Weekly Threat Briefing: Hackers Could Exploit a Zoom App Vulnerability to Disrupt Conferences
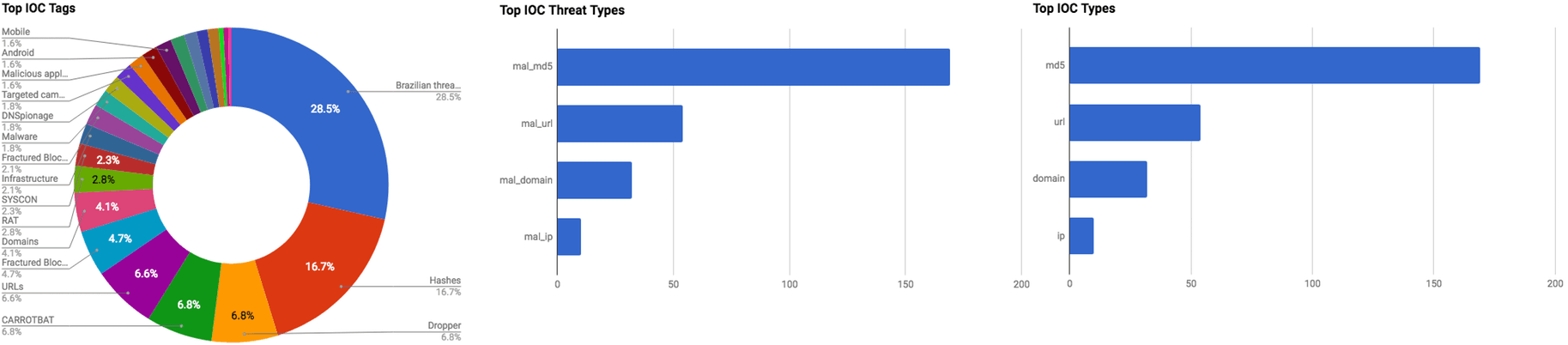

The intelligence in this week’s iteration discuss the following threats: BEC, Data breach, Data theft, Exposed PII, Malicious applications, Phishing, Spear phishing, RAT, Targeted attacks, Unauthorized access, and Vulnerabilities. The IOCs related to these stories are attached to the Community Threat Briefing and can be used to check your logs for potential malicious activity.
Trending Threats
Router Attack Exploits UPnP and NSA Malware to Target PCs (December 3, 2018)
A campaign has been found to be targeting routers with leaked National Security Agency (NSA) tools and their associated vulnerabilities, according to Akamai researchers. Threat actors are using EternalBlue (CVE-2017-0144) and EternalRed (CVE-2017-7494) exploits to target machines that are running “Windows SMB” and “Linux Samba” clients, specifically on ports 145 and 449. The actors behind this campaign are targeting machines and routers, and researchers believe that at least 45,000 routers have been targeted and the amount of vulnerable machines is estimated to be approximately 1.7 million. The affected routers are those that run vulnerable implementations of Universal Plug and Play (UPnP) implementations.
Click here for Anomali recommendation
Hackers Could Exploit a Zoom App Vulnerability to Disrupt Conferences (December 2, 2018)
Security researcher David Wells from Tenable discovered a vulnerability that affects the “Zoom Desktop Conferencing App.” The vulnerability, which existed because of incorrect message validation, could allow a threat actor to gain the ability to execute unauthorized commands on a machine running the affected Zoom application. In addition to the ability the download and execute malware, an actor could also create fake messages, remove meeting attendees, and take control of a presenter’s screen. An actor would need to know the Zoom server IP address and inject custom-created UDP packets into ongoing sessions to exploit this vulnerability.
Click here for Anomali recommendation
Magecart Fiends Punch Card-Skimming Code in Sotheby’s Home Website (November 30, 2018)
The US-based art dealer company “Sotheby’s” had its website compromised by the financially-motivated threat group, “Magecart,” since at least March 2017, according to a statement released by the company to its customers. Sotheby’s confirmed that its website was compromised and infected with card-skimming malware that stole data that was entered in the company’s checkout page. Sotheby’s stated that it “became aware” of the incident on October 10, 2018. The stolen data, which affects an undetermined amount of customers, consisted of the following: addresses, email addresses, and payment card numbers. The company also said that card expiration dates and CVV codes may have also been stolen during the time the website was compromised. Since its discovery, Sotheby has removed the malware from their checkout page and has reportedly implemented additional security measures on their site.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scripting (T1064)
Marriott Announces Data Breach Affecting 500 Million Hotel Guests (November 30, 2018)
The international hotel chain “Marriott,” has confirmed in a statement that it was affected by a data breach dating back to 2014 that affects approximately 500 million individuals who stayed at its “Starwood” hotels. The company stated that it became aware of the breach on September 10, which was two days after Marriott staff observed an alert from an internal security tool. The tool notified the staff about an attempt to access “Starwood,” a Marriott subsidiary, guest reservation database in the US. Marriott stated that the “company has not yet finished identifying duplicate information in the database, but believes it contains information on up to approximately 500 million guests who made a reservation at a Starwood property.” The database that was illicitly accessed contained information such as: arrival and departure information, combination of name, communication preferences, date of birth, email address, passport number, phone number, Starwood preferred guest information, and reservation date. Some individuals’ payment card information was also accessed, albeit the data was encrypted with AES-128.
