HTML page even contains a signed SSL certificate that is issued by “Microsoft IT TLS CA 5” to feign legitimacy under suspicion. If a user enters in their Microsoft Office 365 credentials, that information is sent to the threat actors’ server.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Input Capture (T1056)
Alert (TA18-276B): Advanced Persistent Threat Activity Exploiting Managed Service Providers (October 3, 2018)
The National Cybersecurity and Communications Integration Center (NCCIC) in the United States has uncovered ongoing Advanced Persistent Threat (APT) activity that has been attempting to compromise international Managed Service Providers (MSPs). The APT group is allegedly using stolen credentials and pre-installed Windows-based system tools like command line scripts, such as PowerSploit and Robocopy, to gain access into these MSP networks. The goal is to steal data from these organisations to then use for geopolitical purposes. Whilst this article did not attribute the attack to a specific group, they linked to it a past attack in 2017 that was attributed to APT10, a Chinese government-linked threat group. This prompts many to link the two together since the tactics, techniques, and procedures (TTPs) are strikingly similar.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] PowerShell (T1086) | [MITRE ATT&CK] Scripting (T1064)
Bank Servers Hacked To Trick ATMs Into Spitting Out Millions In Cash (October 3, 2018)
North Korean Advanced Persistent Threat (APT) group “Hidden Cobra,” also known as Lazarus Group, have been observed launching a new attack on ATMs to get them to distribute cash by compromising a bank server. This campaign, dubbed, “FASTCash” compromises bank networks, though the initial attack vector is currently unknown, and infects them with Windows-based malware. The malware then affects the payment switch application server which allows the APT group to intercept transaction requests that are linked to the ATM cards and responds with a legitimate-looking validation response. The fake validation response bypasses actual authentication of the account balance and allows the ATM to give the actor the money. This campaign has been seen targeting banks in Africa and Asia, though it is also suspected that some US banks have also been targeted.
Click here for Anomali recommendation
APT38: Details On New North Korean Regime-Backed Threat Group (October 3, 2018)
Researchers at FireEye have uncovered what they believe to be a new active Advanced Persistent Threat (APT) group linked to the Democratic People’s Republic of Korea (DPRK) government, dubbed “APT38.” This APT group engages in financial crimes, targeting Society for Worldwide Interbank Financial Telecommunication (SWIFT) bank transactions, and at the time of this article’s writing, are believed to have stolen over $100 million USD from various financial institutions. APT38 is patient and, on average, they spend approximately 155 days in a victim’s network before actually engaging in the attack to understand the network layout and system, as well as gain the required permissions. The group targets individuals and infects them using watering hole websites and exploiting out-of-date versions of Apache Struts2 to execute code. The APT group deploys active and passive backdoors onto an infected machine to access the system, and then deploy fraudulent SWIFT transactions and alter the SWIFT history to avoid detection. The stolen money is transferred via several transactions sent to accounts in banks in many different countries to lessen suspicion. They then delete logs and execute disk-wiping malware to make forensic tracing more difficult. APT38 is seen as more aggressive and destructive compared to the other APT groups associated with North Korea.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Drive-by Compromise (T1189) | [MITRE ATT&CK] Valid Accounts (T1078)
DanaBot Gains Popularity and Targets US Organizations in Large Campaigns (October 2, 2018)
Researchers at Proofpoint have observed a new phishing campaign targeting individuals in the United States that attempts to install the “Danabot” banking trojan. The phishing email takes the guise of originating from “eFax,” an online faxing company, with a link to a document attached that is supposedly an invoice. The document link requests macros to be enabled to view that document, and if enabled, Hancitor malware is executed which installs both “Pony” information-stealer and the Danabot banking malware. The Danabot malware downloads a main component that contains a list of 10 hardcoded Command and Control (C2) IP addresses. The hardcoded lists changed approximately every hour when a main component is downloaded. It is suspected that this is to create decoys to make reverse-engineering the malware more difficult, as about only a handful of the C2 IP addresses appear to be routable and responsive. Since the Danabot banking trojan contains several anti-analysis features, it is attractive to threat actors, and therefore there has been an increase in its usage by them.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193)
Vulnerable Android Password Managers Make Phishing Attacks Easier (October 2, 2018)
Academic researchers from the University of Genoa discovered that several Android password managing applications such as LastPass, 1Password, Dashlane, and others, trust an application if it appears to have the correct application package name. This means that these password managing sites can be vulnerable to phishing attacks by threat actors who develop fake applications that impersonate a valid package name. If the password managing applications read the malicious application as trustworthy, it will automatically suggest or fill-in credentials on the login pages. This is dangerous because Google can allow users to “try” Android applications without fully installing them onto their device, called Instant Apps. Threat actors can exploit the Instant Apps feature to trick password managers into filling in credentials, and this gains unauthorised access to legitimate sites.
