Weekly Threat Briefing: Lenovo Patches Arbitrary Code Execution Flaw
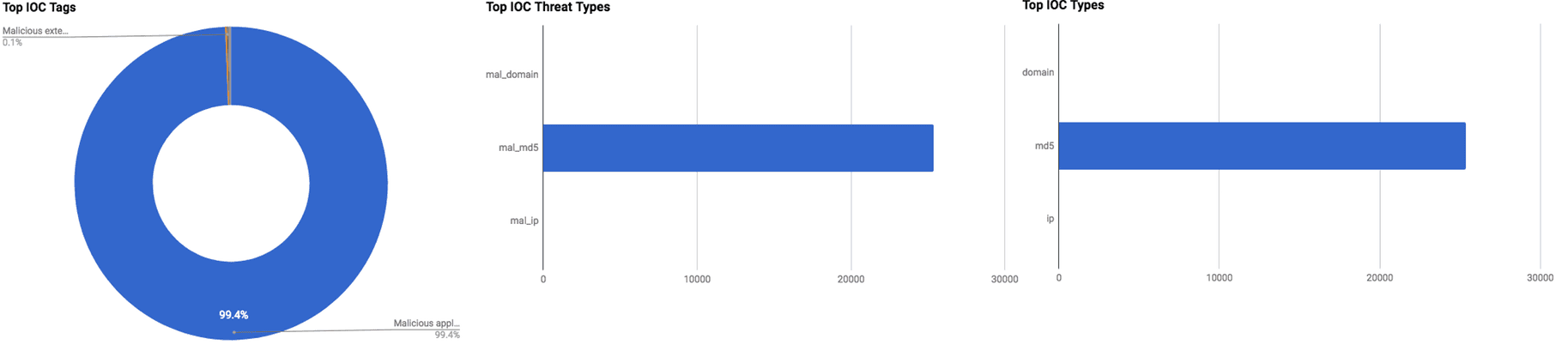

The intelligence in this week’s iteration discuss the following threats: APT, APT28, Cryptocurrency miner, Malspam, Malicious applications, Phishing, Ransomware, Targeted attacks, and Vulnerabilities. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
Lenovo Patches Arbitrary Code Execution Flaw (May 7, 2018)
Lenovo has addressed two security updates that address vulnerabilities which affect products in its “ThinkPad” line and “System x” servers. This first vulnerability addressed lies in “Secure Boot,” which is registered as “CVE-2017-3775,” and is rated as high-severity. The second vulnerability, registered as “CVE-2018-9063,” is a buffer overflow vulnerability rated as medium-severity.
Click here for Anomali recommendation
SynAck Targeted Ransomware Uses the Doppelgänging Technique (May 7, 2018)
Threat actors are using a bypass technique called “Process Doppelgänging” to distribute a new variant of the “SynAck” ransomware, according to Kaspersky Lab researchers. Process Doppelgänging is a fileless code injection technique that works on all Windows versions by utilizing a built-in Windows function and an undocumented implementation of Windows process loader; the technique was first explained at the 2017 BlackHat conference. Researchers observed this technique first being utilized by actors in April 2018. The ransomware encrypts files with the AES-256-ECb algorithm.
Click here for Anomali recommendation
GandCrab V3 Accidentally Locks Systems with New “Change Wallpaper” Feature (May 4, 2018)
The threat actors behind the “GandCrab” ransomware have added new features to the malware and spam email distribution, according to Fortinet researchers. In regards to the email spam distribution, the tactics are essentially the same in that the emails ask the recipient to open an attachment and reply as soon as possible. In a change from previous malicious attachments, the current iteration uses Visual Basic Scripts (VBS) instead of JScripts. After the malware has encrypted files it forces a reboot and changes the machine’s desktop image, however, on Windows 7 the malware gets stuck prior to the Windows Shell completely loading. This means that this version of GandCrab could leave the entire machine “seemingly unusable.”
Click here for Anomali recommendation
Kaspersky Lab Discovers ZooPark, an Android-based Malware Campaign (May 3, 2018)
A previously unknown Advanced Persistent Threat, dubbed “ZooPark,” has been identified to be targeting Android users in Middle Eastern countries, according to Kaspersky Lab researchers. The group was discovered when Kaspersky Lab received a sample of an unknown Android malware. Further research into this malware led to the discovery a recent version of the malware contained in the same application as the initial sample. The malicious applications impersonate legitimate applications with names such as “TelegramGroups” and “Alnaharegypt news,” among others that are relevant in some targeted countries. The ZooPark malware is distributed on news and political websites and is capable of stealing various forms of data as well as executing shell commands.
Click here for Anomali recommendation
Vulnerabilities Affecting Over One Million Dasan GPON Routers Are Now Under Attack (May 4, 2018)
An authentication bypass vulnerability (CVE-2018-10561) and a remote code execution vulnerability (CVE-2018-10562) that affect Dasan Gigabit Passive Optical Network (GPON) routers are actively being exploited, according to Qihoo 360 Netlab researchers. Specifically, the attacks began on May, several days after an anonymous researcher published information discussing both vulnerabilities. In addition, the researcher said that he/she found over one million vulnerable services via the internet scanning tool Shodan.