Click here for Anomali recommendation
The Fractured Block Campaign: CARROTBAT Used to Deliver Malware Targeting Southeast Asia (November 29, 2018)
A new malware campaign has been discovered that is targeting entities located in Southeast Asia, according to Unit 42 researchers. The threat actors behind this campaign were observed using a new, custom dropper that distribute lures themed around North and South Korea. The campaign, dubbed “Fractured Block,” attempts to distribute and subsequently infect machines with a malware family dubbed “CARROTBAT,” which refers to the dropper in this campaign. CARROTBAT was first identified in an attack in December 2017 that targeted a British government entity with a Remote Access Trojan (RAT) called “SYSCON” and it was through this connection that researchers identified the Fractured Block campaign. At the time of this writing, researchers have not specified what CARROTBAT’s initial infection vector is, however, they do note that it has been observed dropping decoy files in 11 different document file formats.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Obfuscated Files or Information (T1027) | [MITRE ATT&CK] Exfiltration Over Command and Control Channel (T1041)
Pervasive Brazilian Financial Malware Targets Bank Customer in Latin America and Europe (November 29, 2018)
Cybereason researchers have published a report in which they detail Brazilian threat actor activity in various campaigns that target more than 60 banks around the globe in 2017 through 2018. Researchers analyzed recent activity originating from Brazil and found that the most targeted country in recent campaigns is Spain, with other highly targeted countries including Argentina, Bolivia, Chile, Colombia, Mexico, and Venezuela. Frequently observed Tactic, Techniques, and Procedures (TTPs) consist of the following: DLL hijacking, living off the land via abuse of Microsoft-signed binaries, multiple redirections via URL shorteners and use of Dynamic DNS services, obfuscated PowerShell downloaders, payloads hosted on authentic online storage services and Content Delivery Networks (CNDs), social engineering as initial entry point, and splitting the primary payload into two or more components.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Spearphishing Attachment (T1193) | [MITRE ATT&CK] Obfuscated Files or Information (T1027) | [MITRE ATT&CK] Trusted Relationship (T1199) | [MITRE ATT&CK] Spearphishing Link (T1192)
Dell Systems Hacked to Steal Customer Information (November 29, 2018)
The US-based computer technology company “Dell,” has confirmed that unknown threat actors managed to gain unauthorized access to its network. Dell detected this unauthorized activity on November 9, 2018 and discovered that actors were attempting to steal dell[.]com information consisting of email addresses, hashed passwords, and names. As of this writing, Dell has not found any “conclusive evidence” that data, including credit card information, was stolen.
Click here for Anomali recommendation
ElasticSearch Server Exposed the Personal Data of Over 57 Million US Citizens (November 28, 2018)
Bob Diachenko, Director of Cyber Risk Research for HackenProof, discovered a publicly accessible ElasticSearch server that contained Personally Identifiable Information (PII) associated to approximately 57 million US citizens. The server was identified on November 20, 2018, and is believed to have been left publicly accessible since at least November 14. The ElasticSearch server contained over 73 gigabytes of data consisting of 56,934,021 records. These records contained information such as: email address, first name, home address, IP address, last name, phone number, state, and ZIP code. In addition, it was also discovered that the server contained a cached database called “Yellow Pages” that contained an additional 25,917,820 records. These records are believed to be business entries and contained information including: carrier routes, company details, company name, census tracts, email addresses, employee counts, latitude/longitude coordinates, North American Industry Classification System (NAIC) codes, Standard Industrial Classification (SIC) codes, and web addresses, among others. At the time of this writing it is unclear who owns this server, but Diachenko believes that it is owned by the Canadian Data forum “Data & Leads.”
Click here for Anomali recommendation
Atrium Health Says Hacking Compromised Personal Data of More Than 2 Million People (November 27, 2018)
The Charlotte, North Carolina-based healthcare company, “Atrium Health,” confirmed that on November 27, 2018, that it had suffered a data breach. Unknown threat actors were able to gain illicit access to Atrium’s billing vendor “AccuDoc” server and patient information between September 22 and 29, 2018. AccuDoc identified the breach on October 1, 2018. This breach is believed to affect approximately 2.65 million individuals out of which 700,000 may have had their social security numbers compromised. Other compromised data consists of: account balance, dates of service, insurance policy information, and medical record numbers. Atrium stated that while the information was accessed, none of it appeared to have been downloaded.
