Blog
Automate Your Workflows With Threat Intelligence Alerts in Slack
Setup alerts that feed from the Anomali ThreatStream Splunk App into Slack.

David Greenwood
August 3, 2017
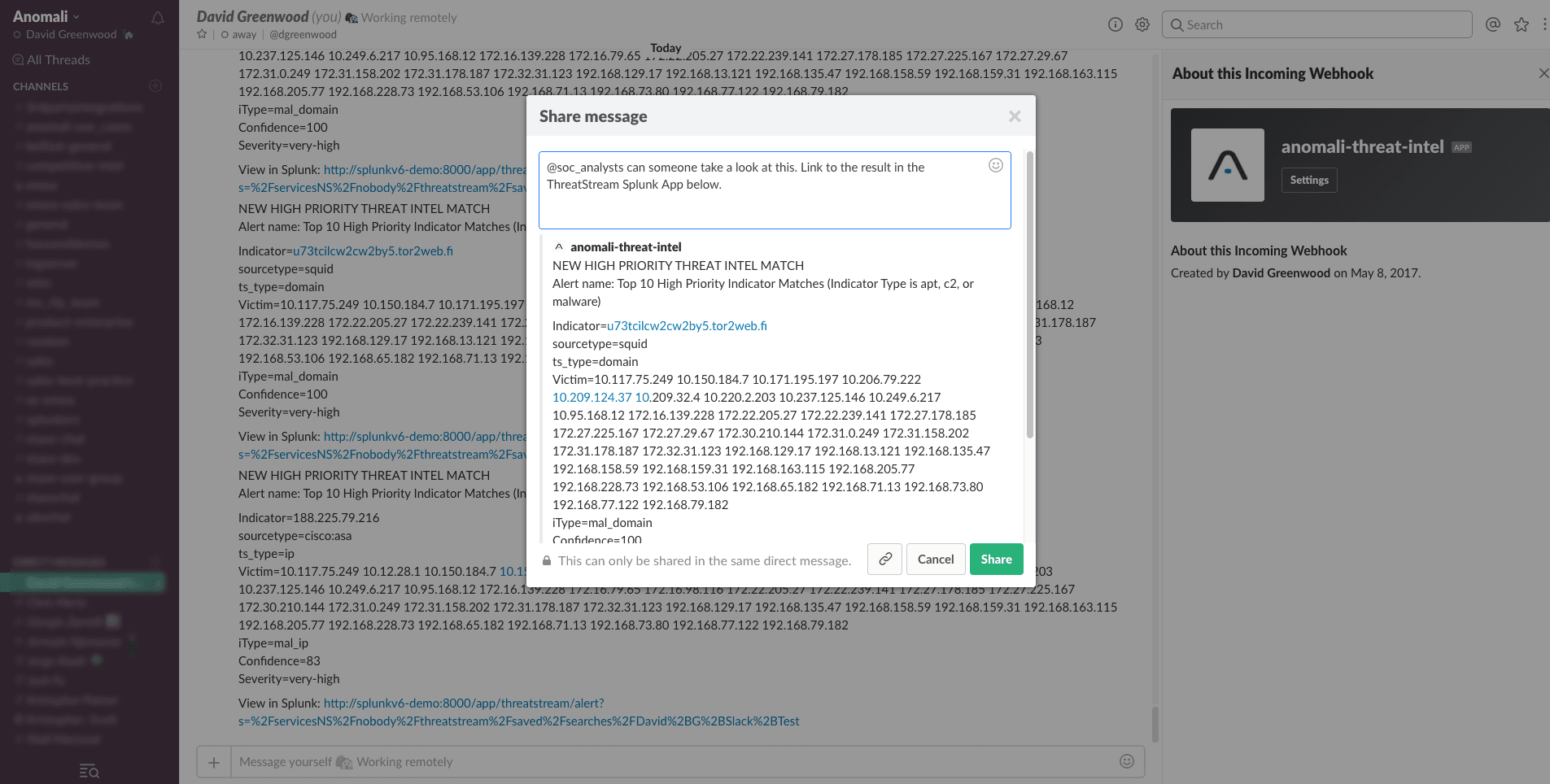
<p>Recently, I was speaking to a friend who is using the popular messaging app, Slack, to help run the Security Operations Centre (SOC) at his organisation. Not only have they have setup alerts that feed from their security tools into Slack, but the analysts can run queries against these tools, like Splunk, directly from Slack messages.</p><p>Clearly this is a very mature security team who have setup a workflow that meets their organisational needs well. It won't work for everyone. None-the-less, many organisations use Slack heavily, including us here at Anomali. My mind then started to dream up ways we could introduce our threat intelligence workflows and investigations into Slack.</p><p>My first thoughts were; the incident information generated by our <a href="https://www.anomali.com/blog/anomali-threatstream-splunk-app-v6-released">Anomali ThreatStream Splunk App</a> would be a perfect place to start, and here's what I setup in a spare 20 minutes.</p><h2>Anomali ThreatStream Splunk App</h2><p><img alt="" src="https://cdn.filestackcontent.com/XRgN4OQOCr6CstC6r3fw"/></p><p>Existing ThreatStream and Splunk customers will be running a large part of their threat intelligence functions through our Splunk App. The app comes pre-built with many saved searches, visualisations, and alerts that help users focus on the most critical security incidents where Splunk events have matched a particularly malicious ThreatStream indicator of compromise (IOC).</p><p>These searches also give us a great starting point for customisation for our own use-cases, for now; deciding what information we want to be notified about in Slack. More to come on that later.</p><h2>Slack Alert Action</h2><p><img alt="" src="https://cdn.filestackcontent.com/bEYvVHSRSP2iKMf8YV1p"/></p><p>We will use Splunk alerts to notify us of high priority ThreatStream matches. Before we can setup the alert, we need to configure the Slack alert action that is performed when a Splunk alert is triggered. Installing the Splunk Slack Webhook Alert App is the easiest way to do this. You can download the app for free here: https://splunkbase.splunk.com/app/3525/</p><p>Once you've installed the app on Splunk, you will need to create an Outgoing Webhook integration in your Slack team settings. Here you can define where the Splunk alert is delivered, amongst other variables.</p><h2>Anomali ThreatStream High Priority Match Alert</h2><p><img alt="" src="https://cdn.filestackcontent.com/lBLLJVaVQG2MncvcVfxH"/></p><p>Many of the visualisations in the ThreatStream Splunk App allow you to pivot on matches by severity or indicator type (i.e. C2 IPs, malware file hashes, etc), for example. We can leverage the searches that power these dashboard panels to create an alert. One of my favourite panels in the app considers the 10 highest priority matches that have been observed (apt, c2, or malware indicators with high confidence scores). The search that powers it looks like this:</p><p><code>index=threatstream_summary (apt_* OR mal_* OR c2_*) (event.ts_itype=*apt_* OR event.ts_itype=*mal_* OR event.ts_itype=*c2_*) | rename event.