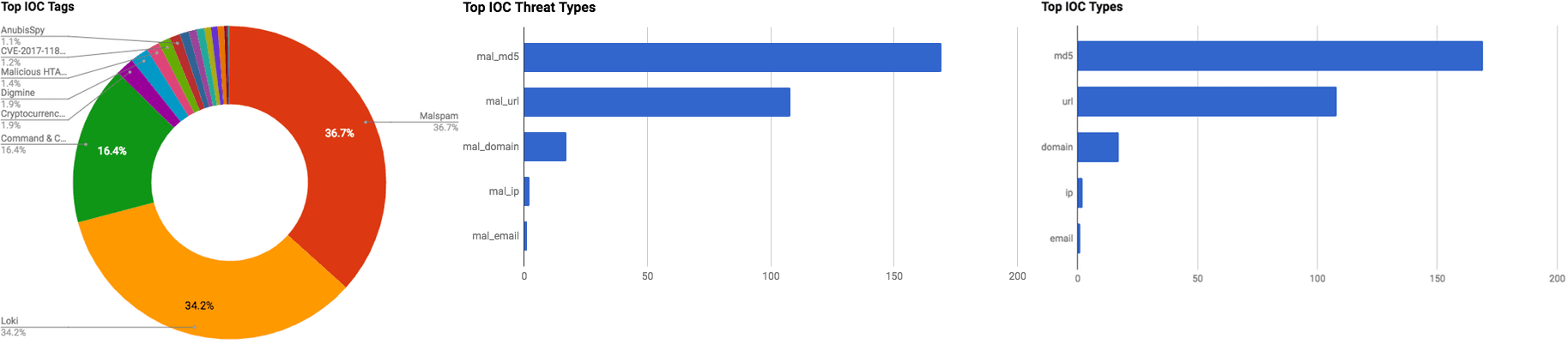

The intelligence in this week’s iteration discuss the following threats: Data leak, Information stealing malware, Malspam, Misconfigured Database, Phishing, RAT, Vulnerabilities, and Zero-day. The IOCs related to these stories are attached to the WTB and can be used to check your logs for potential malicious activity.
Trending Threats
macOS Exploit Published on the Last Day of 2017 (January 2, 2017)
A security researcher going by the alias “Siguza” has released a zero-day vulnerability that affects all versions of the Mac operating system (macOS) since at least 2002. Siguza did not notify Apple prior to publishing a report discussing the vulnerability that affects the “IOHIDFamily” macOS kernel driver. According to Siguza, the vulnerability is a Local Privilege Escalation (LPE) flaw that an actor can only exploit with local access to, or previous malware infection of the affected machine.
Click here for Anomali recommendation
Resume-Themed Malspam Pushing Dreambot Banking Trojan (December 29, 2017)
Researchers have observed a new malspam campaign that is distributing the “Dreambot” banking trojan. In the emails, the actors behind this campaign purport to be sending the recipient a resume to consider. The actors also include “Happy New Year” in the email in an attempt to stay relevant to the current timeframe and to attempt to add legitimacy to the emails. The “resume” attachment is a zip file that, if opened, will extract a JSE file (JScript) and begin the infection process for Dreambot.
Click here for Anomali recommendation
Flaws in Sonos and Bose Smart Speakers Let Hackers Play Pranks on Users (December 27, 2017)
Trend Micro researchers Stephen Hill, has discovered that some “Bose” and “Sonos” smart speakers are affected by vulnerabilities that could allow a threat actor to take over the device. In addition, the vulnerabilities can be exploited by actors who are performing reconnaissance and are trying to gain access to a corporate network, or gather information stored on the device to conduct potentially more effective phishing attacks. Researchers report that the affected smart speakers are “Sonos Play:1” and “Bose SoundTouch,” however, it is possible that more models are also affected.
Click here for Anomali recommendation
Mozilla Releases Security Update for Thunderbird (December 25, 2017)
The United States Computer Emergency Readiness Team (US-CERT) has issued an alert regarding multiple vulnerabilities in Mozilla’s “Thunderbird” platform. Mozilla’s security advisory lists five vulnerabilities that affect Thunderbird 52.5.2. Out of the vulnerabilities, two are listed as critical, two as high, and one as low. Some of the vulnerabilities allow remote code execution.
Click here for Anomali recommendation
Vulnerability Affects Hundreds of Thousands of IoT Devices (December 25, 2017)
Researchers have discovered a vulnerability, registered as “CVE-2017-1756,” in a web server package called “GoAhead” created by the company “Embedthis Software.” GoAhead is located in hundreds of thousands of IoT devices as well as well deployed inside other products such as Comcast, Oracle, and HP, among others. Elttam researchers identified a method in which they could execute malicious code remotely on any device that used the GoAhead web server package.