Click here for Anomali recommendation
Crypto Me0wing Attacks: Kitty Cashes in on Monero (May 2, 2018)
Threat actors are still exploiting the Drupal platform vulnerability, known as “Dupralgeddon2.0” and registered as “CVE-2018-7600,” nearly one month after the vulnerability was addressed. In this instance, actors are exploiting Drupalgeddon2.0 to install a Monero cryptocurrency mining malware called “Kitty,” according to Imperva researchers. The Kitty cryptocurrency malware utilizes a publicly available web browser mining software called “webminerpool” and the “XMRig” CPU miner to mine Monero. In addition to being able to maintain persistence on a web server, Kitty is also capable of infecting visitors to websites hosted on compromised servers.
Click here for Anomali recommendation
Microsoft Releases Security Update (May 2, 2018)
The United States Computer Emergency Readiness Team (US-CERT) has issued an alert regarding a vulnerability in the Windows Host Compute Service Shim (hcsshim). A threat actor could exploit this vulnerability, registered as “CVE-2018-8115,” to execute arbitrary code on an affected system.
Click here for Anomali recommendation
Convincing Fake Netflix Page Phishing for Victims’ Credit Cards (May 1, 2018)
A well-designed phishing campaign has been found by ESET researchers to be targeting Netflix users in attempts to steal credit card information. The phishing emails purport that Netflix was unable to renew the recipient’s subscription, and thus the email serves as a cancellation notice. The emails contain a link for “restarting” the membership that leads to a webpage that impersonated the authentic Netflix login page. After “logging in&rdqurdquo a page is presented that harvests payment data.
Click here for Anomali recommendation
MassMiner Malware Targeting Web Servers (May 1, 2018)
A cryptocurrency mining malware, dubbed “MassMiner,” has been observed to contain more features than a typical mining malware family, according to AlienVault researchers. MassMiner is capable of propagating via the following three vulnerabilities: CVE-2017-10271 (WebLogic vulnerability), CVE-2017-0143 (vulnerability used by EnternalBlue SMB exploit to install DoublePulsar), and CVE-2017-5638 (Apache Struts vulnerability). In addition to exploiting said vulnerabilities, MassMiner is also capable of conducting brute-force attacks against Microsoft SQL Servers via a tool called “SQlck.” Once infection has taken place, the malware will begin mining the “Monero” cryptocurrency.
Click here for Anomali recommendation
Lojack Becomes a Double-Agent (May 1, 2018)
ASERT researchers have discovered that an anti-theft software tool called “Lojack for Laptops,” is being used for malicious purposes by the Russian state-sponsored Advanced Persistent Threat group “APT28” (Fancy Bear, Pawn Storm). Researchers identified that the software was being used by APT28 actors when hijacked Lojack agents were observed pointing to domains known to be associated with the group. APT28 is using the hijacked Lojak agents to disguise their malicious activity to appear to originate from a legitimate source. At the time of this writing it is unknown how APT28 is initially infecting a target, however, it is known that APT28’s primary infection is typically spear phishing emails.
Click here for Anomali recommendation
Legitimate Application AnyDesk Bundles with New Ransomware Variant (May 1, 2018)
A new ransomware, dubbed “Blackheart,” was identified bundled together with the legitimate remote desktop application “AnyDesk,” according to Trend Micro researchers. In addition, researchers note that while the initial infection vector is unknown, they have observed cases in which users unknowingly downloaded Blackheart upon visiting a malicious website. Once the ransomware is executed, it will drop and execute two additional files, the ransomware executable and an AnyDesk executable. The threat actors behind this campaign are demanding 0.06164 bitcoins (approximately $50 USD) for the decryption key.
Click here for Anomali recommendation
Tens of Thousands of Malicious Apps Using Facebook APIs (May 1, 2018)
Approximately 25,936 malicious applications were found to be using one of Facebook’s APIs to gather information, according to Trustlook researchers. This information includes a variety of data that can be gathered from a Facebook profile such as email address, full name, and location. Some of these applications were found to be capable of taking pictures and capturing audio even when the application is closed.
Click here for Anomali recommendation
FacexWorm Targets Cryptocurrency Trading Platforms, Abuses Facebook Messenger for Propagation (April 30, 2018)
Trend Micro researchers have found that the malicious Chrome extension, dubbed “FacexWorm,” has added new features to its malicious capabilities. The malicious extension uses Facebook Messenger for distribution by directing message recipients to a Youtube page that asks the user to install a codec extension; the codec extension is FacexWorm. Installation of the extension results in a request for the privilege to access and change data on a website. These permissions allow FacexWorm to install cryptocurrency miners on web browsers, and hijacks transactions by replacing a user’s wallet with one owned by the threat actor(s) controlling the malware, among other theft techniques.
Click here for Anomali recommendation
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