Click here for Anomali recommendation
New BEC Scams Take Advantage of the California Wildfires (November 27, 2018)
Agari researchers have found that threat actors are attempting to take advantage of the California wildfires for malicious purposes, specifically, a Business Email Compromise (BEC) campaign. Threat actors are distributing emails that purport to be from the CEO of an unnamed company that requests that the recipient send help to assist clients who have been “caught up in the California wildfire disaster.” Interestingly, the actors do not explicitly ask for funds to be transferred, but instead asks the recipient to purchase and subsequently send him/her the card redemption codes listed on four Google Play gift cards valued at $500 USD each. The broken English in the email indicates that the actors are likely not native English-speakers, and the use of Google Play gift cards is an interesting way to acquire illicit funds that are essentially untraceable.
Click here for Anomali recommendation
Autolt-Compiled Worm Affecting Removable Media Drivers Fileless Version of BLADABINDA/njRAT Backdoor (November 27, 2018)
A variant of the “BLADABINDI” (njRAT, Njw0rm) Remote Access Trojan (RAT) has been observed to be distributed through a worm that propagates through removable drives, according to Trend Micro researchers. The worm’s objective is to install a fileless version of the BLADABINDI backdoor that has multiple capabilities including Distributed Denial-of-Service (DDoS) attacks and keylogging, among others. As of this writing, it is unknown how the worm actually arrives on a machine. Researchers note that the use of “Autolt” (the FileInstall command) to compile the RAT payload makes BLADABINDI difficult to detect.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Replication Through Removable Media (T1091)
Fake Voice Apps on Google Play, Botnet Likely in Development (November 27, 2018)
Trend Micro researchers have identified several malicious applications on the Google Play store that appear to be indicative of a botnet being in development. The applications masquerade as authentic voice messenger platforms. Researchers found that the applications contained automatic functionalities, and that applications and their malicious capabilities have been continuously added to since October 2018. Some of the features utilized by these applications consist of automatic pop-ups, fake surveys, and fraudulent advertisement clicks in addition to modular functions such as evolving evasion techniques and different infection actions. The threat actors behind this campaign tagged some of their samples “1.0” which causes researchers to assume assess that this may be a botnet in an early development phase.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Trusted Relationship (T1199)
DNSpionage Targets Middle East (November 27, 2018)
A new campaign has been identified to be targeting Lebanon and the United Arab Emirates .gov domains and a Lebanese airline company, according to Cisco Talos researchers. The unknown threat actors behind this campaign are targeting users of said websites with Microsoft Office documents that contain a malicious macro. The actors attempt to compromise the website visitors, or individuals deemed as targets, by creating domains that impersonated the authentic ones or potentially distributing spear phishing emails. These actor-created websites hosted a document that is a copy of a genuine document that is provided by the Canadian energy company “Suncor Energy” that contains a malicious macro. The document requests the user to “Enable Content,” which will cause a macro to launch when the document is closed that creates a scheduled task for the dropped Remote Access Tool (RAT) payload called “DNSpionage.” The link for the document was likely distributed via a spear phishing campaign, but as of this writing researchers are not certain.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Scheduled Task (T1053) | [MITRE ATT&CK] Obfuscated Files or Information (T1027) | [MITRE ATT&CK] Spearphishing Link (T1192) | [MITRE ATT&CK] Spearphishing Attachment (T1193)
Hacker Stole $1m from Silicon Valley Executive via SIM Swap (November 26, 2018)
A felony complaint has been filed in a California state court for a New York resident named Nicholas Truglia for an alleged theft of one million USD. Trugila is reported to have stolen $500,000 USD worth of cryptocurrency held in two separate accounts in the Coinbase and Gemini cryptocurrency exchanges. Truglia stole the funds via a tactic known as “SIM swapping” in which the actor gained physical access to the victim’s, Robert Ross, cell phone and swapped the SIM cards. This tactic is believed to have been used by Truglia in targeting at least six executives working in Silicon Valley. In Ross’s case, Truglia went on to convert the cryptocurrencies, $500,000 in each Coinbase and Gemini account, into digital money and then into his personal account.
Click here for Anomali recommendation
Rogue Developer Infects Widely Used NodeJS Module to Steal Bitcoins (November 26, 2018)
The open source JavaScript run-time environment, “Node.js,” was observed to have been the victim of a rogue developer who implanted malicious code into the Node.js library “Event-Stream.” The malicious code, discovered by California State University student Ayrton Sparling, was contained inside Event-Stream version 3.3.6 inside of which was a library called “Flatmap-Stream.” The library was created purposely with malicious code designed to steal funds stored in Bitcoin wallet applications. The code, believed to have been developed by an unknown programmer known as “right9ctrl,” was pushed to Node.js on September 9, 2018 and has since garnered approximately eight million downloads.
Click here for Anomali recommendation
MITRE ATT&CK: [MITRE ATT&CK] Supply Chain Compromise (T1195)
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