Click here for Anomali recommendation
Malspam Uses CVE-2017-0199 To Distribute Remcos RAT (December 22, 2017)
Researchers have discovered that threat actors are exploiting the Microsoft Office/WordPad remote code execution vulnerability registered as “CVe-2017-0199” to distribute the “Remcos” Remote Access Trojan (RAT). The malspam emails purport that the attached invoice is incorrect, and requests the recipient to make an amendment so that the sender “Helen Rowe” of “Purchasing Department” can process the payment. The attachment is an RTF file which, if opened, will present a prompt that requests the user to update the document with data from linked files. Clicking yes, and subsequently running the executable will infect the user with Remcos.
Click here for Anomali recommendation
Huawei Home Routers in Botnet Recruitment (December 21, 2017)
An updated variant of the notorious denial-of-service “Mirai” malware called “Satori” is being used to target a zero-day vulnerability in “Huawei” routers, according to Check Point researchers. A threat actor is exploiting a vulnerability, registered as “CVE-2017-17215,” that affects Huawei routers. The threat actor behind this campaign is believe to go under the alias “Nexus Zeta.”
Click here for Anomali recommendation
Digmine Cryptocurrency Miner Spreading via Facebook Messenger (December 21, 2017)
Trend Micro researchers have discovered that threat actors are distributing cryptocurrency miner malware, dubbed “Digimine” via Facebook Messenger. The malware only affects Messenger’s desktop/web browser version on Chrome. Digimine is being propagated to create a cryptocurrency mining botnet installing an auto-start mechanism on infected machines, and then continuing again using Messenger in attempts to infect other machines. Digimine is capable of mining the “Monero” cryptocurrency. The threat actors are sending zip files to their “friends” that will begin the infection process if opened.
Click here for Anomali recommendation
CVE-2017-11882 Exploited to Deliver a Cracked Version of the Loki Infostealer (December 20, 2017)
A new campaign has been found to be delivering a “cracked” version of the “Loki” information stealing malware, according to Trend Micro researchers. Threat actors are using a pirated version of Loki that is being distributed via spam emails that masquerade as an Australian shipping company with an attached receipt. The emails contain a malicious .docx file that then drops a Rich Text Format (RTF) file. The RTF file exploits the Microsoft Office vulnerability registered as “CVE-2017-11882” to download an HTML Application (HTA) dropper that then downloads the Loki payload.
Click here for Anomali recommendation
Home Economics: How Life in 123 Million American Households Was Exposed Online (December 20, 2017)
The UpGuard Cyber Risk Team has discovered that a cloud-based repository belonging to the California-based data analytics firm “Alteryx” was configured for public access. Specifically, the repository was an Amazon Web Services (AWS) S3 cloud storage bucket located on an Alteryx subdomain. The exposed data consists of Personally Identifiable Information (PII) such as financial history and mortgage ownership, in addition to 248 categories of specific data types within the AWS bucket.
Click here for Anomali recommendation
Hidden Backdoor Found In WordPress Captcha Plugin Affects Over 300,000 Sites (December 19, 2017)
Researchers have found that a plugin available for WordPress websites created by the developer “BestWebSoft” was modified by the buyer. The plugin was a Captcha that was modified in such a way that it operated as a backdoor that had the ability to affect approximately 300,000 WordPress websites. An actor could use the backdoor to gain administrator privileges on the affected website.
Click here for Anomali recommendation
Cyberespionage Campaign Sphinx Goes Mobile With AnubisSpy (December 19, 2017)
Trend Micro researchers have discovered malicious applications that made their way into the Google Play store. The applications were identified to contain malware dubbed “AnubisSpy” and are believed to be linked to a cyber espionage campaign called “Sphinx.” Researchers attribute this campaign to the Advanced Persistent Threat group “APT-C-15.” The AnubisSpy malware is capable stealing various forms of data from an infected device in addition to stealing and recording audio.
Click here for Anomali recommendation
TelegramRAT Evades Traditional Defenses via the Cloud (December 18, 2017)
The Remote Access Trojan (RAT) called “TelegramRAT” is being distributed by threat actors via a malicious Microsoft Office document, according to Netskope Threat Research Labs. TelegramRAT exploits the Microsoft vulnerability registered as “CVE-2017-11882.” Additionally, the malicious Office document uses the “Bit.ly” URL shortening service to hide TelegramRAT which is hosted on Dropbox. The RAT uses the messaging service “Telegram’s” BOT API to send and receive commands. TelegramRAT is capable of numerous malicious functions, including stealing various forms of data and deleting evidence of its presence.
Click here for Anomali recommendation
CHM Badness Delivers a Banking Trojan (December 18, 2017)
SpiderLabs researchers have discovered a malspam campaign that is targeting Brazilian institutions with the “Bancos” banking trojan. The threat actors behind this campaign are distributing the trojan via malspam emails that utilize Compiled HTML (CHM) file attachments. This tactic allows actors to conceal malicious downloader code in files and make them more difficult to detect. If the CHM is opened and subsequently decompressed by its default application, “Microsoft Help Viewer”, the HTML objects will run a JavaScript function that begins the Bancos infection process.
Click here for Anomali recommendation
FEATURED RESOURCES

Anomali Cyber Watch: Zero-Click Affects Claude, SolarWinds Vulnerabilities for Velociraptor and more