Click here for Anomali recommendation
New iPhone Passcode Bypass Hack Exposes Photos And Contacts (October 1, 2018)
An independent researcher discovered a password bypass vulnerability in the new iOS 12 update in Apple products. The vulnerability allows a threat actor to access a user’s phone contacts and pictures on a locked iPhone XS device and other recent iPhone models through bypassing the passcode screen. The process takes approximately 37 steps to achieve and requires a threat actor to have physical access to the device in order to attempt the passcode bypass. At the publication of this article, a patch for this vulnerability has yet to be released.
Click here for Anomali recommendation
The Kingdom Came To Canada: How Saudi-Linked Digital Espionage Reached Canadian Soil (October 1, 2018)
A Saudi Arabian activist, Omar Abdulaziz, who is currently residing in Canada had his cell phone targeted and infected with “Pegasus” spyware that was created by the Israeli company, NSO Group. Abdulaziz is a known dissident to Saudi Arabia and has consistently spoken out against the human rights violations and repressive tactics the Saudi government allegedly partakes in. He received a phishing text message regarding a DHL shipment that, upon further research, was a Pegasus domain that exploited his device and subsequently infected it with the spyware. It is suspected that the Saudi government-linked threat group, “KINGDOM,” is behind the spyware infection. This is yet another recent example of spyware intended officially for tracking criminals and terrorists, used to spy on dissidents of more repressive governments.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Link (T1192)
NOKKI Almost Ties the Knot With DOGCALL: Reaper Group Uses New Malware To Deploy RAT (October 1, 2018)
Security researchers at Palo Alto Networks have observed a spear phishing campaign targeting Russian and Cambodian-speaking individuals and organisations. The spear phishing campaign began in July 2018, and attempted to infect individuals with the NOKKI malware. The spear phishing emails contained politically-motivated lures and contained a malicious Microsoft Office Word document that requested macros to be enabled to install the malware. The NOKKI malware sample contains a DOGCALL malware payload within it, which is used by the Advanced Persistent Threat (APT) group, Reaper, so this campaign is suspected to be attributed to them.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Obfuscated Files or Information (T1027) | [MITRE ATT&CK] Spearphishing Attachment (T1193)
Observed Threats
This section includes the top threats observed from the Anomali Community user base as well as sensors deployed by Anomali Labs. Additional information regarding the threats discussed in this week's Community Threat Briefing can be found below:
Lazarus Group
The Advanced Persistent Threat group (APT) “Lazarus Group” is believed to be based in the Democratic People's Republic of Korea (DPRK) and has been active since at least 2009. Lazarus Group is believed to be composed of operatives from “Bureau 121” (121?), the cyber warfare division of North Korea’s Reconnaissance General Bureau. The Reconnaissance General Bureau was formed due to a reorganization in 2009 but its exact structure is not known due to North Korea’s denial and deception tactics. Bureau 121 is North Korea’s most important cyber unit that is used for both offensive and defensive operations. Bureau 121 are referred, in South Korean open-source media, as the “Electronic Reconnaissance Bureau’s Cyber Warfare Guidance Bureau” (????? ???????). The term “guidance” in the context of North Korea often denotes that an organization is personally overseen by the head of state of North Korea as a strategically significant entity. Lazarus Group has targeted financial organizations since at least July 2009, The group is well known for their tendency to engage in data destruction/disk wiping attacks, and network traffic Distributed Denial-of-Service (DDoS) attacks, typically against the Republic of Korea (South Korea). The group targets various industries and sectors including South Korean and US government organizations, Non-Governmental Organizations (NGO), media and entertainment organizations, as well as shipping and transportation organizations, Korean hydro and nuclear power, and jamming of South Korean GPS.
FIN7
The Advanced Persistent Threat (APT) group, “FIN7,” is believed to be a Russia-based group. The group is financially motivated and has been conducting multiple spear phishing campaigns that target government organizations as well as public and private businesses. Researchers believe that FIN7 is associated with another Russian APT group called, “Carbanak” because they use the same backdoor malware.
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