* as * | `ts_get_time_offset(_time, ts_date_last)` | eval my_confidence = max(split(ts_confidence, ";")) | eval age = min(Age) | where my_confidence > 80 AND age < 31 | table _time, Age, ts_confidence, count, victim, ts_lookup_key_value, ts_source, ts_itype, ts_severity, ts_type, sourcetype | foreach * [eval <<field>>=split(<<field>>, ";")] | mvexpand ts_lookup_key_value | stats max(_time) as _time, values(victim) as Victim, min(Age) as Age, values(ts_source) as "Indicator Source", values(ts_itype) as "iType", values(ts_confidence) as Confidence, values(ts_severity) as Severity by ts_lookup_key_value, sourcetype, ts_type | sort Age | head 10 | rename ts_lookup_key_value as Indicator</field></field></code></p><p>For those familiar with Splunk searches, this search can be customised to include different indicators or thresholds. I set the time range to "Last 3 hours", though you can just as easily use a more appropriate time range for your organisations requirements, and saved this as an alert.</p><p>Under trigger actions select the "Slack Webhook Alert" action I then entered the webhook URL generated earlier. <a href="http://docs.splunk.com/Documentation/Splunk/6.6.2/Alert/EmailNotificationTokens">You can customise the Slack message delivered using tokens in Splunk</a>. Here's an example:</p><p><code>NEW HIGH PRIORITY THREAT INTEL MATCH<br/> Alert name: $name$<br/> <br/> Indicator=$result.Indicator$ <br/> sourcetype=$result.sourcetype$ <br/> ts_type=$result.ts_type$ <br/> Victim=$result.Victim$ <br/> iType=$result.iType$ <br/> Confidence=$result.Confidence$ <br/> Severity=$result.Severity$<br/> <br/> View in Splunk: $view_link$</code></p><p>You can view my savedsearch.conf stanza for this alert on Github: https://gist.github.com/himynamesdave/2b0c1c7f6a845bfe383e74bc51fa0850</p><h2>Working With Threat Incidents in Slack</h2><p><img alt="" src="https://cdn.filestackcontent.com/a5ADh7yS3KED6HsgOKcw"/></p><p>Once the message has been delivered, I could start to take action in Slack. Perhaps starting the investigation myself, or forwarding to a team member. The detail provided in the Slack message gives deep context about the threat, in the example above, a malware domain that has been observed on a number of internal servers (victims). What makes it really easy is the Splunk link delivered in the message (using the $view_link$ token setup in Splunk), that links straight back to the ThreatStream Splunk App and the result in question.</p><h2>Not a ThreatStream Customer Yet?</h2><p><a href="https://www.anomali.com/blog/proactively-monitor-your-network-against-attacks-using-our-free-threatstrea">Our ThreatStream Splunk Community App is a limited feature version of our full app described in the post</a>. While functionality and intelligence is significantly reduced in the Community App, you can follow the same logic, with slightly different searches, to create Slack alerts using the threat information it provides.</p>
Discover More About Anomali
Get the latest news about cybersecurity, threat intelligence, and Anomali's Security and IT Operations platform.
Propel your mission with amplified visibility, analytics, and AI.
Learn how Anomali can help you cost-effectively improve your security posture.